
|
시장보고서
상품코드
1674214
보안 오케스트레이션 시장 : 제공별, 최종 이용 산업별, 지역별Security Orchestration Market, By Offering, By End User Industry, By Geography |
||||||
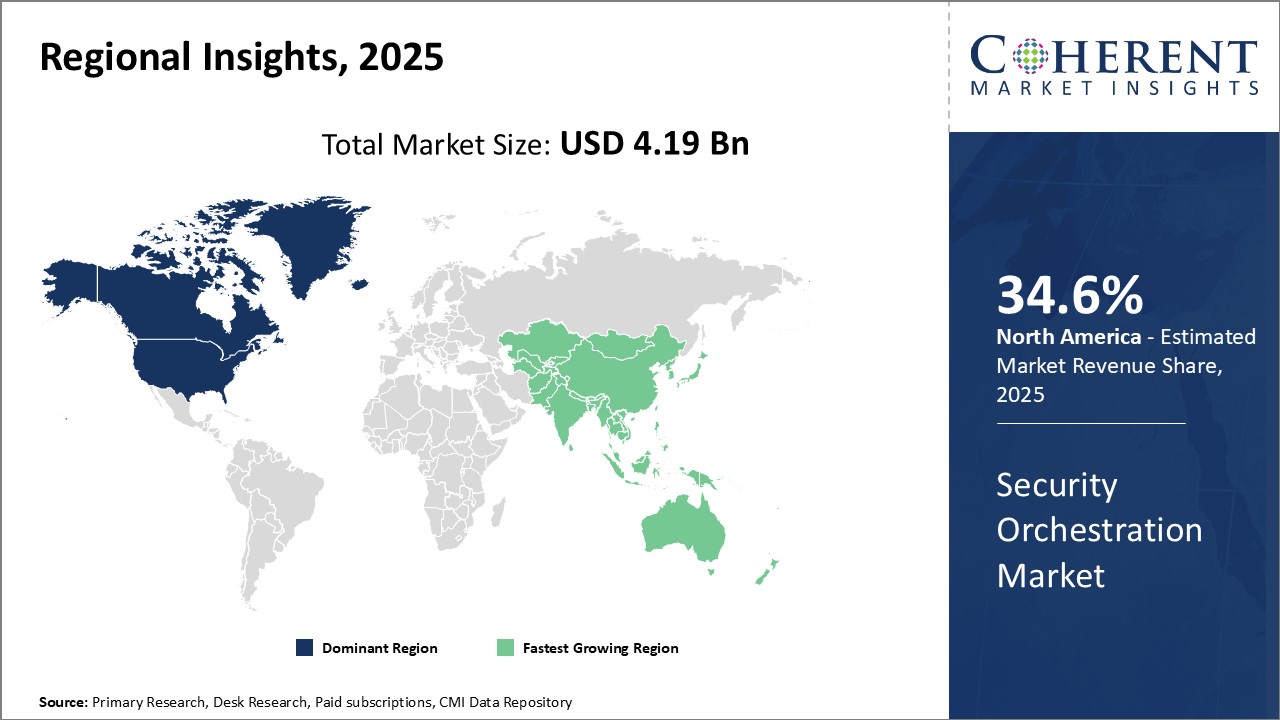
세계 보안 오케스트레이션 시장은 2025년 41억 9,000만 달러로 추정되며, 2032년에는 115억 5,000만 달러에 달할 것으로 예상되며, 2025-2032년 연평균 성장률(CAGR) 15.6%로 성장할 것으로 예상됩니다.
| 보고서 범위 | 보고서 상세 내용 | ||
|---|---|---|---|
| 기준 연도 | 2024년 | 2025년 시장 규모 | 41억 9,000만 달러 |
| 실적 데이터 | 2020-2024년 | 예측 기간 | 2025-2032년 |
| 예측 기간 : 2025-2032년 CAGR | 15.60% | 2032년 가치 예측 | 115억 5,000만 달러 |
보안 오케스트레이션은 IT 보안 솔루션과 기술을 통합하고 다양한 보안 도구에 걸친 대응 조치를 자동화하는 것을 말합니다. 사이버 위협이 점점 더 고도화되고 조직의 디지털 기술 의존도가 높아짐에 따라, 데이터 유출을 방지하고 통합된 대응을 보장하기 위해 중앙 집중식 보안 관리의 필요성이 매우 높아지고 있습니다. 보안 오케스트레이션은 단일 플랫폼에서 이기종 도구를 통합하여 보안 인프라에 대한 가시성을 높이고 복구 프로세스를 자동화할 수 있습니다. 각 산업에서 디지털 전환이 가속화되는 가운데, 최신 하이브리드 IT 환경의 보안 문제를 효과적으로 관리하기 위한 보안 오케스트레이션 솔루션에 대한 수요는 앞으로 더욱 높아질 것으로 보입니다.
