
|
시장보고서
상품코드
1630394
컨텐츠 무해화 및 재조합 : 시장 점유율 분석, 산업 동향 및 통계, 성장 예측(2025-2030년)Global Content Disarm and Reconstruction - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
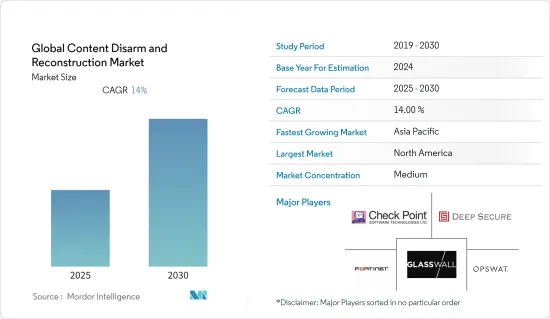
세계의 컨텐츠 무해화 및 재조합 시장은 예측 기간 중에 CAGR 14%를 기록할 전망입니다.

주요 하이라이트
- 랜섬웨어에 의한 피해액은 2015년 약 2억 6,000만 달러에서 두배로 늘었고, 2021년에는 전 세계적으로 150억-160억 달러에 달할 것으로 예측됩니다. 이러한 공격의 급격한 증가로 시장은 1,000건 이상의 거래에 투자자에 의한 기록적인 자금 유입을 목격했으며, 그중 84건은 1억 달러 이상의 거래였습니다.
- Momentum Cyber는 또한 이러한 거래에 산업 사이버 보안 신흥 기업인 Dragos가 확보한 2억 달러의 시리즈 D 투자, Claroty의 1억 4,000만 달러의 사전 IPO 조달, 비밀번호가 없는 인증 회사 Transmit Security가 조달했습니다. 5억 4,300만 달러의 시리즈 A 등이 포함되어 있음을 시사했습니다. 게다가 자금조달 총액은 전년 대비 138%가 되었습니다. 이 역사적인 투자액의 결과, 2021년에는 과거 최다 보안 신흥 기업이 유니콘으로 선출되었습니다. 작년에는 불과 6개 기업이었지만 Wiz, Noname Security, LaceWork 등 30개 이상의 신흥 기업이 10억 달러를 초과하는 가치를 달성했습니다.
- 클라우드 기반 보안 솔루션이 수락되고 보안 위협에 대한 인식이 높아지고 연결된 IoT 디바이스용 사이버 보안 솔루션이 개발되고 있기 때문에 시장 확대가 예상되고 있습니다. 또한 IT 동향의 변화와 클라우드 솔루션의 채용 증가로 조직의 데이터, 브랜드 가치, 아이덴티티를 보호하기 위해 활용되는 컨텐츠 무해화 및 재조합 솔루션의 잠재적인 성장 전망이 열리고 있습니다.
- 또한 일반 데이터 보호 규제(GDPR(EU 개인정보보호규정))의 구현을 통해 기밀 개인 정보의 지속적인 보안 유출을 해결하기 위해 정부와 규제 기관은 컨텐츠 보안에 대한 보다 강력한 컴플라이언스 및 규제 규범을 더욱 기대할 수 있도록 되어 있습니다. 세계 각국의 정부가 디지털화와 IT 인프라의 변화에 상당한 비용을 투자하는 가운데, 컨텐츠 무해화 및 재조합 솔루션 수요가 높아지고 있습니다.
- 또한 Swissinfo.ch는 NCSC(국가 사이버 보안 센터)가 보고한 사이버 공격(피싱, 가짜 사이트, 조직에 대한 직접 공격 등)은 350건으로 발생 건수는 100-150건이었습니다고 말합니다. 재택근무 증가는 코로나 바이러스의 대유행이 원인이며, 재택근무자는 직장환경에서와 같은 본질적인 보호·억지책(인터넷·보안 등)이 부족하기 때문입니다. 이러한 침해의 위협은 악의적인 공격자가 네트워크 경계에 침입하는 것을 방지하기 위해 세계 컨텐츠 무해화 및 재조합 시장에 유리한 기회를 가져올 것으로 보입니다.
