
|
시장보고서
상품코드
1881283
DDOS 방어 및 완화 보안 시장 : 제공 제품별, 솔루션 유형별, 응용 영역별, 전개 모드별, 조직 규모별, 업계별, 지역별, 예측(-2030년)DDoS Protection & Mitigation Security Market by Solution Type, Offering, Application Area - Global Forecast to 2030 |
||||||
DDOS 방어 및 완화 보안 시장 규모는 예측 기간 동안 CAGR 12.3%로 성장하고 2025년 58억 달러, 2030년까지 103억 9,000만 달러에 이를 것으로 예측됩니다.
| 조사 범위 | |
|---|---|
| 조사 기간 | 2019-2030년 |
| 기준 연도 | 2024년 |
| 예측 기간 | 2025-2030년 |
| 대상 단위 | 가치(100만/10억 달러) |
| 부문 | 제공 제품별, 솔루션 유형별, 응용 영역별, 전개 모드별, 조직 규모별, 업계별, 지역별 |
| 대상 지역 | 북미, 유럽, 아시아태평양, 중동, 아프리카, 라틴아메리카 |
BFSI, 의료, IT·ITES 등 시장에서의 기술의 급속한 보급이 성장 기회를 창출하고 있습니다. DDoS 대책 솔루션에 인공지능(AI)과 머신러닝 기능을 통합함으로써 위협 감지 능력의 향상이 기대됩니다. Managed Security Services는 특히 중소기업 수요가 높으며 공급자에게 새로운 성장 분야가 되었습니다. 기술 혁신이 진행되고 있는 다른 분야로는 협력 방어 시스템과 클라우드 보안 시스템이 있으며, 업계에 관계없이 비즈니스 활동을 보호하기 위한 맞춤형 탄력적인 DDoS 보호에 대한 수요가 높아지고 있습니다.

네트워크 트래픽 분석기 부문은 예측 기간 동안 Global Forecast to 2030 82자 DDOS 방어 및 완화 보안 시장에서 최대 시장 규모를 유지할 것으로 예측됩니다. 네트워크 분석기는 흐름 모니터링, 비정상 감지 및 행동 분석과 같은 고급 기술을 사용하여 트래픽의 비정상적인 패턴을 식별하는 데 중요한 역할을합니다. 성공적인 네트워크 활동의 기준값을 설정하여 잠재적인 DDoS 공격을 시사할 수 있는 편차를 감지하고 위협이 에스컬레이션되어 중요한 업무에 영향을 미치기 전에 IT 팀이 즉시 대응할 수 있도록 지원합니다. 또한 최신 네트워크 분석기는 네트워크 동작의 가시성을 높이고 합법적 인 트래픽을 정밀하게 필터링하고 악의적 인 요청을 차단하는 효과적인 속도 제한을 가능하게합니다. 이러한 도구는 볼륨 유형 및 용도 계층 DDoS 공격과 관련된 위험을 줄이면서 서비스 가용성을 유지하고 네트워크 성능을 최적화하는 데 필수적입니다. 조직이 실시간 모니터링과 데이터 중심의 위협 감지를 선호하는 동안, 고성능 네트워크 트래픽 분석기의 도입은 지속적으로 견고하고 시장의 우위를 강화할 것으로 예측됩니다.
봇넷 감지 및 대책 부문은 대규모 봇넷 네트워크를 기반으로 하는 DDoS 공격 증가를 배경으로 예측 기간 동안 가장 빠른 성장을 기록할 것으로 예측됩니다. 이러한 솔루션은 고급 분석 기술, 인공지능 및 머신러닝을 활용하여 네트워크 트래픽을 조작하거나 시스템을 오작동하는 악성 봇 활동을 식별하고 대책합니다. TCP나 UDP 등 여러 프로토콜에 걸친 네트워크 데이터 패킷을 지속적으로 감시함으로써 봇넷 감지 시스템은 감염 장치와 관련된 이상이나 조직적인 공격 패턴을 감지할 수 있습니다. 이러한 기능을 통해 조직은 봇넷이 DDoS 공격에 악용되기 전에 확인할 수 있어 조기 개입과 피해 경감을 실현합니다. 또한 자동 분석 도구가 합법적인 트래픽과 악의적인 트래픽을 실시간으로 분류하므로 감지 정확도가 향상되고 잘못된 감지가 줄어 듭니다. 봇넷의 위협이 확인되면 완화 시스템은 즉시 악성 트래픽을 격리 및 무력화하는 대책을 시행합니다. 봇 구동 공격의 고도화와 IoT 디바이스의 보급 확대로 봇넷의 감지와 완화는 현대의 사이버 보안 기반에서 필수적인 요소가 되어 이 시장 부문의 급속한 성장을 이끌어 가고 있습니다.
아시아태평양의 DDOS 방어 및 완화 보안 시장은 급속한 디지털 변환, 클라우드 도입 증가 및 지역 전반의 연결 장치 급증을 배경으로 예측 기간 동안 가장 높은 성장률을 나타낼 것으로 추정됩니다. 중국, 인도, 일본, 호주 등의 국가들이 이러한 성장을 이끌고 있으며, IoT 기술의 광범위한 도입과 모바일 중심의 비즈니스 에코시스템이 DDoS 공격에 대한 취약성을 높이고 있다는 배경이 있습니다. 또한 이 지역에서는 기업간에 특히 중소기업(SME)을 중심으로 예방적 사이버 방어의 중요성에 대한 인식이 높아지고 있으며, 확장 가능하고 비용 효율적인 DDoS 보호 솔루션에 대한 투자가 촉진되고 있습니다. 인공지능(AI)과 머신러닝을 DDoS 대책 시스템에 통합함으로써 실시간 위협 감지와 자동화된 완화가 가능해져 전체적인 효율성이 향상되고 있습니다. 클라우드 인프라의 대폭적인 확대, 데이터 트래픽 증가, 정부 주도의 디지털화 추진책도 시장의 성장에 기여하고 있습니다. 복잡한 사이버 위협과 각국의 사이버 보안 성숙도의 차이와 같은 과제는 있는 것, 중요한 디지털 자산의 보호와 사업 연속성 확보에 주력이 강해지고 있기 때문에 아시아태평양은 대폭적인 확대가 전망되고 있습니다.
