
|
시장보고서
상품코드
1690127
제로 트러스트 보안 - 시장 점유율 분석, 산업 동향, 통계, 성장 예측(2025-2030년)Zero Trust Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
제로 트러스트 보안 시장 규모는 2025년에 383억 7,000만 달러, 2030년에는 865억 7,000만 달러에 달할 것으로 예측됩니다. 예측 기간(2025-2030년) CAGR은 17.67%를 나타낼 전망입니다.

클라우드 컴퓨팅으로의 전환에 따라 기업은 보안 시스템을 검토해야 합니다. 제로 트러스트는 클라우드 기반 앱과 데이터에 대한 안전한 액세스를 제공하며, 클라우드 퍼스트 계획에 적합합니다. 제로 트러스트는 컴플라이언스를 가능하게 합니다.기업은 기본적인 보안 전략으로서 다양한 부문에서 제로 트러스트의 프레임워크를 보다 널리 활용하고 있습니다.
주요 하이라이트
- 제로 트러스트 보안을 성공적으로 구축하기 위해 기업은 사이버 보안 공급업체 및 관리형 보안 서비스 제공업체(MSSP)와의 제휴를 추진하고 있습니다. 이러한 제휴는 보다 광범위한 보안 경계 보호 문제를 해결하기 위한 지식과 자원을 제공합니다. 유연성, 확장성 및 비용 효율성을 제공하는 클라우드 컴퓨팅의 활용 확대로 기업의 기능이 완전히 변화하고 있습니다. 기밀 정보와 중요한 용도는 더 이상 온프레미스 데이터센터에 국한되지 않으며 보안 경계도 확장되었습니다.
- 엔터프라이즈는 많은 클라우드 공급자를 자주 사용하므로 데이터와 애플리케이션이 흩어져 있습니다. 이러한 멀티클라우드 전략은 확장된 보안 경계를 확보하기가 더 어려워집니다. 책임 공유 접근 방식에서 클라우드 서비스 공급자(CSP)는 인프라를 보호하고 고객은 데이터 및 용도 보호를 담당합니다. 이 책임 분담은 종합적인 보안 계획의 필요성을 강조합니다. 직원 및 타사 파트너는 다양한 위치와 장치를 사용하여 클라우드 서비스에 액세스합니다. 따라서 지속적인 모니터링과 안전한 액세스 제어가 필요합니다.
- 데이터와 사용자가 다수의 위치와 장치에 분산되어 있는 변화하는 보안 경계에 적응하는 것은 사이버 보안의 미래에 필수적입니다. 제로 트러스트 보안은 새로운 위협을 선점하고 현재 문제를 해결하기 위한 확장 가능한 아키텍처를 제공합니다. 세계의 제로 트러스트 보안 시장은 이러한 변화에 대응하여 기업이 보안 시책을 재평가하고, 혁신적인 솔루션이 사이버 보안의 전망을 지속적으로 재구축하고 있기 때문에 지속적인 성장이 예상되고 있습니다.
- 제로 트러스트 보안의 도입은 레거시 시스템이 있는 기업에게 긴 전환 기간이 필요합니다. 그 결과 철저한 보안 조치의 배포가 지연될 수 있습니다. 제로 트러스트 접근 방식에 따라 과거 시스템을 업그레이드하거나 교체하는 데는 시간, 비용 및 노력이 필요합니다. 그 결과, 제로 트러스트의 대처의 채용을 생각하는 기업도 나올 가능성이 있습니다. 조직이 최신 시스템 및 용도에 제로 트러스트 보안을 사용하게 되면 레거시 구성 요소에 보안 결함이 생겨 네트워크의 다른 부분에서 제로 트러스트의 이점이 상쇄될 수 있습니다.
- 제로 트러스트 보안은 COVID-19 이상 환경에서 더욱 중요합니다. 원격 근무, 클라우드, 새로운 위협, 컴플라이언스 의무는 유연하고 사전 활동적인 보안 접근 방식을 필요로 합니다. 제로 트러스트를 채택하는 조직은 포스트 팬데믹 시나리오의 과제를 해결하고 지속적으로 진화하는 디지털 환경에서 가장 중요한 자산을 보호하기 위한 더 나은 체제를 갖추고 있습니다.