컨텐츠 무해화 및 재조합 시장 동향
예측 기간 동안 중소기업 부문의 성장 속도가 증가
- 중소기업 부문은 데이터 보호 규제 강화와 네트워크 인프라 내 고비용 보안 솔루션 부족으로 예측 기간 동안 더 높은 CAGR로 성장할 것으로 예측됩니다. 중소기업은 규모가 작지만 세계적으로 보면 엄청난 수의 고객에게 서비스를 제공합니다. 중소기업에서는 재정적인 제약이 있기 때문에 견고하고 종합적인 컨텐츠 무해화 및 재조합 솔루션은 도입되지 않았습니다. 사이버 보안이 취약하고 예산이 적기 때문에 중소기업은 데이터 유출이나 개인 정보 도난의 영향을 받기 쉽습니다.
- 중소기업은 비용 효율적인 클라우드 배포 모델을 신속하게 채택하므로 클라우드 배포 모드는 높은 CAGR로 성장할 것으로 예상됩니다. 중소기업 간에는 소비자 클라우드 서비스, 파일 공유, CRM, 이메일, 채팅, 사내 커뮤니케이션 등을 위해 PaaS와 IaaS를 활용하는 경향이 커지고 있습니다. 온프레미스 네트워크를 유지하면서도 중소기업은 새로운 기술을 채택함에 따라 클라우드를 자체 네트워크 인프라에 통합하는 데 적극적으로 참여하고 있습니다.
- 전반적으로 중소기업은 경쟁을 극복하기 위해 효과적인 전략을 채택할 수 있는 큰 기회를 누리고 있으며, 클라우드는 그 과정에서 중요한 역할을 합니다. 예를 들어 Microsoft가 최근 실시한 조사에서는 중소기업이 클라우드 컴퓨팅을 도입할 의욕이 있는지를 파악하기 위해 16개국 중소기업 3,000개 이상을 대상으로 조사를 실시했습니다. 그 결과 3년 이내에 43%의 워크로드가 유료 클라우드 서비스가 되는 것으로 나타났습니다.
- 클라우드 솔루션은 중소기업 경영자에게 다양한 이점을 제공합니다. 클라우드 솔루션의 확장성과 유연성을 통해 경쟁 우위를 활용하여 신속하게 전진할 수 있습니다. 예를 들어, Apogaeis Technologies LLP는 많은 세계 소규모 기업들에게 SaaS와 PaaS 솔루션을 제공하며, 비즈니스 프로세스 전체에 부가가치를 부여하고 있습니다.
- 또한 2021년 3월 보안 기관에 따르면 온프레미스 Microsoft Exchange 서버에 대한 공격이 증가하고 있습니다. 중소기업은 전자 메일 서버를 자주 사용합니다. 그러므로 이러한 공격은 그들에 대해 이루어졌습니다. 이러한 이유로 Microsoft는 온프레미스에서 Microsoft Exchange 서버를 사용하는 고객을 위해 한 번의 클릭으로 작업할 수 있는 새로운 완화 도구를 도입했습니다. 패치 및 업데이트 프로세스에 익숙하지 않은 고객은 이 혜택을 누릴 수 있습니다.
북미가 최대 시장 규모
- 북미는 컨텐츠 무해화 및 재조합 솔루션, 서비스 벤더에게 가장 큰 수익을 창출하는 지역이 될 것으로 보입니다. 랜섬웨어, APT, 제로 데이 공격 증가, 멀웨어 및 파일 기반 공격 증가 등이 북미 시장 성장을 가속하는 주요 요인이 되고 있습니다.