본 보고서에서는 세계 DDOS 방어 및 완화 보안 시장에 대해 조사했으며, 제공 제품별, 솔루션 유형별, 응용 영역별, 전개 모드별, 조직 규모별, 업계별, 지역별 동향 및 시장 진출기업 프로파일 등을 정리했습니다.
자주 묻는 질문
목차
제1장 서론
제2장 주요 요약
제3장 중요 인사이트
제4장 시장 개요
- 소개
- 시장 역학
- 언멧 요구와 공백
- 연계 시장 및 교차 산업 기회
- Tier 1/2/3 기업의 전략적 움직임
제5장 업계 동향
- Porter's Five Forces 분석
- 거시경제지표
- 공급망 분석
- 생태계 분석
- 가격 분석
- 주요 회의 및 이벤트
- 고객사업에 영향을 주는 동향/혼란
- 투자 및 자금조달 시나리오
- 사례 연구 분석
- DDoS 공격 방지 기술
- 2025년 미국 관세의 영향-DDOS 방어 및 완화 보안 시장
제6장 기술의 진보, AI에 의한 영향, 특허, 혁신, 장래의 응용
- 주요 신기술
- 보완적 기술
- 인접 기술
- DDOS 방어 및 완화 보안 시장 전망
- 특허 분석
- AI/생성형 AI가 DDOS 방어 및 완화 보안 시장에 미치는 영향
제7장 규제 상황
- 규제 상황
- 규제기관, 정부기관, 기타 조직
제8장 고객정세와 구매행동
- 의사결정 프로세스
- 구매자의 이해관계자와 구매평가기준
- 구매 과정에서 주요 이해관계자
- 구입 기준
- 채택 장벽과 내부 과제
제9장 DDOS 방어 및 완화 보안 시장(제공 제품별)
- 소개
- 하드웨어 솔루션
- 소프트웨어 솔루션
- 서비스
제10장 DDOS 방어 및 완화 보안 시장(솔루션 유형별)
- 소개
- 네트워크 트래픽 분석기
- 위협 경감 시스템
- 봇넷 검출 및 관리
- 기타
제11장 DDOS 방어 및 완화 보안 시장(응용 영역별)
- 소개
- 네트워크 보안
- 용도 보안
- 클라우드 보안
- 엔드포인트 보안
제12장 DDOS 방어 및 완화 보안 시장(전개 모드별)
- 소개
- On-Premise
- 클라우드
제13장 DDOS 방어 및 완화 보안 시장(조직 규모별)
- 소개
- 대기업
- 중소기업
제14장 DDOS 방어 및 완화 보안 시장(업계별)
- 소개
- 정부 및 방위
- 은행/금융서비스/보험
- 제조
- 에너지 및 유틸리티
- IT/ITES
- 통신
- 건강 관리
- 교육
- 소매
- 기타
제15장 DDOS 방어 및 완화 보안 시장(지역별)
- 소개
- 북미
- 북미 : 거시경제 전망
- 미국
- 캐나다
- 유럽
- 유럽 : 거시경제 전망
- 영국
- 독일
- 기타
- 아시아태평양
- 아시아태평양 : 거시경제 전망
- 중국
- 일본
- 인도
- 기타
- 중동 및 아프리카
- 중동 및 아프리카 : 거시경제 전망
- 사우디아라비아
- 아랍에미리트(UAE)
- 남아프리카
- 기타
- 라틴아메리카
- 라틴아메리카 : 거시경제 전망
- 브라질
- 멕시코
- 기타
제16장 경쟁 구도
- 소개
- 주요 참가 기업의 전략/강점, 2022년-2025년
- 수익 분석, 2020년-2024년
- 시장 점유율 분석, 2024년
- 기업평가 매트릭스 : 주요 진입기업, 2024년
- 기업평가 매트릭스 : 스타트업/중소기업, 2024년
- 경쟁 시나리오
- 브랜드/제품 비교
- 기업평가와 재무지표, 2025년
제17장 기업 프로파일
- 주요 진출기업
- NETSCOUT
- AKAMAI TECHNOLOGIES
- RADWARE
- CLOUDFLARE
- FORTINET
- HUAWEI
- LINK11
- IMPERVA(A THALES COMPANY)
- BT
- A10 NETWORKS
- 기타 기업
- FASTLY
- F5
- CORERO
- ALLOT
- STRATACORE
- SUCURI
- NSFOCUS
- LUMEN TECHNOLOGIES
- 중소기업/스타트업
- STACKPATH
- SECEON
- HALTDOS
- DDOS-GUARD
- INDUSFACE
- ACTIVEREACH
- MLYTICS
- NEXUSGUARD
- RIOREY
- PHOENIXNAP
- COMODO SECURITY SOLUTIONS
제18장 조사 방법
제19장 인접 시장과 관련 시장
제20장 부록
SHW 25.12.11The DDoS protection & mitigation security market is estimated to grow from USD 5.80 billion in 2025 to USD 10.39 billion by 2030 at a compound annual growth rate (CAGR) of 12.3% during the forecast period.
| Scope of the Report | |
|---|---|
| Years Considered for the Study | 2019-2030 |
| Base Year | 2024 |
| Forecast Period | 2025-2030 |
| Units Considered | Value (USD Million/Billion) |
| Segments | By Offering , Solution Type, Application Area, Deployment Mode, Organization Size, Vertical |
| Regions covered | North America, Europe, Asia Pacific, Middle East & Africa, Latin America |
The rapid adoption of technologies across markets such as BFSI, healthcare, and IT & ITeS creates growth opportunities. Incorporating artificial intelligence and machine learning capabilities into DDoS protection solutions promises to improve threat detection. Managed security services are in demand, especially by small and medium enterprises, which present new growth frontiers for providers. Other areas where technological innovations are rising include cooperative defense systems and cloud security systems, with an increasing demand for tailored and elastic DDoS protection to safeguard business activities across industries.