시장 역학
세계 보안 오케스트레이션 시장의 성장은 사이버 공격의 빈도와 복잡성 증가, 비즈니스 프로세스의 디지털화, 중앙 집중식 보안 관리에 대한 요구 증가 등의 요인에 의해 주도되고 있습니다. 팬데믹으로 인한 원격 근무의 증가로 사이버 범죄자들의 공격 대상이 더욱 확대되어 보안 사고 대응 능력을 향상시켜야 합니다. 그러나 레거시 보안 시스템 통합에 따른 높은 초기 비용과 어려움은 보안 오케스트레이션 플랫폼의 보급에 걸림돌이 되고 있습니다. 하이브리드 IT 인프라 보안에 대한 수요 증가, IoT 및 운영 기술 등의 부문에서 새로운 기회, AI/ML을 탑재한 차세대 보안 오케스트레이션 솔루션의 가용성 등이 시장 성장을 촉진할 수 있습니다. 벤더들은 시장에서 경쟁 우위를 확보하기 위해 멀티 툴 통합, 자동화, 고급 위협 탐지 기능을 갖춘 확장성과 유연성을 갖춘 제품을 제공하는 데 주력하고 있습니다.
본 조사의 주요 특징
세계의 보안 오케스트레이션 시장을 상세히 분석했으며, 2024년을 기준 연도로 하여 예측 기간(2025-2032년)의 시장 규모와 연평균 성장률(CAGR)에 대해 조사 분석하여 전해드립니다.
또한, 다양한 부문에 걸친 잠재적 수익 기회를 밝히고, 이 시장의 매력적인 투자 제안 매트릭스를 설명합니다.
또한 시장 촉진요인, 억제요인, 기회, 신제품 출시 및 승인, 시장 동향, 지역별 전망, 주요 기업의 경쟁 전략 등에 대한 중요한 인사이트를 제공합니다.
이 보고서는 기업 하이라이트, 제품 포트폴리오, 주요 하이라이트, 재무 성과, 전략 등의 매개 변수를 기반으로 세계 보안 오케스트레이션 시장의 주요 기업을 프로파일링합니다.
조사 대상 주요 기업으로는 Armis, Attivo Networks, Cisco Systems, CrowdStrike, D3 Security, Exabeam, FireEye, Fortinet, IBM, Microsoft, Palo Alto Networks, Rapid7, Splunk, Swimlane, Tines 등이 있습니다.
이 보고서의 인사이트를 통해 마케팅 담당자와 기업 경영진은 향후 제품 출시, 유형화, 시장 확대, 마케팅 전술에 대한 정보에 입각한 의사결정을 내릴 수 있습니다.
세계 보안 오케스트레이션 시장 보고서는 투자자, 공급업체, 제품 제조업체, 유통업체, 신규 진입자, 재무 분석가 등 다양한 이해관계자를 대상으로 합니다.
이해관계자들은 세계 보안 오케스트레이션 시장 분석에 사용되는 다양한 전략 매트릭스를 통해 의사결정을 용이하게 할 수 있습니다.
목차
제1장 조사 목적과 가정
- 조사 목적
- 가정
- 약어
제2장 시장 전망
- 보고서 설명
- 시장 정의와 범위
- 주요 요약
제3장 시장 역학, 규제, 동향 분석
- 시장 역학
- 성장 촉진요인
- 성장 억제요인
- 시장 기회
- 규제 시나리오
- 산업 동향
- 인수합병
- 신시스템의 도입/승인
- COVID-19 팬데믹의 영향
제4장 세계의 보안 오케스트레이션 시장, 제공별, 2020-2032년
- 소개
- 소프트웨어
- 서비스
제5장 세계의 보안 오케스트레이션 시장, 최종 이용 산업별, 2020-2032년
- 소개
- BFSI
- IT·통신
- 정부와 방위
- E-Commerce
- 기타
제6장 세계의 보안 오케스트레이션 시장, 지역별, 2020-2032년
- 소개
- 북미
- 유럽
- 아시아태평양
- 라틴아메리카
- 중동 및 아프리카
제7장 경쟁 구도
- 기업 개요
- Armis
- Attivo Networks
- Cisco Systems, Inc.
