
|
시장보고서
상품코드
1816003
위협 인텔리전스 시장 예측(-2030년) : 오퍼링별, 용도별, 배포 모드별, 유형별, 조직 규모별, 업계별, 지역별Threat Intelligence Market by Solution (Threat Intelligence Platform (TIPS), SIEM Integration), Service (Risk Assessment and Threat Hunting, MDR), Application (Incident Response, Fraud, Threat Hunting), Vertical, Region - Global Forecast to 2030 |
||||||
위협 인텔리전스 시장 규모는 2025년 115억 5,000만 달러에서 2030년에는 229억 7,000만 달러로 성장하며, 예측 기간 중 CAGR은 14.7%로 예측됩니다.
| 조사 범위 | |
|---|---|
| 조사 대상연도 | 2019-2030년 |
| 기준연도 | 2024년 |
| 예측 기간 | 2025-2030년 |
| 검토 단위 | 금액(100만 달러/10억 달러) |
| 부문 | 오퍼링별, 용도별, 배포 모드별, 유형별, 조직 규모별, 업계별, 지역별 |
| 대상 지역 | 북미, 유럽, 아시아태평양, 중동 및 아프리카, 라틴아메리카 |
조직이 사고에 대응하는 것이 아니라 예방과 조기 발견에 중점을 둔 사전 예방적 보안 전략으로 전환하고 있는 것이 지능형 위협 인텔리전스에 대한 수요를 촉진하고 있습니다. 동시에 양자컴퓨팅 연구의 급속한 발전으로 현재 암호화 기술의 장기적인 안전성에 대한 우려가 커지고 있으며, 기업은 새로운 위험을 예측하고 완화하기 위해 더 높은 수준의 인텔리전스 기능을 요구하고 있습니다. 이러한 추세는 지속적인 모니터링, 예측 분석, 실행 가능한 인사이트를 제공하고 진화하는 사이버 위협에 선제적으로 대응할 수 있는 솔루션에 대한 투자를 촉진하고 있습니다.
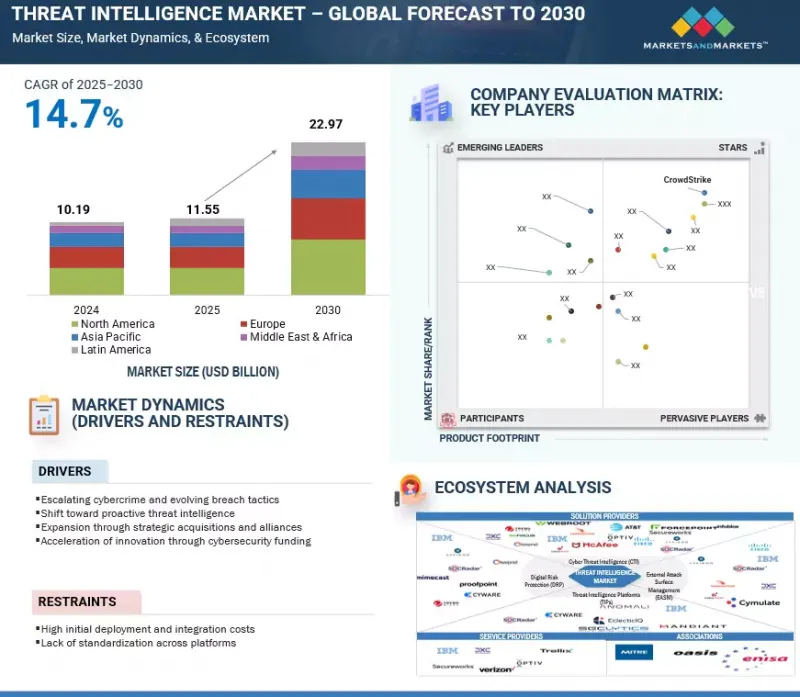
클라우드 기반 위협 인텔리전스 플랫폼의 도입으로 기업은 보안 운영을 신속하게 확장하고 지속적으로 업데이트되는 방대한 데이터 스트림을 활용하여 새로운 위협을 실시간으로 감지하는 데 이상적입니다. 구글 클라우드가 지원한 조사에 따르면 80% 이상의 조직이 데이터 양 증가와 경보 피로로 인한 주요 보안 요구사항을 해결하기 위해 위협 인텔리전스를 이미 사용하고 있거나 도입할 계획인 것으로 나타났습니다. AWS GuardDuty 및 Microsoft Defender for Cloud와 같은 주요 클라우드 네이티브 솔루션은 머신러닝, 이상 징후 감지, 통합 위협 피드를 활용하여 API 설정 오류부터 스텔스 침입 시도에 이르기까지 다양한 위협을 사전에 식별합니다. 또한 위협 인텔리전스를 클라우드에 배포하면 보안 오케스트레이션 워크플로우와 원활하게 통합되어 신속한 사고 대응, 컴플라이언스 향상, 동적 하이브리드 환경 전반에 걸친 보호 강화가 가능해집니다. 또한 클라우드 모델을 통해 소규모 조직도 하드웨어나 전담 SOC 팀에 대한 대규모 선행 투자 없이도 기업급 위협 인텔리전스 기능을 이용할 수 있습니다. 또한 인텔리전스 공유 커뮤니티를 통합함으로써 세계 협업을 가능하게 하고, 업계 전반의 방어 담당자들이 진화하는 공격 전술에 대한 지식을 공유함으로써 이익을 얻을 수 있습니다.
