
|
시장보고서
상품코드
1849828
국방 사이버 보안 : 시장 점유율 분석, 산업 동향, 통계, 성장 예측(2025-2030년)Defense Cyber Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
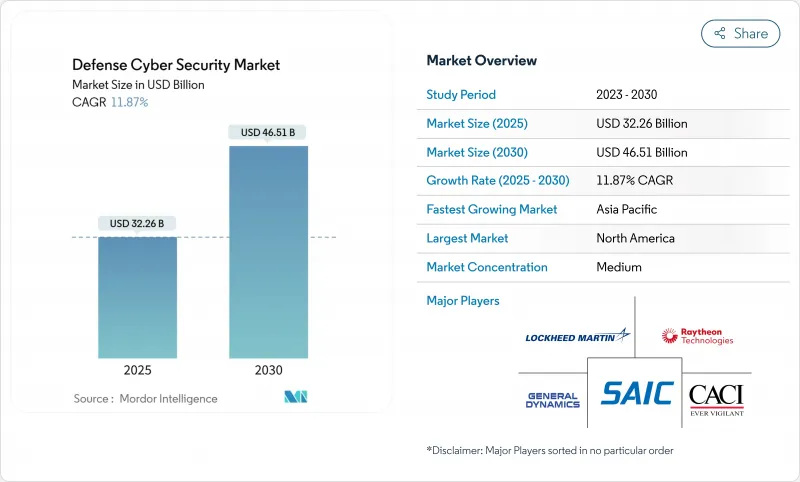
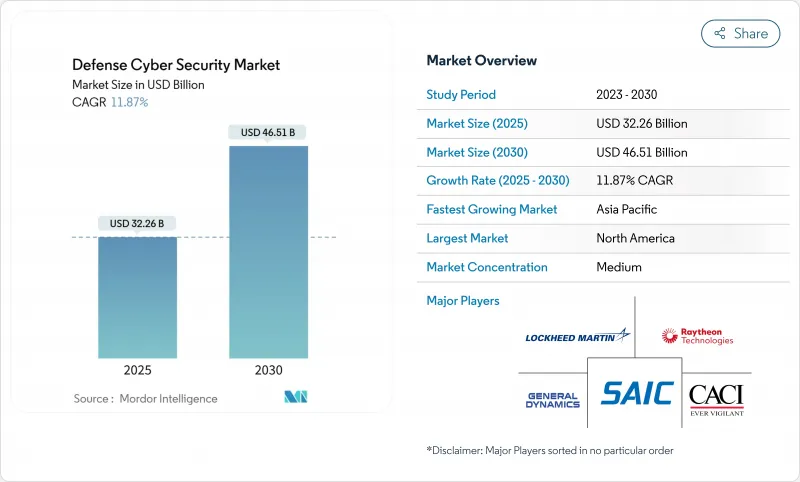
국방 사이버 보안 시장 규모는 2025년에 322억 6,000만 달러로 평가되었고, 2030년에 465억 1,000만 달러에 이를 것으로 예측되고 있습니다.
이는 이 분야가 국가안보시스템 전체에 걸쳐 '절대 신뢰하지 말고 항상 검증하라' 아키텍처로 전환되면서 CAGR은 11.87%를 나타낼 전망입니다.
제로 트러스트 정책의 급속한 제도화, 운영 기술의 무기화, 위성 및 소프트웨어 정의 네트워크 방위에 대한 압박 증가가 결합되어 사이버 작전은 육·해·공·우주와 동등한 전면전 영역으로 격상되고 있습니다. 미국 국방부(DoD)가 2035년까지 모든 무기 플랫폼에 제로 트러스트를 적용하라는 지침을 발표함에 따라 기업 및 전술 계층 모두에서 작동하는 보안 솔루션에 대한 수요가 증폭되고 있습니다. 동시에 JADC2 및 GCIA와 같은 프로그램 하에서 합동 전 영역 작전으로의 전환은 분쟁 지역에서 실시간 데이터 공유가 가능한 안전한 클라우드-엣지 패브릭에 대한 투자를 촉진하고 있습니다.
