
|
시장보고서
상품코드
1850346
디셉션 기술 : 시장 점유율 분석, 산업 동향, 통계, 성장 예측(2025-2030년)Deception Technology - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
디셉션 기술 시장은 2025년에 24억 1,000만 달러를 기록하며, 2030년에는 CAGR 13.3%로 45억 달러로 확대될 것으로 예측됩니다.

제로 데이 공격 증가, 인공지능에 의한 깊은 가짜 사기, 클라우드 네이티브 워크로드 확대로 보안 팀은 피해가 발생하기 전에 네트워크 내부의 공격자를 발견하는 조기 경고 컨트롤을 채택해야합니다. 벤더는 현재 제로 트러스트의 마이크로 세분화에 디코이를 짜넣어, ID나 엔드 포인트가 침해되었을 경우에도 기능하는 트립 와이어를 방어측에 제공합니다. 또한 사이버보험사가 보험료 우대의 조건으로서 프로액티브한 횡이동 검지를 요구하고 있기 때문에 수요도 가속하고 있습니다. 북미는 계속 시장을 선도하고 있지만, 아시아태평양에서는 멀티클라우드 도입이 급증하고, 각국의 규제 당국이 정보 유출 통지에 관한 규제를 강화하고 있기 때문에 디셉션 기술 시장은 급속히 기세를 늘리고 있습니다.
세계의 디셉션 기술 시장 동향과 인사이트
제로 데이 익스플로잇과 타겟 APT의 급증
국가에 지원된 집단이 AI로 정찰을 자동화해, 시그니처 베이스의 방어가 적응하는 것보다 빨리 새로운 취약성을 발견. Institute for Security and Technology는 자동화된 정찰이 공격자의 체류 시간을 단축하고 방어자는 재활용 플레이북을 재검토할 수밖에 없습니다고 지적합니다. 디셉션 플랫폼은 호기심을 무기로 믿을 수 있지만 가짜 자산을 삽입합니다. 위협 인텔리전스 피드가 아닌 공격자의 행동을 기반으로 감지를 수행하기 위해 Deception Technology Market은 해시 매칭 제어를 피하는 맞춤형 멀웨어에 대한 내성을 제공합니다. 공급업체는 현재 산업용 제어 시스템과 SaaS API용 디코이를 미리 패키징하고 있으며 공격자가 운영 기술에 중점을 두고 있음을 반영합니다.
확장 클라우드 네이티브 워크로드가 공격 대상을 확장
컨테이너화된 서버리스 용도는 몇 분 안에 스핀업/다운할 수 있으므로 보안 운영 센터는 동서 트래픽을 파악할 수 없습니다. Zscaler는 대규모 언어 모델의 엔드포인트를 모방하는 일반 AI 디코이를 배포하고 공격자를 계측된 샌드박스로 가져옵니다. 디코이는 Kubernetes 네임스페이스 내에서 자동으로 확장되므로 방어자는 기본 마이크로서비스가 변경되어도 지속적인 적용 범위를 얻을 수 있습니다. Deception Technology Market은 클라우드 제공업체의 메타데이터 API를 활용하여 에이전트를 설치하지 않고 가상 사설 클라우드에 트랩을 설치합니다. 조직이 멀티클라우드 전략을 채택함에 따라 교차 제공업체의 미끼 오케스트레이션은 특히 단일 지역에 로그를 집중할 수 없는 규제 업계에서는 구매 기준이 됩니다.
레거시 허니팟에 대한 의존 정착
많은 기업들은 수년 전에 도입된 정적 허니팟을 계속 운영하고 있습니다. 공격자는 현재 프로토콜 습관과 가동 시간 패턴을 통해 이러한 자산의 지문을 만들고 쉽게 우회합니다. 이 썬크 코스트 바이어스는 운영 체제 배너를 변형하거나 자격 증명을 자동으로 회전시킬 수 있는 적응형 디코이로의 업그레이드를 지연시킵니다. 레거시 허니팟은 수작업으로 로그 분석을 요구하며 실제 공격 경로에 집중해야 하는 리소스를 소모합니다. 이러한 도구는 실용적인 경보를 거의 생성하지 않기 때문에 이사회는 ROI를 의심하고 신규 투자를 억제하고 디셉션 기술 시장의 성장을 억제합니다.
