
|
시장보고서
상품코드
1631576
소프트웨어 구성 분석 : 시장 점유율 분석, 산업 동향 및 통계, 성장 예측(2025-2030년)Software Composition Analysis - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
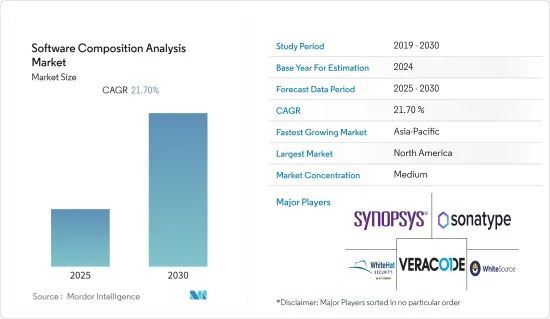
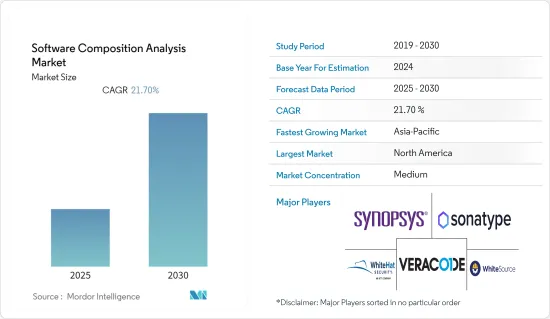
소프트웨어 구성 분석 시장은 예측 기간 동안 21.7%의 CAGR을 기록할 것으로 예상됩니다.
주요 하이라이트
- 오픈 소스 코드의 사용이 증가함에 따라 오픈 소스 취약점 및 위협의 수가 증가하고 있으며, 소프트웨어 구성 분석은 위험에 대한 성공적인 대응을 위해 받아들여지고 있습니다. 오픈 소스 소프트웨어(OSS)는 통합의 단순성, 광범위한 구성요소, 제로 비용 등의 장점과 OSS 라이선스 컴플라이언스 리스크, OSS 보안 리스크, OSS 품질 리스크 등의 단점을 가지고 있습니다. Sonatype의 제6차 소프트웨어 공급망 현황 조사에 따르면, 오픈 소스 구성요소의 취약점을 직접 공격하여 소프트웨어 공급망을 감염시키는 차세대 공격이 430% 증가했다고 합니다. 430% 증가했습니다.
- 인도 중앙은행에 따르면, 지난해 인도에서 유니버설 결제 인터페이스(UPI)의 사용 점유율은 PhonePe가 46%, Google Pay가 34%로 그 뒤를 이었습니다. 주요 핀테크 기업들은 인도에서 UPI 도입의 중요한 원동력이 되고 있습니다. 모바일 결제의 대중화로 인해 이 조사 시장은 성장할 가능성이 있습니다.
- SCA 도구는 패키징 관리자, 매니페스토 파일, 소스 코드, 바이너리 파일, 컨테이너 이미지 및 기타 객체를 검사합니다. 오픈 소스는 BOM(Bill of Materials)으로 정리되어 국가 취약점 데이터베이스를 포함한 여러 데이터베이스와 비교됩니다. 국가 취약점 데이터베이스(NVD, National Vulnerability Database)는 미국 정부가 관리하는 취약점 데이터베이스이며, 이 데이터베이스에는 알려진 일반적인 보안 결함에 대한 정보가 포함되어 있습니다. Synopsys의 내부 취약점 데이터베이스인 Black Duck KnowledgeBase는 오픈 소스 프로젝트, 라이선스 및 보안 정보를 업계에서 가장 완벽하게 정리한 데이터베이스입니다.
- 지난 몇 년 동안 기업은 전염병의 영향으로 온라인 거래를 많이 사용하게 되었고, 그 결과 사람들은 더 많은 비즈니스를 온라인으로 수행해야 했습니다. 디지털 혁신의 필요성은 기업의 시장 출시 시간에 영향을 미쳤습니다. 기업은 사슬이든, 조각이든, 버전이든, 사물을 시장에 출시하는 시간을 단축합니다. 한편, 이러한 기업들은 데이터가 유출되거나 취약점이나 악용의 여지를 남기지 않도록 세심한 주의를 기울여야 합니다. 보안상의 이유로 출시되는 모든 제품 버전은 SCA 절차를 거쳐야 합니다. 이러한 디지털화로의 전환은 팬데믹 기간 동안 지금까지 조사되었던 시장에 기회를 가져왔다고 볼 수 있습니다.