세계의 국방 사이버 보안 시장 동향 및 인사이트
아시아의 소프트웨어 정의 및 위성 기반 전장 네트워크의 신속한 배포
아시아태평양 지역 군대는 지휘관이 통신 토폴로지를 몇 초 만에 재구성할 수 있도록 하는 소프트웨어 정의 네트워크를 현장 테스트 중이며, 이는 적군이 우주에서 해안까지 악용할 수 있는 잠재적 공격 경로를 증대시킵니다. 한국의 2024년 교리는 이제 제로 트러스트 보안 구역과 함께 공격적 사이버 옵션을 통합하여 순수 방위적 태세에서 벗어나 지역적 전환을 시사합니다. 일본의 능동적 사이버 방위법은 2027년까지 시행되며, 이상 징후를 포착하기 위해 정부가 중요 인프라 트래픽을 모니터링할 수 있도록 허용하여 국가 감독이 현저히 확대됩니다. 위성 링크와 지상 5G 노드를 결합하면 복원력이 향상되지만, 우주선 원격 측정 데이터가 스푸핑 및 거부 전술에 노출됩니다. 탈리스만 세이버(Talisman Sabre)와 같은 훈련은 사이버 목표를 물리적 전쟁 게임에 점점 더 통합하며, 국방 사이버 보안 시장이 광범위한 전력 구조 결정과 어떻게 얽혀 있는지를 강조합니다.
미국 및 파이브 아이즈 국방 조달에 의무화된 제로 트러스트 아키텍처
행정명령 14028호와 국가안보지침 8호는 모든 미국 국가안보 시스템에 제로 트러스트 채택을 의무화하여, 기업 IT부터 전술 무기 제어에 이르기까지 규정 준수 중심 조달을 촉진하고 있습니다. 국방부의 평가 워크플로 자동화는 엄격함을 훼손하지 않으면서 인증 절차를 가속화하며, 이는 수백만 엔드포인트로 확장하기 위한 전제 조건입니다. 파이브 아이즈 상호운용성 조항이 제안 요청서(RFP)에 명시되며, 다국적 보안 승인 기준을 충족하는 업체에 혜택이 주어집니다. 2035년까지 제로 트러스트는 발사 시스템, 항공 전자 장비, 사격 통제망에 적용되어야 하며, 통신 차단 환경에서도 암호화 유연성과 지속적인 신원 확인이 요구됩니다.
단편화된 레거시 플랫폼이 종단 간 암호화 도입을 방해
1990년대에 제작된 무기 체계가 여전히 운용 중이지만, 해당 프로세서와 버스 아키텍처는 성능 저하 없이 현대적 암호화를 처리할 수 없습니다. 각 군종은 여전히 플랫폼별 프로토콜을 유지하여 통합 키 관리 추진을 복잡하게 만든다. 지휘관들은 때로 철저한 암호화보다 임무 가동 시간을 우선시하여 기술적 난관과 맞먹는 문화적 저항을 낳는다. 교체 주기가 수십 년에 달하기 때문에, 주요 계약업체들은 소스 코드 재작성 없이 제로 트러스트 원칙을 개조하는 래퍼 솔루션을 설계해야 하며, 이는 국방 사이버 보안 시장의 틈새이지만 성장하는 분야입니다.
부문 분석
솔루션 부문은 2024년 매출의 67%를 차지했으며, 이는 기업 네트워크의 핵심인 방화벽, 보안 게이트웨이 장비, 위협 인텔리전스 플랫폼에 대한 꾸준한 갱신 계약을 반영합니다. 이러한 우위는 기준 연도 국방 사이버 보안 시장 규모에서 216억 달러로 이어졌습니다. 그러나 서비스 부문은 군 당국이 보안을 일회성 설치가 아닌 지속적인 관행으로 인식함에 따라 11.8%의 연평균 성장률(CAGR)로 더 빠르게 확장되고 있습니다.
