
|
시장보고서
상품코드
1887991
네트워크 보안 시장(-2030년) : 솔루션(방화벽 및 차세대 방화벽, 보안 웹 게이트웨이, 통합 위협 관리, 네트워크 검출 및 대응, 네트워크 액세스 제어), 네트워크 환경(브랜치, 캠퍼스, 데이터센터)별Network Security Market By Solution (Firewall/Next Generation Firewall, Secure Web Gateways, Unified Threat Management, Network Detection & Response, Network Access Control), Network Environment (Branch, Campus, Data Center)- Global Forecast to 2030 |
||||||
세계의 네트워크 보안 시장 규모는 예측 기간 동안 CAGR 7.2%로 성장하여 2025년 845억 달러에서 2030년까지 1,197억 달러에 이를 것으로 전망됩니다.
이 시장의 성장은 하이브리드 네트워크, 클라우드 워크로드, 암호화 트래픽을 목표로 하는 사이버 공격의 빈도와 고도화가 진행되고 있기 때문에 조직은 경계 방어와 내부 방어를 모두 강화할 필요가 있습니다.
| 조사 범위 | |
|---|---|
| 조사 대상 기간 | 2019-2030년 |
| 기준 연도 | 2024년 |
| 예측 기간 | 2025-2030년 |
| 단위 | 가치(달러) |
| 부문 | 솔루션, 서비스, 배포 형태, 조직 규모, 네트워크 환경, 산업, 지역 |
| 대상 지역 | 북미, 유럽, 아시아태평양, 중동, 아프리카, 라틴아메리카 |
또한 BYOD(개인 소유 기기의 업무 이용)의 확대 동향에 따라 개인 디바이스가 기업 환경에 접속됨으로써 기업의 공격 대상 영역이 넓어져, 엄격한 액세스 제어, 지속적인 감시, 고도의 위협 대책의 실시가 필요하게 되었습니다. 이러한 요인들이 결합되어 산업 전반에 차세대 네트워크 보안 솔루션의 배치가 가속화되고 있습니다.

"네트워크 환경별로는 데이터센터 부문이 예측 기간 동안 최대 시장 규모를 차지할 전망"
이는 데이터센터가 민감한 워크로드의 대부분, 대규모 구조화/비구조화 데이터, 가상화 환경 및 미션 크리티컬 용도를 수용하기 때문입니다. 기업이 비즈니스를 통합하고, 서버를 가상화하고, 하이브리드 클라우드 전략을 채택함에 따라, 데이터센터는 지능형 지속적 위협(APT), 내부자 위협, 횡방향 이동 공격, 데이터 유출, DDoS 공격, 애플리케이션 계층 침해 등 공격자에게 높은 가치의 목표가 됩니다. 이러한 자산을 보호하기 위해 조직은 세분화, 마이크로 세분화, 침입 감지 및 방지, 차세대 방화벽, 보안 액세스 제어 및 지속적인 모니터링과 같은 강력한 보안 조치를 구현합니다. 가동 시간 확보, 규정 준수, 데이터 기밀성 및 성능 최적화의 중요성으로 인해 데이터센터 보안이 핵심 위치를 유지합니다. 리스크와 가치가 집중되어 있기 때문에 데이터센터 네트워크 보안은 네트워크 보안 투자에서 계속해서 가장 큰 점유율을 유지할 것으로 예측됩니다.
"산업별로는 의료 및 생명과학 분야가 예측 기간 중에 가장 높은 CAGR을 기록할 전망"
의료 및 생명 과학 분야는 디지털화의 진전, 데이터 프라이버시법 등의 규제 압력, 원격 의료의 전개, 클라우드 기반의 환자 데이터 관리, 의료기기의 상호 연결성(IoMT) 증가에 의해 가장 빠르게 성장하고 있는 섹터입니다. 병원, 연구소, 연구 기관은 기밀성이 높은 환자 데이터, 지적 재산, 미션 크리티컬 시스템을 다룹니다. 랜섬웨어 공격, 데이터 침해, 업무 중단 위험의 빈발화에 따라 암호화, 제로 트러스트 액세스, 보안 네트워크 세분화, 클라우드 보안, 지속적인 모니터링 등의 고급 보안 대책의 배치가 필수적입니다. 의료기관이 근대화를 진행하고, 클라우드 기반의 기록 시스템으로 이행해, 세계에 제휴함에 따라, 확장성, 신뢰성 및 컴플라이언스를 갖춘 네트워크 보안이 필요해, 수요가 급증하고 있습니다. 이로써 의료 및 생명과학 분야는 네트워크 보안 시장에서 가장 성장이 현저한 분야로 자리매김하고 있습니다.
"전개 형태별로는 On-Premise 부문이 예측 기간 동안 시장 점유율에서 주도적 입장을 유지할 전망"
On-Premise 배포는 네트워크 보안 분야에서 여전히 주류 배포 형태입니다. 많은 조직, 특히 대기업, 정부 기관 및 규제 산업은 보안 인프라, 데이터 저장 위치, 성능 및 대기 시간을 완전히 제어하는 것을 선호하기 때문입니다. On-Premise 환경에서 조직은 레거시 시스템, 내부 네트워크 및 기존 인프라와 보안 도구를 긴밀하게 통합할 수 있습니다. 설정을 사용자 정의하고, 엄격한 액세스 정책을 적용하고, 내부 거버넌스 규칙을 준수하는 세분화를 수행할 수 있습니다. 은행, 금융, 정부 등의 컴플라이언스 중심 분야에서는 데이터 주권 및 규제 요구 사항에 따라 기밀 데이터를 현장에 보관해야 하는 경우가 많습니다. 또한 On-Premise 배포는 클라우드와 관련된 잠재적인 지연, 가시성 및 공급업체 문제를 제거합니다. 이러한 요인으로 인해 많은 기업들이 On-Premise 보안 인프라에 계속 의존하고 있으며, On-Premise가 최대 배포 모드 부문으로서의 지위를 유지하고 있습니다.
본 보고서에서는 세계 네트워크 보안 시장을 조사했으며, 시장 개요, 시장 성장에 대한 각종 영향요인 분석, 기술 및 특허 동향, 법규제 환경, 사례 연구, 시장 규모 추이와 예측, 각종 구분, 지역/주요 국가별 상세 분석, 경쟁 구도, 주요 기업 프로파일 등을 정리했습니다.