- 소프트웨어 구성 분석 도입의 가장 큰 장벽 중 하나는 숙련된 인력의 부족입니다. 교육 및 숙련된 인력이 부족하기 때문에 유지보수 작업자는 각각 프로그램 사용 방법을 고안해 내고 있습니다. 그 결과 데이터베이스가 복잡해지고 무질서해집니다. 조직은 유료 시간 절약 기능을 사용할 수 없습니다. 그 결과 유능한 인력은 소프트웨어 구성 분석 산업에서 가장 중요한 문제 중 하나가 되었습니다.
소프트웨어 구성 분석 시장 동향
클라우드 부문이 시장을 주도하는 요인 중 하나
- 클라우드 기반 소프트웨어 및 솔루션이 각 산업에서 수용되고 있기 때문에 클라우드 배포는 예측 기간 동안 가장 빠른 성장률을 보일 것으로 예상됩니다. 비용 효율성이 높기 때문에 중소기업에서 가장 많이 도입하고 있습니다. 클라우드 배포 옵션은 소프트웨어를 설치하거나 추가 하드웨어를 유지 관리할 필요 없이 여러 지점이 쉽게 협업할 수 있게 해줍니다.
- 클라우드 컴퓨팅은 상당한 시장 점유율을 차지하고 있으며, 성장세를 더욱 가속화할 것으로 예상됩니다. 클라우드 컴퓨팅이 제공하는 비용 및 운영상의 이점으로 인해 예측 기간 동안 온프레미스 구축 모델에서 클라우드로의 전환이 가속화될 것으로 예상됩니다. 예를 들어, NTT Ltd.의 조사에 따르면, 응답자의 절반 이상(52%)이 클라우드는 조직의 비즈니스 운영에 가장 큰 변화를 가져올 것이라고 답했습니다.
- 클라우드는 모든 규모의 조직이 핵심 역량에 집중하는 동시에 IT 인프라, 연결성 및 관리 책임을 이러한 서비스 개발 및 제공에 능숙한 클라우드 제공업체로 이전할 수 있게함으로써 경제적, 운영적 이점을 입증하고 있습니다. 또한, 통신 산업은 변화하고 있습니다. 빠르게 확장되는 기술, 수요 증가, 고객 기반의 다양화, 저렴한 비용으로 최신 제품 및 서비스에 대한 요구, 위성 및 케이블과 같은 여러 부문이 기존 통신에 통합되는 등 다양한 변화가 일어나고 있습니다. 이처럼 엔터프라이즈 통합 소프트웨어의 도입은 CSP(클라우드 서비스 제공업체)가 서로 다른 독립계 애플리케이션 시스템 간의 논리적 비즈니스 프로세스 통합을 통해 여러 기능에 걸친 다양한 시스템 및 애플리케이션의 관리 및 운영을 지원할 것으로 예상됩니다.
- 또한, 프리즈마 클라우드는 클라우드 네이티브 애플리케이션 보호 플랫폼에 소프트웨어 구성 분석(SCA)을 추가해 보호가 필요한 애플리케이션과 긴밀하게 연계된 코드 보안을 구현할 수 있도록 지원합니다. 이 개발은 업계 최고의 기본 IaC 보안 기능을 기반으로 하며, 애플리케이션 보안에 인프라 컨텍스트를 포함할 수 있는 최초의 컨텍스트 기반 SCA 솔루션을 제공합니다.
- 또한, 퍼블릭 클라우드에 대한 지출은 IT 예산의 중요한 항목이 되고 있습니다. Flexera가 실시한 조사에 따르면, 기업의 37%가 연간 IT 지출이 1,200만 달러 이상이라고 답했으며, 80%는 클라우드 지출이 연간 120만 달러 이상이라고 답했습니다. 라고 답했습니다.