아시아태평양의 위협 인텔리전스 시장은 사이버 범죄자들이 급성장하는 이 지역의 디지털 경제를 점점 더 많이 표적으로 삼으면서 빠르게 성장하고 있습니다. Group-IB에 따르면 2024년에는 APAC 지역이 전 세계 랜섬웨어 공격의 40%를 차지할 것으로 예상되며, 그 중에서도 제조업과 금융 서비스가 가장 큰 타격을 받을 것으로 예측됩니다. 호주사이버보안센터(ACSC)는 2024년 비즈니스 이메일 침해 사례가 23% 증가하여 피해액이 7,000만 달러 이상에 달할 것으로 예상하고 있습니다. 한편, 일본 경찰청은 모바일 결제와 현금 없는 결제의 급속한 보급에 힘입어 2024년에는 사상 최대인 3만 5,000건의 피싱 사건이 발생할 것으로 예상하고 있습니다. 각국 정부는 보다 강력한 프레임워크를 도입하고 있습니다. 싱가포르는 정보 공유를 강화하기 위해 사이버 보안 마스터플랜 2025를 출범시켰고, 인도는 실시간 위협 분석을 개선하기 위해 국가사이버조정센터(NCCC)를 확장하고 있습니다. 5G 및 IoT 생태계의 확장과 함께 국가 지원 캠페인 증가는 AI를 활용한 위협 감지, 자동화된 사고 대응, 중요 인프라 및 기밀 데이터 보호를 위한 국경 간 정보 공유에 대한 강력한 수요를 촉진하고 있습니다.
세계의 위협 인텔리전스 시장에 대해 조사했으며, 오퍼링별, 용도별, 배포 모드별, 유형별, 조직 규모별, 업계별, 지역별 동향 및 시장에 참여하는 기업의 개요 등을 정리하여 전해드립니다.
목차
제1장 서론
제2장 조사 방법
제3장 개요
제4장 주요 인사이트
제5장 시장 개요와 업계 동향
- 서론
- 시장 역학
- 사례 연구 분석
- Porter's Five Forces 분석
- 주요 이해관계자와 구입 기준
- 밸류체인 분석
- 에코시스템 분석
- 특허 분석
- 가격 분석
- 기술 분석
- 위협 인텔리전스 시장에서 AI
- 생성형 AI가 위협 인텔리전스 시장에 미치는 영향
- 고객 비즈니스에 영향을 미치는 동향/혼란
- 규제 상황
- 2025년의 주요 컨퍼런스와 이벤트
- 투자와 자금조달 시나리오
- 무역 분석
- 2025년 미국 관세의 영향-개요
제6장 위협 인텔리전스 시장(오퍼링별)
- 서론
- 솔루션
- 서비스
제7장 위협 인텔리전스 시장(용도별)
- 서론
- 사기 및 금융 범죄 탐지
- 위협 헌팅
- 내부 위협 탐지
- 인시던트 대응
- 리스크와 컴플라이언스 관리
- 기타
제8장 위협 인텔리전스 시장(배포 형태별)
- 서론
- 클라우드
- 온프레미스
- 하이브리드
제9장 위협 인텔리전스 시장(유형별)
- 서론
- 전략
- 운영
- 전술
- 기술
제10장 위협 인텔리전스 시장(조직 규모별)
- 서론
- 대기업
- 중소기업
제11장 위협 인텔리전스 시장(업계별)
- 서론
- 은행, 금융 서비스, 보험
- 정부
- 방위와 정보
- 헬스케어
- 소매
- 여행, 항공, 물류
- IT, ITES, 통신
- 에너지·산업
- 미디어·엔터테인먼트
- 기타
제12장 위협 인텔리전스 시장(지역별)
- 서론
- 북미
- 북미 : 시장 성장 촉진요인
- 북미 : 거시경제 전망
- 미국
- 캐나다
- 유럽
- 유럽 : 시장 성장 촉진요인
- 유럽 : 거시경제 전망
- 영국
- 독일
- 프랑스
- 이탈리아
- 기타
- 아시아태평양
- 아시아태평양 : 시장 성장 촉진요인
- 아시아태평양 : 거시경제 전망
- 중국
- 일본
- 인도
- 싱가포르
- 기타
- 중동 및 아프리카
- 중동 및 아프리카 : 시장 성장 촉진요인
- 중동 및 아프리카 : 거시경제 전망
- 중동
- 아프리카
- 라틴아메리카
- 라틴아메리카 : 시장 성장 촉진요인
- 라틴아메리카 : 거시경제 전망
- 브라질
- 멕시코
- 기타
제13장 경쟁 구도
- 개요
- 주요 참여 기업의 전략/강점
- 매출 분석, 2021-2024년
- 시장 점유율 분석, 2024년
- 제품/브랜드 비교
- 기업 평가와 재무 지표, 2025년
- 기업 평가 매트릭스 : 주요 참여 기업, 2024년
- 기업 평가 매트릭스 : 스타트업/중소기업, 2024년
- 경쟁 시나리오
제14장 기업 개요
- 주요 참여 기업
- PALO ALTO NETWORKS
- CROWDSTRIKE
- IBM
- CISCO
- FORTINET
- CHECK POINT
- TRELLIX
- RAPID7
- RECORDED FUTURE
- GROUP-IB
- KASPERSKY
- ANOMALI
- CPX
- KELA
- ZEROFOX
- ORANGE
- RESECURITY
- HELP AG
- GATEWATCHER
- CYBLE
- CYBERINT
- SOCRADAR
- THREATCONNECT
- QUOINTELLIGENCE
- THREATMON
- SECURITY PACT
- SECURIUM SOLUTIONS
- FLASHPOINT
- RELIAQUEST
- THREAT QUOTIENT
제15장 인접 시장
제16장 부록
KSA 25.09.25The threat intelligence market is projected to grow from USD 11.55 billion in 2025 to USD 22.97 billion by 2030 at a CAGR of 14.7% during the forecast period.
| Scope of the Report | |
|---|---|
| Years Considered for the Study | 2019-2030 |
| Base Year | 2024 |
| Forecast Period | 2025-2030 |
| Units Considered | Value (USD Million/USD Billion) |
| Segments | Offering, Application, Type, Deployment Mode, Organization Size, Vertical, and Region |
| Regions covered | North America, Europe, Asia Pacific, the Middle East & Africa, and Latin America |
The growing shift toward proactive security strategies, where organizations focus on prevention and early detection instead of purely reacting to incidents, is fueling demand for advanced threat intelligence. At the same time, the rapid progress in quantum computing research is raising concerns over the long-term security of current encryption methods, pushing enterprises to seek more sophisticated intelligence capabilities to anticipate and mitigate emerging risks. Together, these trends are driving investment in solutions that deliver continuous monitoring, predictive analytics, and actionable insights to stay ahead of evolving cyber threats.