- 북미에는 미국과 캐나다와 같은 주요 경제권이 포함되어 있으며 CDR 솔루션이 빠르게 활용되고 있습니다. 이 지역의 CDR 시장은 iT 시스템을 멀웨어로부터 보호하기 위한 사전 예방적인 보안 대책으로 주목을 받고 있습니다. 이 지역의 중소기업과 대기업은 CDR 서비스를 강하게 인식하게 되어 사이버 위협과 싸우기 위해 이용하기 시작하고 있습니다.
- 정부와 민간 사업체의 이익을 지키기 위해 향후 몇 년간의 인프라 사이버 보안의 지도를 그릴 것으로 예상되는 다양한 대처가 개시되고 있습니다. 예를 들어, 미국은 2021년 3월, 이 나라의 에너지 시스템의 보안을 보호하기 위해 새롭게 3개의 연구 프로그램을 시작할 계획을 발표했습니다. DOE의 사이버 보안, 에너지 보안 및 긴급 대응국(CESER)은 미국의 에너지 시스템을 증대하는 사이버 위험과 물리적 위험으로부터 보호하기 위한 새로운 프로그램을 발표했습니다. 이와 같은 이니셔티브는 이 분야에서 솔루션을 채택하는 길을 열어줄 것으로 기대됩니다.
- 또한 미국 행정관리예산국에 따르면 미국 정부는 2021년 사이버 보안 예산으로 187억 8,000만 달러를 제안하고, 정부의 안전을 확보하고, 중요한 인프라와 필수 기술의 보안을 강화하기 위한 광범위한 사이버 보안 전략을 지원합니다. 캘리포니아 주에서는 사이버 범죄로 인한 손실액이 5억 7,300만 달러를 넘어 2위 뉴욕주의 2억 9,300만 달러의 거의 두 배에 달한다고 IC3는 말합니다.
- 북미 시장은 컨텐츠 무해화 및 재조합 솔루션이 데이터 침해를 저지하는 프로액티브한 보안 수단을 제공함으로써 견인력을 획득하고 있습니다. 중소기업이나 지역 대기업은 컨텐츠 무해화 및 재조합의 프로세스와 그 이점을 보다 의식하게 되어 사이버 사기나 데이터 도난에 대항하기 위해 도입하기 시작했습니다.
컨텐츠 무해화 및 재조합 산업 개요
컨텐츠 무해화 및 재조합 시장은 적당한 경쟁하는 여러 주요 기업으로 구성되어 있습니다. 세계 서비스를 제공하는 주요 공급업체는 Check Point Software Technologies, Fortinet, Deep Secure, Sasa Software, ReSec Technologies, OPSWAT 등입니다. 이러한 제공업체들은 신제품 출시, 파트너십, 제휴, 인수 등 다양한 유기적·무기적 성장 전략을 채택하여 컨텐츠 무해화 및 재조합 시장에서의 제공을 확대하고 있습니다.
- 2022년 7월 : 중요 인프라 보호(CIP)를 위한 사이버 보안 및 CDR 솔루션인 OPSWAT는 데이터 보호 범주에서 Amazon Web Services(AWS)의 보안 역량을 획득했다고 발표했습니다. 이 인증은 OPSWAT가 데이터 보호의 사이버 보안 전문성을 고객에게 제공하고 클라우드 보안 목표 달성을 지원할 수 있음을 입증하여 AWS의 기술 및 품질 요구 사항을 충족하는 데 성공했습니다.
- 2022년 3월 : 컨텐츠 무해화 및 재조합 기술 제공업체인 Glasswall은 최근 시장을 석권하는 데스크톱 CDR 툴의 프리미엄 버전인 '글라스월 데스크톱 프리덤'을 제공하기 시작했습니다. 이것은 사용자가 모든 파일을 신뢰할 수 있도록 감지를 기다리지 않는 보호 기능을 제공합니다. 이 기술은 멀웨어 및 랜섬웨어와 같은 파일 기반 공격의 위험으로부터 공공 및 민간 부문의 조직을 보호하기 위해 개발되었습니다. 사용자는 첫 다운로드일로부터 12개월 동안 프리미엄 버전에 액세스할 수 있습니다.