북미가 큰 비중을 차지할 전망
- 북미는 새로운 기술을 빠르게 도입하고, 디지털 뱅킹 시스템 이용이 확대되고, 사이버 위협이 증가함에 따라 시장을 독점할 것으로 예상됩니다. 또한, 정부의 엄격한 규제, 온라인 쇼핑의 부상, 주요 시장 진입 기업의 존재 등이 산업 성장을 촉진하고 있습니다.
- WhiteSource는 오픈 소스 악성코드 보안 및 위협 탐지 도구인 Diffend를 인수했다고 밝혔습니다. 화이트소스는 이제 소프트웨어 공급망에서 리스크를 줄일 수 있는 최첨단 플랫폼을 제공할 수 있게 됐습니다.
- 또한 바이든 대통령은 벤더들에게 소프트웨어 부품표를 활용한 안전한 개발 기준을 제시하도록 요구함으로써 미국의 소프트웨어 공급망을 보호하기 위해 민관이 함께 노력하자고 촉구했습니다. SBOM을 통해 정부에 판매되는 상품의 소프트웨어 구성요소를 투명하게 공개하고, 발생할 수 있는 위험도 투명하게 공개할 수 있습니다. 이러한 관행은 시장을 주도할 것으로 예상됩니다.
- 지난해 9월, 세계 애플리케이션 보안 테스트 솔루션 제공업체인 Veracode와 소프트웨어 공급망 위험 및 보안 기술 제공업체인 Cybeats Technologies, Inc.는 협력 관계를 발표했습니다. 이번 제휴는 소비자가 최고의 사이버 보안 솔루션을 얻을 수 있도록 상호 보완적인 기술을 활용하기 위한 것입니다. 고객은 Veracode Partners를 통해 Cybeats의 소프트웨어 공급망 보안 솔루션인 SBOM Studio를 구매할 수 있으며, 양사는 공동 비즈니스를 검토할 예정입니다.
- 지난해 2월 Log4 Shell과 같은 취약점이 화제가 되면서 오픈 소스 구성요소의 위험성이 더욱 부각되면서 조직은 이러한 위험을 관리할 수 있는 애플리케이션 보안 전략을 점점 더 많이 요구하고 있습니다.
- Invicti Security는 기업이 애플리케이션의 오픈 소스 부분을 모니터링, 스캔 및 보호할 수 있도록 지원하는 소프트웨어 구성 분석 제품을 출시했습니다.
소프트웨어 구성 분석 산업 개요
소프트웨어 구성 분석 시장의 경쟁은 중간 정도이며, 여러 대기업으로 구성되어 있습니다. 시장 점유율은 현재 이들 진입 기업 중 몇 개 기업이 시장을 독점하고 있습니다. 경쟁에서 살아남고 세계 진출을 확대하기 위해 주요 기업들은 제품 혁신뿐만 아니라 M&A도 하고 있습니다.
2023년 1월, 기업 및 매니지드 서비스 프로바이더(MSP)의 데이터 관리 및 보안 강화를 지원하는 보안 솔루션 제공업체인 아포나 시큐리티(Apona Security)가 코드 조각을 포함한 라이브러리 및 코드 취약점을 탐지하는 소프트웨어 구성 분석 도구 '아포나(Apona)'를 출시합니다. 코드 조각을 포함한 라이브러리 및 코드 취약점을 탐지하는 소프트웨어 컴포지션 분석(SCA) 도구 '아포나'를 출시합니다. 이 새로운 보안 솔루션은 OSS 재사용으로 인한 보안 문제를 해결하고자 합니다. 매우 효과적인 독자적인 기술로 보안 허점을 면밀히 분석하여 기업의 컴플라이언스 및 보안을 유지하도록 돕습니다.
