
|
시장보고서
상품코드
1630349
네트워크 보안 방화벽 : 시장 점유율 분석, 산업 동향 및 통계, 성장 예측(2025-2030년)Network Security Firewall - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
■ 보고서에 따라 최신 정보로 업데이트하여 보내드립니다. 배송일정은 문의해 주시기 바랍니다.
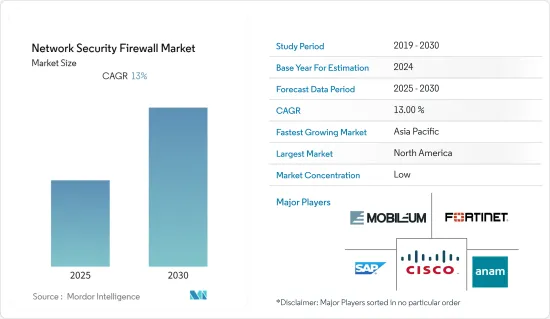
네트워크 보안 방화벽 시장은 예측 기간 동안 CAGR 13%를 기록할 것으로 예상됩니다.
주요 하이라이트
- 네트워크에서 방화벽의 여러 가지 장점, 특히 쉬운 설치와 빠른 속도가 시장 성장을 주도하고 있습니다. 또한, 네트워크에 방화벽을 도입하는 것은 각 컴퓨터를 개별적으로 보호하는 것보다 훨씬 저렴합니다. 그러나 예방적 방화벽 유지보수 인프라의 부족과 하드웨어 및 시스템 호환성 부족은 시장 성장을 저해하는 주요 요인으로 작용하고 있습니다.
- 불법 액세스 및 정보 악용으로부터 통신 경로를 보호하고 부정 행위 및 데이터 침해로부터 기업을 보호하기 위해 외부 네트워크와 내부 네트워크 간의 네트워크 보안을 유지해야 할 필요성이 증가함에 따라 시장 확대와 성장을 주도하고 있습니다.
- 또한, 웹 애플리케이션의 급속한 사용, 클라우드 기술의 급속한 도입, 사이버 공격의 위험을 줄이기 위한 보안 서비스에 대한 수요 증가도 네트워크 보안 방화벽 시장의 성장을 촉진하고 있습니다. 보안 침해 및 사이버 공격으로부터 데이터와 정보를 보호하기 위해 다양한 최종 사용 기업에서 네트워크 보안 방화벽 도입이 확대되고 있습니다. 이는 전체 네트워크 보안 방화벽 시장의 성장을 견인하고 있습니다.
- 코로나 바이러스(COVID-19)의 대유행으로 인해 한편으로는 세계 경제의 주요 부분이 멈춰 섰습니다. 다른 한편으로는 혼란과 불확실성을 이용해 사기 및 피싱 기법을 발전시키려는 악의적인 목적을 가진 사람들이 존재하며, 이는 전 세계 모든 사람들에게 큰 위협이 되고 있습니다.
- Google은 최근 4월 6일부터 13일까지 단 1주일 동안 COVID-19 사기 관련 악성코드 및 피싱 메일이 하루 1,800만 건 이상, 코로나 바이러스 관련 스팸 메일이 하루 2억 4,000만 건 이상 발생했다고 보고했습니다. 방화벽은 상시 연결의 중요한 보안 구성요소이며, 조직은 네트워크 인프라를 보호하기 위해 네트워크 방화벽이 필요하기 때문에 이러한 활동의 증가로 인해 네트워크 보안 방화벽 시장이 성장할 가능성이 높습니다. 성장 가능성이 높습니다.
네트워크 보안 방화벽 시장 동향
솔루션 부문이 큰 성장세를 보일 것으로 전망
- 사기, 사용자 위치 추적, 서비스 거부(DoS) 등 SS7의 취약점을 탐지하고 보호하기 위한 통신 서비스 제공업체의 보안 프로토콜이 지속적으로 개발됨에 따라 솔루션 부문이 전 세계 네트워크 보안 방화벽 시장의 대부분을 점유하고 있습니다. 차지하고 있습니다.