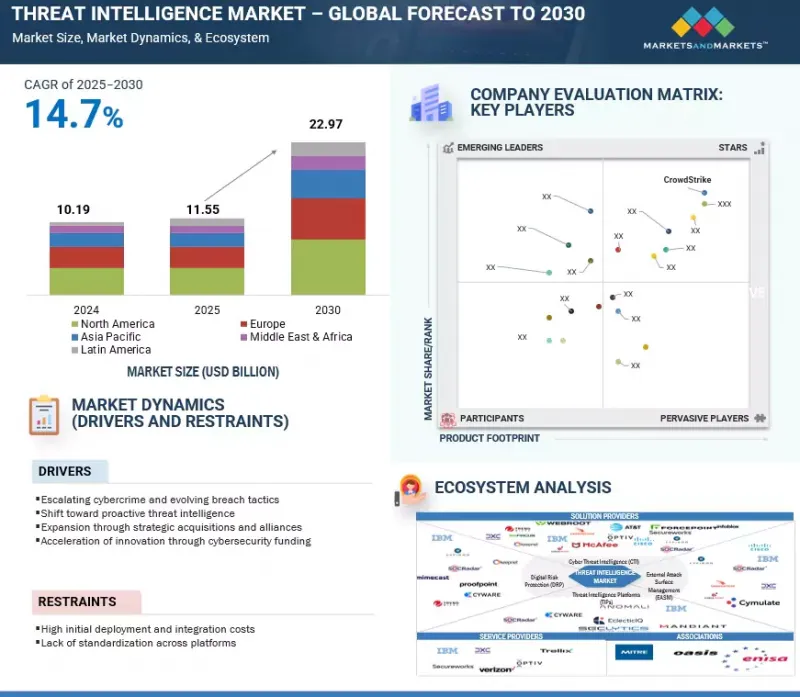
"By deployment mode, the cloud segment is expected to account for the largest market share during the forecast period."
Cloud-based deployment of threat intelligence platforms enables organizations to rapidly scale their security operations and tap into vast, continuously updated data streams, making it ideal for detecting emerging threats in real time. According to a Google Cloud-backed survey, more than 80% of organizations already use or plan to adopt threat intelligence to address key security needs due to escalating data volumes and alert fatigue. Leading cloud-native solutions such as AWS GuardDuty and Microsoft Defender for Cloud harness machine learning, anomaly detection, and integrated threat feeds to proactively identify threats that span from misconfigured APIs to stealthy intrusion attempts. Deploying threat intelligence in the cloud also fosters seamless integration with security orchestration workflows, enabling faster incident response, improved compliance, and enhanced protection across dynamic, hybrid environments. Furthermore, cloud models provide smaller organizations access to enterprise-grade threat intelligence capabilities without heavy upfront investment in hardware or dedicated SOC teams. They also enable global collaborations by integrating intelligence-sharing communities, allowing defenders across industries to benefit from shared insights on evolving attack tactics.
"By region, Asia Pacific is projected to witness the highest growth rate during the forecast period."
The Asia Pacific (APAC) threat intelligence market is witnessing rapid expansion as cybercriminals increasingly target the region's fast-growing digital economies. According to Group-IB, APAC accounted for 40% of global ransomware attacks in 2024, with manufacturing and financial services among the hardest hit. The Australian Cyber Security Centre (ACSC) reported a 23% increase in business email compromise cases in 2024, with losses exceeding USD 70 million. Meanwhile, Japan's National Police Agency noted a record 35,000 phishing cases in 2024, fueled by the surge in mobile and cashless payment adoption. Governments are implementing stronger frameworks; Singapore has launched its Cybersecurity Masterplan 2025 to enhance intelligence sharing, while India is expanding its National Cyber Coordination Centre (NCCC) to improve real-time threat analysis. The rise of nation-state-backed campaigns, coupled with expanding 5G and IoT ecosystems, is driving strong demand for AI-powered threat detection, automated incident response, and cross-border intelligence sharing to safeguard critical infrastructure and sensitive data.
Breakdown of primaries
The study contains insights from various industry experts, from component suppliers to Tier 1 companies and OEMs. The break-up of the primaries is as follows:
- By Company Type: Tier 1 - 35%, Tier 2 - 45%, and Tier 3 - 20%
- By Designation: C-level - 40%, Managers & other Levels- 60%
- By Region: North America - 38%, Europe - 26%, Asia Pacific - 21%, Middle East & Africa - 10%, Latin America - 5%
The key players in the threat intelligence market include Palo Alto Networks (US), Cisco (US), Check Point (Israel), CrowdStrike (US), IBM (US), Recorded Future (US), Google (US), Flashpoint (US), Group-IB (Singapore), Kaspersky (Russia), Trellix (US), Rapid7 (US), Fortinet (US), ReliaQuest (US), CPX (UAE), ZeroFox (US), Orange (France), Anomali (US), Resecurity (US), Help AG (UAE), Gatewatcher (France), Cyble (US), Cyberint (Israel), SOCRadar (US), ThreatConnect (US), ThreatQuotient (US), Quontelligence (Netherlands), ThreatMon (Turkey), Security Pact (France), and Securium Solutions (India), among others.
Research Coverage
The report segments the threat intelligence market and forecasts its size by offering (solutions, services), application (digital risk & brand protection, fraud & financial crime detection, threat hunting, incident response, insider threat detection, risk & compliance management, others (vulnerability intelligence and third-party intelligence)), type (strategic, operational, tactical, technical), deployment mode (on-premises, cloud, hybrid), organization size (large enterprises, SMEs), vertical (banking, financial services, and insurance (BFSI), government, defense & intelligence, healthcare, retail, travel, aviation, & logistics, IT, ITeS, & telecom, energy & industrial, media & entertainment, other verticals (education, construction, and real estate)), and region (North America, Europe, Asia Pacific, Middle East & Africa, and Latin America).
The study also includes an in-depth competitive analysis of the market's key players, their company profiles, key observations related to product and business offerings, recent developments, and key market strategies.