팔로알토 네트웍스는 지난 9월, 개발자들이 오픈 소스 소프트웨어 컴포넌트의 보안을 확보할 수 있도록 지원하는 최초의 컨텍스트 기반 소프트웨어 구성 분석(SCA) 툴을 출시했습니다. 클라우드 네이티브 보안 분야의 업계 리더로서 팔로알토 네트웍스의 입지를 더욱 공고히 할 수 있게 됐습니다. 기존 SCA 솔루션은 독립형 제품으로 많은 경보를 발생시킬 수 있지만, 문제를 식별하고 해결하는 데 도움이 되는 런타임 컨텍스트가 부족한 반면, SCA는 개발자와 보안 팀이 프리즈마 클라우드 플랫폼의 애플리케이션 라이프사이클에 영향을 미치는 알려진 취약점을 파악할 수 있도록 돕습니다. 라이프사이클에 영향을 미치는 알려진 취약점을 발견하고 우선순위를 지정할 수 있습니다.
기타 혜택
- 엑셀 형식의 시장 예측(ME) 시트
- 3개월간의 애널리스트 지원
목차
제1장 소개
- 조사 가정과 시장 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 인사이트
- 시장 개요
- 산업의 매력 - Porter's Five Forces 분석
- 구매자/소비자의 협상력
- 공급 기업의 교섭력
- 신규 참여업체의 위협
- 대체품의 위협
- 경쟁 기업 간의 경쟁 강도
제5장 시장 역학
- 시장 성장 촉진요인
- 상업용과 IoT 기반 소프트웨어 제품의 오픈 소스 코드에 대한 의존도
- 엄격한 규제와 오픈 소스 코드의 위협과 리스크 레벨 상승
- 시장 성장 억제요인
- 기업 직원의 기술적 전문 지식 부족
- Devops에 의한 원활한 서비스와 민첩성이 성장을 억제
- 산업 밸류체인 분석
- COVID-19의 산업에 대한 영향 평가
제6장 시장 세분화
- 구성요소별
- 솔루션
- 서비스별
- 전개 방식별
- 클라우드
- 온프레미스
- 산업별
- IT·통신
- BFSI
- 소매·E-Commerce
- 정부기관
- 기타 산업별(의료, 자동차)
- 지역
- 북미
- 유럽
- 아시아태평양
- 라틴아메리카
- 중동 및 아프리카
제7장 경쟁 구도
- 기업 개요
- Synopsys, Inc.
- Sonatype Inc.
- WhiteHat Security, Inc.
- Veracode Inc.
- WhiteSource Software Inc.
- Flexera Inc.
- Contrast Security, Inc.
- NexB, Inc
- Dahua Technology Co., Ltd.
- SourceClear Inc.
- Rogue Wave Software
제8장 투자 분석
제9장 시장 기회와 향후 동향
ksm 25.01.23The Software Composition Analysis Market is expected to register a CAGR of 21.7% during the forecast period.
Key Highlights
- With the increased use of open source codes, the number of open source vulnerabilities and threats is increasing, as is the acceptance of software composition analysis to successfully counter the risks. Open source software (OSS) has its advantages, such as simplicity of integration, a wide range of components, zero cost, and so on, as well as disadvantages, such as OSS license compliance risk, OSS security risk, OSS quality risk, and so on. These open-source vulnerabilities provide extraordinarily lucrative potential for hackers. According to Sonatype's sixth annual state of the software supply chain study, there has been a 430% increase in next-generation assaults that target open-source component vulnerabilities directly to infect software supply chains.
- According to the Reserve Bank of India, PhonePe had a 46% share of universal payments interface (UPI) usage in India in the last fiscal year, followed by Google Pay with a 34% share. Leading fintech companies have been important drivers of UPI adoption in India. The study market could grow as a result of the widespread use of mobile payments.
- SCA tools check package managers, manifest files, source code, binary files, container images, and other objects. The open source is assembled into a bill of materials (BOM), which is then compared against several databases, including the National Vulnerability Database. These databases contain information on known and prevalent security flaws. The National Vulnerability Database (NVD) is a vulnerability database maintained by the US government. Synopsys' internal vulnerability database, Black Duck KnowledgeBase, is the industry's most complete compilation of open-source project, licensing, and security information.