기타 혜택 :
- 엑셀 형식 시장 예측(ME) 시트
- 3개월간의 애널리스트 서포트
목차
제1장 서론
- 조사의 전제조건과 시장 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 역학
- 시장 개요
- 시장 성장 촉진요인
- Ransomware, Apts, Zero-Day 공격 증가
- 엄격한 규제와 컴플라이언스 강화
- 악성코드 및 파일 기반 공격 증가
- 시장 성장 억제요인
- 컨텐츠 무해화 및 재조합 솔루션 도입의 예산상의 장벽
- 업계의 매력 - Porter's Five Forces 분석
- 공급기업의 협상력
- 소비자의 협상력
- 신규 진입업자의 위협
- 대체품의 위협
- 경쟁 기업 간 경쟁 관계의 강도
- COVID-19의 업계에 대한 영향 평가
제5장 시장 세분화
- 구성 요소별
- 솔루션
- 서비스
- 배포 모드별
- 온프레미스
- 클라우드
- 용도별
- 이메일
- 웹
- 파일 전송 프로토콜
- 기타 용도 분야
- 조직 규모별
- 중소기업
- 대기업
- 업계별
- BFSI
- IT 및 통신
- 정부기관
- 제조업
- 헬스케어
- 기타 업계별
- 지역별
- 북미
- 유럽
- 아시아태평양
- 라틴아메리카
- 중동 및 아프리카
제6장 경쟁 구도
- 기업 프로파일
- Fortinet, Inc.
- Check Point Software Technologies
- OPSWAT, Inc.
- Deep Secure Inc.
- Re-Sec Technologies Ltd.
- Votiro Inc.
- Glasswall Solutions Limited
- Sasa Software(CAS) Ltd.
- Peraton Corporation
- YazamTech Inc.
- Jiransecurity Ltd.
- Mimecast Services limited.
- SoftCamp Co., Ltd.
- Cybace Solutions
제7장 투자 분석
제8장 시장 기회와 앞으로의 동향
KTH 25.02.05The Global Content Disarm and Reconstruction Market is expected to register a CAGR of 14% during the forecast period.
Key Highlights
- The ransomware damages are predicted to reach a global number of USD 15-16 billion in 2021, up many times from the global damages it achieved in 2015, which was around USD 260 million. Owing to such a rapid increase in attacks, the market witnessed a record influx of capital by investors into more than 1,000 deals, of which 84 were more significant than USD 100 million.
- The Momentum Cyber also suggested that these transactions included a USD 200 million Series D investment secured by industrial cybersecurity startup Dragos, Claroty's USD 140 million pre-IPO raise, and the USD 543 million Series A raised by passwordless authentication company Transmit Security. Additionally, the total financing value was 138% over the previous year. As a result of this historic investment volume, a record number of security startups were minted as unicorns in 2021. More than 30 startups achieved USD 1 billion-plus valuations, including Wiz, Noname Security, and LaceWork, compared to just six startups the previous year.
- The market is expected to rise due to the rising acceptance of cloud-based security solutions, increased awareness of security threats, and the developing of cybersecurity solutions for connected IoT devices. Furthermore, shifting IT trends and the increasing adoption of cloud solutions are opening potential growth prospects for content disarm and reconstruction solutions, which are utilized to protect an organization's data, brand value, and identity.
- Furthermore, with implementing the general data protection regulation (GDPR) to help combat persistent security leaks of sensitive personal information, governments and regulatory bodies are increasingly expecting more robust compliance and regulation norms for content security. The demand for content disarm, and reconstruction solutions are growing as governments across the globe spend extensively on digitalization and the transformation of IT infrastructure.
