
|
시장보고서
상품코드
1549868
데이터센터 물리적 보안 : 시장 점유율 분석, 산업 동향 및 통계, 성장 예측(2024-2029년)Global Data Center Physical Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2024 - 2029) |
||||||
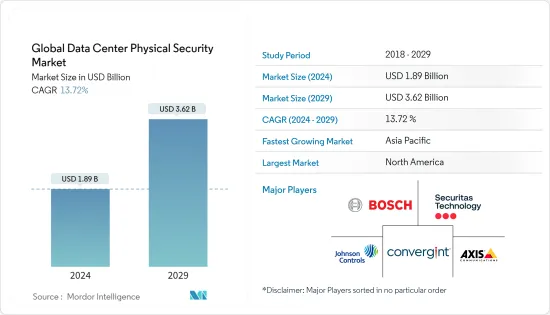
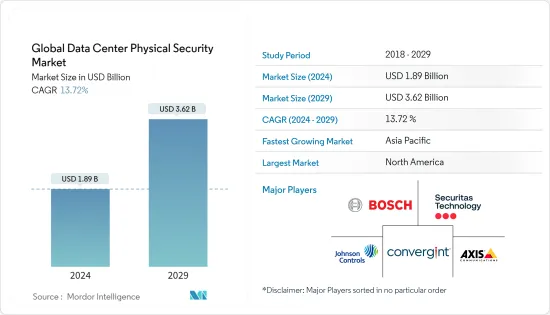
세계의 데이터센터 물리적 보안 시장 규모는 2024년 18억 9,000만 달러로 추정되며, 2029년에는 36억 2,000만 달러에 달할 것으로 예상되며, 예측 기간(2024-2029) 동안 13.72%의 CAGR로 성장할 것으로 예상됩니다.
보안 대책은 경계 보안, 전산실 관리, 시설 관리, 캐비닛 관리 등 4가지로 분류할 수 있습니다. 데이터센터 보안의 첫 번째 층은 경계에서 인원의 무단 침입을 차단, 감지, 지연시킵니다. 경계 감시가 위반되면 두 번째 방어 계층은 액세스를 거부합니다. 이는 카드 스와이프 또는 생체인식을 이용한 출입 통제 시스템입니다.
제3의 물리적 보안 계층은 모든 제한 구역의 모니터링, 회전식 개찰구와 같은 출입 제한 배치, 손가락, 지문, 홍채, 혈관 패턴 등을 확인하는 생체인식 출입 통제 장치 제공, VCA 제공, 무선 주파수 식별 사용 등 다양한 검증 방법을 통해 출입을 더욱 제한합니다. 처음 세 계층은 허가된 사람만 출입할 수 있도록 보장합니다. 출입을 제한하는 추가 보안에는 캐비닛 잠금 장치가 포함됩니다. 이 계층은 악의적 인 직원과 같은 "내부 위협"에 대한 두려움을 해결합니다.
세계의 데이터센터 물리적 보안 시장의 향후 IT 부하 용량은 2029년까지 71,000MW에 달할 것으로 예상됩니다.
조사 대상 시장의 바닥 면적 증가는 2029년까지 2억 7,390만 평방피트까지 증가할 것으로 예상됩니다.
2029년까지 이 지역에 설치될 총 랙 수는 1,420만 개에 달할 것으로 예상됩니다. 북미는 2029년까지 가장 많은 수의 랙이 설치될 것으로 예상됩니다.
세계 각지를 연결하는 해저 케이블 시스템은 약 500개에 달하며, 그 중 상당수가 건설 중인데, 2025년에 서비스를 시작할 것으로 예상되는 해저 케이블 중 하나는 미국 글로버 비치(Grover Beach)를 기점으로 12,000km 이상에 달하는 CAP-1입니다.