제로 트러스트 보안 시장 동향
주요 성장을 목격한 중소기업
- 중소기업은 금융포섭 강화에 기여하고 빈곤층이나 충분한 서비스를 받지 못한 시장에 상품이나 서비스를 공급하는 등 경제 상황에서 중심적인 역할을 하고 있습니다. 이러한 기업들은 혁신의 중요한 추진력이며 높은 성장 가능성을 지니고 있습니다. 예를 들어, 유럽 위원회에 따르면 유럽 연합(EU)은 2023년에 약 2,440만 개의 중소기업(SME)이 존재할 것으로 추정되고 있으며, 중소기업은 유럽 경제의 중추를 형성하고 있습니다.
- 하이브리드 모델에 따라 대부분의 중소기업은 미래의 직장환경과 직원 정책의 유연성에 아직 대응하지 못하고 있습니다.
- 클라우드 기반 환경은 장기적인 지속가능성과 탄력성을 보장하며 중소기업을 위한 다양한 사이버 보안 전략에 대한 수요를 추진하고 있습니다. 제로 트러스트 보안을 통해 견고하고 안전한 업무 환경이 보장되며, 조직의 네트워크 아키텍처에 액세스하려는 시도는 신뢰가 검증되어야만 성공할 수 있습니다. 사용자가 애플리케이션에 액세스하면 사용자와 장치가 지속적으로 모니터링됩니다. 이로 인해 모든 사용자, 장치 및 위치에서 조직의 애플리케이션과 환경을 보호 할 수 있습니다.
- 기존 사이버 보안 기업과 신흥 사이버 보안 기업의 대부분은 증가하는 수요에 대응하기 위해 중소기업을 위한 제로 트러스트 네트워크 액세스(ZTNA) 서비스를 제공합니다.
큰 성장이 기대되는 아시아태평양
- 아시아의 기술력은 지난 10년간 향상되어 많은 기업이 디지털 전환을 중요한 목표 중 하나로 내세워왔습니다.
- 아시아태평양은 세계의 제조업을 석권해 특히 중국에서 가장 높은 연간 성장률을 나타낼 것으로 예상됩니다.
- 중국은 디지털화를 선호하고 사이버 보안 태세를 지속적으로 개선하고 있습니다.
- 2023년 8월 아시아를 선도하는 통신 기술 그룹인 싱텔은 아시아에서 처음으로 Zscaler의 보안 솔루션을 제공하는 전략적 파트너십을 발표했습니다.
- 싱텔의 매니지드 보안 서비스 에지(MSSE)는 전임의 사이버 보안 전문가에 의한 프리세일즈로부터 포스트 세일즈 서포트, 구축, 플랫폼 컨설테이션, 유지관리, 24시간 체제의 위협 완화 등의 자원을 기재하고 있습니다.
제로 트러스트 보안 시장 개요
제로 트러스트 보안 시장은 Cisco Systems Inc., Palo Alto Networks Inc., IBM Corporation Inc., Broadcom Inc. Symantec Corporation, Microsoft Corporation 등 세계적 및 지역적 진출기업이 존재하고, 분열화되어 있습니다.
- 2023년 9월 Broadcom은 VMware를 인수했으며, 브로드컴은 시만텍의 보안 포트폴리오와 VMware의 SD-WAN 기능을 통합할 수 있습니다. Black의 보안 기능 중 일부를 통합함으로써 Broadcom은 단일 공급업체의 보안 액세스 서비스 에지(SASE) 산업에 진출하여 성공적으로 전체 SASE 산업의 점유율과 수익을 높일 수 있습니다. SASE 및 보안 서비스 에지(SSE) 포트폴리오에는 보안 웹 게이트웨이(SWG), 데이터 유출 방지(DLP), 클라우드 액세스 보안 브로커(CASB), 제로 트러스트 네트워크 액세스(ZTNA), SSL 검사, 웹 격리 등의 구성 요소가 포함됩니다.
- 2023년 7월, Accenture는 Palo Alto Networks와 제휴하여 제로 트러스트 보안을 강화했습니다. Networks와 Accenture는 기업의 과제를 해결하는 종합적인 관리형 SASE 솔루션을 제공합니다.
