
|
시장보고서
상품코드
1556132
사이버 보안 시장(2024-2034년)Global Cybersecurity Market 2024-2034 |
||||||
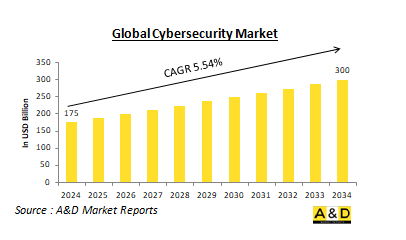
세계의 사이버 보안 시장은 2024년에 1, 750억 달러에 이르고, 예측 기간 동안 복합 연간 성장률(CAGR)은 5.54%로 추정되며, 3, 000억 달러로 성장할 것으로 예측되고 있습니다.
세계 사이버 보안 시장 개요
세계의 사이버 보안 방어란 디지털 자산, 중요 인프라, 기밀 정보를 사이버 위협으로부터 보호하기 위한 국가, 조직, 개인의 종합적인 대처를 말합니다. 상호 연결이 진행되는 세계에서 사이버 보안은 정부와 기업에게 최우선 과제입니다. 사이버 보안은 기밀 정보에 대한 접근, 변경, 파괴, 금전의 공갈, 통상 업무의 방해 등을 목적으로 하는 해커, 스패머, 사이버 범죄자에 의한 악질적인 공격으로부터 몸을 지키는데 필수적입니다. 이러한 위협은 사이버 범죄와 함께 더욱 정교해지고 광범위하게 확산되고 있습니다. 결과적으로 정부와 조직은 디지털 자산을 보호하고 이해 관계자의 신뢰를 유지하기 위해 고급 사이버 보안 기술과 전략에 많은 투자를 하고 있습니다.
세계 사이버 보안 시장의 기술 영향
기술 진보는 위협과 방어의 양면에서 세계의 사이버 보안 상황에 큰 영향을 미칩니다. 생성형 AI 및 기타 신기술의 급속한 보급은 사이버 공격자들에게 쉽게 활용되어 기업과 공공 생활에 심각한 위협을 가져오고 있습니다. 깊은 가짜와 정교한 피싱 캠페인은 민주주의의 과정을 혼란시키는 무기가 될 가능성을 가지고 있습니다. 동시에 사이버 보안 방어를 강화하기 위해 새로운 기술이 활용되고 있습니다. 인공지능(AI)과 머신러닝(ML)은 엄청난 양의 데이터를 분석하고 패턴에서 학습하며 잠재적인 위협에 대한 예측을 통해 업계에 혁명을 일으키고 있습니다. 행동 생체인식스는 ML 알고리즘을 사용하여 사용자 행동을 분석하고 계정에 무단으로 액세스한 해커와 같은 잠재적 위협을 탐지합니다. 몇 가지 중요한 기술은 세계의 사이버 보안 방어에 큰 영향을 미치고 있습니다. 제로 트러스트 아키텍처는 최전선에 있으며 네트워크 및 리소스에 액세스하려는 모든 사람과 장치에 대해 엄격한 본인 확인을 요구하며 기본적으로 아무도 신뢰할 수 없습니다는 원칙에 따라 운영됩니다. 블록체인 기술은 또한 기밀 정보를 안전하게 저장하기 위한 분산 데이터베이스를 제공함으로써 사이버 보안을 변화시키고 있습니다. 양자 컴퓨팅은 여전히 초기 단계이지만, 보다 안전한 암호화 방법을 가능하게 함으로써 사이버 보안에 혁명을 일으킬 가능성을 갖고 있습니다. 또한 다중 요소 인증, 암호화 및 액세스 제어와 같은 클라우드 보안 기술은 클라우드 환경에서 데이터를 보호하는 데 필수적입니다. 이러한 기술이 발전함에 따라 세계의 사이버 보안 방어 상황은 점점 더 형성되고 있습니다.