부문 분석
2024년 디셉션 기술 시장 점유율의 67.9%는 On-Premise형이며, 컴플라이언스와 포렌식 관리를 위해 높은 상호작용 디코이를 왕관과 같은 시스템 가까이에 두고 싶다는 기업의 요구를 나타냈습니다. 그러나 이 관리는 하드웨어 업데이트 주기와 변경 관리 오버헤드를 초래하여 민첩성을 제한합니다. 클라우드의 도입은 현재 사소한 비율을 차지하고 있지만, 2030년까지 15.2%의 연평균 복합 성장률(CAGR)을 나타낼 예정이며, 이것은 디셉션 기술 시장 내에서 가장 빠른 페이스입니다. 클라우드 기반 콘솔은 몇 분 안에 지역을 가로 지르는 미끼 시스템을 시작하기 때문에 세계 지점 배포에 매력적입니다.
하이브리드 모델은 실용적인 브리지 역할로 등장하며, 팀은 기밀성이 높은 데이터베이스 디코이를 On-Premise에 두면서 분석 및 스케일링 작업을 퍼블릭 클라우드로 오프로드할 수 있습니다. 멀티클라우드 배포가 진행됨에 따라 구매자는 AWS, Azure, Google Cloud를 가로지르는 단일 창 보기를 요청하고 공급자는 ID 페더레이션 및 불변 인프라 블루프린트에 투자하게 됩니다. 이러한 기능을 통해 클라우드 모듈의 디셉션 기술 시장 규모는 확대되어 공유 책임 모델에서도 감사 통제를 충족할 수 있다는 것을 규제에 속하는 부문에 납득시킵니다.
대기업은 2024년에 70.2%의 매출 점유율을 유지해 API 깊이, MITRE ATT&CK와의 무결성, 고급 분석을 고집함으로써 기능 로드맵을 형성했습니다. 그러나 중소기업은 현재 14.9%의 성장률을 기록하고 있으며, 디셉션 기술 시장에서 대기업 지출을 상회하고 있습니다. 자산별로 청구되는 구독 기반 관리형 Deception 서비스는 진입 장벽을 줄이고 소규모 팀의 대역폭에 맞는 선별된 경보를 제공합니다.
클라우드 콘솔은 하드웨어 구매를 필요로 하지 않기 때문에 중소기업은 자본을 직원 의식 향상 프로그램으로 돌려보낼 수 있어 절약 효과가 더욱 높아집니다. 공급업체에게 이 부문의 스케일 효과는 설득력이 있습니다. 수천 명의 중간 규모 고객은 Fortune 500에 이름을 붙이는 소수 기업의 라이선스 수익과 비교할 수 있습니다. 결과적으로 로드맵의 우선순위에는 로우코드 플레이북과 자동 디코이 배치가 포함됩니다. 이 기능은 온보딩을 몇 주에서 몇 시간으로 단축하여 중소기업의 디셉션 기술 시장 규모를 확대하도록 설계된 기능입니다.
Deception Technology Market Report는 배포(On-Premise 및 클라우드), 조직 규모(대규모 및 중소기업(SME)), 서비스(관리 및 전문 서비스), Deception Stack(데이터 보안, 용도 보안 등), 최종 사용자(정부, 방위, 은행, 금융서비스 및 보험(BFSI), IT 및 통신 등), 지역별로 분류됩니다.
지역 분석
북미는 2024년 매출액의 41.8%를 차지해, 인시던트 보고에 관한 CISA의 지령과 같은 엄격한 의무화나, 특수한 컨트롤에 자금을 제공할 수 있는 포춘 100의 본사가 집중하고 있는 것이 추풍이 되었습니다. 연방정부와의 계약은 사기기능의 지정이 증가하고 있으며, 디셉션 기술 시장에서 이 지역의 리더십은 더욱 견고합니다.