기타 혜택
- 엑셀 형식 시장 예측(ME) 시트
- 3개월의 애널리스트 서포트
목차
제1장 서론
- 조사의 전제조건과 시장 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 인사이트
- 시장 개요
- 산업의 매력 - Porter's Five Forces 분석
- 공급기업의 협상력
- 구매자의 협상력
- 신규 참가업체의 위협
- 대체품의 위협
- 경쟁 기업간 경쟁 관계
- COVID-19의 영향
- 산업 밸류체인 분석
- 기술 스냅샷
- 제로 트러스트 네트워크
- 제로 트러스트 디바이스
- 제로 트러스트 데이터
- 제로 트러스트 ID 확인
- 제로 트러스트 용도(가시화 및 분석)
제5장 시장 역학
- 시장 성장 촉진요인
- 데이터 유출 증가
- 조직의 보안 경계가 직장에 한정되지 않는 것
- 시장 성장 억제요인
- 제로 트러스트 모델을 채용하기 어려운 레거시인 용도, 인프라, 오퍼레이팅 시스템
제6장 시장 세분화
- 전개별
- 온프레미스
- 클라우드
- 조직 규모별
- 중소기업
- 대기업
- 최종 사용자 산업별
- IT 및 통신
- BFSI
- 제조업
- 의료
- 에너지 전력
- 소매업
- 정부기관
- 기타
- 지역별
- 북미
- 유럽
- 아시아
- 호주 및 뉴질랜드
- 라틴아메리카
- 중동 및 아프리카
제7장 경쟁 구도
- 기업 프로파일
- Cisco Systems Inc.
- Palo Alto Networks Inc.
- Broadcom Inc.(Symantec Corporation)
- Microsoft Corporation
- IBM Corporation
- Google Inc.
- Check Point Software Technologies Ltd
- Blackberry Limited
- Akamai Technologies Inc.
- Delinea(Centrify Corporation)
- Okta Inc.
- Fortinet Inc.
- Sophos Group PLC
- Cyxtera Technologies Inc.
제8장 투자 분석
제9장 시장의 미래
SHW 25.05.09The Zero Trust Security Market size is estimated at USD 38.37 billion in 2025, and is expected to reach USD 86.57 billion by 2030, at a CAGR of 17.67% during the forecast period (2025-2030).
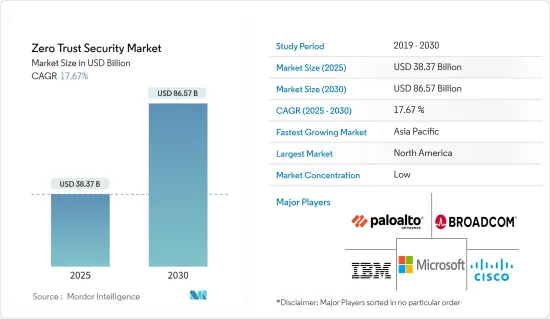
Organizations have had to review their security postures due to the move toward cloud computing. Zero Trust facilities secure access to cloud-based apps and data, which fits well with cloud-first plans. Organizations must develop robust data protection mechanisms to comply with strict data privacy laws like GDPR and CCPA, making Zero Trust a compliance enabler. Businesses use the Zero Trust framework in various sectors more widely as a fundamental security strategy. The conventional perimeter-based paradigm is being abandoned. Big technology corporations are buying Zero Trust security businesses to improve security services.
Key Highlights
- To successfully adopt zero-trust security, businesses are increasingly developing alliances with cybersecurity vendors and managed security service providers (MSSPs). These collaborations contribute knowledge and resources to handle the challenges of protecting the wider security perimeter. The growing use of cloud computing, which provides flexibility, scalability, and cost-efficiency, has completely changed how businesses function. Sensitive information and essential applications are no longer restricted to on-premises data centers, which also expanded the security perimeter.
- Businesses frequently use numerous cloud providers, which results in scattered data and applications. The enlarged security perimeter is more difficult to secure with this multi-cloud strategy. Under a shared responsibility approach, cloud service providers (CSPs) secure the infrastructure while customers are in charge of protecting their data and applications. This shared duty emphasizes the necessity of an all-encompassing security plan. Employees and third-party partners use a variety of locations and devices to access cloud services. So, there is a need for continuous monitoring and safe access controls.