세계의 데이터센터 물리적 보안 시장 동향
출입통제 솔루션이 큰 폭의 성장세를 기록
- 데이터센터 보안을 유지하기 위해서는 강력한 접근 제어를 도입하는 것이 필수적입니다. 과거에는 데이터센터 내 서버를 UPS로 도난당한 사례가 보고된 바 있습니다. 범죄자들은 암시장에서 판매하기로 선택하지만, 항상 완전한 PC나 UPS 장비를 팔려고 하는 것은 아닙니다. 종종 가치가 있는 것은 원자재입니다. 영국의 금속 절도 동향은 2012년 이후 감소 추세에 있으며, 2016년과 2017년에 기록된 범죄 건수는 13,033건으로 최저치를 기록했지만 이후 증가 추세에 있으며 2021년과 2022년에는 두 배 이상 증가한 29,920건까지 증가했습니다.
- 출입 통제는 데이터센터의 보안을 보장하는 가장 효율적이고 확장 가능하며 경제적으로 유익한 방법 중 하나입니다. 물리적 보안, 정보 보안, 데이터 보안 등의 보안 메커니즘이 액세스 제어 시스템을 구성하며, LenelS2와 같은 기업은 추가 하드웨어나 소프트웨어 없이 기존 바코드 인프라를 활용하여 데이터센터 자산에 대한 강력한 추적 기능을 제공합니다. 데이터센터 자산에 대한 강력한 추적 기능을 제공합니다.
- 생체인식 기기에 대한 접근 편의성이 높아지면서 출입통제 산업의 성장을 촉진하고 있습니다. 지문 인식은 간편하고 비용 효율적인 접근 제어를 제공하기 때문에 널리 사용되어 시장 성장을 견인하고 있습니다. 시장 성장의 배경에는 장비의 상호 연결성 증가와 보안 위험의 급증도 한몫을 하고 있습니다.
- IBM에 따르면 데이터 침해의 세계 평균 비용은 2022년 사상 최고치인 435만 달러에 달해 2년 만에 약 13% 증가했다고 합니다. 미국 조직의 비용은 데이터 침해 1건당 944만 달러로 두 배 이상 증가했으며, IBM 보고서에 따르면 조사 대상 조직의 83%가 한 번 이상 데이터 유출을 경험했으며, 가장 일반적인 4가지 방법(도난 및 인증 정보 유출 포함)이 2023년 기준 19%의 기여도를 차지합니다.
- 전체적으로 예측 기간 동안 보안 침해가 증가함에 따라 출입통제 솔루션에 대한 시장 수요는 증가할 것으로 예상됩니다.
북미 시장 점유율이 가장 큰 비중을 차지
- 미국은 물리적 보안 솔루션의 채택이 증가함에 따라 북미의 주요 시장으로 부상하고 있으며, Demand Sage Inc.에 따르면 미국 기업의 67% 이상이 클라우드 기반 인프라를 도입했으며, 2023년 미국 전체 IT 지출의 약 20%가 클라우드 서비스에 지출될 것으로 예상됩니다. 가 클라우드 서비스에 지출될 것으로 예상하고 있습니다. 이러한 사례는 데이터센터의 대규모 도입으로 이어져 액세스 제어에 대한 수요를 충족시킬 수 있습니다.
- 캘리포니아주는 CPRA(California Privacy Rights Act)와 Virginia CDPA(Consumer Data Protection Act)를 통해 CCPA를 개정하여 미국 내에서 엄격한 보안 및 프라이버시 요건을 부과하고 있습니다. 마찬가지로 캐나다에서는 개인정보보호 및 전자문서법(PIPEDA)과 같은 데이터 보호 규정이 엄격한 보안 및 개인정보 보호 요건을 부과하고 있습니다. 이러한 규정은 물리적 보안 솔루션을 준수해야 하며, 이는 조사 대상 시장의 수요를 촉진할 수 있습니다.