Key Benefits of Buying the Report
The report will help market leaders and new entrants with information on the closest approximations of the revenue numbers for the overall threat intelligence market and its subsegments. It will also help stakeholders understand the competitive landscape and gain more insights to better position their businesses and plan suitable go-to-market strategies. The report also helps stakeholders understand the market pulse and provides information on key market drivers, restraints, challenges, and opportunities.
The report provides insights on the following pointers:
- Analysis of key drivers (Escalating cybercrime and evolving breach tactics, shift toward proactive threat intelligence, expansion through strategic acquisitions and alliances, acceleration of innovation through cybersecurity funding), restraints (High initial deployment and integration costs, lack of standardization across platforms), opportunities (Expansion of connected devices and IoT risks, rising cloud security challenges, malicious use of AI and machine learning), and challenges (Lack of trained security analysts to analyze threat intelligence systems, management of voluminous data)
- Product Development/Innovation: Detailed insights on upcoming technologies, research & development activities, and product & service launches in the threat intelligence market.
- Market Development: Comprehensive information about lucrative markets - the report analyzes the threat intelligence market across varied regions.
- Market Diversification: Exhaustive information about new products & services, untapped geographies, recent developments, and investments in the threat intelligence market.
- Competitive Assessment: In-depth assessment of market shares, growth strategies, and service offerings of leading players such Palo Alto Networks (US), Cisco (US), Check Point (Israel), CrowdStrike (US), IBM (US), Recorded Future (US), Google (US), Flashpoint (US), Group-IB (Singapore), Kaspersky (Russia), Trellix (US), Rapid7 (US), Fortinet (US), ReliaQuest (US), CPX (UAE), ZeroFox (US), Orange (France), Anomali (US), Resecurity (US), Help AG (UAE), Gatewatcher (France), Cyble (US), Cyberint (Israel), SOCRadar (US), ThreatConnect (US), ThreatQuotient (US), Quontelligence (Netherlands), ThreatMon (Turkey), Security Pact (France), and Securium Solutions (India) in the threat intelligence market.
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 STUDY OBJECTIVES
- 1.2 MARKET DEFINITION
- 1.3 STUDY SCOPE
- 1.3.1 MARKET SEGMENTATION AND REGIONAL SCOPE
- 1.3.2 INCLUSIONS & EXCLUSIONS
- 1.4 YEARS CONSIDERED
- 1.5 CURRENCY CONSIDERED
- 1.6 STAKEHOLDERS
- 1.7 SUMMARY OF CHANGES
2 RESEARCH METHODOLOGY
- 2.1 RESEARCH DATA
- 2.1.1 SECONDARY DATA
- 2.1.2 PRIMARY DATA
- 2.1.2.1 Breakup of primary profiles
- 2.1.2.2 Key industry insights
- 2.2 DATA TRIANGULATION
- 2.3 MARKET SIZE ESTIMATION
- 2.3.1 TOP-DOWN APPROACH
- 2.3.2 BOTTOM-UP APPROACH
- 2.4 MARKET FORECAST
- 2.5 RESEARCH ASSUMPTIONS
- 2.6 RESEARCH LIMITATIONS
3 EXECUTIVE SUMMARY
4 PREMIUM INSIGHTS
- 4.1 ATTRACTIVE OPPORTUNITIES FOR PLAYERS IN THREAT INTELLIGENCE MARKET
- 4.2 THREAT INTELLIGENCE MARKET, BY OFFERING
- 4.3 THREAT INTELLIGENCE MARKET, BY APPLICATION
- 4.4 THREAT INTELLIGENCE MARKET, BY DEPLOYMENT MODE
- 4.5 THREAT INTELLIGENCE MARKET, BY ORGANIZATION SIZE
- 4.6 THREAT INTELLIGENCE MARKET, BY VERTICAL, 2025-2030
- 4.7 MARKET INVESTMENT SCENARIO
5 MARKET OVERVIEW AND INDUSTRY TRENDS
- 5.1 INTRODUCTION
- 5.2 MARKET DYNAMICS
- 5.2.1 DRIVERS
- 5.2.1.1 Escalating cybercrime and evolving breach tactics
- 5.2.1.2 Shift toward proactive threat intelligence
- 5.2.1.3 Expansion through strategic acquisitions and alliances
- 5.2.1.4 Advancing threat intelligence capabilities through cybersecurity funding
- 5.2.2 RESTRAINTS
- 5.2.2.1 High initial deployment and integration costs
- 5.2.2.2 Lack of standardization across platforms
- 5.2.3 OPPORTUNITIES
- 5.2.3.1 Expansion of connected devices and IoT risks
- 5.2.3.2 Rising cloud security challenges
- 5.2.3.3 Malicious use of AI and Machine Learning
- 5.2.4 CHALLENGES
- 5.2.4.1 Lack of trained security analysts to analyze threat intelligence systems