자주 묻는 질문
목차
제1장 서론
제2장 조사 방법
제3장 주요 요약
제4장 중요 인사이트
제5장 시장 개요
- 시장 역학
- 성장 촉진요인
- 억제요인
- 기회
- 과제
- 미충족 요구와 화이트 스페이스
- 관련 시장 및 이업종과의 분야 횡단적 기회
- Tier 1/2/3 기업의 전략적 움직임
제6장 산업 동향
- Porter's Five Forces 분석
- 거시경제지표
- 밸류체인 분석
- 생태계 분석
- 가격 분석
- 무역 분석
- 2025-2026년 주요 회의 및 이벤트
- 고객의 비즈니스에 영향을 미치는 동향/혁신
- 투자 및 자금조달 시나리오
- 사례 연구 분석
- 2025년 미국 관세의 영향 - 네트워크 보안 시장
제7장 기술, 특허, 디지털, AI 전개에 의한 전략적 혁신
- 주요 신기술
- 방화벽 및 차세대 방화벽
- 침입 감지 및 방지 시스템
- 가상 사설망
- AI/머신러닝
- 보완적 기술
- 보안정보 이벤트 관리(SIEM)
- 네트워크 세분화
- 위협 인텔리전스
- 보안 액세스 서비스 엣지
- 제로 트러스트 네트워크 액세스
- 기술/제품 로드맵
- 특허 분석
- 미래의 응용
- AI/생성형 AI가 네트워크 보안 시장에 미치는 영향
제8장 규제 상황
- 지역 규제 및 규정 준수
제9장 소비자 동향과 구매 행동
- 의사결정 프로세스
- 이해관계자와 구매평가기준
- 채용 장벽과 내부 과제
- 다양한 최종 사용자 산업의 미충족 요구
제10장 네트워크 보안 시장 : 솔루션별
- 방화벽 및 차세대 방화벽
- 가상 사설망
- 네트워크 액세스 제어
- 데이터 유출 방지
- 침입 감지 및 방지 시스템
- 보안 웹 게이트웨이
- 분산형 서비스 거부 공격(DDOS) 완화
- 통합 위협 관리
- 네트워크 검출 및 응답
제11장 네트워크 보안 시장 : 서비스별
- 전문 서비스
- 설계, 컨설팅, 구현
- 리스크 및 위협 평가
- 트레이닝 및 교육
- 지원 및 유지 보수
- 매니지드 서비스
제12장 네트워크 보안 시장 : 네트워크 환경별
- 브랜치 네트워크 보안
- 캠퍼스 네트워크 보안
- 데이터센터 네트워크 보안
제13장 네트워크 보안 시장 : 전개 형태별
- On-Premise
- 클라우드
- 하이브리드
제14장 네트워크 보안 시장 : 조직 규모별
- 대기업
- 중소기업
제15장 네트워크 보안 시장 : 산업별
- 은행, 금융서비스 및 보험(BFSI)
- 정부
- 헬스케어 및 생명과학
- 항공우주 및 방위
- 제조
- IT 및 ITES
- 소매 및 E커머스
- 에너지 및 유틸리티
- 통신
- 수송 및 물류
- 미디어 및 엔터테인먼트
- 기타
제16장 네트워크 보안 시장 : 지역별
- 북미
- 시장 성장 촉진요인
- 미국
- 캐나다
- 유럽
- 시장 성장 촉진요인
- 영국
- 독일
- 프랑스
- 이탈리아
- 기타
- 아시아태평양
- 시장 성장 촉진요인
- 중국
- 일본
- 인도
- 싱가포르
- 기타
- 중동 및 아프리카
- 시장 성장 촉진요인
- 중동
- 기타
- 아프리카
- 라틴아메리카
- 브라질
- 멕시코
- 기타
제17장 경쟁 구도
- 주요 진입기업의 전략/강점
- 수익 분석
- 시장 점유율 분석
- 브랜드/제품 비교
- 기업평가와 재무지표
- 기업 평가 매트릭스 : 주요 기업
- 기업 평가 매트릭스 : 스타트업/중소기업
- 경쟁 시나리오
제18장 기업 프로파일
- 주요 기업
- PALO ALTO NETWORKS
- CISCO
- FORTINET
- CHECK POINT
- TREND MICRO
- VERIZON
- IBM
- BROADCOM
- JUNIPER NETWORKS
- AKAMAI
- NETSKOPE
- MICROSOFT
- CROWDSTRIKE
- HUAWEI
- BARRACUDA NETWORKS
- ZSCALER
- TRELLIX
- CLOUDFLARE
- 기타 기업
- AMAZON WEB SERVICES
- OPENTEXT
- SONICWALL
- FORCEPOINT
- SOPHOS
- ZYXEL NETWORKS
- NORDLAYER
- CATO NETWORKS
- HILLSTONE NETWORKS
- VERSA NETWORKS
- WIJUNGLE
- CYNET
- SECNAP
- NOMIOS
- EASI
- GAJSHIELD
- STELLAR CYBER
- STAMUS NETWORKS
- CORELIGHT
- NETSCOUT
- FIDELIS SECURITY
제19장 부록
JHS 25.12.26The network security market is projected to grow from USD 84.50 billion in 2025 to USD 119.70 billion by 2030 at a Compound Annual Growth Rate (CAGR) of 7.2% during the forecast period. The market is driven by the increasing frequency and sophistication of cyberattacks targeting hybrid networks, cloud workloads, and encrypted traffic, prompting organizations to strengthen both perimeter and internal defenses.
| Scope of the Report | |
|---|---|
| Years Considered for the Study | 2019-2030 |
| Base Year | 2024 |
| Forecast Period | 2025-2030 |
| Units Considered | Value (USD Million/ Billion) |
| Segments | Solution, Service, Deployment Mode, Organization Size, Network Environment, Vertical, and Region |
| Regions covered | North America, Europe, Asia Pacific, Middle East & Africa, Latin America |
At the same time, the growing BYOD trend is expanding enterprise attack surfaces as personal devices connect to corporate environments, necessitating the implementation of strict access controls, continuous monitoring, and advanced threat prevention. Together, these factors accelerate the adoption of next-generation network security solutions across industries.