- 지난 9월, 넷스코프는 클라우드 방화벽 솔루션의 기능 강화를 발표했습니다. 회사에 따르면 SASE 플랫폼의 FWaaS(Firewall-as-a-Service) 구성요소는 고객이 운영을 단순화하고 위협을 방지하며 사용자가 어디에 있든 전 세계적으로 일관된 방화벽 커버리지를 제공 할 수 있도록 설계되었습니다.
- 또한, 통신사업자들이 SMS 방화벽 솔루션의 채택을 확대함에 따라 솔루션 부문은 예측 기간 동안 가장 빠른 CAGR을 기록할 것으로 예상되며, SMS 방화벽 솔루션은 통신사업자의 네트워크에서 악성코드를 탐지하는 네트워크 보안 방화벽 애플리케이션에 사용됩니다. 네트워크 보안 방화벽 애플리케이션에 사용됩니다.
- 통신 산업에서 직경 공격의 증가로 인해 방화벽 솔루션 도입이 증가하고 있으며, 이는 네트워크 보안 방화벽 솔루션 시장의 성장에 기여하고 있습니다.
북미가 가장 큰 시장 점유율을 차지
- 북미는 네트워크 보안 방화벽 시장에서 가장 큰 점유율을 차지하고 있으며, 이 지역에는 여러 주요 네트워크 보안 제공업체가 존재하기 때문에 예측 기간 동안에도 그 우위를 유지할 것으로 예상됩니다.
- 또한 북미는 모바일 보안 기술의 급속한 발전으로 인해 향후 몇 년 동안 네트워크 보안 방화벽 시장 수익에서 가장 큰 점유율을 차지할 것으로 예상됩니다. 이 지역의 큰 점유율은 주로 사이버 공격이 크게 증가함에 따라 데이터 보안에 대한 막대한 투자에 기인합니다.
- 지난 몇 년 동안 많은 사이버 공격이 북미의 조직을 표적으로 삼고 있습니다. 이로 인해 방화벽 솔루션에 대한 인식이 높아지면서 다양한 지역의 주요 기업에서 방화벽 솔루션을 채택하여 시장 성장에 기여하고 있습니다.
- 이 지역에서는 국가 및 개인에 의한 사이버 공격과 랜섬웨어 공격이 활발히 일어나고 있습니다. 예를 들어, CISA(Cybersecurity and Infrastructure Security Agency)와 미국 연방수사국(FBI)에 따르면, 러시아는 2022년 2월 말 러시아의 침공 시 우크라이나의 지휘통제를 혼란에 빠뜨리기 위해 상업용 위성통신망에 대한 사이버 공격을 감행했습니다. 사이버 공격을 실시하여 다른 유럽 국가로 파급되었습니다.
- 진화하는 인텔리전스에 따르면, 러시아 정부는 향후 사이버 공격에 대한 대안을 검토하고 있습니다. 최근 러시아 국가 주도의 사이버 작전에는 우크라이나 정부 및 주요 인프라 기업에 대한 분산서비스거부(DDoS) 공격과 유해한 악성코드 배포 등이 포함됩니다.
- 미국 해커들에게도 정부 인프라와 비상장 기업은 주요 공격 대상입니다. 예를 들어, 2021년 8월 중국 해커 집단인 Hafnium은 Microsoft Exchange의 취약점을 발견하여 미국 내 최소 3만 개, 전 세계 25만 개의 이메일 계정에 대한 액세스를 제공했습니다. 서버의 취약점을 패치하기 시작한 직후부터 최소 10개 이상의 지능형지속위협 그룹이 코인 채굴과 스파이 활동을 위해 보안 허점을 악용하기 시작했습니다.
네트워크 보안 방화벽 산업 개요
네트워크 보안 방화벽 시장은 매우 세분화되어 있습니다. 주요 기업들은 신제품 출시, 사업 확장, 계약, 합작투자, 파트너십, 인수 등의 전략을 통해 이 시장에서 입지를 넓혀가고 있습니다. 주요 시장 개척은 다음과 같습니다.