- 5.2.4.2 Management of voluminous data
- 5.2.1 DRIVERS
- 5.3 CASE STUDY ANALYSIS
- 5.4 PORTER'S FIVE FORCES ANALYSIS
- 5.4.1 THREAT OF NEW ENTRANTS
- 5.4.2 THREAT OF SUBSTITUTES
- 5.4.3 BARGAINING POWER OF SUPPLIERS
- 5.4.4 BARGAINING POWER OF BUYERS
- 5.4.5 INTENSITY OF COMPETITIVE RIVALRY
- 5.5 KEY STAKEHOLDERS & BUYING CRITERIA
- 5.5.1 KEY STAKEHOLDERS IN BUYING PROCESS
- 5.5.2 BUYING CRITERIA
- 5.6 VALUE CHAIN ANALYSIS
- 5.6.1 PLANNING AND DESIGNING
- 5.6.2 THREAT INTELLIGENCE SOLUTION
- 5.6.3 SYSTEM INTEGRATION
- 5.6.4 CONSULTATION
- 5.6.5 VERTICALS
- 5.7 ECOSYSTEM ANALYSIS
- 5.8 PATENT ANALYSIS
- 5.8.1 LIST OF TOP PATENTS IN THREAT INTELLIGENCE MARKET, 2022-2025
- 5.9 PRICING ANALYSIS
- 5.9.1 AVERAGE SELLING PRICE OF THREAT INTELLIGENCE SOLUTIONS, BY KEY PLAYER, 2025
- 5.9.2 INDICATIVE PRICING ANALYSIS, BY APPLICATION, 2025
- 5.10 TECHNOLOGY ANALYSIS
- 5.10.1 KEY TECHNOLOGIES
- 5.10.1.1 AI/ML
- 5.10.1.2 Endpoint Detection and Response
- 5.10.2 COMPLEMENTARY TECHNOLOGIES
- 5.10.2.1 Extended Detection and Response
- 5.10.2.2 Network Detection and Response
- 5.10.3 ADJACENT TECHNOLOGIES
- 5.10.3.1 Deception
- 5.10.3.2 Firewall and Intrusion Detection/Prevention Systems
- 5.10.1 KEY TECHNOLOGIES
- 5.11 AI IN THREAT INTELLIGENCE MARKET
- 5.11.1 GLOBAL AI TRENDS IN THREAT INTELLIGENCE MARKET
- 5.11.1.1 Integration of AI with Cyber Threat Intelligence
- 5.11.1.2 Advancements in Natural Language Processing
- 5.11.1.3 Surge in Cloud-based AI threat intelligence solutions
- 5.11.1.4 Adoption of predictive AI threat intelligence
- 5.11.1.5 Accelerated adoption of AI for military-grade cyber threat detection
- 5.11.1.6 Rise of AI-powered botnets
- 5.11.2 FACTORS DRIVING ADOPTION OF AI IN THREAT INTELLIGENCE MARKET
- 5.11.2.1 Growing demand for automated security solutions
- 5.11.2.2 Generative AI advancements
- 5.11.2.3 Emerging AI regulations and governance frameworks
- 5.11.3 INVESTMENTS AND FUNDING SCENARIO RELATED TO AI IN THREAT INTELLIGENCE MARKET
- 5.11.3.1 Key insights
- 5.11.1 GLOBAL AI TRENDS IN THREAT INTELLIGENCE MARKET
- 5.12 IMPACT OF GENERATIVE AI ON THREAT INTELLIGENCE MARKET
- 5.12.1 TOP USE CASES & MARKET POTENTIAL
- 5.12.1.1 Key use cases
- 5.12.2 IMPACT OF GEN AI ON INTERCONNECTED AND ADJACENT ECOSYSTEM
- 5.12.2.1 Security Information and Event Management (SIEM)
- 5.12.2.2 Security Orchestration, Automation, and Response (SOAR)
- 5.12.2.3 Endpoint Detection and Response (EDR)
- 5.12.2.4 Managed Detection and Response (MDR)
- 5.12.1 TOP USE CASES & MARKET POTENTIAL
- 5.13 TRENDS/DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- 5.14 REGULATORY LANDSCAPE
- 5.14.1 TARIFF RELATED TO MACHINES FOR RECEPTION, CONVERSION, AND TRANSMISSION OR REGENERATION OF VOICE AND IMAGES
- 5.14.2 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- 5.14.3 KEY REGULATIONS
- 5.14.3.1 NIS2 Directive (EU)
- 5.14.3.2 Cybersecurity Information Sharing Act (CISA) - USA
- 5.14.3.3 China Cybersecurity Law
- 5.14.3.4 General Data Protection Regulation (GDPR)
- 5.14.3.5 IT Act & CERT-In Guidelines - India
- 5.15 KEY CONFERENCES & EVENTS IN 2025
- 5.16 INVESTMENT AND FUNDING SCENARIO
- 5.17 TRADE ANALYSIS
- 5.17.1 EXPORT SCENARIO
- 5.17.2 IMPORT SCENARIO
- 5.18 IMPACT OF 2025 US TARIFF - OVERVIEW
- 5.18.1 INTRODUCTION
- 5.18.2 KEY TARIFF RATES
- 5.18.3 PRICE IMPACT ANALYSIS
- 5.18.4 IMPACT ON COUNTRY/REGION
- 5.18.4.1 North America
- 5.18.4.1.1 United States
- 5.18.4.1.2 Canada
- 5.18.4.1.3 Mexico
- 5.18.4.1.4 Market Challenges
- 5.18.4.1.5 Mitigation Measures
- 5.18.4.2 Europe
- 5.18.4.2.1 Germany
- 5.18.4.2.2 France
- 5.18.4.2.3 United Kingdom
- 5.18.4.2.4 Market Challenges
- 5.18.4.2.5 Mitigation Measures
- 5.18.4.3 Asia Pacific
- 5.18.4.3.1 China
- 5.18.4.3.2 India
- 5.18.4.3.3 Japan
- 5.18.4.4 Market Challenges
- 5.18.4.5 Mitigation Measures
- 5.18.4.1 North America
- 5.18.5 INDUSTRIES
6 THREAT INTELLIGENCE MARKET, OFFERING
- 6.1 INTRODUCTION
- 6.1.1 OFFERING: THREAT INTELLIGENCE MARKET DRIVERS
- 6.2 SOLUTIONS
- 6.2.1 THREAT INTELLIGENCE PLATFORMS
- 6.2.1.1 Surge in targeted attacks, ransomware, and APTs to drive market
- 6.2.2 SIEM/SOAR INTEGRATION