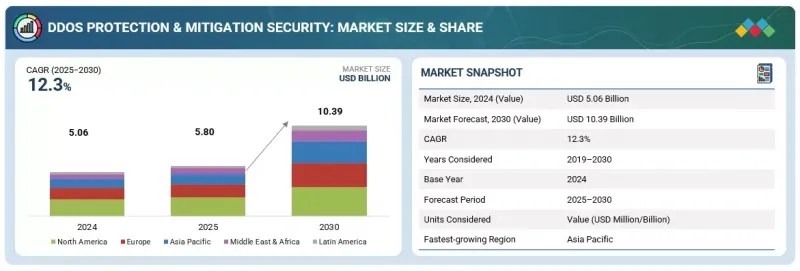
"By solution type, the network traffic analyzers segment is estimated to account for the largest market size during the forecast period."
The network traffic analyzers segment is anticipated to hold the largest market size in the DDoS protection and mitigation security market during the forecast period. Network analyzers play a crucial role in identifying abnormal patterns in traffic by using advanced techniques such as flow monitoring, anomaly detection, and behavioral analytics. By establishing a baseline for normal network activity, these tools can detect deviations that may indicate potential DDoS attacks, allowing IT teams to take immediate action before the threat escalates and impacts critical business operations. Moreover, modern network analyzers enhance visibility into network behavior, enabling precise filtering of legitimate traffic and effective rate limiting to block malicious requests. These tools are integral to maintaining service availability and optimizing network performance while mitigating risks associated with volumetric and application-layer DDoS attacks. As organizations continue to prioritize real-time monitoring and data-driven threat detection, the adoption of high-performance network traffic analyzers is expected to remain strong, reinforcing their dominance in the market.
"By solution type, the botnet detection & mitigation segment is estimated to register the fastest growth rate during the forecast period."
The botnet detection & mitigation segment is projected to record the fastest growth during the forecast period, driven by the rising number of DDoS attacks originating from large-scale botnet networks. These solutions leverage advanced analytics, artificial intelligence, and machine learning to identify and mitigate malicious bot activities that manipulate network traffic or overwhelm systems. By continuously monitoring network data packets across multiple protocols such as TCP and UDP, botnet detection systems can spot anomalies linked to infected devices or coordinated attack patterns. Such capabilities allow organizations to identify botnets before they are weaponized for DDoS assaults, ensuring early intervention and reduced damage. In addition, automated analysis tools categorize legitimate and illegitimate traffic in real time, improving detection accuracy and reducing false positives. Once a botnet threat is identified, mitigation systems immediately deploy countermeasures to isolate and neutralize the malicious traffic. The growing sophistication of bot-driven attacks and the expanding use of IoT devices make botnet detection and mitigation an essential part of modern cybersecurity infrastructure, driving rapid growth in this market segment.
"By region, Asia Pacific is projected to record the highest growth rate during the forecast period."
The Asia Pacific DDoS protection & mitigation security market is estimated to witness the highest growth rate during the forecast period, fueled by rapid digital transformation, increasing cloud adoption, and the surge in connected devices across the region. Countries such as China, India, Japan, and Australia are leading this growth, supported by the widespread deployment of Internet of Things (IoT) technologies and mobile-driven business ecosystems that heighten vulnerability to DDoS attacks. The region is also witnessing growing awareness among enterprises regarding the importance of proactive cyber defense, prompting investments in scalable, cost-effective DDoS protection solutions, particularly among small and medium-sized enterprises (SMEs). The integration of artificial intelligence and machine learning into DDoS protection systems has enabled real-time threat detection and automated mitigation, improving overall efficiency. The substantial expansion of cloud infrastructure, rising data traffic, and government-led digital initiatives further contribute to the market's growth. Despite challenges such as complex cyber threats and varying levels of cybersecurity maturity across countries, the Asia Pacific region is poised for significant expansion due to its increasing focus on protecting critical digital assets and ensuring business continuity.
In-depth interviews have been conducted with chief executive officers (CEOs), Directors, and other executives from various key organizations operating in the DDoS protection & mitigation security market.
- By Company Type: Tier 1 - 70%, Tier 2 - 20%, and Tier 3 - 10%
- By Designation: Directors - 73%, Managers - 18%, and Others - 9%
- By Region: North America - 30%, Europe - 25%, Asia Pacific - 35%, RoW - 10%
The major players in the DDoS protection & mitigation security market include NetScout (US), Akamai (US), Radware (Israel), Huawei (China), Fortinet (US), Imperva (US), F5 (US), Cloudflare (US), BT (UK), and A10 Networks (US). These players have adopted various growth strategies, such as partnerships, agreements and collaborations, new product launches, enhancements, and acquisitions, to expand their DDoS protection & mitigation security market footprint.