- 2022년 8월 - 컴캐스트 비즈니스(Comcast Business)가 포괄적이고 통합적이며 자동화된 사이버 보안 솔루션 분야의 세계 리더인 포티넷(Fortinet(R))과의 전략적 제휴를 발표했습니다. 이번 제휴를 통해 기업들은 보안 서비스 엣지(SASE)와 보안 서비스 엣지(SSE)의 새로운 솔루션 세트를 제공받게 되며, 클라우드 기반 접근 방식을 통해 분산된 인력을 보호하고, Comcast Business의 매니지드 서비스 전문성을 확장합니다.
- 2022년 8월 - IT 및 네트워크 기술 통합 분야의 선도기업인 NEC Corporation과 포괄적이고 통합적이며 자동화된 사이버 보안 솔루션 분야의 세계 리더인 Fortinet(R)이 통신 서비스 제공업체(CSP)를 위한 안전한 5G 네트워크를 구축하기 위한 국제 계약을 체결했습니다. 통신 서비스 제공업체(CSP)를 위한 안전한 5G 네트워크를 공동 구축하기 위한 국제적인 계약을 체결했습니다. 이번 제휴를 통해 포티넷은 세계에서 가장 많이 도입된 차세대 방화벽이자 가장 고성능의 하이퍼스케일 방화벽인 포티게이트(FortiGate)를 포함한 포괄적이고 동급 최강의 보안 솔루션을 제공하게 됩니다. 동시에 NEC는 통신 산업에서 입증된 전문성을 바탕으로 5G에 필요한 캐리어급 지속가능한 네트워킹을 구현할 수 있는 전문 서비스를 제공합니다.
기타 혜택
- 엑셀 형식의 시장 예측(ME) 시트
- 3개월간의 애널리스트 지원
목차
제1장 소개
- 조사 가정과 시장 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 역학
- 시장 개요
- 시장 성장 촉진요인
- 차세대 네트워크 기술의 도입
- 네트워크 보안 애플리케이션 방화벽을 장려하는 행정 규제
- 통신 산업의 디지털 변혁 진전
- 시장 성장 억제요인
- 기본적인 네트워크 방화벽 복구 부재
- 산업 밸류체인 분석
- 산업의 매력 - Porter's Five Forces 분석
- 신규 참여업체의 위협
- 구매자/소비자의 협상력
- 공급 기업의 교섭력
- 대체품의 위협
- 경쟁 기업 간의 경쟁 강도
- COVID-19가 네트워크 보안 방화벽 시장에 미치는 영향 평가
제5장 시장 세분화
- 구성요소별
- 솔루션
- 시그널링 방화벽
- SMS 방화벽
- 서비스
- 매니지드 서비스
- 전문 서비스
- 솔루션
- 유형별
- 패킷 필터링
- 스테이트 풀 패킷 인스펙션
- 차세대 방화벽
- 통합 위협 관리
- 전개별
- 온프레미스
- 클라우드
- 네트워크 기능 가상화(NFV)
- 최종사용자별
- 통신·IT
- BFSI
- 교육
- 소비재·소매
- 제조업
- 의료 생명과학
- 기타
- 지역별
- 북미
- 유럽
- 아시아태평양
- 기타
제6장 경쟁 구도
- 기업 개요
- SAP SE
- Cisco System Inc.
- Mobileum Inc
- ANAM Technologies
- Fortinet Inc.
- BICS SA
- Cellusys
- Amd Telecom Private Limited
- NetNumber Inc.
- Openmind Networks
- Juniper Networks Inc.
- Watchguard Technology Inc.
- Checkpoint Software Technology Limited
- Palo Alto Networks Inc.
제7장 투자 분석
제8장 시장 기회와 향후 동향
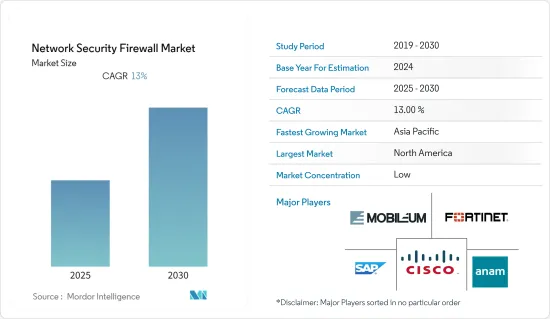
ksm 25.01.23The Network Security Firewall Market is expected to register a CAGR of 13% during the forecast period.