- 6.2.2.1 High volume of alerts from SIEM and SOAR platforms to enrich security events with contextualized threat data
- 6.2.3 THREAT FEED AGGREGATORS
- 6.2.3.1 Reduction of false positives to build cost-effective threat monitoring capabilities
- 6.2.3.1.1 Commercial
- 6.2.3.1.2 Open-source
- 6.2.3.1 Reduction of false positives to build cost-effective threat monitoring capabilities
- 6.2.4 MALWARE & VULNERABILITY TOOLS
- 6.2.4.1 Surge in phishing, trojans, and fileless attacks to boost demand for advanced behavioral malware detection
- 6.2.5 THREAT ENRICHMENT API
- 6.2.5.1 API-driven enrichment supporting proactive threat hunting and SOC playbooks to reduce mean time to detect
- 6.2.6 DIGITAL RISK PROTECTION
- 6.2.6.1 Growing online presence and digital footprint to boost adoption of threat intelligence solutions
- 6.2.7 EXTERNAL ATTACK SURFACE MANAGEMENT
- 6.2.7.1 Technological advancements, shifting economic landscapes, and evolving security measures to drive market
- 6.2.1 THREAT INTELLIGENCE PLATFORMS
- 6.3 SERVICES
- 6.3.1 PROFESSIONAL SERVICES
- 6.3.1.1 Organizations seeking proactive threat hunting and vulnerability assessments to leverage expert services and reduce risks
- 6.3.1.2 Designing, integration, & deployment
- 6.3.1.3 Consulting & advisory services
- 6.3.1.4 Risk assessment & threat hunting
- 6.3.1.4.1 Forensic investigation & post-breach analysis
- 6.3.1.4.2 Threat hunting & incident detection
- 6.3.1.4.3 Cyber risk & exposure assessment
- 6.3.1.5 Training & support
- 6.3.2 MANAGED SERVICES
- 6.3.2.1 Adoption of tailored security strategies and continuous risk assessments to drive market
- 6.3.2.2 Managed detection & Response
- 6.3.2.3 Threat Intelligence as a Service
- 6.3.1 PROFESSIONAL SERVICES
7 THREAT INTELLIGENCE MARKET, BY APPLICATION
- 7.1 INTRODUCTION
- 7.1.1 APPLICATION: THREAT INTELLIGENCE MARKET DRIVERS
- 7.2 FRAUD & FINANCIAL CRIME DETECTION
- 7.2.1 INCREASING CYBER FRAUD, PAYMENT FRAUD, AND IDENTITY THEFT TO DRIVE DEPLOYMENT OF AI/ML-POWERED DETECTION SYSTEMS
- 7.3 THREAT HUNTING
- 7.3.1 GROWING SOPHISTICATION OF ATTACKS AND TARGETED APT CAMPAIGNS TO BOOST MARKET
- 7.4 INSIDER THREAT DETECTION
- 7.4.1 ESCALATING CYBER INCIDENTS AND BREACH COMPLEXITY TO DRIVE ADOPTION OF AUTOMATED AND EXPERT-LED RESPONSE FRAMEWORKS
- 7.5 INCIDENT RESPONSE
- 7.5.1 PERSISTENT INSIDER RISKS IN REMOTE AND HYBRID WORK ENVIRONMENTS TO DRIVE DEPLOYMENT OF BEHAVIOR ANALYTICS
- 7.6 RISK & COMPLIANCE MANAGEMENT
- 7.6.1 EXPANDING REGULATORY MANDATES TO DRIVE IMPLEMENTATION OF INTEGRATED RISK AND COMPLIANCE PLATFORMS
- 7.7 OTHER APPLICATIONS
8 THREAT INTELLIGENCE MARKET, BY DEPLOYMENT MODE
- 8.1 INTRODUCTION
- 8.1.1 DEPLOYMENT MODE: THREAT INTELLIGENCE MARKET DRIVERS
- 8.2 CLOUD
- 8.2.1 COST-EFFECTIVENESS AND EASE OF SECURING APPLICATIONS ON CLOUD TO BOOST MARKET
- 8.3 ON-PREMISES
- 8.3.1 COMPLETE CONTROL OVER PLATFORMS, SYSTEMS, AND DATA TO BOOST DEMAND FOR ON-PREMISES SOLUTIONS
- 8.4 HYBRID
- 8.4.1 PHASED CLOUD MIGRATION TO DRIVE DEMAND FOR HYBRID XDR UNIFIED SECURITY
9 THREAT INTELLIGENCE MARKET, BY TYPE
- 9.1 INTRODUCTION
- 9.2 STRATEGIC
- 9.2.1 RISING ADVANCED PERSISTENT THREATS TO BOOST DEMAND FOR ACTIONABLE INTELLIGENCE
- 9.3 OPERATIONAL
- 9.3.1 ESCALATING INSIDER THREATS TO DRIVE DEMAND FOR OPERATIONAL THREAT INTELLIGENCE IN ANOMALY DETECTION
- 9.4 TACTICAL
- 9.4.1 INCREASING SPEED OF CYBERATTACKS TO BOOST ADOPTION OF REAL-TIME TACTICAL FEEDS
- 9.5 TECHNICAL
- 9.5.1 AI-GENERATED MALWARE TO DRIVE NEED FOR DEEPER TECHNICAL ANALYSIS
10 THREAT INTELLIGENCE MARKET, BY ORGANIZATION SIZE
- 10.1 INTRODUCTION
- 10.1.1 ORGANIZATION SIZE: THREAT INTELLIGENCE MARKET DRIVERS
- 10.2 LARGE ENTERPRISES
- 10.2.1 SURGING DEMAND FOR EFFECTIVE MANAGEMENT OF BUSINESS APPLICATIONS TO BOOST MARKET
- 10.3 SMALL & MEDIUM-SIZED ENTERPRISES
- 10.3.1 ADOPTION OF REMOTE WORK TO CREATE DEMAND FOR INTELLIGENCE-DRIVEN MONITORING SOLUTIONS
11 THREAT INTELLIGENCE MARKET, BY VERTICAL
- 11.1 INTRODUCTION
- 11.1.1 VERTICAL: THREAT INTELLIGENCE MARKET DRIVERS
- 11.2 BANKING, FINANCIAL SERVICES, & INSURANCE
- 11.2.1 RAPID GROWTH OF DIGITAL BANKING, MOBILE WALLETS, AND FINTECH TO DRIVE MARKET
- 11.3 GOVERNMENT
- 11.3.1 PROTECTION OF CRITICAL INFRASTRUCTURE AND SENSITIVE CITIZEN DATA TO BOOST TIP ADOPTION