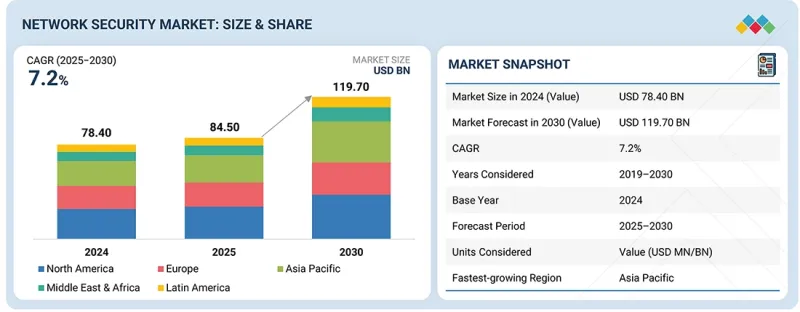
"By network environment, the data center network security segment is expected to hold the largest market size during the forecast period."
Data center network security is expected to be the largest segment in the network environment because data centers house the bulk of sensitive workloads, large volumes of structured/unstructured data, virtualized environments, and mission-critical applications. As enterprises consolidate operations, virtualize servers, and adopt hybrid cloud strategies, data centers become high-value targets for attackers, including advanced persistent threats, insider threats, and lateral movement attacks, as well as data exfiltration, DDoS, and application-layer breaches. To safeguard these assets, organizations deploy robust security measures, including segmentation, micro-segmentation, intrusion detection/prevention, next-generation firewalls, secure access controls, and continuous monitoring. The importance of uptime, regulatory compliance, data confidentiality, and performance optimization ensures that data-center security remains central. Given the concentration of risk and value, data center network security continues to command the largest share of network security investments.
"By vertical, the cloud segment is projected to register the highest CAGR during the forecast period."
The healthcare and life sciences vertical is the fastest-growing sector due to rising digitization, regulatory pressure such as data privacy laws, the adoption of telemedicine, cloud-based patient data management, and the increasing interconnectedness of medical devices (IoMT - Internet of Medical Things). Hospitals, laboratories, and research institutions handle sensitive patient data, intellectual property, and mission-critical systems. The growing frequency of ransomware attacks, data breaches, and disruption risks necessitates the implementation of advanced security measures, including encryption, zero-trust access, secure network segmentation, cloud security, and continuous monitoring. As healthcare organizations modernize, move to cloud-based record systems, and collaborate globally, they require scalable, reliable, and compliant network security, prompting a surging demand and positioning the healthcare & life sciences sector as the fastest-growing vertical in the network security market.
By deployment mode, the on-premises segment is expected to lead in terms of market share during the forecast period.
On-premises deployment remains the dominant deployment mode in network security because many organizations, especially large enterprises, government institutions, and regulated industries, prefer full control over their security infrastructure, data residency, performance, and latency. On-premises setups allow organizations to integrate security tools tightly with legacy systems, internal networks, and existing infrastructure. They can customize configurations, enforce strict access policies, and apply segmentation in ways that suit internal governance rules. For compliance-driven sectors such as banking, finance, and government, data sovereignty and regulatory mandates often require sensitive data to remain on-site. Additionally, on-premises deployments eliminate potential cloud-related latency, visibility, or vendor dependency issues. Because of these factors, many enterprises continue to rely on on-premises security infrastructure, sustaining its position as the largest deployment mode segment.
Breakdown of Primaries
The study draws insights from a range of industry experts, including component suppliers, Tier 1 companies, and OEMs. The break-up of the primaries is as follows:
- By Company Type: Tier 1 - 40%, Tier 2 - 35%, and Tier 3 - 25%
- By Designation: Directors - 45%, Managers - 35%, Others - 20%
- By Region: North America - 35%, Europe - 30%, Asia Pacific - 25%, Middle East & Africa - 5%, Latin America - 5%
Major vendors in the network security market include Cisco (US), Palo Alto Networks (US), Fortinet (US), Check Point (US), Trend Micro (Japan), Verizon (US), IBM (US), Broadcom (US), Juniper Networks (US), Akamai (US), Netskope (US), Microsoft (US), CrowdStrike (US), Zscaler (US), Cloudflare (US), AWS (US), OpenText (Canada), Hillstone Networks (US), Barracuda Networks (US), Huawei (China), Trellix (US), SonicWall (US), Forcepoint (US), Sophos (UK), Ivanti (US), Extreme Networks (US), Zyxel Networks (Taiwan), Cato Networks (Israel), NordLaver (US), Versa Networks (US), WiJungle (India), Cynet (US), SECNAP Network Security (US), Nomios (Netherlands), easi (Belgium), GajShield (India), Stellar Cyber (US), NETSCOUT (US), and Fidelis Security (US).
The study includes an in-depth competitive analysis of the key players in the network security market, their company profiles, recent developments, and key market strategies.
Research Coverage
The report segments the network security market and forecasts its size based on solution (firewall/next-generation firewall, virtual private network, network access control, data loss prevention, intrusion detection/intrusion prevention systems, secure web gateways, distributed denial-of-service mitigation, unified threat management, network detection & response, and other solutions such as URL/content filtering, web/DNS filtering, and vulnerability scanning), service (professional services-including design, consulting & implementation, risk & threat assessment, training & education, support & maintenance-and managed services), network environment (branch, campus, and data center network security), deployment mode (cloud, on-premises, and hybrid), organization size (large enterprises and small & medium-sized enterprises), and vertical (BFSI, government, healthcare & life sciences, manufacturing, IT & ITeS, retail & e-commerce, energy & utilities, telecommunications, transportation & logistics, media & entertainment, aerospace & defense, and other verticals such as education, construction, real estate, and travel & hospitality).
The study also includes an in-depth competitive analysis of the market's key players, their company profiles, key observations related to product and business offerings, recent developments, and key market strategies.
Key Benefits of Buying the Report
The report will help market leaders/new entrants with information on the closest approximations of revenue numbers for the overall network security market and its subsegments. This report will help stakeholders understand the competitive landscape and gain valuable insights to better position their businesses and plan suitable go-to-market strategies. The report also helps stakeholders understand the market pulse and provides information on key market drivers, restraints, challenges, and opportunities.