세계 사이버 보안 시장의 주요 촉진요인
몇 가지 중요한 요소가 세계 사이버 보안 방어 시장의 성장을 가속하고 있습니다. 사이버 위협 증가는 주요 촉진요인이며, 사이버 공격의 빈도와 복잡성은 최근 세계적으로 증가하고 있습니다. 이러한 사고는 엄청난 금전적 손실, 호평 피해, 법적 책임을 초래할 수 있습니다. 정부 및 산업 단체는 유럽 연합(EU)의 일반 데이터 보호 규칙(GDPR(EU 개인정보보호규정))과 같은 데이터 프라이버시 및 보안 규정을 강화하고 있습니다. 조직은 엄격한 벌금과 법적 결과를 피하기 위해 이러한 규정을 준수해야 합니다. 또한 사물 인터넷(IoT)의 급속한 디지털화와 보급은 사이버 범죄자의 공격 대상 영역을 확대하여 취약성과 데이터 침해의 위험을 높여줍니다. 지정학적 긴장은 사이버 보안 상황에 더욱 영향을 미칩니다. 분쟁과 불안정한 상황은 위험 역학을 빠르게 변화시키고 사이버 공격은 종종 전쟁의 도구로서 중요한 인프라와 공급망을 표적으로 할 수 있기 때문입니다. 또한 개인, 조직, 정부 간 사이버 보안의 중요성에 대한 인식이 높아지고 있으며, 디지털 자산을 보호하고 디지털 생태계의 신뢰를 유지하기 위한 노력이 강화되고 있습니다. 이러한 시장 성장 촉진요인은 향후 수년간 세계 사이버 보안 방어 시장 성장을 가속할 것으로 예상됩니다.
세계 사이버 보안 시장의 지역별 동향
세계의 사이버 보안 방어 시장은 다양한 위협 상황, 규제 환경 및 투자 우선순위에 의해 형성되는 명확한 지역별 동향을 보여줍니다. 북미는 기술 진보, 첨단 연결 솔루션에 대한 높은 수요, 방어 및 항공우주 분야에 많은 투자를 통해 시장을 선도하고 있습니다. 미국과 캐나다는 확립된 규제 프레임워크와 우주 및 위성 이니셔티브에 대한 지원을 통해 이 지역 시장 우위를 높이고 있습니다. 유럽에서는 일반 데이터 보호 규칙(GDPR(EU 개인정보보호규정))과 같은 엄격한 데이터 프라이버시 규정이 고급 사이버 보안 기술과 전략 채택에 박차를 가하고 있습니다. 유럽 연합(EU)은 또한 새로운 위협에 앞서 연구개발에 많은 투자를 하고 있습니다. 아시아태평양에서는 디지털 기술의 도입이 진행됨에 따라 사이버 위협에 대한 의식이 높아지고 있으며, 사이버 보안 방어 시장이 급성장하고 있습니다. 중국과 인도와 같은 국가들은 중요한 자산을 보호하고 경제 안정을 유지하기 위해 사이버 보안 인프라에 많은 투자를 하고 있습니다. 중동 및 아프리카에서는 자원과 전문 지식이 제한되어 있기 때문에 사이버 보안 방어에서 현저한 과제에 직면하고 있습니다. 그러나 국익을 지키고 해외 투자를 불러들이는 사이버 보안의 중요성에 대한 인식은 높아지고 있습니다. 이러한 세계 동향은 복잡하고 진화하는 사이버 보안 위협의 상황을 해결하기 위해 세계에서 협조적인 접근의 필요성을 돋보이게 합니다.
사이버 보안의 주요 프로그램
Accenture Federal Services는 미국 해군 해상부대가 SHARKCAGE 환경 내에서 통합 사이버 보안 전략을 시행할 수 있도록 10년간 7억 8, 900만 달러의 계약을 획득했습니다. 이 계약에서 Accenture Federal Services는 해상 지휘, 제어, 통신, 컴퓨터, 정보 프로그램 관리자, 전쟁 사이버 보안 담당 프로그램, 이그제큐티브 오피스를 지원하기 위해 육상, 함재 SHARKCAGE 시스템을 제공합니다. 이 시스템은 상용 및 기성품 하드웨어 및 소프트웨어로 구성되며 InformationTechnology-21, ONENet, 해군/해병대 인트라넷과 같은 해군 네트워크에 방어적인 사이버 공간 운영 분석을 제공하도록 설계되었습니다. 이 회사의 책임에는 이러한 시스템의 시스템 설계, 아키텍처, 테스트, 생산, 납품, 설치 지원, 통합 물류 지원이 포함됩니다.
CACI International Inc.는 미국 육군 전투 능력 개발 사령부(CCDC)의 C5ISR(지휘, 제어, 컴퓨터, 통신, 사이버, 첩보, 감시, 정찰) 센터에서 5년간의 단발 태스크 오더를 획득했다고 발표했습니다. 이 작업 순서는 최대 4억 6, 500만 달러 이상으로 암호화의 현대화, 정보 보안, 전술 네트워크 보호 연구 개발에 중점을 둡니다. GSA Alliant II 계약에 따라 육군 사이버 보안 및 정보 부서(CSIA)에서 수여 한 CACI는 C5ISR 시스템의 사이버 방어 능력을 강화하기위한 전문 지식을 제공합니다.