- 시장의 주요 기업들은 시장 수요를 충족시키기 위해 데이터센터 물리적 보안 솔루션을 개선하는 데 주력하고 있으며, 2023년 6월 보쉬는 건물 및 제한 구역에 대한 모바일 액세스 솔루션을 발표했습니다.
- 이 모바일 액세스 솔루션은 보쉬의 입증된 액세스 관리 시스템에 완벽하게 통합되어 건물 소유주, 방문자 및 직원에게 효율성, 보안, 편의성 등 다양한 이점을 제공합니다. 우선 베네룩스 지역, 스위스, 독일, 오스트리아, 캐나다, 미국 고객을 대상으로 합니다.
세계의 데이터센터 물리적 보안 산업 개요
세계의 데이터센터 물리적 보안 시장은 Axis Communications AB, ABB Ltd, Bosch Sicherheitssysteme GmbH 등 기업의 기능 확장에 중요한 역할을 하는 기업들에 의해 고도로 세분화되어 있습니다. 시장 지향성은 고도의 경쟁 환경으로 이어집니다. 압도적인 시장 점유율을 가진 이들 대기업들은 지역 내 고객 기반을 확대하는 데 주력하고 있습니다. 이들은 시장 점유율과 수익성을 높이기 위해 전략적 협업 이니셔티브를 활용하고 있습니다.
2023년 4월, 슈나이더일렉트릭은 모듈형 데이터센터 에코케어(EcoCare for Modular Data Centers) 멤버십 서비스를 시작했습니다. 이 혁신적인 서비스 회원은 24/7 사전 예방적 원격 모니터링 및 상태 기반 유지보수를 통해 모듈형 데이터센터의 가동 시간을 최대화하기 위한 전문 지식을 이용할 수 있습니다.
2023년 5월, 알카트라즈 AI는 2023년 6월에 개최되는 데이터센터 포럼 헬싱키(Data Center Forum Helsinki)에 참가한다고 발표했습니다. 이 행사는 400명 이상의 데이터센터 전문가들이 모이는 행사로, Alcatraz AI가 데이터센터 물리적 보안을 위한 혁신적인 생체인식 액세스 제어 솔루션을 시연할 수 있는 이상적인 기회를 제공할 것으로 기대되고 있습니다.
기타 혜택
- 엑셀 형식의 시장 예측(ME) 시트
- 3개월간의 애널리스트 지원
목차
제1장 소개
- 조사 상정과 시장 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 역학
- 시장 개요
- 시장 성장 촉진요인
- 하이퍼스케일 및 코로케이션 사업자에 의한 데이터센터 활동과 투자 증가
- 클라우드 시스템에 접속된 비디오 감시 시스템의 진보
- 시장 성장 억제요인
- 운영과 투자 수익률에 관한 우려
- 밸류체인/공급망 분석
- 업계의 매력 - Porter's Five Forces 분석
- 신규 참여업체의 위협
- 구매자/소비자의 협상력
- 공급 기업의 교섭력
- 대체품의 위협
- 경쟁 기업 간의 경쟁 강도
- COVID-19의 영향 평가
제5장 시장 세분화
- 솔루션 유형별
- 비디오 감시
- 입퇴실 관리 솔루션
- 기타(맨트랩, 펜스, 감시 솔루션)
- 서비스 유형별
- 컨설팅 서비스
- 프로페셔널 서비스
- 기타(시스템 인테그레이션 서비스)
- 최종사용자
- IT·통신
- BFSI
- 정부기관
- 헬스케어
- 기타 최종사용자
- 지역
- 북미
- 유럽
- 아시아
- 남미
- 중동
- 아프리카
제6장 경쟁 상황
- 기업 개요
- Axis Communications AB
- Convergint Technologies LLC
- Securitas Technology
- Bosch Sicherheitssysteme GmbH
- Johnson Controls International
- Honeywell International Inc.
- Schneider Electric
- AMAG Technology
- Brivo Systems LLC
- Suprema Inc.