- CrowdStrike
- D3 Security
- Exabeam
- FireEye, Inc.
- Fortinet
- IBM Corporation
- Microsoft Corporation
- Palo Alto Networks
- Rapid7
- Splunk
- Swimlane
- Tines
제8장 애널리스트의 추천사항
- Wheel of Fortune
- Coherent Opportunity Map
제9장 참고문헌과 조사 방법
- 참고문헌
- 조사 방법
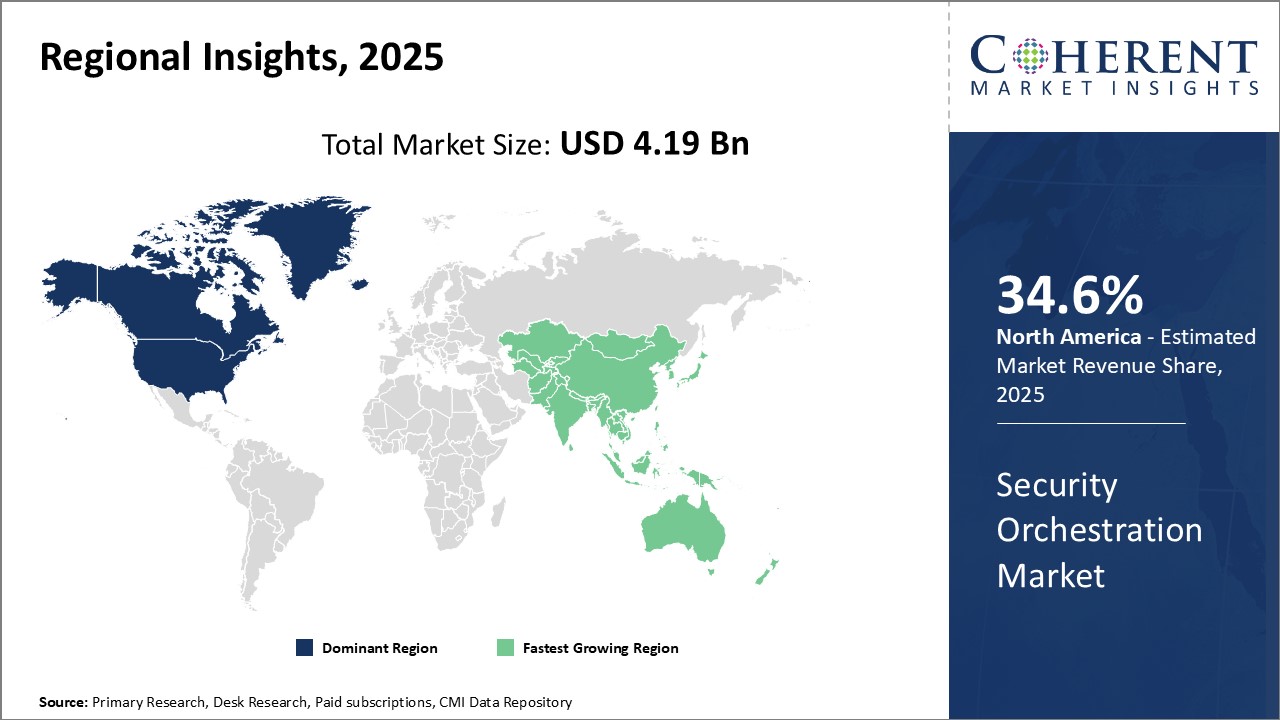
Global Security Orchestration Market is estimated to be valued at USD 4.19 Bn in 2025 and is expected to reach USD 11.55 Bn by 2032, growing at a compound annual growth rate (CAGR) of 15.6% from 2025 to 2032.
| Report Coverage | Report Details | ||
|---|---|---|---|
| Base Year: | 2024 | Market Size in 2025: | USD 4.19 Bn |
| Historical Data for: | 2020 To 2024 | Forecast Period: | 2025 To 2032 |
| Forecast Period 2025 to 2032 CAGR: | 15.60% | 2032 Value Projection: | USD 11.55 Bn |
Security orchestration refers to the integration of IT security solutions and technologies to automate response actions across different security tools. With increasing sophistication of cyber threats and growing dependence of organizations on digital technologies, there has been huge need for centralized security management to prevent data breaches and ensure coordinated response. T Security orchestration allows organizations to gain enhanced visibility over their security infrastructure and automate remediation processes through integration of disparate tools on a single platform. As digital transformation accelerate across industries, there will be huge demand for security orchestration solutions to manage security challenges of modern hybrid IT environments effectively.