목차
시장 정의
시장 내역
- 컴포넌트별
- 지역별
- 보안유형별
시장 전망(향후 10년간)
시장 기술
시장 예측
지역별 동향과 예측
- 북미
- 촉진, 억제요인, 과제
- PEST 분석
- 시장 예측과 시나리오 분석
- 주요 기업
- 공급자 계층의 상황
- 기업 벤치마킹
- 유럽
- 중동
- 아시아태평양
- 남미
국가별 분석
- 미국
- 방어 계획
- 최신 동향
- 특허
- 이 시장의 현재 기술 성숙 수준
- 시장 예측과 시나리오 분석
- 캐나다
- 이탈리아
- 프랑스
- 독일
- 네덜란드
- 벨기에
- 스페인
- 스웨덴
- 그리스
- 호주
- 남아프리카
- 인도
- 중국
- 러시아
- 한국
- 일본
- 말레이시아
- 싱가포르
- 브라질
시장 기회 매트릭스
전문가의 견해
결론
Aviation and Defense Market Reports 정보
BJH 24.09.24The Global Cybersecurity Market is estimated at USD 175 billion in 2024, projected to grow to USD 300 billion by 2034 at a Compound Annual Growth Rate (CAGR) of 5.54% over the forecast period 2024-2034

Introduction to Global Cybersecurity Market:
Global Cybersecurity Defense refers to the collective efforts of nations, organizations, and individuals to protect digital assets, critical infrastructure, and sensitive information from cyber threats. In an increasingly interconnected world, cybersecurity has become a top priority for governments and businesses alike. Cybersecurity is essential for safeguarding against malicious attacks by hackers, spammers, and cybercriminals who aim to access, change, or destroy sensitive information; extort money; or disrupt normal operations. These threats have become more sophisticated and widespread, with cybercrime. As a result, governments and organizations are investing heavily in advanced cybersecurity technologies and strategies to protect their digital assets and maintain the trust of their stakeholders.
Technology Impact in Global Cybersecurity Market:
Technological advancements have had a significant impact on the global cybersecurity landscape, both in terms of the threats and the defenses. The rapid spread of generative AI and other new technologies can easily be used by cyberattackers, posing a serious threat to businesses and public life[3]. Deepfakes and sophisticated phishing campaigns have the potential to become weaponized to disrupt democratic processes. At the same time, emerging technologies are being leveraged to enhance cybersecurity defenses. Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing the industry by analyzing vast amounts of data, learning from patterns, and making predictions about potential threats[5]. Behavioral biometrics uses ML algorithms to analyze user behavior and detect potential threats, such as hackers who have gained unauthorized access to an account. Several key technologies are significantly impacting global cybersecurity defense. Zero Trust Architecture is at the forefront, requiring rigorous identity verification for every person or device attempting to access a network or resource, operating on the principle that no one is trusted by default. Blockchain technology is also transforming cybersecurity by offering a decentralized database for securely storing sensitive information, which greatly complicates unauthorized access for hackers. Quantum Computing, though still in its early stages, holds the potential to revolutionize cybersecurity by enabling more secure encryption methods. Additionally, Cloud Security technologies, such as multi-factor authentication, encryption, and access controls, are crucial for safeguarding data in cloud environments. As these technologies advance, they will increasingly shape the global cybersecurity defense landscape.
Key Drivers in Global Cybersecurity Market:
Several key factors are driving the growth of the global cybersecurity defense market. Increasing cyber threats are a primary driver, with the frequency and complexity of cyberattacks rising globally in recent years. These incidents can lead to significant financial losses, reputational damage, and legal liabilities. Another crucial factor is regulatory compliance; governments and industry bodies are enforcing stricter regulations on data privacy and security, such as the General Data Protection Regulation (GDPR) in the European Union. Organizations must adhere to these regulations to avoid severe fines and legal consequences. The rapid digitalization and proliferation of the Internet of Things (IoT) are also expanding the attack surface for cybercriminals, increasing the risk of vulnerabilities and data breaches. Geopolitical tensions further impact the cybersecurity landscape, as conflicts and instability can shift risk dynamics quickly, with cyberattacks often targeting critical infrastructure and supply chains as tools of warfare. Additionally, growing awareness among individuals, organizations, and governments about the importance of cybersecurity is enhancing efforts to protect digital assets and maintain trust in the digital ecosystem. These drivers are expected to continue propelling the growth of the global cybersecurity defense market in the coming years.