- Assa Abloy AB
- Milestone Systems A/S
- Cisco Systems Inc.
- ABB Ltd
- American Integrated Security Group
제7장 투자 분석
제8장 시장 기회와 향후 동향
ksm 24.09.13The Global Data Center Physical Security Market size is estimated at USD 1.89 billion in 2024, and is expected to reach USD 3.62 billion by 2029, growing at a CAGR of 13.72% during the forecast period (2024-2029).
Security measures can be categorized into four, namely perimeter security, computer room controls, facility controls, and cabinet controls. The first layer of data center security discourages, detects, and delays any unauthorized entry of personnel at the perimeter. In case of any infringement in the perimeter monitoring, the second layer of defense denies access. It is an access control system utilizing card swipes or biometrics.
The third layer of physical security further restricts access through various verification methods, including monitoring all restricted areas, deploying entry restrictions such as turnstiles, providing biometric access control devices to verify finger and thumbprints, irises, or vascular patterns, providing VCA, and using radio frequency identification. The first three layers ensure the entry of only authorized people. Further security to restrict admission includes cabinet locking mechanisms. This layer addresses the fear of an 'insider threat,' such as a malicious employee.
The upcoming IT load capacity of the global data center physical security market is expected to reach 71,000 MW by 2029.
The construction of raised floor area in the market studied is expected to increase to 273.9 million sq. ft by 2029.
The region's total number of racks to be installed is expected to reach 14.2 million units by 2029. North America is expected to house the maximum number of racks by 2029.
There are close to 500 submarine cable systems connecting the regions globally, and many are under construction. One such submarine cable that is estimated to start service in 2025 is CAP-1, which stretches over 12,000 km with a landing point in Grover Beach, United States.
Global Data Center Physical Security Market Trends
Access Control Solutions to Register Significant Growth
- Implementing strong access controls is vital in maintaining the security of data centers. In the past, instances of UPS theft of servers in data centers have been reported. Criminals choose to sell on the black market, but they are not always looking to sell complete PCs or UPS equipment. For many, the raw materials are where the value exists. UK metal theft offenses have been declining since 2012, reaching a low of 13,033 recorded offenses in 2016 and 2017, but have been on an upward trend since then, more than doubling to 29,920 offenses in 2021 and 2022.
- Access control is one of the most efficient, scalable, and financially profitable ways of securing data centers. Security mechanisms, such as physical security, information security, and data security, comprise the access control system. Players such as LenelS2 provide robust tracking for data center assets utilizing existing barcode infrastructure with no additional hardware or software requirement.
- The growing accessibility to biometric equipment is driving the growth of the access control industry. As fingerprint recognition provides easy and cost-effective access control, it is extensively used, fueling the market growth. The market growth can also be attributed to the increasing interconnectedness of devices and the surging security risks.
- According to IBM, the global average cost of a data breach reached an all-time high of USD 4.35 million in 2022, an increase of almost 13% over two years. The cost for US organizations was more than double at USD 9.44 million per data breach. The IBM report found that 83% of the organizations studied have had more than one data breach, with the four most popular methods, including stolen and compromised credentials, catering to 19% contribution as of 2023.
- Overall, during the forecast period, the market demand for access control solutions is expected to increase with increasing security breaches.
North America to Hold Significant Market Share
- The United States is a prominent market in North America, owing to the growing adoption of physical security solutions. According to Demand Sage Inc., more than 67% of enterprises in the United States have cloud-based infrastructure. Around 20% of total IT spending in the United States in 2023 was on cloud services. Such instances will lead to major data center adoption, catering to the demand for access control.
- California amended the CCPA with the California Privacy Rights Act (CPRA) and Consumer Data Protection Act (Virginia CDPA), which impose strict security and privacy requirements within the United States. Similarly, data protection regulations, such as the Personal Information Protection and Electronic Documents Act ("PIPEDA"), impose strict security and privacy requirements within Canada. These regulations must be complied with physical security solutions, which may propel the demand in the market studied.
