
|
시장보고서
상품코드
1630170
웹 애플리케이션 방화벽(WAF) 시장 : 시장 점유율 분석, 산업 동향 및 통계, 성장 예측(2025-2030년)Web Application Firewall - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
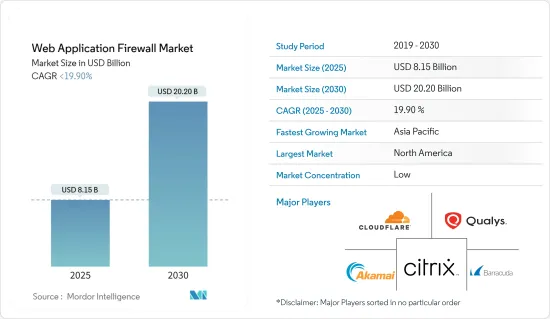
웹 애플리케이션 방화벽 시장 규모는 2025년에 81억 5,000만 달러로 추정되고, 예측 기간 2025년부터 2030년까지의 CAGR은 19.9% 미만으로 전망되며, 2030년에는 202억 달러에 달할 것으로 예측됩니다.

사이버 도둑질과 사기 사건 증가, 데이터와 사이버 보안을 관리하는 정부의 엄격한 정책이 시장 성장의 원동력이 될 것입니다. 또한 웹 기반 앱과 서비스는 오늘날의 비즈니스, 정부, 교육 분야에서 정보 유통 및 정보 교환 방식을 바꾸고 있습니다. 방화벽 시장은 정보의 저비용화와 온라인 및 웹 기반의 광범위한 서비스를 통해 내부 정보 시스템을 더욱 깊게 통합하는 데 점점 더 중요해지고 있습니다.
주요 하이라이트
- 명시적이든 간접적이든, 특정 기업 및 정부 법률은 WAF(Web Application Firewall) 솔루션을 채택해야 합니다. 예를 들어,(PCI-DSS)는 WAF 사용을 지원하는 유명하고 중요한 표준입니다. WAF 기능은 소프트웨어 또는 하드웨어로 구현되며 어플라이언스 장치 또는 동일한 운영 체제를 실행하는 기존 서버에서 작동합니다.
- 또한 온라인 상거래 및 뱅킹 플랫폼을 갖춘 조직은 주로 WAF를 사용하여 업무를 보호하고 기밀성이 높은 소비자 데이터를 보호합니다. 여기에서도 건강 관리에서 방화벽의 사용 증가가 시장을 견인하고 있습니다. WAF는 Wi-Fi 지원 장비 및 기타 관련 장비를 사용하여 중요한 건강 관리 네트워크 및 전자 환자 정보에 대한 무단 액세스를 방지합니다.
- 반면에 웹 애플리케이션 방화벽은 비용과 성능이라는 두 가지 주요 과제에 직면하고 있습니다. 이러한 도구는 용도 계층에서 모든 송수신 정보를 모니터링하기 때문에 일반적으로 성능이 문제가 됩니다. HTTP 및 SMTP와 같은 각 프로토콜에는 프록시 프로그램이 있으며 새 네트워크 애플리케이션 및 프로토콜이 지원되기까지 오랜 시간이 걸릴 수 있습니다.
- 비정상적인 상황 때문에 COVID-19는 지난 2년 동안 웹 애플리케이션 방화벽 솔루션에 대한 수요를 증가시켰습니다. 예를 들어, 많은 기업들은 재택 근무 시스템의 엔드포인트 보호에 보안 노력을 집중시켰습니다. 또한 기업 보안 팀은 여러 온라인 애플리케이션 보안 문제를 해결하기 위해 더 많은 리소스를 필요로 했으며 신뢰할 수 있는 웹 애플리케이션 방화벽에 대한 수요가 증가했습니다.
웹 애플리케이션 방화벽(WAF) 시장 동향
클라우드 기반이 크게 성장
- 웹 애플리케이션 방화벽 시장의 발전은 소셜 미디어 플랫폼의 사용뿐만 아니라 클라우드 기반 기술의 수용 증가에 의해 추진되고 있습니다. 현재 모든 업계에서 클라우드 기술이 널리 사용되고 있으며 기업에 비용 효율적인 보안 솔루션을 제공합니다.