컨설팅 팀들은 이제 애자일 소프트웨어 개발 환경 내에 DevSecOps 전문가를 배치하여 코드 파이프라인이 운영 승인 기준을 첫날부터 충족하도록 보장합니다. 관리형 탐지 및 대응 제공업체들은 공군의 글로벌 인프라 전반에서 매일 발생하는 수백만 건의 경보를 분류하며, AI를 활용해 잡음을 억제하고 실행 가능한 위협을 선별합니다. 제로 트러스트 개념, 양자 안전 암호화, 적대적 AI를 다루는 훈련 프로그램이 무기한 공급 계약 하에 민간 아카데미에서 제공되고 있습니다. 이러한 활동은 반복 수익을 창출하고 지출을 서비스 쪽으로 전환시키며, 이로 인해 2030년까지 국방 사이버 보안 시장 내 서비스 비중이 3분의 1로 증가할 전망입니다.
2024년 네트워크 보안은 42%로 여전히 핵심 분야를 차지했으며, 이는 국방 사이버 보안 시장 규모 136억 달러에 해당합니다. 방화벽, 침입방지시스템, 보안 게이트웨이는 여전히 군부대 네트워크를 보호하지만, 클라우드 보안은 연평균 15.7% 성장률로 급속히 확대 중입니다. JADC2는 기밀 클라우드부터 연합군 클라우드, 상용 클라우드에 이르는 다단계 보안 아키텍처를 요구하며, 인프라스트럭처-어즈-코드(IAC)에 맞춤화된 신원 관리, 구성 관리, 데이터 유출 방지 제어 수단의 조달을 강제합니다.
모든 드론, 레이더, 전투 차량이 국방 네트워크의 노드로 변모함에 따라 엔드포인트 및 애플리케이션 보안 부문이 점진적으로 주목받고 있습니다. 양자 난수 생성 및 AI 기반 위협 헌팅은 벤처 캐피털과 EDF(국방전자연구국) 보조금을 유치하는 신흥 하위 부문입니다. 클라우드 환경에서 기존 경계 방위와 컨테이너화된 마이크로서비스를 아우를 수 있는 벤더들이 국방 사이버 보안 시장 점유율을 통합할 것입니다.
지역 분석
북미는 2024년 매출의 38%를 차지하며 선두를 유지했습니다. 이는 의회 예산 배정 과정에서 모든 주요 획득 프로그램에 사이버 보안 항목이 포함되었기 때문입니다. CMMC 2.0과 같은 규정 준수 체제는 주계약업체부터 하위 공급업체에 이르기까지 전체 방위 산업 기반이 입찰 전 통제 조치를 시행하도록 의무화하여 군 고객을 넘어선 잠재 수요를 확대하고 있습니다. 캐나다는 파이브 아이즈(Five Eyes) 상호운용성 유지를 위해 미국 프레임워크를 따르고 있으며, 멕시코의 조달 연계는 국경 간 방위 기술 이전을 통해 추진력을 얻고 있습니다.
아시아태평양 지역은 일본과 한국의 가속화된 사이버 교리, 인도와 호주·미국 간 3자 협력, 분쟁 수로 감시를 위한 동남아시아 함대 현대화 등에 힘입어 2030년까지 연평균 11.4% 성장률을 기록할 전망입니다. 주권 클라우드 의무화와 위성 네트워크 투자가 결합되면서 해당 지역은 방위 사이버 보안 시장에서 전진 배치된 소프트웨어 정의 역량을 목표로 하는 벤더들에게 가장 역동적인 무대가 되고 있습니다.