유럽에서는 NIS2 지침에 따라 능동적인 위협 감지 프로그램을 유지해야하는 기업의 범위가 확대되고 꾸준히 전진하고 있습니다. EU의 신흥 클라우드 제공업체는 현재 속임수 기능을 기본적으로 통합하고 중견 시장의 산업 장비 제조업체에 호소하는 컴플라이언스 지원 번들 제품을 제공합니다.
아시아태평양은 CAGR 13.8%로 계속 급성장하고 있습니다. 일본, 인도, 싱가포르의 각 정부는 디셉션을 포함한 제로 트러스트 시험 운용에 공동 출자하는 조성금 프로그램을 개시. 통신 사업자에 의한 5G 독립형 코어의 전개에 의해 공격 대상이 확대되고, 통신 사업자는 부정한 기지국 등록의 시도를 검출하는 시그널링 프로토콜의 디코이를 설치하도록 촉구됩니다. 이러한 노력은이 지역의 디셉션 기술 시장 규모를 확대하고 있습니다. 한편 라틴아메리카와 중동 및 아프리카에서는 예산의 제약과 인재 부족으로 단기적인 도입은 어려운 것, 중요한 인프라의 쇄신에 디셉션을 통합하기 시작합니다.
기타 혜택 :
- 엑셀 형식 시장 예측(ME) 시트
- 3개월간의 애널리스트 지원
목차
제1장 서론
- 조사 전제조건과 시장 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 상황
- 시장 개요
- 시장 성장 촉진요인
- 제로데이 공격과 표적형 APT의 급증
- 클라우드 네이티브 워크로드의 확대에 의해 공격 대상 영역이 확대
- CISO는 저마찰로 에이전트리스 검출 툴을 선호
- AI 생성 딥 페이크 ID 공격 증가
- 제로 트러스트·마이크로 세분화에 의한 기만의 융합
- 적극적인 횡방향 이동 검출을 요구하는 사이버 보험 정책
- 시장 성장 억제요인
- 기존 허니 포트에의 뿌리 깊은 의존
- 기만 스킬을 가진 SecOps 직원의 부족
- 적대자가 대규모 언어 모델 정찰을 이용하여 디코이를 발견(잠재적)
- 번들된 EDR/XDR 플랫폼에 의한 예산의 교섭
- 밸류체인 분석
- 규제 상황
- 기술의 전망
- Porter's Five Forces 분석
- 신규 참가업체의 위협
- 공급기업의 협상력
- 구매자의 협상력
- 대체품의 위협
- 경쟁 기업 간 경쟁 관계
- 투자분석
- 거시 경제 동향이 시장에 미치는 영향 평가
제5장 시장 규모와 성장 예측
- 배포별
- On-Premise
- 클라우드
- 조직 규모별
- 대기업
- 중소기업
- 서비스별
- 매니지드 서비스
- 전문 서비스
- 디셉션 스택
- 데이터 보안
- 애플리케이션 보안
- 엔드포인트 보안
- 네트워크 보안
- 최종 사용자별
- 정부
- 방위
- BFSI
- IT 및 통신
- 헬스케어
- 기타 최종 사용자
- 지역별
- 북미
- 미국
- 캐나다
- 멕시코
- 유럽
- 독일
- 영국
- 프랑스
- 이탈리아
- 스페인
- 러시아
- 기타 유럽
- 아시아태평양
- 중국
- 일본
- 인도
- 한국
- 호주 및 뉴질랜드
- 기타 아시아태평양
- 남미
- 브라질
- 아르헨티나
- 기타 남미
- 중동 및 아프리카
- 중동
- 사우디아라비아
- 아랍에미리트(UAE)
- 튀르키예
- 기타 중동
- 아프리카
- 남아프리카
- 나이지리아
- 기타 아프리카
- 북미
제6장 경쟁 구도
- 시장 집중도
- 전략적 동향
- 시장 점유율 분석
- 기업 프로파일
- Illusive Networks
- Attivo Networks(SentinelOne)
- Rapid7
- Acalvio Technologies
- CounterCraft
- CyberTrap
- TrapX Security
- Smokescreen Technologies
- Ridgeback Network Defense
- LogRhythm
- WatchGuard Technologies
- Broadcom(Symantec)
- Morphisec
- Fortinet(FortiDeceptor)
- Zscaler
- Microsoft(Security Honeytokens)
- Akamai
- Palo Alto Networks
- Fidelis Cybersecurity
- Commvault(TrapX integration)
제7장 시장 기회와 향후 전망
KTH 25.11.10The deception technology market posted USD 2.41 billion in 2025 and is set to advance at a 13.3% CAGR to USD 4.50 billion by 2030.