- 클라우드 기반 WAF 솔루션은 멀웨어, 피싱, 랜섬웨어, 새로운 사이버 위협과 같은 취약점에 대한 최상의 방어를 제공하는 위협 방지 기술의 종합적인 스택으로 구성된 소프트웨어 패키지로 제공됩니다. 클라우드 기반 WAF 솔루션은 사용자가 VPN에 연결되어 있지 않아도 네트워크(VPN)를 보호하고 보호합니다. WAF가 제공하는 서비스에는 봇 식별 및 강제, 액세스 제어, 캐시, 위협 인텔리전스, API 보안, 바이러스 감지, 분산 서비스 거부(DDoS) 완화 등이 있습니다.
- 클라우드 컴퓨팅은 언제 어디서나 조작할 수 있는 모델을 가능하게 합니다. 또한 클라우드 도입으로 조직은 소프트웨어 정의 경계와 같은 보완적인 인프라 기술을 통합하여 내구성이 높고 안전한 시스템을 구축할 수 있습니다. 그 결과 클라우드 기반 솔루션의 활용 확대가 웹 애플리케이션 방화벽 시장 점유율 확대를 뒷받침하고 있습니다.
- 클라우드 기반의 서비스 이용이 확대됨에 따라 WAF 솔루션의 수가 증가하고 있으며 예측 기간을 통해 세계의 웹 애플리케이션 방화벽 시장 규모를 높일 것으로 예상됩니다. 게다가 컴플라이언스 요구사항과 보안법(PCI DSS)과(GDPR : EU 개인정보보호규정)의 수가 증가하고 있다는 것은 세계 업계를 추진하고 있습니다.
아시아태평양은 웹 애플리케이션 방화벽 시장에 큰 수요가 기대됩니다.
- 아시아태평양에서는 호주, 중국, 인도, 일본이 클라우드 도입 증가로 인한 주요 경제국이며 BYOD가 성장의 원동력으로 인기를 끌고 있습니다. 리모트 워크와 모바일 워크의 보급과 BYOD의 동향에 의해 해커는 개인 전자 메일을 이용해 타겟을 일부 직원으로부터 네트워크 전체로 확대하고 있습니다. 기업이 클라우드로의 전략적 전환을 계속하면서 네트워크 보안을 강화하기 위해 암호화 및 이메일 아카이브 솔루션과 같은 새롭고 혁신적인 기술에 대한 수요가 증가하고 있습니다.
- 게다가 직원의 위치가 다양해지고 있기 때문에 기업은 견고한 보안 대책에 투자하고 APAC 네트워크 보안 방화벽의 성장을 이끌고 있습니다. 또한 지역 전체의 인구 증가와 생활 수준의 향상도 클라우드 및 BYOD 기술 개발을 뒷받침하고 있습니다. 이처럼 클라우드와 BYOD 기술의 성장은 향후 수년간 네트워크 보안 방화벽에 대한 큰 수요를 창출할 것으로 예상되며, APAC 시장을 더욱 견인할 것으로 예상됩니다.
- 아시아태평양은 GDPR(EU 개인정보보호규정)과 같은 엄격한 규제 프레임 워크와 데이터 보호법이 있기 때문에 수요는 더 빠른 속도로 성장할 것으로 예상됩니다. 또한 클라우드 컴퓨팅, IoT, 5G 등의 기술 채택이 증가하고 있기 때문에 이 지역에서는 혁신적인 보안 솔루션이 요구되고 있습니다.
- 신흥 국가에서 인터넷 사용이 증가함에 따라 보안 솔루션 채택이 증가하고 있습니다. 게다가, 디바이스에 대한 무선 네트워크의 확장으로 인한 데이터 민감성의 향상으로 네트워크 보안은 모든 조직에서 매우 중요한 요소가 되었습니다. 이들은 아시아태평양 시장 수요를 높이는 중요한 요인의 일부입니다.