The report provides insights into the following pointers:
- Analysis of key drivers (Increasing frequency and sophistication of cyberattacks, Growing BYOD trend necessitating network security measures, Rising cloud adoption and remote work trend), restraints (High implementation costs, Shortage of skilled cybersecurity professionals), opportunities (Simplified management and enhanced protection achieved using secure access service edge framework, Implementation of zero-trust approach in network security), and challenges (Lack of awareness and training concerning network security technologies, Integration complexities)
- Product Development/Innovation: Detailed insights on upcoming technologies, research & development activities, and new product & service launches in the network security market
- Market Development: Comprehensive information about lucrative markets - the report analyses the network security market across varied regions
- Market Diversification: Exhaustive information about new products & services, untapped geographies, recent developments, and investments in the network security market
- Competitive Assessment: In-depth assessment of market shares, growth strategies, and service offerings of leading players in the network security market, including Palo Alto Networks (US), Cisco (US), CrowdStrike (US), Check Point (Israel), and Trend Micro (Japan)
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 STUDY OBJECTIVES
- 1.2 MARKET DEFINITION
- 1.3 STUDY SCOPE AND SEGMENTATION
- 1.3.1 MARKETS COVERED AND REGIONAL SCOPE
- 1.3.2 INCLUSIONS AND EXCLUSIONS
- 1.3.3 YEARS CONSIDERED
- 1.3.4 CURRENCY CONSIDERED
- 1.3.5 STAKEHOLDERS
- 1.3.6 SUMMARY OF CHANGES
2 RESEARCH METHODOLOGY
- 2.1 RESEARCH DATA
- 2.1.1 SECONDARY DATA
- 2.1.2 PRIMARY DATA
- 2.1.2.1 Breakup of primaries
- 2.1.2.2 Key industry insights
- 2.2 MARKET SIZE ESTIMATION
- 2.2.1 TOP-DOWN APPROACH
- 2.2.2 BOTTOM-UP APPROACH
- 2.3 MARKET DATA TRIANGULATION
- 2.4 FACTOR ANALYSIS
- 2.5 RESEARCH ASSUMPTIONS
- 2.6 RESEARCH LIMITATIONS
3 EXECUTIVE SUMMARY
- 3.1 KEY INSIGHTS AND MARKET HIGHLIGHTS
- 3.2 KEY MARKET PARTICIPANTS: SHARE INSIGHTS & STRATEGIC DEVELOPMENTS
- 3.3 DISRUPTIVE TRENDS SHAPING MARKET
- 3.4 HIGH-GROWTH SEGMENTS & EMERGING FRONTIERS
- 3.5 SNAPSHOT: GLOBAL MARKET SIZE, GROWTH RATE, AND FORECAST
4 PREMIUM INSIGHTS
- 4.1 ATTRACTIVE OPPORTUNITIES FOR PLAYERS IN NETWORK SECURITY MARKET
- 4.2 NETWORK SECURITY MARKET, BY SOLUTION
- 4.3 NETWORK SECURITY MARKET, BY SERVICE
- 4.4 NETWORK SECURITY MARKET, BY NETWORK ENVIRONMENT
- 4.5 NETWORK SECURITY MARKET, BY ORGANIZATION SIZE
- 4.6 NETWORK SECURITY MARKET, BY DEPLOYMENT MODE
- 4.7 NETWORK SECURITY MARKET, BY VERTICAL
- 4.8 NETWORK SECURITY MARKET, BY REGION
5 MARKET OVERVIEW
- 5.1 INTRODUCTION
- 5.2 MARKET DYNAMICS
- 5.2.1 DRIVERS
- 5.2.1.1 Increasing frequency and sophistication of cyberattacks
- 5.2.1.2 Growing BYOD trend necessitating network security measures
- 5.2.1.3 Increased cloud adoption and remote work trend
- 5.2.2 RESTRAINTS
- 5.2.2.1 High implementation costs
- 5.2.2.2 Shortage of skilled cybersecurity professionals
- 5.2.3 OPPORTUNITIES
- 5.2.3.1 Simplified management and enhanced protection using SASE framework
- 5.2.3.2 Implementation of zero-trust approach in network security
- 5.2.4 CHALLENGES
- 5.2.4.1 Lack of awareness and training on network security technologies
- 5.2.4.2 Integration complexities
- 5.2.1 DRIVERS
- 5.3 UNMET NEEDS AND WHITE SPACES
- 5.4 INTERCONNECTED MARKETS AND CROSS-SECTOR OPPORTUNITIES
- 5.4.1 BFSI
- 5.4.2 HEALTHCARE & LIFE SCIENCES
- 5.4.3 GOVERNMENT
- 5.4.4 IT & ITES
- 5.4.5 TELECOMMUNICATIONS
- 5.5 STRATEGIC MOVES BY TIER 1/2/3 PLAYERS
- 5.5.1 STRATEGIC TRENDS
- 5.5.1.1 Rise of secure access service edge (SASE)
- 5.5.1.2 Adoption of zero trust network principles
- 5.5.1.3 AI-driven network analytics and automated threat response
- 5.5.1.4 Convergence of networking and security platforms
- 5.5.1.5 Privacy-preserving network inspection and encrypted traffic visibility
- 5.5.1 STRATEGIC TRENDS
6 INDUSTRY TRENDS
- 6.1 PORTER'S FIVE FORCES ANALYSIS
- 6.1.1 THREAT OF NEW ENTRANTS