Research Coverage
The market study covers the DDoS protection & mitigation security market size across different segments. It aims to estimate the market size and the growth potential across various segments, including offering (with hardware solutions, software solutions, services), solution type, application area, deployment mode, organization size, vertical, and region. The study includes an in-depth competitive analysis of the leading market players, their company profiles, key observations related to product and business offerings, recent developments, and market strategies.
Key Benefits of Buying the Report
The report will help market leaders and new entrants with information on the closest approximations of the global DDoS protection and mitigation security market's revenue numbers and subsegments. This report will help stakeholders understand the competitive landscape and gain more insights to better position their businesses and plan suitable go-to-market strategies. Moreover, the report will provide insights for stakeholders to understand the market's pulse and provide them with information on key market drivers, restraints, challenges, and opportunities.
The report provides insights into the following pointers:
Analysis of key drivers (rise in multi-vector DDoS attacks, DDoS attacks during holidays, ease of availability of DDoS-for-hire services, high demand for cloud-based and hybrid DDoS protection and mitigation security solutions), restraints (budget constraints among SMEs, easy availability of free and pirated DDoS protection and mitigation security solutions), opportunities (increase in the number of DDoS threats across IoT ecosystem, need for DDoS defense solutions for 5G ecosystem, highly regulated verticals and gaming sector to create attractive opportunities for DDoS vendors, rising DDoS threats on cryptocurrency exchange entities), and challenges (sweep period of attacks, large-scale traffic defense with zero latency, and SSL encrypted attacks in DDoS area, dearth of security skills among security professionals and lack of pre-planning among enterprises, DDoS-for-hire services that are easy to find and created for minimum charges).
1. Product Development/Innovation: Detailed insights on upcoming technologies, research & development activities, and new product & service launches in the DDoS protection & mitigation security market.
2. Market Development: The report provides comprehensive information about lucrative markets and analyzes the DDoS protection & mitigation security market across various regions.
3. Market Diversification: Exhaustive information about new products & services, untapped geographies, recent developments, and investments in the DDoS protection & mitigation security market.
4. Competitive Assessment: In-depth assessment of market shares, growth strategies and service offerings of leading include NetScout (US), Akamai (US), Radware (Israel), Huawei (China), Fortinet (US), Imperva (US), F5 (US), Cloudflare (US), BT (UK), A10 Networks (US), Link11 (Germany), Fastly (US), Corero (UK), AIIoT (Israel), Stratacore (US), Sucuri (US), NSFOCUS (China), Lumen Technologies (US), StackPath (US), Seceon (US), Haltdos (India), DDoS-Guard (Russia), Indusface (India), activereach (US), Mlytics (Singapore), Nexusguard (Singapore), RioRey (US), and PheonixNAP (US), and Comodo Security Solutions (US).
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 STUDY OBJECTIVES
- 1.2 MARKET DEFINITION
- 1.3 STUDY SCOPE
- 1.3.1 MARKET SEGMENTATION AND REGIONS COVERED
- 1.3.2 INCLUSIONS & EXCLUSIONS
- 1.4 YEARS CONSIDERED
- 1.5 CURRENCY CONSIDERED
- 1.6 STAKEHOLDERS
- 1.7 SUMMARY OF CHANGES
2 EXECUTIVE SUMMARY
- 2.1 KEY INSIGHTS AND MARKET HIGHLIGHTS
- 2.2 KEY MARKET PARTICIPANTS: MAPPING OF STRATEGIC DEVELOPMENTS
- 2.3 DISRUPTIONS SHAPING MARKET
- 2.4 HIGH GROWTH SEGMENTS
- 2.5 SNAPSHOT: GLOBAL MARKET SIZE, GROWTH RATE, AND FORECAST