Regional Trends in Global Cybersecurity Market:
The global cybersecurity defense market displays distinct regional trends, shaped by varying threat landscapes, regulatory environments, and investment priorities. North America leads the market, driven by technological advancements, a high demand for advanced connectivity solutions, and substantial investments in defense and aerospace sectors. The U.S. and Canada benefit from well-established regulatory frameworks and support for space and satellite initiatives, bolstering the region's market dominance. In Europe, strict data privacy regulations, such as the General Data Protection Regulation (GDPR), are fueling the adoption of advanced cybersecurity technologies and strategies. The European Union is also investing heavily in research and development to stay ahead of emerging threats. The Asia-Pacific region is experiencing rapid growth in the cybersecurity defense market, driven by the increasing adoption of digital technologies and a heightened awareness of cyber threats. Countries like China and India are significantly investing in cybersecurity infrastructure to protect their critical assets and maintain economic stability. In the Middle East and Africa, the region faces notable challenges in cybersecurity defense due to limited resources and expertise. However, there is growing recognition of the importance of cybersecurity for protecting national interests and attracting foreign investment. These regional trends underscore the need for a global, coordinated approach to address the complex and evolving cybersecurity threat landscape.
Key Cybersecurity market programs:
Accenture Federal Services has secured a ten-year, $789 million contract to assist U.S. Navy maritime forces in executing unified cybersecurity operations within the SHARKCAGE environment, the Navy's integrated system designed to safeguard a continuous, unified security perimeter. Under this contract, Accenture Federal Services will support the Navy's Program Executive Office for Command, Control, Communications, Computers and Intelligence Program Manager, Warfare Cybersecurity, by providing both shore-based and shipborne SHARKCAGE systems. These systems, comprising commercial and off-the-shelf hardware and software, are designed to deliver defensive cyberspace operations analytics across Navy networks such as InformationTechnology-21, ONENet, and the Navy/Marine Corps Intranet. The company's responsibilities will include system design, architecture, testing, production, delivery, installation support, and integrated logistics support for these systems.
CACI International Inc. announced that it has secured a five-year, single-award task order from the U.S. Army Combat Capabilities Development Command's (CCDC) Command, Control, Computers, Communications, Cyber, Intelligence, Surveillance, and Reconnaissance (C5ISR) center. The task order, with a ceiling value of over $465 million, focuses on research and development in cryptographic modernization, information security, and tactical network protection. Awarded by the Army's Cyber Security and Information Division (CSIA) under the GSA Alliant II contract vehicle, CACI will provide specialized expertise to enhance cyber defense capabilities for C5ISR systems.
Table of Contents
Market Definition
Market Segmentation
By Component
By Region
By Security Type
10 Year Market Outlook
The 10-year market outlook would give a detailed overview of changing dynamics, technology adoption overviews and the overall market attractiveness is covered in this chapter.
Market Technologies
This segment covers the top 10 technologies that is expected to impact this market and the possible implications these technologies would have on the overall market.
Global Market Forecast
The 10-year market forecast of this market is covered in detailed across the segments which are mentioned above.
Regional Market Trends & Forecast
The regional market trends, drivers, restraints and Challenges of this market, the Political, Economic, Social and Technology aspects are covered in this segment. The market forecast and scenario analysis across regions are also covered in detailed in this segment. The last part of the regional analysis includes profiling of the key companies, supplier landscape and company benchmarking.
North America
Drivers, Restraints and Challenges
PEST
Market Forecast & Scenario Analysis
Key Companies
Supplier Tier Landscape
Company Benchmarking
Europe
Middle East
APAC
South America
Country Analysis
This chapter deals with the key defense programs in this market, it also covers the latest news and patents which have been filed in this market. Country level 10 year market forecast and scenario analysis are also covered in this chapter.
US
Defense Programs
Latest News
Patents
Current levels of technology maturation in this market
Market Forecast & Scenario Analysis
Canada
Italy
France
Germany
Netherlands
Belgium
Spain
Sweden
Greece
Australia
South Africa
India
China
Russia
South Korea
Japan
Malaysia
Singapore
Brazil
Opportunity Matrix
The opportunity matrix helps the readers understand the high opportunity segments in this market.
Expert Opinions
Hear from our experts their opinion of the possible outlook for this market.
Conclusions
About Aviation and Defense Market Reports



