- Further, Swissinfo.ch stated that the NCSC (National Cyber Security Center) reported 350 cyberattacks (phishing, fake websites, direct attacks on organizations, etc.), compared to 100-150 occurrences. The increase in working from home was attributed to the coronavirus pandemic, as persons working at home lack the same intrinsic protection and deterrent measures as those in a working environment (e.g., internet security). The threat of such breaches will create lucrative opportunities for the global content disarm and reconstruction market to prevent malicious attackers from entering the network perimeter.
Content Disarm and Reconstruction Market Trends
SMEs Segment to Grow at a Higher Pace During the Forecast Period
- The SME segment is anticipated to grow at a higher CAGR during the forecast period due to the growing data protection regulations and scarcity of high-cost security solutions within the network infrastructure. SMEs are small in terms of size but cater to a vast number of clients globally. The robust and comprehensive content disarm, and reconstruction solution is not implemented in SMEs due to financial constraints in these organizations. Weak cybersecurity and low budget make SMEs more susceptible to data breaches and identity thefts.
- The cloud deployment mode is expected to grow at a higher CAGR as Small and Medium-sized Enterprises (SMEs) quickly adopt the cost-effective cloud deployment model. There is an increasing trend of PaaS and IaaS among SMBs for consumer cloud services, file sharing, CRM, email, chat, and internal communication. While retaining the on-premise network, SMBs are more willing to integrate the cloud into their network infrastructure as they adopt new technologies.
- Overall, SMBs have great opportunities to adopt effective strategies to stand in the competition, and the cloud has a vital role in the process. For instance, a recent study done by Microsoft surveyed more than 3,000 SMEs across 16 countries to understand whether SMEs have an appetite for adopting Cloud computing. One of the findings was that within three years, the workloads of 43 % would become paid Cloud services.
- Cloud Solutions offers a gamut of advantages to small and medium business owners. With the scalability and flexibility of cloud solutions, one can quickly move forward by taking competitive advantages. For instance, Apogaeis Technologies LLP provides SaaS and PaaS solutions to many global SMEs and adds value to their entire business process.
- Moreover, in March 2021, Attacks on on-premise Microsoft Exchange servers have increased, according to security agencies. Small and medium-sized enterprises frequently use email servers. Therefore, these attacks were carried out on them. For these reasons, Microsoft has introduced a new one-click Mitigation Tool for clients with Microsoft Exchange servers on-premise. Customers who are inexperienced with the patch/update process will benefit from this.
North America to Account for the Largest Market Size
- North America is supposed to become the most significant revenue-generating area for content disarm, reconstruction solutions, and service vendors. The growing number of ransomware, APTs, zero-day attacks, and the mounting amount of malware and file-based attacks are some of the principal factors anticipated to feed the market growth in North America.
- North America includes major economies, such as the United States of America and Canada, quickly using the CDR solution. The CDR market in the region is getting traction as it gives proactive security measures for securing I.T. systems from malware. SMEs and large companies in the area have become highly aware of CDR services and have begun using them to fight cyber threats.
- To safeguard the interest of governments and private entities, various initiatives have been launched that are expected to draw the map for infrastructure cybersecurity over the coming years. For example, in March 2021, the United States announced its plans to launch three new research programs to protect the security of the country's energy system. The DOE Office of Cybersecurity, Energy Security, and Emergency Response (CESER) announced new programs to help safeguard the U.S. energy system from increasing cyber and physical hazards. Such initiatives are expected to pave the way for adopting solutions in the segment.
- Also, according to the United States Office of Management and Budget, for F.Y. 2021, the United States government proposed an 18.78 billion U.S. dollar budget for cybersecurity, supporting a broad-based cybersecurity strategy for securing the government and enhancing the security of critical infrastructure and essential technologies. California reported a loss of more than 573 million U.S. dollars through cybercrime, almost double the amount of second-placed New York, which said 293 million U.S. dollars of losses, says IC3.