3 PREMIUM INSIGHTS
- 3.1 ATTRACTIVE OPPORTUNITIES FOR PLAYERS IN DDOS PROTECTION & MITIGATION SECURITY MARKET
- 3.2 DDOS PROTECTION & MITIGATION SECURITY MARKET, BY OFFERING AND ORGANIZATION SIZE
- 3.3 DDOS PROTECTION & MITIGATION SECURITY MARKET, BY APPLICATION AREA
- 3.4 DDOS PROTECTION & MITIGATION SECURITY MARKET, BY VERTICAL
4 MARKET OVERVIEW
- 4.1 INTRODUCTION
- 4.2 MARKET DYNAMICS
- 4.2.1 DRIVERS
- 4.2.1.1 Rising frequency and complexity of DDoS attacks
- 4.2.1.2 Growing internet penetration and connectivity
- 4.2.2 RESTRAINTS
- 4.2.2.1 Limited integration across multi-vendor environments
- 4.2.2.2 Regulatory and data sovereignty constraints
- 4.2.3 OPPORTUNITIES
- 4.2.3.1 AI-driven predictive mitigation and automated threat correlation
- 4.2.3.2 Growing partnerships between ISPs, cloud providers, and security vendors
- 4.2.4 CHALLENGES
- 4.2.4.1 Lack of skilled cybersecurity professionals
- 4.2.4.2 Cost and complexity of solutions
- 4.2.1 DRIVERS
- 4.3 UNMET NEEDS AND WHITE SPACES
- 4.4 INTERCONNECTED MARKETS AND CROSS-SECTOR OPPORTUNITIES
- 4.5 STRATEGIC MOVES BY TIER-1/2/3 PLAYERS
5 INDUSTRY TRENDS
- 5.1 PORTER'S FIVE FORCES ANALYSIS
- 5.1.1 THREAT OF NEW ENTRANTS
- 5.1.2 THREAT OF SUBSTITUTES
- 5.1.3 BARGAINING POWER OF SUPPLIERS
- 5.1.4 BARGAINING POWER OF BUYERS
- 5.1.5 INTENSITY OF COMPETITIVE RIVALRY
- 5.2 MACROECONOMICS INDICATORS
- 5.2.1 INTRODUCTION
- 5.2.2 GDP TRENDS AND FORECAST
- 5.2.3 TRENDS IN GLOBAL DDOS PROTECTION & MITIGATION SECURITY INDUSTRY
- 5.3 SUPPLY CHAIN ANALYSIS
- 5.4 ECOSYSTEM ANALYSIS
- 5.5 PRICING ANALYSIS
- 5.5.1 AVERAGE SELLING PRICE TREND OF KEY PLAYERS, BY OFFERING, 2024
- 5.5.2 INDICATIVE PRICING ANALYSIS OF DDOS PROTECTION AND MITIGATION SECURITY, BY OFFERING, 2024
- 5.6 KEY CONFERENCES AND EVENTS
- 5.7 TRENDS/DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- 5.8 INVESTMENT AND FUNDING SCENARIO
- 5.9 CASE STUDY ANALYSIS
- 5.9.1 XTEL COMMUNICATIONS CHOSE NETSCOUT TO IMPROVE VISIBILITY INTO NETWORK TRAFFIC
- 5.9.2 PENTELEDATA SELECTED RADWARE'S AMS FOR TECHNICAL INTEGRATION WITH KENTIK TECHNOLOGIES
- 5.9.3 CNI CHOSE CORERO TO PROTECT ITS CUSTOMERS FROM DDOS ATTACKS
- 5.10 DDOS PREVENTION TECHNIQUES
- 5.11 IMPACT OF 2025 US TARIFF - DDOS PROTECTION AND MITIGATION SECURITY MARKET
- 5.11.1 INTRODUCTION
- 5.11.2 KEY TARIFF RATES
- 5.11.3 PRICE IMPACT ANALYSIS
- 5.11.4 IMPACT ON COUNTRY/REGION
- 5.11.4.1 North America
- 5.11.4.2 Europe
- 5.11.4.3 Asia Pacific
- 5.11.5 IMPACT ON END-USE INDUSTRIES
6 TECHNOLOGICAL ADVANCEMENTS, AI-DRIVEN IMPACT, PATENTS, INNOVATIONS, AND FUTURE APPLICATIONS
- 6.1 KEY EMERGING TECHNOLOGIES
- 6.1.1 TRAFFIC FILTERING
- 6.1.2 RATE LIMITING
- 6.1.3 WEB APPLICATION FIREWALL (WAF)
- 6.2 COMPLEMENTARY TECHNOLOGIES
- 6.2.1 ARTIFICIAL INTELLIGENCE (AI)
- 6.2.2 MACHINE LEARNING (ML)
- 6.3 ADJACENT TECHNOLOGIES
- 6.3.1 LOAD BALANCERS
- 6.3.2 CONTENT DELIVERY NETWORKS (CDNS)
- 6.4 FUTURE LANDSCAPE OF DDOS PROTECTION AND MITIGATION SECURITY MARKET
- 6.4.1 DDOS PROTECTION AND MITIGATION SECURITY TECHNOLOGY ROADMAP TILL 2030
- 6.4.1.1 Short-term roadmap (2025-2026)
- 6.4.1.2 Mid-term roadmap (2027-2028)
- 6.4.1.3 Long-term roadmap (2029-2030)
- 6.4.1 DDOS PROTECTION AND MITIGATION SECURITY TECHNOLOGY ROADMAP TILL 2030
- 6.5 PATENT ANALYSIS
- 6.5.1 METHODOLOGY
- 6.5.2 KEY PATENTS
- 6.6 IMPACT OF AI/GEN AI ON DDOS PROTECTION AND MITIGATION SECURITY MARKET
- 6.6.1 USE CASES OF GENERATIVE AI IN DDOS PROTECTION AND MITIGATION SECURITY
- 6.6.2 BEST PRACTICES
- 6.6.2.1 BFSI
- 6.6.2.2 Government
- 6.6.2.3 Healthcare
- 6.6.3 CASE STUDIES OF GENERATIVE AI IMPLEMENTATION
- 6.6.3.1 GenAI-enhanced traffic intelligence for large-scale cloud infrastructure
- 6.6.3.2 AI-automated incident analysis for multi-national financial group
- 6.6.3.3 GenAI-driven botnet attribution for government cyber defense agency
- 6.6.4 CLIENT READINESS AND IMPACT ASSESSMENT
- 6.6.4.1 Client A: Global digital commerce platform