- The key players in the market are focused on improving data center physical security solutions to meet the market demand. In June 2023, Bosch introduced a Mobile Access solution to buildings and restricted areas, which allows access without any identification media such as plastic cards.
- This Mobile Access solution is fully integrated into the tried-and-tested Access Management System from Bosch and provides various benefits, including efficiency, security, and convenience for building owners, visitors, and employees. This was initially available to customers in the Benelux region, Switzerland, Germany, Austria, Canada, and the United States..
Global Data Center Physical Security Industry Overview
The global data center physical security market is highly fragmented due to players like Axis Communications AB, ABB Ltd, and Bosch Sicherheitssysteme GmbH, which play a vital role in upscaling the capabilities of enterprises. Market orientation leads to a highly competitive environment. These major players, with a prominent market share, focus on expanding their customer base across the region. These companies leverage strategic collaborative initiatives to increase their market share and profitability.
In April 2023, Schneider Electric launched EcoCare for Modular Data Centers services membership. Members of this innovative service benefit from specialized expertise to maximize modular data centers' uptime with 24/7 proactive remote monitoring and condition-based maintenance.
In May 2023, Alcatraz AI, one of the prominent providers of autonomous access control solutions, announced its participation at the Data Center Forum Helsinki in June 2023. The event was expected to bring together more than 400 data center professionals and provide Alcatraz AI with an ideal opportunity to demonstrate its innovative biometric access control solution for data center physical security.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumption & Market Definition
- 1.2 Scope of the Study
2 Research Methodology
3 Executive Summary
4 Market Dynamics
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Increased Data Center Activities and Investment by the Hyperscale and Colocation Operators
- 4.2.2 Advancements in Video Surveillance Systems Connected to Cloud Systems
- 4.3 Market Restraints
- 4.3.1 Operational and Return On Investment Concerns
- 4.4 Value Chain / Supply Chain Analysis
- 4.5 Industry Attractiveness - Porter's Five Forces Analysis
- 4.5.1 Threat of New Entrants
- 4.5.2 Bargaining Power of Buyers/Consumers
- 4.5.3 Bargaining Power of Suppliers
- 4.5.4 Threat of Substitute Products
- 4.5.5 Intensity of Competitive Rivalry
- 4.6 Assessment of COVID-19 Impact
5 MARKET SEGMENTATION
- 5.1 By Solution Type
- 5.1.1 Video Surveillance
- 5.1.2 Access Control Solutions
- 5.1.3 Others (Mantraps, Fences, and Monitoring Solutions)
- 5.2 By Service Type
- 5.2.1 Consulting Services
- 5.2.2 Professional Services
- 5.2.3 Others (System Integration Services)
- 5.3 End User
- 5.3.1 IT and Telecommunication
- 5.3.2 BFSI
- 5.3.3 Government
- 5.3.4 Healthcare
- 5.3.5 Other End Users
- 5.4 Geography
- 5.4.1 North America
- 5.4.2 Europe
- 5.4.3 Asia
- 5.4.4 South America
- 5.4.5 Middle East
- 5.4.6 Africa
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles
- 6.1.1 Axis Communications AB
- 6.1.2 Convergint Technologies LLC
- 6.1.3 Securitas Technology
- 6.1.4 Bosch Sicherheitssysteme GmbH
- 6.1.5 Johnson Controls International
- 6.1.6 Honeywell International Inc.
- 6.1.7 Schneider Electric
- 6.1.8 AMAG Technology
- 6.1.9 Brivo Systems LLC
- 6.1.10 Suprema Inc.
- 6.1.11 Assa Abloy AB
- 6.1.12 Milestone Systems A/S
- 6.1.13 Cisco Systems Inc.
- 6.1.14 ABB Ltd
- 6.1.15 American Integrated Security Group



