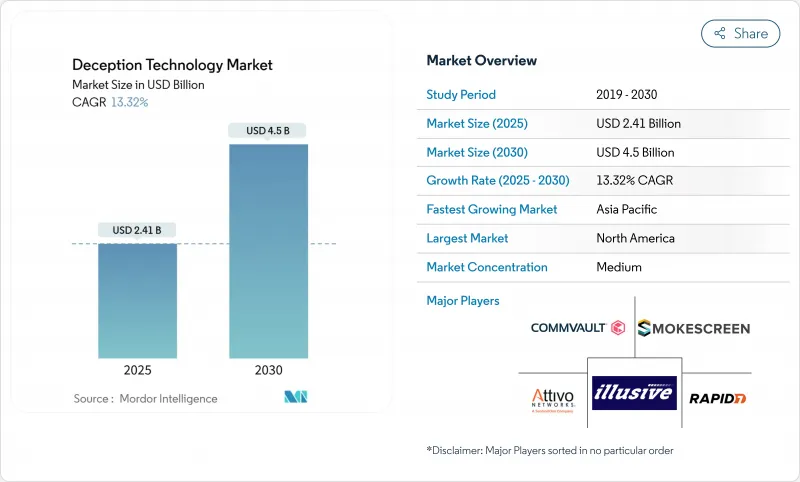
Rising zero-day exploits, AI-driven deepfake fraud, and cloud-native workload expansion compel security teams to adopt early-warning controls that spot attackers inside the network before damage occurs. Vendors now weave decoys into zero-trust micro-segmentation, giving defenders tripwires that work even when identities or endpoints are compromised. Demand also accelerates because cyber-insurance carriers require proactive lateral-movement detection as a condition for favorable premiums. Although North America keeps spending leadership, the deception technology market gains rapid momentum in Asia-Pacific as multicloud adoption surges and local regulators tighten breach-notification rules.
Global Deception Technology Market Trends and Insights
Surge in Zero-Day Exploits and Targeted APTs
State-sponsored collectives automate reconnaissance with AI, finding novel vulnerabilities faster than signature-based defenses adapt. The Institute for Security and Technology notes that automated reconnaissance compresses attacker dwell time, forcing defenders to rethink reactive playbooks. Deception platforms insert believable but fake assets that weaponize curiosity; once probed, alerts trigger in seconds while production systems stay untouched. Because detection is based on attacker behavior rather than threat-intelligence feeds, the deception technology market provides resilience against bespoke malware that evades hash-matching controls. Vendors now pre-package decoys for industrial control systems and SaaS APIs, reflecting attacker pivot toward operational technology.
Escalating Cloud-Native Workloads Broaden Attack Surface
Containerized and serverless applications can spin up and down within minutes, leaving security operations centers blind to east-west traffic. Zscaler deploys generative-AI decoys that mimic large-language-model endpoints, luring attackers into instrumented sandboxes. Because decoys scale automatically inside Kubernetes namespaces, defenders gain continuous coverage even as underlying microservices change. The deception technology market capitalizes on cloud providers' metadata APIs to place traps inside virtual private clouds without installing agents. As organizations adopt multi-cloud strategies, cross-provider decoy orchestration becomes a buying criterion, especially in regulated industries that cannot centralize logs in a single region.
Entrenched Reliance on Legacy Honeypots
Many firms still run static honeypots deployed years ago. Attackers now fingerprint such assets through protocol quirks or uptime patterns, bypassing them with ease. This sunk-cost bias delays upgrades to adaptive decoys able to morph operating-system banners or rotate credentials automatically. Legacy honeypots also demand manual log parsing, consuming resources that should focus on real attack paths. Because these tools produce few actionable alerts, boards question ROI, thereby constraining new investment and dampening growth of the deception technology market.