- 6.6.4.2 Client B: Major public sector department
- 6.6.4.3 Client C: Large healthcare network
7 REGULATORY LANDSCAPE
- 7.1 REGULATORY LANDSCAPE
- 7.1.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- 7.1.1.1 National Credit Union Administration
- 7.1.1.2 Federal Financial Institutions Examination Council
- 7.1.1.3 General Data Protection Regulation (GDPR)
- 7.1.1.4 Payment Card Industry Data Security Standard (PCI-DSS)
- 7.1.1.5 Health Insurance Portability And Accountability Act (HIPAA)
- 7.1.1.6 Gramm-Leach-Bliley (GLB) Act
- 7.1.1.7 Sarbanes-Oxley (SOX) Act
- 7.1.1.8 SOC 2
- 7.1.1.9 SWIFT CSP
- 7.1.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
8 CUSTOMER LANDSCAPE AND BUYER BEHAVIOR
- 8.1 DECISION-MAKING PROCESS
- 8.2 BUYER STAKEHOLDERS AND BUYING EVALUATION CRITERIA
- 8.2.1 KEY STAKEHOLDERS IN BUYING PROCESS
- 8.2.2 BUYING CRITERIA
- 8.2.3 ADOPTION BARRIERS AND INTERNAL CHALLENGES
9 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY OFFERING
- 9.1 INTRODUCTION
- 9.1.1 OFFERING: DDOS PROTECTION AND MITIGATION SECURITY MARKET DRIVERS
- 9.2 HARDWARE SOLUTIONS
- 9.2.1 FIREWALLS
- 9.2.1.1 Hardware firewalls filter and block malicious traffic to enable efficient server access for legitimate requests
- 9.2.2 INTRUSION DETECTION AND PREVENTION SYSTEMS (IDPS)
- 9.2.2.1 IDPS prevents DDoS attacks by continuously monitoring network traffic and actively blocking malicious requests
- 9.2.3 LOAD BALANCERS
- 9.2.3.1 Load balancers protect against DDoS attacks by distributing traffic across multiple servers
- 9.2.4 OTHER HARDWARE SOLUTIONS
- 9.2.1 FIREWALLS
- 9.3 SOFTWARE SOLUTIONS
- 9.3.1 GLOBAL RISE IN IOT DEVICES TO DRIVE MARKET
- 9.4 SERVICES
- 9.4.1 PROFESSIONAL SERVICES
- 9.4.2 DESIGN AND IMPLEMENTATION
- 9.4.2.1 Increase in need to improve network performance and reliability
- 9.4.3 CONSULTING AND ADVISORY
- 9.4.3.1 Growing concerns for cybersecurity and adoption of advanced technologies
- 9.4.4 TRAINING AND EDUCATION
- 9.4.4.1 Rising need for training and creating awareness of DDoS attacks
- 9.4.5 SUPPORT AND MAINTENANCE
- 9.4.5.1 Rising need for support for technical issues and guidance
- 9.4.6 MANAGED SERVICES
- 9.4.6.1 Need to increase business efficiency and operations
10 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY SOLUTION TYPE
- 10.1 INTRODUCTION
- 10.1.1 SOLUTION TYPE: DDOS PROTECTION AND MITIGATION SECURITY MARKET DRIVERS
- 10.2 NETWORK TRAFFIC ANALYZERS
- 10.2.1 NETWORK LAYER ATTACKS TO INCREASE ADOPTION OF DDOS PROTECTION SOLUTIONS
- 10.3 THREAT MITIGATION SYSTEMS
- 10.3.1 RISE IN LAYER 7 ATTACKS TO INCREASE DEMAND FOR DDOS PROTECTION AND MITIGATION SECURITY SOLUTIONS
- 10.4 BOTNET DETECTION & MANAGEMENT
- 10.4.1 EVOLVING DISRUPTIVE TECHNOLOGIES AND EASY AVAILABILITY OF CLOUD-BASED APPLICATIONS TO DRIVE MARKET
- 10.5 OTHER SOLUTION TYPES
11 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY APPLICATION AREA
- 11.1 INTRODUCTION
- 11.1.1 APPLICATION AREA: DDOS PROTECTION AND MITIGATION SECURITY MARKET DRIVERS
- 11.2 NETWORK SECURITY
- 11.2.1 INCREASING NEED TO ENHANCE NETWORK PERFORMANCE AND ELIMINATE DISRUPTIONS
- 11.3 APPLICATION SECURITY
- 11.3.1 RISING NEED TO MITIGATE DDOS ATTACKS AND MAINTAIN PROTECTION
- 11.4 CLOUD SECURITY
- 11.4.1 GREATER NEED FOR CLOUD-BASED APPLICATIONS SECURITY TO DRIVE MARKET
- 11.5 ENDPOINT SECURITY
- 11.5.1 INCREASING MOBILE DEVICES AND DIGITAL TRANSFORMATIONS TO DRIVE MARKET
12 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY DEPLOYMENT MODE
- 12.1 INTRODUCTION
- 12.1.1 DEPLOYMENT MODE: DDOS PROTECTION AND MITIGATION SECURITY MARKET DRIVERS
- 12.2 ON-PREMISES
- 12.2.1 ON-PREMISES SERVICES PROVIDE FULL CONTROL OF DEPLOYED SOLUTIONS IT'S STAFF
- 12.3 CLOUD
- 12.3.1 CLOUD DEPLOYMENT HELPS MANAGE DNS, REROUTE TRAFFIC, AND SAFEGUARD WEBSITE TRAFFIC
13 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY ORGANIZATION SIZE
- 13.1 INTRODUCTION
- 13.1.1 ORGANIZATION SIZE: DDOS PROTECTION AND MITIGATION SECURITY MARKET DRIVERS