유럽은 2021-2027년 유럽방위기금(EDF) 80억 유로(85억 달러) 지원과 NATO 수요 신호와 벤처 캐피털을 결합한 DIANA 가속기 프로그램의 혜택을 받고 있습니다. 유럽투자은행(EIB)이 2025년 6월 안보 기술에 배정할 89억 유로(94억 달러) 규모의 자금 지원은 공공재정 도구가 주권 사이버 복원력 프로젝트에 자본을 집중시키고 있음을 보여줍니다. 한편 중동 및 아프리카 지역은 예산이 우선적으로 물리적 시스템에 할당되면서 건실하지만 낮은 성장률을 기록하고 있으나, NATO 표준 채택으로 잠재 수요가 발생하여 글로벌 통합업체들이 이를 활용하려 하고 있습니다.
기타 혜택 :
- 엑셀 형식 시장 예측(ME) 시트
- 3개월간의 애널리스트 지원
목차
제1장 서론
- 조사의 전제조건과 시장의 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 상황
- 시장 개요
- 시장 성장 촉진요인
- 아시아 지역에서의 소프트웨어 정의 및 위성 기반 전장 네트워크 신속 구축
- 미국 및 파이브 아이즈(Five-Eyes) 국방 조달에서의 제로 트러스트(Zero-Trust) 아키텍처 의무화
- 실시간 OT-IT 보안을 요구하는 디지털 트윈 및 자율 플랫폼 도입 가속화
- 국방 클라우드-엣지 마이그레이션 프로그램(JADC2, GCIA 등)이 보안 데이터 패브릭 지출 촉진
- NATO DIANA 및 EU EDF 자금 지원이 국경 간 사이버 레인지 투자 촉진
- 시장 성장 억제요인
- 단편화된 레거시 플랫폼이 종단 간 암호화 도입 저해
- 기밀 프로젝트에서 지속되는 보안 승인 인재 부족
- 다중 영역 솔루션에 대한 비용 부담이 큰 운영 승인(ATO) 및 인증 주기
- 낮은 자금 우선순위와 효과적인 ROI 지표 부재
- 밸류체인 분석
- 규제 전망
- 기술의 전망
- Porter's Five Forces 분석
- 신규 참가업체의 위협
- 구매자의 협상력
- 공급기업의 협상력
- 대체품의 위협
- 경쟁 기업간 경쟁 관계
- 시장의 거시 경제 동향 평가
제5장 시장 규모와 성장 예측(가치관)
- 컴포넌트별
- 솔루션
- 서비스
- 보안 유형별
- 네트워크 보안
- 엔드포인트 보안
- 애플리케이션 보안
- 클라우드 보안
- 기타 보안 유형
- 전개 모드별
- 온프레미스
- 클라우드와 하이브리드
- 최종 사용자별
- 육군
- 해군
- 공군
- 지역별
- 북미
- 미국
- 캐나다
- 멕시코
- 유럽
- 영국
- 독일
- 프랑스
- 이탈리아
- 스페인
- 기타 유럽
- 아시아태평양
- 중국
- 인도
- 일본
- 한국
- 기타 아시아태평양
- 남미
- 브라질
- 칠레
- 콜롬비아
- 기타 남미
- 중동
- 사우디아라비아
- 아랍에미리트(UAE)
- 이스라엘
- 카타르
- 튀르키예
- 기타 중동
- 아프리카
- 남아프리카
- 나이지리아
- 기타 아프리카
- 북미
제6장 경쟁 구도
- 시장 집중도
- 전략적 움직임(파트너십, 합작 사업, 연구 개발)
- 시장 점유율 분석
- 기업 프로파일
- CACI International Inc.
- SAIC Inc.
- Raytheon Technologies Corp.
- Lockheed Martin Corp.
- General Dynamics Corp.
- L3Harris Technologies Inc.
- BAE Systems plc
- Northrop Grumman Corp.
- Booz Allen Hamilton Holding Corp.
- Leidos Holdings Inc.
- Thales Group
- Airbus Defence and Space
- Leonardo SpA
- QinetiQ Group plc
- Palantir Technologies Inc.
- Darktrace plc
- Viasat Inc.