- Adapting to the changing security perimeter, where data and users are dispersed across numerous locations and devices, is essential for the future of cybersecurity. Zero-trust security offers a scalable architecture to keep ahead of new threats and address current issues. The global zero-trust security market has been anticipated to experience sustained growth as enterprises continue to reevaluate their security policies in response to these shifts, with innovative solutions continuously reshaping the cybersecurity landscape.
- Adopting zero-trust security requires a longer transition period for organizations with legacy systems. The deployment of thorough security measures may be delayed as a result. It takes time, money, and labor to upgrade or replace historical systems so they align with the zero-trust approach. As a result, some businesses may be discouraged from adopting zero-trust efforts. Legacy components may develop security flaws as organizations progressively use zero-trust security for their contemporary systems and applications, thereby offsetting the advantages of zero trust elsewhere in the network.
- Zero Trust Security has become much more crucial in the post-COVID-19 environment. Remote work, the cloud, emerging threats, and compliance obligations highlight the necessity for a flexible, proactive security approach. Organizations that adopt zero trust are better equipped to deal with the challenges of the post-pandemic scenario and protect their most essential assets in a constantly evolving digital environment.
Zero Trust Security Market Trends
Small and Medium Enterprises to Witness Major Growth
- SMEs play a central role in the economic landscape, helping to strengthen financial inclusion and supplying goods and services to poor and underserved markets. These enterprises are critical drivers of innovation and offer high growth potential. For instance, according to the European Commission, approximately 24.4 million small and medium-sized enterprises (SMEs) were estimated to be in the European Union in 2023, as SMEs form the backbone of the European economy.
- Even following a hybrid model, most small businesses have yet to prepare for flexibility within future work environments and employee policies. Growth in working from home, hybrid modalities, and family-focused employee structures aid quick transition to more secure strategies. To ensure sustainability, MSMEs should identify market opportunities and consumer demands.
- The cloud-based environment ensures long-term sustainability and resilience, driving the demand for various cybersecurity strategies for SMEs. A robust and secure work environment is guaranteed with zero-trust security, and an attempt to access an organization's network architecture can only succeed once trust is validated. When a user accesses an application, the user and device are confirmed, and trust is continuously monitored. This helps secure the organization's applications and environments from any user, device, and location, which is vital for SME's future growth.
- Many established and emerging cybersecurity players offer zero-trust network access (ZTNA) services for small and medium enterprises to cater to the rising demands. The cloud-delivered service extends the company's zero-trust solutions to cloud-native businesses and enterprises, embracing cloud adoption and giving SMEs improved productivity, better security, greater visibility, and a significantly reduced attack surface.
Asia Pacific Expected to Register Significant Growth
- Asia's technological abilities have increased over the past decade, with many businesses concentrating on the digital shift as one of their key goals throughout the pandemic. While the revolutions of digital transformation were set in motion much earlier, the pandemic accelerated their speed. It particularly impacted how organizations approach their IT ecosystem and security.
- Asia-Pacific is anticipated to dominate the global manufacturing industry, recording the highest inter-annual growth rate, especially in China. This country has achieved significant growth in its production rates compared to its pre-pandemic pace.
- China keeps prioritizing digitalization and improving its cybersecurity posture. ZAT solutions safeguard its digital operations and help comply with regulatory standards. Chinese businesses are increasingly realizing the value of ZAT solutions, making the Chinese market a key driver of adoption in the Asia-Pacific region.
- In August 2023, Singtel, Asia's leading telecommunications technology group, announced a strategic partnership to offer Zscaler's security solutions in Asia, a first for the region. Through this partnership, Singtel's MSSE offers businesses impacted by insufficient in-house resources or skill sets an all-in-one digital security solution that helps to protect their digital assets against cyber threats.
- Enterprises in the APAC region will now have seamless access to Zscaler's Zero Trust Exchange, a cloud-based platform, through Singtel's Managed Security Service Edge (MSSE) suite of services, which includes pre-sales to post-sales support from dedicated cybersecurity experts as well as resources such as build implementation, platform consultation, maintenance, and round-the-clock threat mitigation. As the rate of enterprise digitalization continues to accelerate at an unprecedented pace, so does the risk of cyber threats.