- 13.2 LARGE ENTERPRISES
- 13.2.1 INCREASING SEVERITY OF DDOS DAMAGE CAUSED BY SINGLE ATTACK TO DRIVE MARKET
- 13.3 SMALL & MEDIUM-SIZED ENTERPRISES
- 13.3.1 GROWING NEED TO MITIGATE SECURITY ATTACKS TO ENHANCE MARKET GROWTH
14 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY VERTICAL
- 14.1 INTRODUCTION
- 14.1.1 VERTICAL: DDOS PROTECTION AND MITIGATION SECURITY MARKET DRIVERS
- 14.2 GOVERNMENT AND DEFENSE
- 14.2.1 INCREASING NEED FOR DDOS PROTECTION AND MITIGATION SECURITY SOLUTIONS AND SERVICES TO HELP MARKET GROWTH
- 14.3 BANKING, FINANCIAL SERVICES, AND INSURANCE
- 14.3.1 FRAGILE DATA CENTER SECURITY AND RISK OF CLOUD STORAGE DATA LEAKS TO DRIVE MARKET
- 14.4 MANUFACTURING
- 14.4.1 EVOLVING VOLUMETRIC DDOS ATTACKS ON MANUFACTURING PROCESSES TO CONTRIBUTE TO MARKET GROWTH
- 14.5 ENERGY AND UTILITIES
- 14.5.1 INCREASING ADOPTION OF SMART SYSTEMS AND APPLICATIONS TO DRIVE MARKET
- 14.6 IT AND ITES
- 14.6.1 RISE OF ADVANCED TECHNOLOGIES TO FUEL MARKET
- 14.7 TELECOM
- 14.7.1 RISE IN NUMBER OF WEB AND MOBILE APPLICATIONS TO FUEL MARKET
- 14.8 HEALTHCARE
- 14.8.1 REGULATORY NORMS TO INCREASE DEPLOYMENT OF DDOS PROTECTION AND MITIGATION SECURITY SOLUTIONS
- 14.9 EDUCATION
- 14.9.1 NEED FOR CONFIDENTIALITY, INTEGRITY, AND EASY AVAILABILITY OF DATA AND RESOURCES TO AUGMENT MARKET GROWTH
- 14.10 RETAIL
- 14.10.1 GROWING CYBERATTACKS AND DATA THEFT TO INCREASE ADOPTION OF DDOS PROTECTION AND MITIGATION SECURITY SOLUTIONS
- 14.11 OTHER VERTICALS
15 DDOS PROTECTION AND MITIGATION SECURITY MARKET, BY REGION
- 15.1 INTRODUCTION
- 15.2 NORTH AMERICA
- 15.2.1 NORTH AMERICA: MACROECONOMIC OUTLOOK
- 15.2.2 US
- 15.2.2.1 Presence of major vendors in US driving market growth
- 15.2.3 CANADA
- 15.2.3.1 Rapid technological advancements and increasing DDoS attacks on network infrastructure to drive market
- 15.3 EUROPE
- 15.3.1 EUROPE: MACROECONOMIC OUTLOOK
- 15.3.2 UK
- 15.3.2.1 Increasing demand for monitoring solutions among SMEs to drive market
- 15.3.3 GERMANY
- 15.3.3.1 Increasing investments in DDoS protection and mitigation solutions to drive market
- 15.3.4 REST OF EUROPE
- 15.4 ASIA PACIFIC
- 15.4.1 ASIA PACIFIC: MACROECONOMIC OUTLOOK
- 15.4.2 CHINA
- 15.4.2.1 Development of cybersecurity safeguard system to fuel market
- 15.4.3 JAPAN
- 15.4.3.1 Stringent laws and regulations for cybersecurity to drive market
- 15.4.4 INDIA
- 15.4.4.1 Increasing DDoS attacks leading to adoption of DDoS protection and mitigation security solutions
- 15.4.5 REST OF ASIA PACIFIC
- 15.5 MIDDLE EAST & AFRICA
- 15.5.1 MIDDLE EAST & AFRICA: MACROECONOMIC OUTLOOK
- 15.5.2 KSA
- 15.5.2.1 Increasing investments in mitigation security and growth in number of startups to drive market
- 15.5.3 UAE
- 15.5.3.1 Growing reliance on cloud-based applications to boost market
- 15.5.4 SOUTH AFRICA
- 15.5.4.1 Government initiatives and substantial foreign investments to drive market
- 15.5.5 REST OF MIDDLE EAST & AFRICA
- 15.6 LATIN AMERICA
- 15.6.1 LATIN AMERICA: MACROECONOMIC OUTLOOK
- 15.6.2 BRAZIL
- 15.6.2.1 Increasing focus on establishing effective cybersecurity strategies to drive market
- 15.6.3 MEXICO
- 15.6.3.1 Rising adoption of cloud-based services to drive market
- 15.6.4 REST OF LATIN AMERICA
16 COMPETITIVE LANDSCAPE
- 16.1 INTRODUCTION
- 16.2 KEY PLAYER STRATEGIES/RIGHT TO WIN, 2022-2025
- 16.3 REVENUE ANALYSIS, 2020-2024
- 16.4 MARKET SHARE ANALYSIS, 2024
- 16.4.1 MARKET RANKING ANALYSIS, 2024
- 16.5 COMPANY EVALUATION MATRIX: KEY PLAYERS, 2024
- 16.5.1 STARS
- 16.5.2 EMERGING LEADERS
- 16.5.3 PERVASIVE PLAYERS
- 16.5.4 PARTICIPANTS
- 16.5.5 COMPANY FOOTPRINT: KEY PLAYERS, 2024
- 16.5.5.1 Company footprint
- 16.5.5.2 Regional footprint
- 16.5.5.3 Offering footprint
- 16.5.5.4 Vertical footprint
- 16.6 COMPANY EVALUATION MATRIX: STARTUPS/SMES, 2024
- 16.6.1 PROGRESSIVE COMPANIES
- 16.6.2 RESPONSIVE COMPANIES
- 16.6.3 DYNAMIC COMPANIES
- 16.6.4 STARTING BLOCKS