- IBM Corporation
- DXC Technology
- Rohde and Schwarz Cybersecurity
제7장 시장 기회와 장래의 전망
HBR 25.11.12The Defense cyber security market size stood at USD 32.26 billion in 2025 and is projected to reach USD 46.51 billion by 2030, reflecting an 11.87% CAGR as the sector pivots toward "never-trust, always-verify" architectures across national security systems.
Rapid institutionalization of zero-trust policies, the weaponization of operational technology, and mounting pressure to defend satellite and software-defined networks combine to elevate cyber operations to a full war-fighting domain on par with land, sea, air, and space. Mandates issued by the United States Department of Defense (DoD) to embed zero trust into every weapons platform by 2035 amplify demand for security solutions that operate at both enterprise and tactical echelons. At the same time, the shift to joint, all-domain operations under programs such as JADC2 and GCIA is propelling investment in secure cloud-edge fabrics capable of real-time data sharing in contested theaters.
Global Defense Cyber Security Market Trends and Insights
Rapid Deployment of Software-Defined & Satellite-Based Battlefield Networks in Asia
Asia-Pacific militaries are field-testing software-defined networks that let commanders reconfigure communications topologies in seconds, multiplying potential attack vectors that adversaries can exploit from space to shore. South Korea's 2024 doctrine now integrates offensive cyber options alongside zero-trust secure enclaves, signaling a regional transition from purely defensive postures. Japan's active cyber defense law takes effect by 2027 and permits government monitoring of critical infrastructure traffic to flag anomalies, a marked expansion of state oversight. Coupling satellite links with terrestrial 5G nodes improves resilience, yet exposes spacecraft telemetry to spoofing and denial tactics. Exercises such as Talisman Sabre increasingly weave cyber objectives into kinetic war-games, underscoring how the Defense cyber security market is entwined with broader force-structure decisions.
Mandated Zero-Trust Architectures in U.S. & Five-Eyes Defence Procurement
Executive Order 14028 and National Security Memorandum 8 oblige every U.S. national-security system to embrace zero trust, fueling compliance-driven procurement that extends from enterprise IT to tactical weapon controls. The Pentagon's automation of assessment workflows accelerates accreditation without diluting rigor, a prerequisite for scaling across millions of endpoints. Five Eyes interoperability clauses now appear in request-for-proposal language, rewarding vendors that can satisfy multinational security-clearance thresholds. By 2035, zero trust must permeate launch-systems, avionics, and fire-control chains, demanding cryptographic agility and continuous identity verification even in communications-denied settings.
Fragmented Legacy Platforms Hindering End-to-End Encryption Roll-Out
Weapon systems built in the 1990s remain on duty, yet their processors and buses cannot handle modern cryptography without performance trade-offs. Each service branch still sustains platform-specific protocols, complicating any push for unified key-management. Commanders sometimes prefer mission uptime over exhaustive encryption, creating cultural resistance that matches the technical impasse. Because replacement cycles span decades, prime contractors must architect wrapper solutions that retrofit zero-trust principles without rewriting source code, a niche but growing slice of the Defense cyber security market.
Other drivers and restraints analyzed in the detailed report include:
- Accelerated Digital-Twin & Autonomous Platform Adoption Demanding Real-Time OT-IT Security
- Defense Cloud-Edge Migration Programmes (JADC2, GCIA) Driving Secure Data-Fabric Spend
- Prolonged Security-Cleared Talent Gap in Classified Projects
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Solutions captured 67% revenue in 2024, reflecting steady refresh contracts for firewalls, secure-gateway appliances, and threat-intelligence platforms that anchor enterprise networks. That dominance translated into USD 21.6 billion of the Defense cyber security market size in the base year. Yet services are scaling faster, advancing at 11.8% CAGR, because militaries increasingly view security as a continuous practice rather than a one-off install.
Consulting teams now embed DevSecOps experts inside agile software factories to ensure code pipelines meet authority-to-operate standards from day one. Managed detection and response providers triage millions of daily alerts across the Air Force's global infrastructure, employing AI to suppress noise and elevate actionable threats. Training regimens covering zero-trust concepts, quantum-safe encryption, and adversarial AI are being delivered by private academies under indefinite-delivery contracts. These activities grow recurring revenue and tilt spending toward services, a pattern that will likely lift the Defense cyber security market share of services to one-third by 2030.