Other drivers and restraints analyzed in the detailed report include:
- CISO Preference for Low-Friction, Agent-Less Detection Tools
- Rise of AI-Generated Deepfake Identity Attacks
- Scarcity of Deception-Skilled SecOps Staff
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
On-premises deployment commanded 67.9% of deception technology market share in 2024, illustrating enterprises' need to keep high-interaction decoys close to crown-jewel systems for compliance and forensic control. That control, however, brings hardware refresh cycles and change-management overhead that limit agility. Cloud deployment contributes a modest slice today but is slated to rise at a 15.2% CAGR through 2030, the fastest pace within the deception technology market. Cloud-based consoles spin up decoys across regions within minutes, making them attractive for global branch rollouts.
Hybrid models emerge as a pragmatic bridge, letting teams place sensitive database decoys on-premises while offloading analysis and scaling tasks to public clouds. As multicloud adoption rises, buyers demand single-pane views across AWS, Azure, and Google Cloud, pushing providers to invest in identity federation and immutable infrastructure blueprints. These capabilities enhance the deception technology market size for cloud modules and convince regulation-bound sectors that shared-responsibility models can still satisfy audit controls.
Large enterprises retained 70.2% revenue share in 2024 and continue shaping feature roadmaps by insisting on API depth, MITRE ATT&CK alignment, and advanced analytics. Yet SMEs now register a 14.9% growth trajectory, outpacing big-company spending within the deception technology market. Subscription-based managed deception services, billed per asset, cut entry barriers and deliver curated alerts that fit smaller teams' bandwidth.
Savings compound because cloud consoles eliminate hardware purchase, allowing SMEs to reallocate capital toward employee awareness programs. For vendors, the segment's scale effect is compelling; thousands of mid-sized customers can equal the license revenue of a handful of Fortune 500 accounts. Consequently, roadmap priorities now include low-code playbooks and automated decoy placement, features designed to compress onboarding from weeks to hours and thereby expand deception technology market size among smaller firms.
The Deception Technology Market Report is Segmented by Deployment (On-Premises and Cloud), Organization Size (Large Enterprises and Small and Medium Enterprises (SMEs)), Service (Managed Services and Professional Services), Deception Stack (Data Security, Application Security, and More), End-User (Government, Defense, BFSI, IT and Telecommunication, and More), and Geography.
Geography Analysis
North America generated 41.8% of revenue in 2024, buoyed by stringent mandates such as CISA's directive on incident reporting and a concentration of Fortune 100 headquarters that can fund specialized controls. Federal contracts increasingly specify deception capabilities, further cementing the region's leadership within the deception technology market.
Europe advances steadily as the NIS2 Directive broadens the scope of entities required to maintain proactive threat-detection programs Local vendors stress data-sovereignty features, ensuring logs stay inside EU borders. Emerging EU cloud providers now embed deception natively, offering compliance-ready bundles that appeal to mid-market industrial manufacturers.
Asia-Pacific remains the fastest-growing territory at 13.8% CAGR. Governments in Japan, India, and Singapore launch grant programs that co-fund zero-trust pilots incorporating deception. Telecom rollouts of 5G standalone cores enlarge attack surfaces, pushing operators to install signaling-protocol decoys that detect rogue base-station registration attempts. These initiatives collectively enlarge deception technology market size in the region. Meanwhile, Latin America and Middle East and Africa start integrating deception into critical-infrastructure revamps, although budget constraints and talent gaps temper near-term uptake.