Zero Trust Security Market Overview
The zero trust security market is fragmented with the presence of global and regional players such as Cisco Systems Inc., Palo Alto Networks Inc., IBM Corporation Inc., Broadcom Inc. (Symantec Corporation), and Microsoft Corporation. Moderate to high product differentiation, growing levels of product penetration, and high levels of competition characterize the market. Generally, the solutions are offered as a package solution, making the consolidated offering look like a part of the product's service.
- In September 2023, Broadcom acquired Vmware. With its potential VMware acquisition, Broadcom can meld Symantec's security portfolio with VMware's SD-WAN capabilities. By integrating Symantec, VMware SD-WAN, and some of Carbon Black's security capabilities, Broadcom could enter the single-vendor secure access service edge (SASE) industry and boost its overall SASE industry share and revenue if executed well. Broadcom's current Symantec SASE and security service edge (SSE) portfolio includes components such as secure web gateway (SWG), data loss prevention (DLP), cloud access security brokers (CASB), zero-trust network access (ZTNA), SSL inspection, and web isolation.
- In July 2023, Accenture teamed with Palo Alto Networks to bolster Zero Trust Security. In order to enable enterprises to improve their cybersecurity posture and speed up the implementation of business transformation initiatives, they have joined forces to deliver jointly secure access service edge solutions using a SASE solution. Palo Alto Networks and Accenture provide a comprehensive managed SASE solution that tackles organizations' challenges. Enterprises worldwide can accelerate their business transformation by combining the strength of the largest global systems integrator with the SASE solution, benefiting from improved network performance and a consistent security policy and implementation.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Attractiveness - Porter's Five Forces Analysis
- 4.2.1 Bargaining Power of Suppliers
- 4.2.2 Bargaining Power of Buyers
- 4.2.3 Threat of New Entrants
- 4.2.4 Threat of Substitutes
- 4.2.5 Intensity of Competitive Rivalry
- 4.3 Impact of COVID-19
- 4.4 Industry Value Chain Analysis
- 4.5 Technology Snapshot
- 4.5.1 Zero Trust Networks
- 4.5.2 Zero Trust Devices
- 4.5.3 Zero Trust Data
- 4.5.4 Zero Trust Identities
- 4.5.5 Zero Trust Applications (Visibility and Analytics)
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Increasing Number of Data Breaches
- 5.1.2 Security Perimeter of an Organization not Being Limited to Workplace
- 5.2 Market Restraints
- 5.2.1 Legacy Applications, Infrastructure, and Operating Systems Not Likely to Adopt Zero Trust Model
6 MARKET SEGMENTATION
- 6.1 By Deployment
- 6.1.1 On-premise
- 6.1.2 Cloud
- 6.2 By Organization Size
- 6.2.1 Small and Medium Enterprises
- 6.2.2 Large Enterprises
- 6.3 By End-user Industry
- 6.3.1 IT and Telecom
- 6.3.2 BFSI
- 6.3.3 Manufacturing
- 6.3.4 Healthcare
- 6.3.5 Energy and Power
- 6.3.6 Retail
- 6.3.7 Government
- 6.3.8 Other End-user Industries
- 6.4 By Geography
- 6.4.1 North America
- 6.4.2 Europe
- 6.4.3 Asia
- 6.4.4 Australia and New Zealand
- 6.4.5 Latin America
- 6.4.6 Middle East and Africa
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 Cisco Systems Inc.
- 7.1.2 Palo Alto Networks Inc.
- 7.1.3 Broadcom Inc. (Symantec Corporation)
- 7.1.4 Microsoft Corporation
- 7.1.5 IBM Corporation
- 7.1.6 Google Inc.
- 7.1.7 Check Point Software Technologies Ltd
- 7.1.8 Blackberry Limited
- 7.1.9 Akamai Technologies Inc.
- 7.1.10 Delinea (Centrify Corporation)
- 7.1.11 Okta Inc.
- 7.1.12 Fortinet Inc.
- 7.1.13 Sophos Group PLC
- 7.1.14 Cyxtera Technologies Inc.



