- 6.1.2 THREAT OF SUBSTITUTES
- 6.1.3 BARGAINING POWER OF SUPPLIERS
- 6.1.4 BARGAINING POWER OF BUYERS
- 6.1.5 INTENSITY OF COMPETITIVE RIVALRY
- 6.2 MACROECONOMIC INDICATORS
- 6.2.1 INTRODUCTION
- 6.2.2 GDP TRENDS AND FORECAST
- 6.2.3 TRENDS IN GLOBAL ICT INDUSTRY
- 6.2.4 TRENDS IN GLOBAL CYBERSECURITY INDUSTRY
- 6.3 VALUE CHAIN ANALYSIS
- 6.3.1 PLANNING AND DESIGNING
- 6.3.2 NETWORK SECURITY SOLUTION AND SERVICE PROVIDERS
- 6.3.3 SYSTEM INTEGRATION
- 6.3.4 DISTRIBUTION/RESELLERS/VALUE-ADDED RESELLERS
- 6.3.5 END USERS
- 6.4 ECOSYSTEM ANALYSIS
- 6.5 PRICING ANALYSIS
- 6.5.1 AVERAGE SELLING PRICE, BY SOLUTION, 2025
- 6.5.2 INDICATIVE PRICING ANALYSIS OF PRODUCTS, BY VENDOR, 2025
- 6.6 TRADE ANALYSIS
- 6.6.1 IMPORT SCENARIO (HS CODE 8517)
- 6.6.2 EXPORT SCENARIO (HS CODE 8517)
- 6.7 KEY CONFERENCES & EVENTS, 2025-2026
- 6.8 TRENDS/DISRUPTIONS IMPACTING CUSTOMERS' BUSINESSES
- 6.9 INVESTMENT AND FUNDING SCENARIO
- 6.10 CASE STUDY ANALYSIS
- 6.10.1 JUNIPER NETWORKS HELPED BEELINE ENHANCE EFFICIENCY AND CYBERSECURITY
- 6.10.2 AMANA BANK BUILT A ROBUST AND EASILY MANAGEABLE CYBERSECURITY INFRASTRUCTURE USING SOPHOS' TECHNOLOGIES
- 6.10.3 FORCEPOINT HELPED BURGER KING SECURE SCALABLE NETWORK TRANSITION
- 6.11 IMPACT OF 2025 US TARIFFS-NETWORK SECURITY MARKET
- 6.11.1 INTRODUCTION
- 6.11.2 KEY TARIFF RATES
- 6.11.3 PRICE IMPACT ANALYSIS
- 6.11.4 IMPACT ON COUNTRIES/REGIONS
- 6.11.4.1 North America
- 6.11.4.2 Europe
- 6.11.4.3 Asia Pacific
- 6.11.5 IMPACT ON END-USE INDUSTRIES
7 STRATEGIC DISRUPTION THROUGH TECHNOLOGY, PATENTS, DIGITAL, AND AI ADOPTION
- 7.1 KEY EMERGING TECHNOLOGIES
- 7.1.1 FIREWALLS/NEXT-GENERATION FIREWALLS
- 7.1.2 INTRUSION DETECTION SYSTEMS/INTRUSION PREVENTION SYSTEMS
- 7.1.3 VIRTUAL PRIVATE NETWORKS
- 7.1.4 AI/ML
- 7.2 COMPLEMENTARY TECHNOLOGIES
- 7.2.1 SECURITY INFORMATION AND EVENT MANAGEMENT (SIEM)
- 7.2.2 NETWORK SEGMENTATION
- 7.2.3 THREAT INTELLIGENCE
- 7.2.4 SECURE ACCESS SERVICE EDGE
- 7.2.5 ZERO TRUST NETWORK ACCESS
- 7.3 TECHNOLOGY/PRODUCT ROADMAP
- 7.3.1 SHORT-TERM (2025-2027) | FOUNDATION & EARLY COMMERCIALIZATION
- 7.3.2 MID-TERM (2027-2030) | EXPANSION & STANDARDIZATION
- 7.3.3 LONG-TERM (2030-2035+) | GLOBAL CONSOLIDATION & INTELLIGENT SECURITY ECOSYSTEMS
- 7.4 PATENT ANALYSIS
- 7.5 FUTURE APPLICATIONS
- 7.5.1 ZERO-TRUST ARCHITECTURES: BEYOND-PERIMETER NETWORK SECURITY
- 7.5.2 AI-POWERED THREAT DETECTION & AUTONOMOUS RESPONSE
- 7.5.3 SECURE ACCESS SERVICE EDGE (SASE) & SECURITY SERVICE EDGE (SSE)
- 7.5.4 OT & ICS CYBERSECURITY FOR CRITICAL INFRASTRUCTURE
- 7.5.5 5G/6G SECURITY & ULTRA-CONNECTED NETWORK DEFENSE
- 7.6 IMPACT OF AI/GEN AI ON NETWORK SECURITY MARKET
- 7.6.1 BEST PRACTICES IN NETWORK SECURITY MARKET
- 7.6.2 CASE STUDIES OF AI IMPLEMENTATION IN THE NETWORK SECURITY MARKET
- 7.6.3 INTERCONNECTED ADJACENT ECOSYSTEM AND IMPACT ON MARKET PLAYERS
- 7.6.4 CLIENTS' READINESS TO ADOPT GENERATIVE AI IN NETWORK SECURITY MARKET
8 REGULATORY LANDSCAPE
- 8.1 REGIONAL REGULATIONS AND COMPLIANCE
- 8.1.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- 8.1.2 INDUSTRY STANDARDS
9 CONSUMER LANDSCAPE & BUYER BEHAVIOR
- 9.1 DECISION-MAKING PROCESS
- 9.2 BUYER STAKEHOLDERS AND BUYING EVALUATION CRITERIA
- 9.2.1 KEY STAKEHOLDERS IN BUYING PROCESS
- 9.2.2 BUYING CRITERIA
- 9.3 ADOPTION BARRIERS & INTERNAL CHALLENGES
- 9.4 UNMET NEEDS FROM VARIOUS END-USE INDUSTRIES
10 NETWORK SECURITY MARKET, BY SOLUTION
- 10.1 INTRODUCTION
- 10.1.1 SOLUTIONS: NETWORK SECURITY MARKET DRIVERS
- 10.2 FIREWALL/NEXT-GENERATION FIREWALL
- 10.2.1 NEED FOR SIMPLIFICATION AND AUTOMATION OF ENTERPRISE-GRADE SECURITY WITH CENTRALIZED MANAGEMENT ACROSS DISTRIBUTED NETWORKS TO DRIVE MARKET
- 10.3 VIRTUAL PRIVATE NETWORK
- 10.3.1 INCREASING DEMAND FOR MAINTAINING DATA SECURITY, PRIVACY, AND NETWORK INTEGRITY TO DRIVE MARKET
- 10.4 NETWORK ACCESS CONTROL
- 10.4.1 INCREASING NEED FOR STREAMLINING AUTHENTICATION PROCESS, REDUCING TIME AND COSTS TO FUEL MARKET GROWTH
- 10.5 DATA LOSS PREVENTION
- 10.5.1 DATA LOSS PREVENTION SOLUTIONS TO ENHANCE INTERNAL SECURITY AND MAINTAIN REGULATORY COMPLIANCE
- 10.6 INTRUSION DETECTION SYSTEM/INTRUSION PREVENTION SYSTEM