- The North American market is attaining traction, as the content disarm and reconstruction solution gives proactive security means for stopping data breaches. SMEs and large regional organizations have become more conscious of the content disarm and reconstruction process and its advantages and started embracing them to fight cyber fraud and data thefts.
Content Disarm and Reconstruction Industry Overview
The Content Disarm and Reconstruction Market is moderately competitive and consists of several key players. Significant vendors who offer services across the globe are Check Point Software Technologies, Fortinet, Deep Secure, Sasa Software, ReSec Technologies, and OPSWAT, among others. These vendors have adopted various organic and inorganic growth strategies, such as new product launches, partnerships, collaborations, and acquisitions, to expand their offerings in the content disarm and reconstruction market.
- July 2022: OPSWAT, cybersecurity and CDR solutions for critical infrastructure protection (CIP), announced that it had attained the Amazon Web Services (AWS) Security Competency in the data protection category. This accreditation acknowledges that OPSWAT has proven that it can provide clients with cybersecurity expertise in Data Protection to assist them in achieving their cloud security objectives and has successfully met AWS's technical and quality requirements.
- March 2022: Glasswall, a provider of Content Disarm and Reconstruction (CDR) technology, recently made its market-dominating desktop CDR tool available in a freemium version called Glasswall Desktop Freedom. It provides protection that doesn't wait for detection so that users can trust every file. This technology was developed to assist safeguard organizations in the public and private sectors from the hazards of file-based attacks like malware and ransomware. Users have access to the freemium edition for 12 months after the date of their original download.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Growing Number of Ransomware, Apts, and Zero-Day Attacks
- 4.2.2 Augmented Stringent Regulations and Compliances
- 4.2.3 Rising Number of Malware and File-Based Attacks
- 4.3 Market Restraints
- 4.3.1 Budgetary Obstacles in Deploying Content Disarm and Reconstruction Solutions
- 4.4 Industry Attractiveness - Porter's Five Forces Analysis
- 4.4.1 Bargaining Power of Suppliers
- 4.4.2 Bargaining Power of Consumers
- 4.4.3 Threat of New Entrants
- 4.4.4 Threat of Substitutes
- 4.4.5 Intensity of Competitive Rivalry
- 4.5 Assessment of Impact of COVID-19 on the Industry
5 MARKET SEGMENTATION
- 5.1 By Component
- 5.1.1 Solutions
- 5.1.2 Services
- 5.2 By Deployment Mode
- 5.2.1 On-Premises
- 5.2.2 Cloud
- 5.3 By Application Area
- 5.3.1 Email
- 5.3.2 Web
- 5.3.3 File Transfer Protocol
- 5.3.4 Other Application Areas
- 5.4 By Organization Size
- 5.4.1 Small and Medium-Sized Enterprises
- 5.4.2 Large Enterprises
- 5.5 By End-user Vertical
- 5.5.1 BFSI
- 5.5.2 IT and Telecom
- 5.5.3 Government
- 5.5.4 Manufacturing
- 5.5.5 Healthcare
- 5.5.6 Other End-user Verticals
- 5.6 By Geography
- 5.6.1 North America
- 5.6.2 Europe
- 5.6.3 Asia Pacific
- 5.6.4 Latin America
- 5.6.5 Middle East and Africa
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles
- 6.1.1 Fortinet, Inc.
- 6.1.2 Check Point Software Technologies
- 6.1.3 OPSWAT, Inc.
- 6.1.4 Deep Secure Inc.
- 6.1.5 Re-Sec Technologies Ltd.
- 6.1.6 Votiro Inc.
- 6.1.7 Glasswall Solutions Limited
- 6.1.8 Sasa Software (CAS) Ltd.
- 6.1.9 Peraton Corporation
- 6.1.10 YazamTech Inc.
- 6.1.11 Jiransecurity Ltd.
- 6.1.12 Mimecast Services limited.
- 6.1.13 SoftCamp Co., Ltd.
- 6.1.14 Cybace Solutions