Key Highlights
- Owing to the numerous advantages of a firewall in a network, especially the easy installation and the high speed are fuelling the market growth. Additionally, implementing a firewall for a network is also much less costly than having to secure each computer individually. However, the lack of preventive firewall maintenance infrastructure and poor hardware and system compatibility are a few major factors hindering the market growth.
- The increasing need to secure communication paths from unlawful access and information misuse and maintain network safety between the external and internal networks to safeguard the company from fraud and data violations is helping the market expand and grow.
- The rapid use of web applications, rapid adoption of cloud technologies, and the increasing demand for security services to mitigate the risk of cyberattacks are also driving the growth of the network security firewall market. To protect the data & information from security breaches and cyber-attacks, the implementation of network security firewalls is growing across various end-use enterprises. Consequently, driving the growth of the overall network security firewalls market.
- Due to the coronavirus (Covid-19) pandemic, on one side, there is shutting down major parts of the global economy. On the other side, there are those with nefarious ends who are trying to take advantage of chaos and uncertainty and are evolving scams and phishing techniques which is a big threat to everyone globally.
- Google recently reported that in just one week, from 6 to 13 April, it saw more than 18 million daily malware and phishing emails related to Covid-19 scams, and that's in addition to the 240 million daily spam messages it saw related to coronavirus. Due to the rise in such activities network security firewall market is likely to grow as the firewall is a critical security component for connections that are always on, and organizations need network firewalls to protect network infrastructure.
Network Security Firewall Market Trends
Solution Segment is Expected to Witness Significant Growth
- The solution segment claimed the majority of share in the global network security firewall market owing to the continuous development in security protocols of telecom service providers to detect and protect against SS7 vulnerabilities, such as fraud, user location tracking, and denial of service (DoS).
- In September 2022, Netskope launched enhancements to the cloud firewall solution. The company states that the firewall-as-a-service (FWaaS) component of its converged SASE platform is designed to help customers simplify operations, prevent threats, and provide consistent firewall coverage worldwide anywhere their users are located.
- The solutions segment is also expected to witness the fastest CAGR over the forecast period owing to telecom organizations' growing adoption of SMS firewall solutions. SMS firewall solutions are used in network security firewall applications to detect malware over the operator's network.
- The growing number of diameter attacks in the telecom industry also supports the deployment of firewall solutions, thus, contributing to the growth of the network security firewall solutions market.
North America to Account for Largest Market Share
- North America accounted for the largest share of the network security firewall market and is expected to maintain its dominance throughout the forecast period as the region is home to several leading network security providers.
- North America is also anticipated to capture the largest share of the network security firewalls market in terms of revenue over the coming years, owing to rapid advancements in mobile security technologies in this region. The large share of this region is mainly attributed to its considerable investments in data security due to the significant rise in cyber-attacks.
- Over the past few years, many cyberattacks have targeted organizations in the North American region. This has led to a greater awareness of firewall solutions and their adoption among major companies across different regional sectors, thus contributing to market growth.
- The region is active in state-sponsored and individual cyberattacks and ransomware attacks. For instance, according to the CISA (Cybersecurity and Infrastructure Security Agency) and the Federal Bureau of Investigation (FBI) US, Russia conducted cyberattacks against commercial satellite communications networks in late February 2022 to disrupt Ukrainian command and control during the Russian invasion, with spillover effects in other European countries.
- According to evolving intelligence, the Russian government is considering alternatives for prospective cyberattacks. Recent Russian state-sponsored cyber operations have included distributed denial-of-service (DDoS) attacks against the Ukrainian government and critical infrastructure companies and the deployment of harmful malware.
- The government infrastructure and private companies are also major targets for hackers in the United States. For instance, in August 2021, Hafnium, a Chinese hacker gang, discovered Microsoft Exchange vulnerabilities that provided them access to the email accounts of at least 30,000 firms in the United States and 250,000 globally. At least ten more advanced persistent threat groups began exploiting the security holes for coin mining and espionage shortly after Microsoft publicized the problems and began patching the email server vulnerabilities.