Network security remained the anchor at 42% in 2024, equivalent to USD 13.6 billion of the Defense cyber security market size. Firewalls, intrusion-prevention systems, and secure gateways still safeguard garrison networks, but cloud security is streaking ahead at 15.7% CAGR. JADC2 mandates multi-level security architectures that stretch from classified to coalition to commercial clouds, forcing procurement of identity, configuration, and data-loss-prevention controls tailored for infrastructure-as-code.
Endpoint and application security segments gain incremental traction as every drone, radar, and combat vehicle morphs into a node on the defense network. Quantum-random-number-generation and AI-enabled threat hunting are emerging sub-segments attracting venture capital and EDF grants. Vendors capable of spanning traditional perimeter defenses and containerized micro-services in cloud environments will consolidate share in the Defense cyber security market.
The Defense Cyber Security Market is Segmented by Component (Solutions, Services), Security Type (Network Security, Endpoint Security, Application Security, Cloud Security, Other Security Types), Deployment Mode (On-Premises, Cloud and Hybrid), End-User (Land Force, Naval Force. Air Force), and Geography. The Market Forecasts are Provided in Terms of Value (USD).
Geography Analysis
North America retained the lead with 38% revenue in 2024 as congressional appropriations embedded cybersecurity line-items in every major acquisition program. Compliance regimes such as CMMC 2.0 obligate the entire defense industrial base-from primes to sub-tier suppliers-to implement controls before bidding, enlarging addressable demand beyond uniformed customers. Canada follows U.S. frameworks to preserve Five Eyes interoperability, while Mexico's procurement ties gain momentum through cross-border defense technology transfers.
Asia-Pacific is expanding at 11.4% CAGR through 2030 on the strength of accelerated cyber doctrine in Japan and South Korea, India's trilateral partnerships with Australia and the United States, and South-East Asian fleet upgrades designed to monitor contested waterways. Sovereign-cloud mandates coupled with satellite network investments make the region the most dynamic theater for vendors targeting forward-deployed, software-defined capabilities within the Defense cyber security market.
Europe benefits from EUR 8 billion (USD 8.5 billion) in EDF funding for 2021-2027, plus the DIANA accelerator that marries NATO demand signals with venture capital. The European Investment Bank's June 2025 tranche of EUR 8.9 billion (USD 9.4 billion) earmarked for security technologies underlines how public-finance tools are funneling capital into sovereign cyber resilience projects. Meanwhile, the Middle East and Africa register healthy but lower growth as budgets prioritize kinetic systems first; nonetheless, adoption of NATO-aligned standards creates latent demand that global integrators aim to unlock.
- CACI International Inc.
- SAIC Inc.
- Raytheon Technologies Corp.
- Lockheed Martin Corp.
- General Dynamics Corp.
- L3Harris Technologies Inc.
- BAE Systems plc
- Northrop Grumman Corp.
- Booz Allen Hamilton Holding Corp.
- Leidos Holdings Inc.
- Thales Group
- Airbus Defence and Space
- Leonardo S.p.A
- QinetiQ Group plc
- Palantir Technologies Inc.
- Darktrace plc
- Viasat Inc.