- Illusive Networks
- Attivo Networks (SentinelOne)
- Rapid7
- Acalvio Technologies
- CounterCraft
- CyberTrap
- TrapX Security
- Smokescreen Technologies
- Ridgeback Network Defense
- LogRhythm
- WatchGuard Technologies
- Broadcom (Symantec)
- Morphisec
- Fortinet (FortiDeceptor)
- Zscaler
- Microsoft (Security Honeytokens)
- Akamai
- Palo Alto Networks
- Fidelis Cybersecurity
- Commvault (TrapX integration)
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Surge in zero-day exploits and targeted APTs
- 4.2.2 Escalating cloud-native workloads broaden attack surface
- 4.2.3 CISO preference for low-friction, agent-less detection tools
- 4.2.4 Rise of AI-generated deepfake identity attacks
- 4.2.5 Convergence of deception with zero-trust micro-segmentation
- 4.2.6 Cyber-insurance policies demanding proactive lateral-movement detection
- 4.3 Market Restraints
- 4.3.1 Entrenched reliance on legacy honeypots
- 4.3.2 Scarcity of deception-skilled SecOps staff
- 4.3.3 Adversary use of large-language-model recon to spot decoys (under-the-radar)
- 4.3.4 Budget cannibalization by bundled EDR/XDR platforms
- 4.4 Value Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Porter's Five Forces Analysis
- 4.7.1 Threat of New Entrants
- 4.7.2 Bargaining Power of Suppliers
- 4.7.3 Bargaining Power of Buyers
- 4.7.4 Threat of Substitutes
- 4.7.5 Intensity of Competitive Rivalry
- 4.8 Investment Analysis
- 4.9 Assessment of the Impact of Macroeconomic Trends on the Market
5 MARKET SIZE AND GROWTH FORECASTS (VALUE)
- 5.1 By Deployment
- 5.1.1 On-premises
- 5.1.2 Cloud
- 5.2 By Organization Size
- 5.2.1 Large Enterprises
- 5.2.2 Small and Medium Enterprises (SMEs)
- 5.3 By Service
- 5.3.1 Managed Services
- 5.3.2 Professional Services
- 5.4 By Deception Stack
- 5.4.1 Data Security
- 5.4.2 Application Security
- 5.4.3 Endpoint Security
- 5.4.4 Network Security
- 5.5 By End-User
- 5.5.1 Government
- 5.5.2 Defense
- 5.5.3 BFSI
- 5.5.4 IT and Telecommunication
- 5.5.5 Healthcare
- 5.5.6 Other End-Users
- 5.6 By Geography
- 5.6.1 North America
- 5.6.1.1 United States
- 5.6.1.2 Canada
- 5.6.1.3 Mexico
- 5.6.2 Europe
- 5.6.2.1 Germany
- 5.6.2.2 United Kingdom
- 5.6.2.3 France
- 5.6.2.4 Italy
- 5.6.2.5 Spain
- 5.6.2.6 Russia
- 5.6.2.7 Rest of Europe
- 5.6.3 Asia-Pacific
- 5.6.3.1 China
- 5.6.3.2 Japan
- 5.6.3.3 India
- 5.6.3.4 South Korea
- 5.6.3.5 Australia and New Zealand
- 5.6.3.6 Rest of Asia-Pacific
- 5.6.4 South America
- 5.6.4.1 Brazil
- 5.6.4.2 Argentina
- 5.6.4.3 Rest of South America
- 5.6.5 Middle East and Africa
- 5.6.5.1 Middle East
- 5.6.5.1.1 Saudi Arabia
- 5.6.5.1.2 United Arab Emirates
- 5.6.5.1.3 Turkey
- 5.6.5.1.4 Rest of Middle East
- 5.6.5.2 Africa
- 5.6.5.2.1 South Africa
- 5.6.5.2.2 Nigeria
- 5.6.5.2.3 Rest of Africa
- 5.6.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 Illusive Networks
- 6.4.2 Attivo Networks (SentinelOne)
- 6.4.3 Rapid7
- 6.4.4 Acalvio Technologies
- 6.4.5 CounterCraft
- 6.4.6 CyberTrap
- 6.4.7 TrapX Security
- 6.4.8 Smokescreen Technologies
- 6.4.9 Ridgeback Network Defense
- 6.4.10 LogRhythm
- 6.4.11 WatchGuard Technologies
- 6.4.12 Broadcom (Symantec)
- 6.4.13 Morphisec
- 6.4.14 Fortinet (FortiDeceptor)
- 6.4.15 Zscaler
- 6.4.16 Microsoft (Security Honeytokens)
- 6.4.17 Akamai
- 6.4.18 Palo Alto Networks
- 6.4.19 Fidelis Cybersecurity
- 6.4.20 Commvault (TrapX integration)
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-need Assessment



