- 11.4 DEFENSE & INTELLIGENCE
- 11.4.1 PROTECTION OF CLASSIFIED DATA, SATELLITE SYSTEMS, AND MILITARY COMMUNICATIONS TO BOOST ADOPTION
- 11.5 HEALTHCARE
- 11.5.1 RISING RANSOMWARE AND DATA BREACH INCIDENTS TARGETING HOSPITALS AND CLINICS TO DRIVE MARKET
- 11.6 RETAIL
- 11.6.1 E-COMMERCE FRAUD, PAYMENT THEFT, AND BOT ATTACKS TO DRIVE MARKET
- 11.7 TRAVEL, AVIATION, & LOGISTICS
- 11.7.1 RISING RANSOMWARE ATTACKS ON AIRLINES AND LOGISTICS TO BOOST DEMAND FOR THREAT INTELLIGENCE SYSTEMS
- 11.8 IT, ITES, & TELECOM
- 11.8.1 RAPID DIGITAL TRANSFORMATION ACROSS IT & ITES TO DRIVE MARKET
- 11.9 ENERGY & INDUSTRIAL
- 11.9.1 INCREASING CYBERATTACKS ON OT AND ICS SYSTEMS TO FUEL ADOPTION OF TIP SYSTEMS
- 11.10 MEDIA & ENTERTAINMENT
- 11.10.1 INCREASING DDOS ATTACKS ON STREAMING PLATFORMS TO BOOST ADOPTION OF THREAT INTELLIGENCE SOLUTIONS
- 11.11 OTHER VERTICALS
12 THREAT INTELLIGENCE MARKET, BY REGION
- 12.1 INTRODUCTION
- 12.2 NORTH AMERICA
- 12.2.1 NORTH AMERICA: MARKET DRIVERS
- 12.2.2 NORTH AMERICA: MACROECONOMIC OUTLOOK
- 12.2.3 US
- 12.2.3.1 Rising regulatory and compliance pressures to drive broader adoption of threat intelligence solutions
- 12.2.4 CANADA
- 12.2.4.1 Rising awareness among SMEs and large enterprises of reputational and financial risks from cyber incidents
- 12.3 EUROPE
- 12.3.1 EUROPE: MARKET DRIVERS
- 12.3.2 EUROPE: MACROECONOMIC OUTLOOK
- 12.3.3 UK
- 12.3.3.1 Growing demand for automated threat detection and real-time intelligence platforms to drive market
- 12.3.4 GERMANY
- 12.3.4.1 Rising awareness among businesses and public institutions of cyber risks and reputational impact to drive market
- 12.3.5 FRANCE
- 12.3.5.1 Rising cyberattacks and data breaches to drive adoption of advanced security solutions
- 12.3.6 ITALY
- 12.3.6.1 Digitalization in public and private sectors to increase exposure to cyber threats and advanced security solutions
- 12.3.7 REST OF EUROPE
- 12.4 ASIA PACIFIC
- 12.4.1 ASIA PACIFIC: MARKET DRIVERS
- 12.4.2 ASIA PACIFIC: MACROECONOMIC OUTLOOK
- 12.4.3 CHINA
- 12.4.3.1 Growing sophistication of AI-driven malware, phishing, and social engineering attacks to drive market
- 12.4.4 JAPAN
- 12.4.4.1 Expansion of public-private collaboration and intelligence-sharing initiatives to drive market
- 12.4.5 INDIA
- 12.4.5.1 Rapid digital transformation and fintech expansion to drive market
- 12.4.6 SINGAPORE
- 12.4.6.1 Growing cross-industry collaboration to counter transnational cybercrime
- 12.4.7 REST OF ASIA PACIFIC
- 12.5 MIDDLE EAST & AFRICA
- 12.5.1 MIDDLE EAST & AFRICA: MARKET DRIVERS
- 12.5.2 MIDDLE EAST & AFRICA: MACROECONOMIC OUTLOOK
- 12.5.3 MIDDLE EAST
- 12.5.3.1 Regional conflicts and state-sponsored campaigns to increase sophistication and frequency of cyberattacks
- 12.5.3.2 KSA
- 12.5.3.3 UAE
- 12.5.3.4 Rest of Middle East
- 12.5.4 AFRICA
- 12.5.4.1 Regional alliances and intelligence-sharing initiatives to counter cross-border cybercrime
- 12.6 LATIN AMERICA
- 12.6.1 LATIN AMERICA: MARKET DRIVERS
- 12.6.2 LATIN AMERICA: MACROECONOMIC OUTLOOK
- 12.6.3 BRAZIL
- 12.6.3.1 Rising cyber-attacks to drive demand for threat intelligence solutions
- 12.6.4 MEXICO
- 12.6.4.1 Implementation of cybersecurity laws and sector-specific mandates to drive adoption of structured threat intelligence
- 12.6.5 REST OF LATIN AMERICA
13 COMPETITIVE LANDSCAPE
- 13.1 OVERVIEW
- 13.2 KEY PLAYER STRATEGIES/RIGHT TO WIN
- 13.3 REVENUE ANALYSIS, 2021-2024
- 13.4 MARKET SHARE ANALYSIS, 2024
- 13.5 PRODUCT/BRAND COMPARISON
- 13.6 COMPANY VALUATION AND FINANCIAL METRICS, 2025
- 13.7 COMPANY EVALUATION MATRIX: KEY PLAYERS, 2024
- 13.7.1 STARS
- 13.7.2 EMERGING LEADERS
- 13.7.3 PERVASIVE PLAYERS
- 13.7.4 PARTICIPANTS
- 13.7.5 COMPANY FOOTPRINT: KEY PLAYERS, 2024
- 13.7.5.1 Company footprint
- 13.7.5.2 Region footprint
- 13.7.5.3 Offering footprint
- 13.7.5.4 Deployment mode footprint
- 13.7.5.5 Vertical footprint
- 13.8 COMPANY EVALUATION MATRIX: STARTUPS/SMES, 2024
- 13.8.1 PROGRESSIVE COMPANIES
- 13.8.2 RESPONSIVE COMPANIES
- 13.8.3 DYNAMIC COMPANIES
- 13.8.4 STARTING BLOCKS
- 13.8.5 COMPETITIVE BENCHMARKING: STARTUPS/SMES, 2024