Market Dynamics:
Global security orchestration market growth is driven by factors such as growing frequency and complexity of cyber-attacks, increasing digitization of business processes, and rising need for centralized security management. Rising remote working during the pandemic has further expanded the attack surface for cybercriminals, necessitating improved security incident response capabilities. However, high initial costs and difficulties associated with integrating legacy security systems can pose challenges for widespread adoption of security orchestration platforms. Rising demand to secure hybrid IT infrastructures, emerging opportunities in sectors like IOT and operational technology, and availability of AI/ML-powered next-gen security orchestration solutions can drive the market growth. Vendors are focusing on offering scalable and flexible products with multi-tool integration, automation, and advanced threat detection to gain competitive edge in the market.
Key features of the study:
This report provides in-depth analysis of the global security orchestration market, and provides market size (US$ Bn) and compound annual growth rate (CAGR%) for the forecast period (2025-2032), considering 2024 as the base year
It elucidates potential revenue opportunities across different segments and explains attractive investment proposition matrices for this market
This study also provides key insights about market drivers, restraints, opportunities, new product launches or approval, market trends, regional outlook, and competitive strategies adopted by key players
It profiles key players in the global security orchestration market based on the following parameters - company highlights, products portfolio, key highlights, financial performance, and strategies
Key companies covered as a part of this study include Armis, Attivo Networks, Cisco Systems, Inc., CrowdStrike, D3 Security, Exabeam, FireEye, Inc., Fortinet, IBM Corporation, Microsoft Corporation, Palo Alto Networks, Rapid7, Splunk, Swimlane, and Tines
Insights from this report would allow marketers and the management authorities of the companies to make informed decisions regarding their future product launches, type up-gradation, market expansion, and marketing tactics
Global security orchestration market report caters to various stakeholders in this industry including investors, suppliers, product manufacturers, distributors, new entrants, and financial analysts
Stakeholders would have ease in decision-making through various strategy matrices used in analyzing the global security orchestration market
Detailed Segmentation:
- By Offering
- Software
- Services
- By End User Industry
- BFSI
- IT and Telecommunication
- Government and Defense
- E-commerce
- Others
- By Region:
- North America
- Europe
- Asia Pacific
- Latin America
- Middle East & Africa
- Key Players Insights
- Armis
- Attivo Networks
- Cisco Systems, Inc.
- CrowdStrike
- D3 Security
- Exabeam
- FireEye, Inc.
- Fortinet
- IBM Corporation
- Microsoft Corporation
- Palo Alto Networks
- Rapid7
- Splunk
- Swimlane
- Tines
Table of Contents
1. Research Objectives and Assumptions
- Research Objectives
- Assumptions
- Abbreviations
2. Market Purview
- Report Description
- Market Definition and Scope
- Executive Summary
- Market Snippet, By Offering
- Market Snippet, By End User Industry
- Market Snippet, By Region
3. Market Dynamics, Regulations, and Trends Analysis
- Market Dynamics
- Drivers
- Restraints
- Market Opportunities
- Regulatory Scenario
- Industry Trend
- Merger and Acquisitions
- New System Launches/Approvals
- Impact of COVID-19 Pandemic
4. Global Security Orchestration Market, By Offering, 2020-2032, (US$ Bn)
- Introduction
- Market Share Analysis, 2025 and 2032 (%)
- Y-o-Y Growth Analysis, 2021-2032
- Segment Trends
- Software
- Introduction
- Market Size and Forecast, 2020-2032, (US$ Bn)
- Services
- Introduction
- Market Size and Forecast, 2020-2032, (US$ Bn)
5. Global Security Orchestration Market, By End User Industry, 2020-2032, (US$ Bn)
- Introduction
- Market Share Analysis, 2025 and 2032 (%)
- Y-o-Y Growth Analysis, 2021-2032
- Segment Trends
- BFSI
- Introduction
- Market Size and Forecast, 2020-2032, (US$ Bn)
- IT and Telecommunication
- Introduction
- Market Size and Forecast, 2020-2032, (US$ Bn)
- Government and Defense
- Introduction
- Market Size and Forecast, 2020-2032, (US$ Bn)
- E-commerce
- Introduction
- Market Size and Forecast, 2020-2032, (US$ Bn)
- Others
- Introduction
- Market Size and Forecast, 2020-2032, (US$ Bn)
6. Global Security Orchestration Market, By Region, 2020-2032, (US$ Bn)
- Introduction
- Market Share Analysis, By Region, 2025 and 2032 (%)
- North America
- Regional Trends
- Market Size and Forecast, By Offering, 2020-2032, (US$ Bn)
- Market Size and Forecast, By End User Industry, 2020-2032, (US$ Bn)
- Market Size and Forecast, By Country, 2020-2032, (US$ Bn)
- U.S.