웹 애플리케이션 방화벽(WAF) 산업 개요
웹 애플리케이션 방화벽은 세분화된 시장입니다. 현재, 웹 애플리케이션 공격의 수가 점점 증가하고, 기업을 위한 새로운 공간을 만들고, 기존 기업은 중소, 대기업으로서 비즈니스 기업으로 세분화되고 있습니다. 경쟁업체 간의 적대관계가 높은 것은 중소규모의 기업입니다. 주요 기업은 Akamai Technologies Inc., F5 Networks Inc., Barracuda Networks Inc., Imperva, Inc. 등입니다.
- 2023년 4월-Akamai Technologies Inc.가 Prolexic Network Cloud Firewall을 발표했습니다. 이 새로운 Akamai Prolexic의 기능을 통해 고객은 액세스 제어 목록(ACL)을 정의하고 관리하면서 아카마이의 클라우드 기반 DDoS 방어 플랫폼이 애플리케이션, 데이터센터 및 인터넷을 향한 인프라에 도달하기 전에 공격을 차단할 네트워크 에지의 보안을 보다 유연하게 확보할 수 있습니다.
- 2023년 4월-바라쿠다 네트웍스는 걸프 지역에서 인그램 마이크로와의 판매 제휴를 발표했습니다. 이 제휴를 통해 Ingram Micro는 UAE, 쿠웨이트, 카타르, 오만, 바레인, 예멘, 파키스탄 리셀러에게 바라쿠다 이메일, 애플리케이션 클라우드, 네트워크 및 데이터 보안 솔루션을 전반적으로 제공할 수 있습니다.
기타 혜택
- 엑셀 형식 시장 예측(ME) 시트
- 3개월간의 애널리스트 서포트
목차
제1장 서론
- 조사의 전제조건
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 인사이트
- 시장 개요
- 밸류체인 분석
- 업계의 매력도-Porter's Five Forces 분석
- 구매자 및 소비자의 협상력
- 공급기업의 협상력
- 신규 진입업자의 위협
- 대체품의 위협
- 경쟁 기업간 경쟁 관계의 강도
제5장 시장 역학
- 시장 성장 촉진요인 및 시장 성장 억제요인의 소개
- 시장 성장 촉진요인
- 사이버 도둑질, 스파이 행위, 파괴 행위, 사기 등의 웹 공격 증가
- 다양한 최종 사용자 용도에서 IoT의 기술적 진보와 보급 확대
- 시장 성장 억제요인
- 어플라이언스형 WAF의 높은 도입 비용
제6장 시장 세분화
- 컴포넌트별
- 솔루션
- 하드웨어 어플라이언스
- 가상 어플라이언스
- 클라우드 기반
- 서비스
- 컨설팅
- 지원 및 유지 보수
- 트레이닝 및 교육
- 전문 서비스
- 시스템 통합
- 솔루션
- 조직 규모별
- 중소기업
- 대기업
- 업계별
- BFSI
- 소매
- IT 및 통신
- 정부 및 방위
- 헬스케어
- 에너지 및 유틸리티
- 교육
- 기타 업계별
- 지역별
- 북미
- 미국
- 캐나다
- 유럽
- 영국
- 독일
- 프랑스
- 기타 유럽
- 아시아태평양
- 중국
- 인도
- 일본
- 기타 아시아태평양
- 세계 기타 지역
- 라틴아메리카
- 중동 및 아프리카
- 북미
제7장 경쟁 구도
- 기업 프로파일
- Akamai Technologies, Inc.
- Barracuda Networks, Inc.
- Cloudflare, Inc.
- Citrix Systems, Inc.
- Qualys, Inc.
- F5 Networks, Inc.
- Imperva, Inc.
- Fortinet, Inc.
- Penta Security Systems Inc.
- Radware Ltd.
- Trustwave Holdings, Inc.
- Nsfocus Information Technology Co., Ltd.
- Sophos Group PLC
제8장 투자 분석
제9장 시장 기회 및 앞으로의 동향
AJY 25.02.05The Web Application Firewall Market size is estimated at USD 8.15 billion in 2025, and is expected to reach USD 20.20 billion by 2030, at a CAGR of less than 19.9% during the forecast period (2025-2030).