- 10.6.1 INCREASING DEMAND FOR ROBUST NETWORK SECURITY TO BOOST MARKET
- 10.7 SECURE WEB GATEWAY
- 10.7.1 SURGING DEMAND FOR SAFE INTERNET ACCESS TO DRIVE MARKET
- 10.8 DISTRIBUTED DENIAL-OF-SERVICE MITIGATION
- 10.8.1 RISING NEED TO PROTECT CONFIDENTIALITY, INTEGRITY, AND AVAILABILITY OF RESOURCES TO FUEL MARKET GROWTH
- 10.9 UNIFIED THREAT MANAGEMENT
- 10.9.1 RISING POPULARITY OF UNIFIED THREAT MANAGEMENT SOLUTIONS TO DRIVE MARKET
- 10.10 NETWORK DETECTION AND RESPONSE
- 10.10.1 DELIVERS THREAT DETECTION, INCIDENT RESPONSE, AND FORENSICS FROM A UNIFIED NETWORK-CENTRIC PERSPECTIVE
11 NETWORK SECURITY MARKET, BY SERVICE
- 11.1 INTRODUCTION
- 11.1.1 SERVICES: NETWORK SECURITY MARKET DRIVERS
- 11.2 PROFESSIONAL SERVICES
- 11.2.1 NEED FOR RAPID RESPONSE TO BREACHES AND EXTERNAL SUPPORT TO DRIVE ADOPTION
- 11.2.2 DESIGN, CONSULTING, AND IMPLEMENTATION
- 11.2.3 RISK & THREAT ASSESSMENT
- 11.2.4 TRAINING & EDUCATION
- 11.2.5 SUPPORT & MAINTENANCE
- 11.3 MANAGED SERVICES
- 11.3.1 INCREASING DEMAND FOR SPECIALIZED SECURITY SERVICES TO BOOST MARKET GROWTH
12 NETWORK SECURITY MARKET, BY NETWORK ENVIRONMENT
- 12.1 INTRODUCTION
- 12.1.1 NETWORK ENVIRONMENT: NETWORK SECURITY MARKET DRIVERS
- 12.2 BRANCH NETWORK SECURITY
- 12.2.1 SURGING NEED FOR PROTECTION OF SENSITIVE INFORMATION AND ENFORCING OPERATIONAL CONTINUITY TO DRIVE MARKET
- 12.3 CAMPUS NETWORK SECURITY
- 12.3.1 STRENGTHENED VISIBILITY AND SAFE CONNECTIVITY ACROSS LARGE DISTRIBUTED FACILITIES TO DRIVE MARKET
- 12.4 DATA CENTER NETWORK SECURITY
- 12.4.1 INCREASING NEED FOR ENSURING CRITICAL ASSET AVAILABILITY, RELIABILITY, AND CONFIDENTIALITY TO ACCELERATE MARKET GROWTH
13 NETWORK SECURITY MARKET, BY DEPLOYMENT MODE
- 13.1 INTRODUCTION
- 13.1.1 DEPLOYMENT MODE: NETWORK SECURITY MARKET DRIVERS
- 13.2 ON-PREMISES
- 13.2.1 ON-PREMISES DEPLOYMENT TO HELP MAINTAIN COMPLIANCE, PROTECT DATA, AND CUSTOMIZE SECURITY CONFIGURATIONS
- 13.3 CLOUD
- 13.3.1 COST-EFFECTIVENESS AND EASE OF MAINTENANCE TO BOOST DEMAND FOR CLOUD-BASED SOLUTIONS
- 13.4 HYBRID
- 13.4.1 HYBRID APPROACH TO OFFER DATA SECURITY, FLEXIBILITY, COST-EFFICIENCY, AND THE RAPID DEPLOYMENT CAPABILITIES OF CLOUD SERVICES
14 NETWORK SECURITY MARKET, BY ORGANIZATION SIZE
- 14.1 INTRODUCTION
- 14.1.1 ORGANIZATION SIZE: NETWORK SECURITY MARKET DRIVERS
- 14.2 LARGE ENTERPRISES
- 14.2.1 INCREASING NEED FOR EFFECTIVE SECURITY MANAGEMENT TO BOOST MARKET
- 14.3 SMALL & MEDIUM-SIZED ENTERPRISES
- 14.3.1 INCREASING CYBER THREATS, REGULATORY COMPLIANCE REQUIREMENTS, AND NEED FOR PROTECTION OF SENSITIVE DATA TO DRIVE MARKET
15 NETWORK SECURITY MARKET, BY VERTICAL
- 15.1 INTRODUCTION
- 15.1.1 VERTICAL: NETWORK SECURITY MARKET DRIVERS
- 15.2 BANKING, FINANCIAL SERVICES, AND INSURANCE (BFSI)
- 15.2.1 INCREASING DEMAND FOR MAINTAINING COMPETITIVE EDGE, REDUCING COSTS, AND IMPROVING CUSTOMER EXPERIENCE WITH VALUE-ADDED SERVICES TO DRIVE MARKET
- 15.3 GOVERNMENT
- 15.3.1 NETWORK SECURITY SOLUTIONS TO HELP IMPROVE SECURITY OF CRITICAL INFORMATION AND REDUCE THREAT OF UNAUTHORIZED ACCESS
- 15.4 HEALTHCARE & LIFE SCIENCES
- 15.4.1 RISING USE OF NETWORK SECURITY SOLUTIONS AND INCREASING AWARENESS OF REGULATORY COMPLIANCE TO DRIVE MARKET
- 15.5 AEROSPACE & DEFENSE
- 15.5.1 SURGING DEMAND FOR OPERATIONAL EFFECTIVENESS AND NATIONAL SECURITY TO PROPEL MARKET
- 15.6 MANUFACTURING
- 15.6.1 INCREASING DEMAND FOR EFFICIENT REAL-TIME DATA ACCESS AND SECURE NETWORK CONNECTIVITY TO PROPEL MARKET
- 15.7 IT & ITES
- 15.7.1 INCREASING SHIFT TOWARD HYBRID AND REMOTE WORK MODELS TO HEIGHTEN DEMAND FOR SECURE REMOTE ACCESS SOLUTIONS
- 15.8 RETAIL & ECOMMERCE
- 15.8.1 RISING NETWORK-BASED CYBER-ATTACKS AND DATA THEFT ACTIVITIES TO BOOST ADOPTION OF NETWORK SECURITY SOLUTIONS
- 15.9 ENERGY & UTILITIES
- 15.9.1 NEED TO STRENGTHEN NETWORK SECURITY AND REDUCE COMPLEXITIES TO FUEL ADOPTION
- 15.10 TELECOMMUNICATIONS
- 15.10.1 NEED TO PROTECT VAST AND COMPLEX COMMUNICATION NETWORKS FROM CYBER THREATS TO PROPEL MARKET
- 15.11 TRANSPORTATION & LOGISTICS
- 15.11.1 STRENGTHENING TRANSPORTATION AND LOGISTICS OPERATIONS THROUGH ENHANCED NETWORK SECURITY TO PROPEL MARKET
- 15.12 MEDIA & ENTERTAINMENT