- IBM Corporation
- DXC Technology
- Rohde and Schwarz Cybersecurity
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Rapid Deployment of Software-Defined and Satellite-Based Battlefield Networks in Asia
- 4.2.2 Mandated Zero-Trust Architectures in U.S. and Five-Eyes Defence Procurement
- 4.2.3 Accelerated Digital Twin and Autonomous Platform Adoption Demanding Real-Time OT-IT Security
- 4.2.4 Defence Cloud-Edge Migration Programmes (e.g., JADC2, GCIA) Driving Secure Data Fabric Spend
- 4.2.5 NATO DIANA and EU EDF Funding Catalysing Cross-Border Cyber Range Investments
- 4.3 Market Restraints
- 4.3.1 Fragmented Legacy Platforms Hindering End-to-End Encryption Roll-Out
- 4.3.2 Prolonged Security-Cleared Talent Gap in Classified Projects
- 4.3.3 Cost-Heavy Authority-to-Operate (ATO) and Certification Cycles for Multi-Domain Solutions
- 4.3.4 Low Funding Priority and the Lack of Effective ROI Metric
- 4.4 Value Chain Analysis
- 4.5 Regulatory Outlook
- 4.6 Technological Outlook
- 4.7 Porter's Five Forces Analysis
- 4.7.1 Threat of New Entrants
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Bargaining Power of Suppliers
- 4.7.4 Threat of Substitutes
- 4.7.5 Competitive Rivalry
- 4.8 Assessment of Macro Economic Trends on the Market
5 MARKET SIZE AND GROWTH FORECASTS (VALUES)
- 5.1 By Component
- 5.1.1 Solutions
- 5.1.2 Services
- 5.2 By Security Type
- 5.2.1 Network Security
- 5.2.2 Endpoint Security
- 5.2.3 Application Security
- 5.2.4 Cloud Security
- 5.2.5 Other Security Types
- 5.3 By Deployment Mode
- 5.3.1 On-Premises
- 5.3.2 Cloud and Hybrid
- 5.4 By End-User
- 5.4.1 Land Force
- 5.4.2 Naval Force
- 5.4.3 Air Force
- 5.5 By Geography
- 5.5.1 North America
- 5.5.1.1 United States
- 5.5.1.2 Canada
- 5.5.1.3 Mexico
- 5.5.2 Europe
- 5.5.2.1 United Kingdom
- 5.5.2.2 Germany
- 5.5.2.3 France
- 5.5.2.4 Italy
- 5.5.2.5 Spain
- 5.5.2.6 Rest of Europe
- 5.5.3 Asia-Pacific
- 5.5.3.1 China
- 5.5.3.2 India
- 5.5.3.3 Japan
- 5.5.3.4 South Korea
- 5.5.3.5 Rest of Asia-Pacific
- 5.5.4 South America
- 5.5.4.1 Brazil
- 5.5.4.2 Chile
- 5.5.4.3 Colombia
- 5.5.4.4 Rest of South America
- 5.5.5 Middle East
- 5.5.5.1 Saudi Arabia
- 5.5.5.2 United Arab Emirates
- 5.5.5.3 Israel
- 5.5.5.4 Qatar
- 5.5.5.5 Turkey
- 5.5.5.6 Rest of Middle East
- 5.5.6 Africa
- 5.5.6.1 South Africa
- 5.5.6.2 Nigeria
- 5.5.6.3 Rest of Africa
- 5.5.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves (Partnerships, JVs, RandD)
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global Level Overview, Market Level Overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 CACI International Inc.
- 6.4.2 SAIC Inc.
- 6.4.3 Raytheon Technologies Corp.
- 6.4.4 Lockheed Martin Corp.
- 6.4.5 General Dynamics Corp.
- 6.4.6 L3Harris Technologies Inc.
- 6.4.7 BAE Systems plc
- 6.4.8 Northrop Grumman Corp.
- 6.4.9 Booz Allen Hamilton Holding Corp.
- 6.4.10 Leidos Holdings Inc.
- 6.4.11 Thales Group
- 6.4.12 Airbus Defence and Space
- 6.4.13 Leonardo S.p.A
- 6.4.14 QinetiQ Group plc
- 6.4.15 Palantir Technologies Inc.
- 6.4.16 Darktrace plc
- 6.4.17 Viasat Inc.
- 6.4.18 IBM Corporation
- 6.4.19 DXC Technology
- 6.4.20 Rohde and Schwarz Cybersecurity
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-Space and Unmet-Need Assessment