Rising cyber theft and fraud incidents and rigorous government policies governing data and cyber security will likely drive market growth. Furthermore, web-based apps and services have changed the nature of information distribution and exchange in today's business, government, and educational sectors. The firewall market is becoming increasingly crucial for the deeper integration of internal information systems because of the low cost of information and the wide range of online and web-based services.
Key Highlights
- Whether expressly or indirectly, specific enterprise and government laws necessitate the adoption of a WAF (Web Application Firewall) solution. For example,(PCI-DSS) is a renowned and significant standard that supports the use of WAF. WAF functionality may be implemented in software or hardware and operate on an appliance device or a conventional server running the same operating system.
- Furthermore, organizations with online commerce and banking platforms primarily use WAFs to safeguard their operations and protect sensitive consumer data. Again, the rising use of firewalls in healthcare is driving the market. WAFs prevent unauthorized access to critical healthcare networks and electronic patient information using Wi-Fi-enabled equipment and other related devices.
- On the other hand, web application firewalls confront two significant challenges: cost and performance. Performance is typically challenging with these tools since they monitor all incoming and outgoing information at the application layer. Each protocol, such as HTTP and SMTP, has its proxy program, and it might take a long time for new network applications and protocols to receive support.
- Due to unusual conditions, the COVID-19 outbreak increased demand for web application firewall solutions during the last two years. Many firms, for example, centered their security efforts on endpoint protection for work-from-home systems. Furthermore, enterprise security teams needed more resources to address multiple online application security concerns, increasing the demand for a reliable web application firewall.
Web Application Firewall (WAF) Market Trends
Cloud-Based to Witness Significant Growth
- Web application firewall market development is being driven by the increased acceptance of cloud-based technologies as well as the use of social media platforms. All industries now widely use cloud technology, providing corporations with cost-effective security solutions.
- Cloud-based WAF solutions are available as software packages that comprise a comprehensive stack of threat prevention technologies that provide the best defense against vulnerabilities such as malware, phishing, ransomware, and new cyber threats. Cloud-based WAF solutions safeguard and protect the network (VPN) even when users are not connected to their VPN. Among the services they offer are bot identification and enforcement, access control, caching, threat intelligence, API security, virus detection, and Distributed Denial of Service (DDoS) mitigation.
- Cloud computing enables the model to operate from anywhere and at any time. Furthermore, cloud deployment allows organizations to integrate supplemental infrastructure technologies such as software-defined perimeters to construct durable and highly secure systems. As a result, the growing usage of cloud-based solutions propels the expansion of the web application firewall market share.
- The growing use of cloud-based services has increased the number of WAF solutions, which is expected to boost the global web application firewall market size throughout the forecast period. Furthermore, the growing number of compliance requirements and security laws (PCI DSS) and (GDPR) propel the global industry.
Asia Pacific Region Expected Significant Demand for Web Application Firewall Market
- Australia, China, India, and Japan are the leading economies in Asia Pacific due to the rising adoption of cloud, and BYOD is gaining popularity as a growth driver. With the proliferation of remote and mobile work and the BYOD trend, hackers have heightened their target from a few employees to the entire network with the help of private emails. As enterprises continue to make strategic shifts to the cloud, they have raised the demand for new and innovative methods, such as encryption and email archiving solutions, to enhance the security of their networks.
- Additionally, as the diversity in the employees' whereabouts continues to expand, the companies are investing in robust security measures, driving the growth of the APAC network security firewalls. The growing population across the region and living standards are also bolstering cloud and BYOD technology development. Thus, the growth of cloud and BYOD technology is expected to create a significant demand for network security firewalls in the coming years, which is further anticipated to drive the market in APAC.
- The demand is expected to grow at a faster pace owing to the stringent regulatory framework and data protection laws like local GDPR; Asia-Pacific is attributed to increasing investments in cyber security by organizations. Also, the increasing adoption of technologies like cloud computing, IoT, and 5G calls for innovative security solutions in the region.
- The growing internet usage in developing countries increases the adoption of security solutions. Further, due to improved data susceptibility brought on by the expansion of the wireless network for devices, network security has become a crucial component of every organization. These are some of the critical factors in the Asia Pacific region that have boosted the market demand.