- 13.8.5.1 Detailed list of key startups/SMEs
- 13.8.5.2 Competitive benchmarking of key startups/SMEs
- 13.9 COMPETITIVE SCENARIO
- 13.9.1 PRODUCT LAUNCHES/DEVELOPMENTS
- 13.9.2 DEALS
14 COMPANY PROFILE
- 14.1 KEY PLAYERS
- 14.1.1 PALO ALTO NETWORKS
- 14.1.1.1 Business overview
- 14.1.1.2 Products/Solutions/Services offered
- 14.1.1.3 Recent developments
- 14.1.1.3.1 Product launches/developments
- 14.1.1.3.2 Deals
- 14.1.1.4 MnM view
- 14.1.1.4.1 Key strengths
- 14.1.1.4.2 Strategic choices
- 14.1.1.4.3 Weaknesses and competitive threats
- 14.1.2 CROWDSTRIKE
- 14.1.2.1 Business overview
- 14.1.2.2 Products/Solutions/Services offered
- 14.1.2.3 Recent developments
- 14.1.2.3.1 Product launches/developments
- 14.1.2.3.2 Deals
- 14.1.2.4 MnM view
- 14.1.2.4.1 Key strengths
- 14.1.2.4.2 Strategic choices
- 14.1.2.4.3 Weaknesses and competitive threats
- 14.1.3 IBM
- 14.1.3.1 Business overview
- 14.1.3.2 Products/Solutions/Services offered
- 14.1.3.3 Recent developments
- 14.1.3.3.1 Product launches/developments
- 14.1.3.3.2 Deals
- 14.1.3.4 MnM view
- 14.1.3.4.1 Key strengths
- 14.1.3.4.2 Strategic choices
- 14.1.3.4.3 Weaknesses and competitive threats
- 14.1.4 CISCO
- 14.1.4.1 Business overview
- 14.1.4.2 Products/Solutions/Services offered
- 14.1.4.3 Recent developments
- 14.1.4.3.1 Deals
- 14.1.4.4 MnM view
- 14.1.4.4.1 Key strengths
- 14.1.4.4.2 Strategic choices
- 14.1.4.4.3 Weaknesses and competitive threats
- 14.1.5 GOOGLE
- 14.1.5.1 Business overview
- 14.1.5.2 Products/Solutions/Services offered
- 14.1.5.3 Recent developments
- 14.1.5.3.1 Product launches/developments
- 14.1.5.3.2 Deals
- 14.1.5.4 MnM view
- 14.1.5.4.1 Key strengths
- 14.1.5.4.2 Strategic choices
- 14.1.5.4.3 Weaknesses and competitive threats
- 14.1.6 FORTINET
- 14.1.6.1 Business overview
- 14.1.6.2 Products/Solutions/Services offered
- 14.1.6.3 Recent developments
- 14.1.6.3.1 Deals
- 14.1.7 CHECK POINT
- 14.1.7.1 Business overview
- 14.1.7.2 Products/Solutions/Services offered
- 14.1.7.3 Recent developments
- 14.1.7.3.1 Product launches/developments
- 14.1.7.3.2 Deals
- 14.1.8 TRELLIX
- 14.1.8.1 Business overview
- 14.1.8.2 Products/Solutions/Services offered
- 14.1.8.3 Recent developments
- 14.1.8.3.1 Product launches/developments
- 14.1.8.3.2 Deals
- 14.1.8.3.3 Expansions
- 14.1.9 RAPID7
- 14.1.9.1 Business overview
- 14.1.9.2 Products/Solutions/Services offered
- 14.1.9.3 Recent developments
- 14.1.9.3.1 Product launches/developments
- 14.1.9.3.2 Deals
- 14.1.10 RECORDED FUTURE
- 14.1.10.1 Business overview
- 14.1.10.2 Products/Solutions/Services offered
- 14.1.10.3 Recent developments
- 14.1.10.3.1 Deals
- 14.1.11 GROUP-IB
- 14.1.11.1 Business overview
- 14.1.11.2 Products/Solutions/Services offered
- 14.1.11.3 Recent developments
- 14.1.11.3.1 Deals
- 14.1.12 KASPERSKY
- 14.1.12.1 Business overview
- 14.1.12.2 Products/Solutions/Services offered
- 14.1.12.3 Recent developments
- 14.1.12.3.1 Product launches/developments
- 14.1.12.3.2 Deals
- 14.1.13 ANOMALI
- 14.1.13.1 Business overview
- 14.1.13.2 Products/Solutions/Services offered
- 14.1.13.3 Recent developments
- 14.1.13.3.1 Product launches/developments
- 14.1.13.3.2 Deals
- 14.1.14 CPX
- 14.1.14.1 Business overview
- 14.1.14.2 Products/Solutions/Services offered
- 14.1.14.3 Recent developments
- 14.1.14.3.1 Deals
- 14.1.15 KELA
- 14.1.15.1 Business overview
- 14.1.15.2 Products/Solutions/Services offered
- 14.1.15.3 Recent developments
- 14.1.15.3.1 Product launches
- 14.1.15.3.2 Deals
- 14.1.16 ZEROFOX
- 14.1.17 ORANGE
- 14.1.18 RESECURITY
- 14.1.19 HELP AG
- 14.1.20 GATEWATCHER
- 14.1.21 CYBLE
- 14.1.22 CYBERINT
- 14.1.23 SOCRADAR
- 14.1.24 THREATCONNECT
- 14.1.25 QUOINTELLIGENCE
- 14.1.26 THREATMON
- 14.1.27 SECURITY PACT
- 14.1.28 SECURIUM SOLUTIONS
- 14.1.29 FLASHPOINT
- 14.1.30 RELIAQUEST
- 14.1.31 THREAT QUOTIENT
- 14.1.1 PALO ALTO NETWORKS
15 ADJACENT MARKETS
- 15.1 INTRODUCTION
- 15.1.1 LIMITATIONS
- 15.2 CYBERSECURITY MARKET
- 15.3 SECURITY AND VULNERABILITY MARKET
16 APPENDIX
- 16.1 DISCUSSION GUIDE
- 16.2 KNOWLEDGESTORE: MARKETSANDMARKETS' SUBSCRIPTION PORTAL
- 16.3 AVAILABLE CUSTOMIZATIONS
- 16.4 RELATED REPORTS
- 16.5 AUTHOR DETAILS



