- 15.12.1 NETWORK SECURITY MEASURES TO SAFEGUARD AGAINST UNAUTHORIZED ACCESS, ENSURE THE INTEGRITY OF CONTENT, AND PROTECT CONSUMER PRIVACY
- 15.13 OTHER VERTICALS
16 NETWORK SECURITY MARKET, BY REGION
- 16.1 INTRODUCTION
- 16.2 NORTH AMERICA
- 16.2.1 NORTH AMERICA: NETWORK SECURITY MARKET DRIVERS
- 16.2.2 US
- 16.2.2.1 Increasing network attacks, cyber threats, and evolving regulatory norms to boost market
- 16.2.3 CANADA
- 16.2.3.1 Rapid digitalization and government initiatives to boost market
- 16.3 EUROPE
- 16.3.1 EUROPE: NETWORK SECURITY MARKET DRIVERS
- 16.3.2 UK
- 16.3.2.1 Surging demand for bolstering cybersecurity to drive market
- 16.3.3 GERMANY
- 16.3.3.1 Increasing cybercrimes and sophisticated cyberattacks to boost market
- 16.3.4 FRANCE
- 16.3.4.1 Compliance with stringent EU regulations to drive adoption of comprehensive security frameworks
- 16.3.5 ITALY
- 16.3.5.1 Adoption of modern network security solutions to protect digital infrastructure to drive market
- 16.3.6 REST OF EUROPE
- 16.4 ASIA PACIFIC
- 16.4.1 ASIA PACIFIC: NETWORK SECURITY MARKET DRIVERS
- 16.4.2 CHINA
- 16.4.2.1 Rapid digitalization and growing importance of safeguarding country's expansive digital economy to boost market
- 16.4.3 JAPAN
- 16.4.3.1 Intricate cyberattacks to drive adoption of network security solutions
- 16.4.4 INDIA
- 16.4.4.1 Increased internet penetration, improved telecom services, and government initiatives to drive market
- 16.4.5 SINGAPORE
- 16.4.5.1 Growing emphasis on cybersecurity measures and increasing investments in advanced network security measures to foster market growth
- 16.4.6 REST OF ASIA PACIFIC
- 16.5 MIDDLE EAST & AFRICA
- 16.5.1 MIDDLE EAST & AFRICA: NETWORK SECURITY MARKET DRIVERS
- 16.5.2 MIDDLE EAST
- 16.5.2.1 Rapid expansion of connected systems accelerating the demand for comprehensive network security solutions
- 16.5.2.2 GCC
- 16.5.2.3 UAE
- 16.5.2.3.1 Digital transformation and increasing cyber threats to drive adoption of modern network security solutions
- 16.5.2.4 KSA
- 16.5.2.4.1 Digital transformation and evolving threat landscape to boost market
- 16.5.2.5 Rest of GCC countries
- 16.5.3 REST OF MIDDLE EAST
- 16.5.4 AFRICA
- 16.5.4.1 Rising cyber risks and increasing digital adoption driving the growth of network security market
- 16.6 LATIN AMERICA
- 16.6.1 BRAZIL
- 16.6.1.1 Rising DDoS attacks in Brazil to propel market growth
- 16.6.2 MEXICO
- 16.6.2.1 Increasing demand for protection of sensitive information to bolster market growth
- 16.6.3 REST OF LATIN AMERICA
- 16.6.1 BRAZIL
17 COMPETITIVE LANDSCAPE
- 17.1 KEY PLAYER STRATEGIES/RIGHT TO WIN
- 17.2 REVENUE ANALYSIS
- 17.3 MARKET SHARE ANALYSIS
- 17.4 BRAND/PRODUCT COMPARISON
- 17.5 COMPANY VALUATION AND FINANCIAL METRICS
- 17.5.1 COMPANY VALUATION, 2025
- 17.5.2 FINANCIAL METRICS USING EV/EBITDA, 2025
- 17.6 COMPANY EVALUATION MATRIX: KEY PLAYERS, 2024
- 17.6.1 STARS
- 17.6.2 EMERGING LEADERS
- 17.6.3 PERVASIVE PLAYERS
- 17.6.4 PARTICIPANTS
- 17.6.5 COMPANY FOOTPRINT: KEY PLAYERS, 2024
- 17.6.5.1 Company footprint
- 17.6.5.2 Region footprint
- 17.6.5.3 Solution footprint
- 17.6.5.4 Service footprint
- 17.6.5.5 Vertical footprint
- 17.7 COMPANY EVALUATION MATRIX: STARTUPS/SMES, 2024
- 17.7.1 PROGRESSIVE COMPANIES
- 17.7.2 RESPONSIVE COMPANIES
- 17.7.3 DYNAMIC COMPANIES
- 17.7.4 STARTING BLOCKS
- 17.7.5 COMPETITIVE BENCHMARKING: STARTUPS/SMES, 2024
- 17.7.5.1 Detailed list of key startups/SMEs
- 17.7.5.2 Competitive benchmarking of key startups/SMEs
- 17.8 COMPETITIVE SCENARIO
- 17.8.1 PRODUCT LAUNCHES AND ENHANCEMENTS
- 17.8.2 DEALS
18 COMPANY PROFILES
- 18.1 MAJOR PLAYERS
- 18.1.1 PALO ALTO NETWORKS
- 18.1.1.1 Business overview
- 18.1.1.2 Products/Solutions/Services offered
- 18.1.1.3 Recent developments
- 18.1.1.3.1 Product launches and enhancements
- 18.1.1.3.2 Deals
- 18.1.1.4 MnM view
- 18.1.1.4.1 Key strengths
- 18.1.1.4.2 Strategic choices made
- 18.1.1.4.3 Weaknesses and competitive threats
- 18.1.2 CISCO
- 18.1.2.1 Business overview
- 18.1.2.2 Products/Solutions/Services offered
- 18.1.2.3 Recent developments
- 18.1.2.3.1 Product launches and enhancements