Web Application Firewall (WAF) Industry Overview
The web application firewall is a fragmented market. Currently, the number of web application attacks is increasingly creating new spaces for the players, and the existing players are segmented into business enterprises as small, medium, and large sectors. The high rivalry is among small and medium players, which the competitive rivalry is high in the market. Key players are Akamai Technologies Inc., F5 Networks Inc., Barracuda Networks Inc., Imperva, Inc., etc.
- April 2023 - Akamai Technologies Inc. launched its Prolexic Network Cloud Firewall. This new Akamai Prolexic ability allows customers to define and manage their access control lists (ACLs) while providing greater flexibility to secure their network edge, where Akamai's cloud-based DDoS protection platform stops attacks before they reach applications, data centers, and internet-facing infrastructure.
- April 2023 - Barracuda Networks Inc. announced a distribution arrangement with Ingram Micro for the Gulf area. Through this partnership, Ingram Micro will be able to provide Barracuda's whole range of email, application cloud, network, and data security solutions to resellers in the UAE, Kuwait, Qatar, Oman, Bahrain, Yemen, and Pakistan.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Value Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Forces Analysis
- 4.3.1 Bargaining Power of Buyers/Consumers
- 4.3.2 Bargaining Power of Suppliers
- 4.3.3 Threat of New Entrants
- 4.3.4 Threat of Substitute Products
- 4.3.5 Intensity of Competitive Rivalry
5 MARKET DYNAMICS
- 5.1 Introduction to Market Drivers and Restraints
- 5.2 Market Drivers
- 5.2.1 Rising Instances of Web Attacks, Such as Cyber Theft, Espionage, Vandalism, and Fraud
- 5.2.2 Technological Advancement and Increasing Penetration of IoT Across Various End-user Applications
- 5.3 Market Restraints
- 5.3.1 High Cost of Deployment for Appliance-based WAF
6 MARKET SEGMENTATION
- 6.1 By Component
- 6.1.1 Solutions
- 6.1.1.1 Hardware Appliances
- 6.1.1.2 Virtual Appliances
- 6.1.1.3 Cloud-Based
- 6.1.2 Services
- 6.1.2.1 Consulting
- 6.1.2.2 Support and Maintenance
- 6.1.2.3 Training and Education
- 6.1.2.4 Professional Services
- 6.1.2.5 System Integration
- 6.1.1 Solutions
- 6.2 By Organization Size
- 6.2.1 Small and Medium-Sized Enterprises
- 6.2.2 Large Enterprises
- 6.3 By Industry Vertical
- 6.3.1 BFSI
- 6.3.2 Retail
- 6.3.3 IT and Telecommunications
- 6.3.4 Government and Defense
- 6.3.5 Healthcare
- 6.3.6 Energy and Utilities
- 6.3.7 Education
- 6.3.8 Other Industry Verticals
- 6.4 By Geography
- 6.4.1 North America
- 6.4.1.1 United States
- 6.4.1.2 Canada
- 6.4.2 Europe
- 6.4.2.1 United Kingdom
- 6.4.2.2 Germany
- 6.4.2.3 France
- 6.4.2.4 Rest of Europe
- 6.4.3 Asia-Pacific
- 6.4.3.1 China
- 6.4.3.2 India
- 6.4.3.3 Japan
- 6.4.3.4 Rest of Asia-Pacific
- 6.4.4 Rest of the World
- 6.4.4.1 Latin America
- 6.4.4.2 Middle East & Africa
- 6.4.1 North America
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 Akamai Technologies, Inc.
- 7.1.2 Barracuda Networks, Inc.
- 7.1.3 Cloudflare, Inc.
- 7.1.4 Citrix Systems, Inc.
- 7.1.5 Qualys, Inc.
- 7.1.6 F5 Networks, Inc.
- 7.1.7 Imperva, Inc.
- 7.1.8 Fortinet, Inc.
- 7.1.9 Penta Security Systems Inc.
- 7.1.10 Radware Ltd.
- 7.1.11 Trustwave Holdings, Inc.
- 7.1.12 Nsfocus Information Technology Co., Ltd.
- 7.1.13 Sophos Group PLC



