- 16.6.5 COMPETITIVE BENCHMARKING: STARTUPS/SMES, 2024
- 16.6.5.1 Detailed list of key startups/SMEs
- 16.6.5.2 Competitive benchmarking of key startups/SMEs
- 16.7 COMPETITIVE SCENARIO
- 16.7.1 PRODUCT LAUNCHES & ENHANCEMENTS
- 16.7.2 DEALS
- 16.8 BRAND/PRODUCT COMPARISON
- 16.9 COMPANY VALUATION AND FINANCIAL METRICS, 2025
- 16.9.1 COMPANY VALUATION
- 16.9.2 FINANCIAL METRICS
17 COMPANY PROFILES
- 17.1 KEY PLAYERS
- 17.1.1 NETSCOUT
- 17.1.1.1 Business overview
- 17.1.1.2 Products/Solutions/Services offered
- 17.1.1.3 Recent developments
- 17.1.1.3.1 Product launches & enhancements
- 17.1.1.3.2 Deals
- 17.1.1.3.3 Expansions
- 17.1.1.4 MnM view
- 17.1.1.4.1 Right to win
- 17.1.1.4.2 Strategic choices
- 17.1.1.4.3 Weaknesses and competitive threats
- 17.1.2 AKAMAI TECHNOLOGIES
- 17.1.2.1 Business overview
- 17.1.2.2 Products/Solutions/Services offered
- 17.1.2.3 Recent developments
- 17.1.2.3.1 Product launches & enhancements
- 17.1.2.3.2 Deals
- 17.1.2.3.3 Expansions
- 17.1.2.4 MnM view
- 17.1.2.4.1 Right to win
- 17.1.2.4.2 Strategic choices
- 17.1.2.4.3 Weaknesses and competitive threats
- 17.1.3 RADWARE
- 17.1.3.1 Business overview
- 17.1.3.2 Products/Solutions/Services offered
- 17.1.3.3 Recent developments
- 17.1.3.3.1 Product launches & enhancements
- 17.1.3.3.2 Deals
- 17.1.3.4 MnM view
- 17.1.3.4.1 Right to win
- 17.1.3.4.2 Strategic choices
- 17.1.3.4.3 Weaknesses and competitive threats
- 17.1.4 CLOUDFLARE
- 17.1.4.1 Business overview
- 17.1.4.2 Products/Solutions/Services offered
- 17.1.4.3 MnM view
- 17.1.4.3.1 Key strengths
- 17.1.4.3.2 Strategic choices
- 17.1.4.3.3 Weaknesses and competitive threats
- 17.1.5 FORTINET
- 17.1.5.1 Business overview
- 17.1.5.2 Products/Solutions/Services offered
- 17.1.5.3 Recent developments
- 17.1.5.3.1 Deals
- 17.1.5.4 MnM view
- 17.1.5.4.1 Key strengths
- 17.1.5.4.2 Strategic choices
- 17.1.5.4.3 Weaknesses and competitive threats
- 17.1.6 HUAWEI
- 17.1.6.1 Business overview
- 17.1.6.2 Products/Solutions/Services offered
- 17.1.6.3 Recent developments
- 17.1.6.3.1 Deals
- 17.1.7 LINK11
- 17.1.7.1 Business overview
- 17.1.7.2 Products/Solutions/Services offered
- 17.1.7.3 Recent developments
- 17.1.7.3.1 Product launches & enhancements
- 17.1.7.3.2 Deals
- 17.1.8 IMPERVA (A THALES COMPANY)
- 17.1.8.1 Business overview
- 17.1.8.2 Products/Solutions/Services offered
- 17.1.8.3 Recent developments
- 17.1.8.3.1 Deals
- 17.1.9 BT
- 17.1.9.1 Business overview
- 17.1.9.2 Products/Solutions/Services offered
- 17.1.9.3 Recent developments
- 17.1.9.3.1 Deals
- 17.1.10 A10 NETWORKS
- 17.1.10.1 Business overview
- 17.1.10.2 Products/Solutions/Services offered
- 17.1.1 NETSCOUT
- 17.2 OTHER PLAYERS
- 17.2.1 FASTLY
- 17.2.2 F5
- 17.2.3 CORERO
- 17.2.4 ALLOT
- 17.2.5 STRATACORE
- 17.2.6 SUCURI
- 17.2.7 NSFOCUS
- 17.2.8 LUMEN TECHNOLOGIES
- 17.3 SMES/STARTUPS
- 17.3.1 STACKPATH
- 17.3.2 SECEON
- 17.3.3 HALTDOS
- 17.3.4 DDOS-GUARD
- 17.3.5 INDUSFACE
- 17.3.6 ACTIVEREACH
- 17.3.7 MLYTICS
- 17.3.8 NEXUSGUARD
- 17.3.9 RIOREY
- 17.3.10 PHOENIXNAP
- 17.3.11 COMODO SECURITY SOLUTIONS
18 RESEARCH METHODOLOGY
- 18.1 RESEARCH DATA
- 18.1.1 SECONDARY DATA
- 18.1.2 PRIMARY DATA
- 18.1.2.1 Primary interviews with experts
- 18.1.2.2 Breakdown of primary profiles
- 18.1.2.3 Key insights from industry experts
- 18.2 MARKET SIZE ESTIMATION
- 18.2.1 TOP-DOWN APPROACH
- 18.2.2 BOTTOM-UP APPROACH
- 18.2.3 DDOS PROTECTION AND MITIGATION SECURITY MARKET ESTIMATION: DEMAND-SIDE ANALYSIS
- 18.3 DATA TRIANGULATION
- 18.4 RISK ASSESSMENT
- 18.5 RESEARCH ASSUMPTIONS
- 18.6 RESEARCH LIMITATIONS
19 ADJACENT AND RELATED MARKETS
- 19.1 INTRODUCTION
- 19.2 CYBERSECURITY MARKET
- 19.2.1 MARKET DEFINITION
- 19.3 SECURITY AS A SERVICE MARKET
- 19.3.1 MARKET DEFINITION
20 APPENDIX
- 20.1 DISCUSSION GUIDE
- 20.2 KNOWLEDGESTORE: MARKETSANDMARKETS' SUBSCRIPTION PORTAL
- 20.3 CUSTOMIZATION OPTIONS
- 20.4 RELATED REPORTS
- 20.5 AUTHOR DETAILS



