- 18.1.2.3.2 Deals
- 18.1.2.4 MnM view
- 18.1.2.4.1 Key strengths
- 18.1.2.4.2 Strategic choices made
- 18.1.2.4.3 Weaknesses and competitive threats
- 18.1.3 FORTINET
- 18.1.3.1 Business overview
- 18.1.3.2 Products/Solutions/Services offered
- 18.1.3.3 Recent developments
- 18.1.3.3.1 Product launches and enhancements
- 18.1.3.3.2 Deals
- 18.1.3.4 MnM view
- 18.1.3.4.1 Key strengths
- 18.1.3.4.2 Strategic choices made
- 18.1.3.4.3 Weaknesses and competitive threats
- 18.1.4 CHECK POINT
- 18.1.4.1 Business overview
- 18.1.4.2 Products/Solutions/Services offered
- 18.1.4.3 Recent developments
- 18.1.4.3.1 Product launches
- 18.1.4.3.2 Deals
- 18.1.4.4 MnM view
- 18.1.4.4.1 Key strengths
- 18.1.4.4.2 Strategic choices made
- 18.1.4.4.3 Weaknesses and competitive threats
- 18.1.5 TREND MICRO
- 18.1.5.1 Business overview
- 18.1.5.2 Products/Solutions/Services offered
- 18.1.5.3 Recent developments
- 18.1.5.3.1 Product launches
- 18.1.5.3.2 Deals
- 18.1.5.4 MnM view
- 18.1.5.4.1 Key strengths
- 18.1.5.4.2 Strategic choices made
- 18.1.5.4.3 Weaknesses and competitive threats
- 18.1.6 VERIZON
- 18.1.6.1 Business overview
- 18.1.6.2 Products/Solutions/Services offered
- 18.1.6.3 Recent developments
- 18.1.6.3.1 Product launches
- 18.1.6.3.2 Deals
- 18.1.7 IBM
- 18.1.7.1 Business overview
- 18.1.7.2 Products/Solutions/Services offered
- 18.1.7.3 Recent developments
- 18.1.7.3.1 Product enhancements
- 18.1.7.3.2 Deals
- 18.1.8 BROADCOM
- 18.1.8.1 Business overview
- 18.1.8.2 Products/Solutions/Services offered
- 18.1.8.3 Recent developments
- 18.1.8.3.1 Product launches and enhancements
- 18.1.8.3.2 Deals
- 18.1.9 JUNIPER NETWORKS
- 18.1.9.1 Business overview
- 18.1.9.2 Products/Solutions/Services offered
- 18.1.9.3 Recent developments
- 18.1.9.3.1 Product launches and enhancements
- 18.1.9.3.2 Deals
- 18.1.10 AKAMAI
- 18.1.10.1 Business overview
- 18.1.10.2 Products/Solutions/Services offered
- 18.1.10.3 Recent developments
- 18.1.10.3.1 Product launches
- 18.1.10.3.2 Deals
- 18.1.11 NETSKOPE
- 18.1.11.1 Business overview
- 18.1.11.2 Products/Solutions/Services offered
- 18.1.11.3 Recent developments
- 18.1.11.3.1 Product launches
- 18.1.11.3.2 Deals
- 18.1.12 MICROSOFT
- 18.1.12.1 Business overview
- 18.1.12.2 Products/Solutions/Services offered
- 18.1.12.3 Recent developments
- 18.1.12.3.1 Deals
- 18.1.13 CROWDSTRIKE
- 18.1.13.1 Business overview
- 18.1.13.2 Products/Solutions/Services offered
- 18.1.13.3 Recent developments
- 18.1.13.3.1 Deals
- 18.1.14 HUAWEI
- 18.1.14.1 Business overview
- 18.1.14.2 Products/Solutions/Services offered
- 18.1.14.3 Recent developments
- 18.1.14.3.1 Product launches
- 18.1.14.3.2 Deals
- 18.1.15 BARRACUDA NETWORKS
- 18.1.15.1 Business overview
- 18.1.15.2 Products/Solutions/Services offered
- 18.1.15.3 Recent developments
- 18.1.15.3.1 Product launches and enhancements
- 18.1.15.3.2 Deals
- 18.1.16 ZSCALER
- 18.1.16.1 Business overview
- 18.1.16.2 Products/Solutions/Services offered
- 18.1.16.3 Recent developments
- 18.1.16.3.1 Product launches
- 18.1.16.3.2 Deals
- 18.1.17 TRELLIX
- 18.1.17.1 Business overview
- 18.1.17.2 Products/Solutions/Services offered
- 18.1.17.3 Recent developments
- 18.1.17.3.1 Product launches
- 18.1.17.3.2 Deals
- 18.1.18 CLOUDFLARE
- 18.1.18.1 Business overview
- 18.1.18.2 Products/Solutions/Services offered
- 18.1.18.3 Recent developments
- 18.1.18.3.1 Product launches and enhancements
- 18.1.18.3.2 Deals
- 18.1.1 PALO ALTO NETWORKS
- 18.2 OTHER PLAYERS
- 18.2.1 AMAZON WEB SERVICES
- 18.2.2 OPENTEXT
- 18.2.3 SONICWALL
- 18.2.4 FORCEPOINT
- 18.2.5 SOPHOS
- 18.2.6 ZYXEL NETWORKS
- 18.2.7 NORDLAYER
- 18.2.8 CATO NETWORKS
- 18.2.9 HILLSTONE NETWORKS
- 18.2.10 VERSA NETWORKS
- 18.2.11 WIJUNGLE
- 18.2.12 CYNET
- 18.2.13 SECNAP
- 18.2.14 NOMIOS
- 18.2.15 EASI
- 18.2.16 GAJSHIELD
- 18.2.17 STELLAR CYBER
- 18.2.18 STAMUS NETWORKS
- 18.2.19 CORELIGHT
- 18.2.20 NETSCOUT
- 18.2.21 FIDELIS SECURITY
19 APPENDIX
- 19.1 DISCUSSION GUIDE
- 19.2 KNOWLEDGESTORE: MARKETSANDMARKETS' SUBSCRIPTION PORTAL
- 19.3 CUSTOMIZATION OPTIONS
- 19.4 RELATED REPORTS
- 19.5 AUTHOR DETAILS



