Network Security Firewall Industry Overview
The network security firewall market is highly fragmented. The major players use strategies such as new product launches, expansions, agreements, joint ventures, partnerships, acquisitions, and others to increase their footprints in this market. Some of the key developments in the market are:
- August 2022 - Comcast Business announced a strategic partnership with Fortinet(R), a global leader in comprehensive, integrated, and automated cybersecurity solutions. This collaboration will deliver enterprises a new set of secure access service edge (SASE) and security service edge (SSE) solutions to help enterprises protect their distributed workforces using a cloud-delivered approach to security policy enforcement and expand Comcast Business's managed services expertise.
- August 2022 - NEC Corporation, a leader in the integration of IT and network technologies, and Fortinet(R), a global leader in comprehensive, integrated, and automated cybersecurity solutions, have entered an international agreement to jointly build secure 5G networks for communication service providers (CSPs). Through the partnership, Fortinet will provide its comprehensive, best-in-class security solutions, including FortiGate - the world's most deployed next-generation firewall and highest performing hyper-scale firewall. At the same time, NEC will offer professional services built on its solid track record in the telecom industry to deliver carrier-grade, sustainable networking required in 5G.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Implementation of Next-Generation Networking Technologies
- 4.2.2 Administrative Regulations Encouraging Network Security Application Firewall
- 4.2.3 Advancement of Digital Transformation in the Telecommunications Industry
- 4.3 Market Restraints
- 4.3.1 The Absence of Basic Network Firewall Restoration
- 4.4 Industry Value Chain Analysis
- 4.5 Industry Attractiveness - Porter's Five Forces Analysis
- 4.5.1 Threat of New Entrants
- 4.5.2 Bargaining Power of Buyers/Consumers
- 4.5.3 Bargaining Power of Suppliers
- 4.5.4 Threat of Substitute Products
- 4.5.5 Intensity of Competitive Rivalry
- 4.6 Assessment of Impact of Covid-19 on the Network Security Firewall Market
5 MARKET SEGMENTATION
- 5.1 By Component
- 5.1.1 Solutions
- 5.1.1.1 Signaling Firewall
- 5.1.1.2 SMS Firewall
- 5.1.2 Services
- 5.1.2.1 Managed Services
- 5.1.2.2 Professional Services
- 5.1.1 Solutions
- 5.2 By Type
- 5.2.1 Packet Filtering
- 5.2.2 State full Packet Inspection
- 5.2.3 Next Generation Firewall
- 5.2.4 Unified Threat Management
- 5.3 By Deployment
- 5.3.1 On-Premises
- 5.3.2 Cloud
- 5.3.3 Network Functions Virtualization (NFV)
- 5.4 By End-User
- 5.4.1 Telecommunication and IT
- 5.4.2 BFSI
- 5.4.3 Education
- 5.4.4 Consumer Goods and Retail
- 5.4.5 Manufacturing
- 5.4.6 Healthcare and Life Sciences
- 5.4.7 Other End-Users
- 5.5 By Geography
- 5.5.1 North America
- 5.5.2 Europe
- 5.5.3 Asia-Pacific
- 5.5.4 Rest of the World
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles
- 6.1.1 SAP SE
- 6.1.2 Cisco System Inc.
- 6.1.3 Mobileum Inc
- 6.1.4 ANAM Technologies
- 6.1.5 Fortinet Inc.
- 6.1.6 BICS SA
- 6.1.7 Cellusys
- 6.1.8 Amd Telecom Private Limited
- 6.1.9 NetNumber Inc.
- 6.1.10 Openmind Networks
- 6.1.11 Juniper Networks Inc.
- 6.1.12 Watchguard Technology Inc.
- 6.1.13 Checkpoint Software Technology Limited
- 6.1.14 Palo Alto Networks Inc.
7 INVESTMENT ANALYSIS
8 MARKET OPPORTUNITIES AND FUTURE TRENDS
샘플 요청 목록

