- Canada
- Europe
- Regional Trends
- Market Size and Forecast, By Offering, 2020-2032, (US$ Bn)
- Market Size and Forecast, By End User Industry, 2020-2032, (US$ Bn)
- Market Size and Forecast, By Country, 2020-2032, (US$ Bn)
- Germany
- U.K.
- Spain
- France
- Italy
- Russia
- Rest of Europe
- Asia Pacific
- Regional Trends
- Market Size and Forecast, By Offering, 2020-2032, (US$ Bn)
- Market Size and Forecast, By End User Industry, 2020-2032, (US$ Bn)
- Market Size and Forecast, By Country, 2020-2032, (US$ Bn)
- China
- India
- Japan
- ASEAN
- Australia
- South Korea
- Rest of Asia Pacific
- Latin America
- Regional Trends
- Market Size and Forecast, By Offering, 2020-2032, (US$ Bn)
- Market Size and Forecast, By End User Industry, 2020-2032, (US$ Bn)
- Market Size and Forecast, By Country, 2020-2032, (US$ Bn)
- Brazil
- Argentina
- Mexico
- Rest of Latin America
- Middle East & Africa
- Regional Trends
- Market Size and Forecast, By Offering, 2020-2032, (US$ Bn)
- Market Size and Forecast, By End User Industry, 2020-2032, (US$ Bn)
- Market Size and Forecast, By Country, 2020-2032, (US$ Bn)
- South Africa
- Israel
- GCC Countries
- Rest of the Middle East & Africa
7. Competitive Landscape
- Company Profiles
- Armis
- Company Overview
- Product Portfolio
- Financial Performance
- Key Strategies
- Recent Developments/Updates
- Attivo Networks
- Company Overview
- Product Portfolio
- Financial Performance
- Key Strategies
- Recent Developments/Updates
- Cisco Systems, Inc.
- Company Overview
- Product Portfolio
- Financial Performance
- Key Strategies
- Recent Developments/Updates
- CrowdStrike
- Company Overview
- Product Portfolio
- Financial Performance
- Key Strategies
- Recent Developments/Updates
- D3 Security
- Company Overview
- Product Portfolio
- Financial Performance
- Key Strategies
- Recent Developments/Updates
- Exabeam
- Company Overview
- Product Portfolio
- Financial Performance
- Key Strategies
- Recent Developments/Updates
- FireEye, Inc.
- Company Overview
- Product Portfolio
- Financial Performance
- Key Strategies
- Recent Developments/Updates
- Fortinet
- Company Overview
- Product Portfolio
- Financial Performance
- Key Strategies
- Recent Developments/Updates
- IBM Corporation
- Company Overview
- Product Portfolio
- Financial Performance
- Key Strategies
- Recent Developments/Updates
- Microsoft Corporation
- Company Overview
- Product Portfolio
- Financial Performance
- Key Strategies
- Recent Developments/Updates
- Palo Alto Networks
- Company Overview
- Product Portfolio
- Financial Performance
- Key Strategies
- Recent Developments/Updates
- Rapid7
- Company Overview
- Product Portfolio
- Financial Performance
- Key Strategies
- Recent Developments/Updates
- Splunk
- Company Overview
- Product Portfolio
- Financial Performance
- Key Strategies
- Recent Developments/Updates
- Swimlane
- Company Overview
- Product Portfolio
- Financial Performance
- Key Strategies
- Recent Developments/Updates
- Tines
- Company Overview
- Product Portfolio
- Financial Performance
- Key Strategies
- Recent Developments/Updates
- Armis
8. Analyst Recommendation
- Wheel of Fortune
- Analyst View
- Coherent Opportunity Map
9. Reference and Research Methodology
- References
- Research Methodology
- About us and Sales Contact



