- In the last few years, businesses have used online transactions more because of the pandemic.COVID-19 and the resulting constraints compelled people to conduct more business online. The necessity of digital transformation influenced firms' time to market. Businesses reduce the time it takes to bring things to market, whether in chains, pieces, or versions. On the other hand, these firms must exercise extreme caution to avoid leaking data or allowing room for vulnerabilities or exploits. For security reasons, every version of a product that is launched must go through the SCA procedure. Such a transition toward digitalization would have created opportunities for the previously researched market during the pandemic.
- One of the most significant barriers to the adoption of software composition analysis is the scarcity of skilled workers. Due to a lack of training and skilled staff, each maintenance crew member devises their own methods for using the program. As a result, the database grows more complicated and disorganized. The organizations are unable to access the paid-for time-saving features. As a result, competent labor is one of the most significant issues in the software composition analysis industry.
Software Composition Analysis Market Trends
Cloud Segment is one of the Factor Driving the Market
- Due to the growing acceptance of cloud-based software and solutions across industries, cloud deployment is seeing the fastest growth rate during the anticipated period. Due to the cost-efficiency of the deployment, small and medium-sized businesses (SMEs) are where adoption is most prevalent. The cloud deployment option makes it easy for multiple sites to work together without having to install software or keep up with extra hardware.
- Cloud computing is expected to command a sizable market share and even accelerate growth. The cost and operational benefits offered by the deployment mode are expected to shift the trend away from the on-premise deployment model over the forecasted period. For instance, according to the study by NTT Ltd., over half of the respondents (52%) mentioned that the cloud would have the most transformational impact on their organization's business operations.
- The cloud has proven itself economically and operationally by allowing organizations of all sizes to focus on their core competencies while transferring IT infrastructure, connectivity, and management responsibility to cloud providers who excel at developing and delivering these services. Further, the telecommunications industry is changing. This is due to rapidly expanding technology, increased demand, client base diversification, the need for current products and services at low rates, and the integration of several sectors, such as satellite and cable, with existing telecommunications. Thus, the implementation of enterprise-integrated software is anticipated to assist CSPs (cloud service providers) in managing and administering various systems and applications across multiple functions by enabling them to achieve logical business process integration across different independent application systems.
- Further, Prisma Cloud has added Software Composition Analysis (SCA) to its cloud-native application protection platform to assist teams in obtaining code security that is as tightly linked as the apps they need to protect. This development builds on our industry-leading basic IaC security capabilities and makes possible the first context-aware SCA solution that can include the infrastructure context in application security.
- Furthermore, public cloud spending is a significant line item in IT budgets. The increasing use of the public cloud is driving up cloud spending for organizations of all sizes. According to a survey conducted by Flexera, 37 percent of enterprises said their annual IT spend exceeded USD 12 million, and 80% reported that their cloud spending exceeds USD 1.2 million per year.
North America is Expected to Hold Major Share
- North America is expected to dominate the market due to its early embrace of new technologies, growing use of digital banking systems, and rising cyber threats. In addition, the strict rules set by the government, the rise of online shopping, and the presence of major market players in the area are all helping the industry grow.
- WhiteSource disclosed that it had acquired Diffend, an open-source malware security and threat detection tool. Differnd's commercial offerings will be free to use following the acquisition under the new brand WhiteSource Diffend.WhiteSource can now offer cutting-edge platforms to cut down on risk in the software supply chain.
- Additionally, President Biden urged the public and private sectors to safeguard the US software supply chain by requesting vendors to show secure development standards utilizing a software bill of materials. The software components of goods sold to the government are transparent thanks to an SBOM, as are any possible dangers. Such practices are expected to drive the market.
- In September last year, Veracode, a global provider of application security testing solutions, and Cybeats Technologies, Inc., a software supply chain risk and security technology provider, announced a collaborative relationship. The alliance will take advantage of complementary skills to guarantee that consumers obtain the best cybersecurity solutions. Customers can buy SBOM Studio, a software supply chain security solution from Cybeats, through Veracode Partners, and the two companies will look into doing business together.
- In February last year, organizations increasingly required application security strategies that managed this risk as the hazards posed by open-source components became more prominent thanks to vulnerabilities making headlines like Log4 Shell. Invicti Security has released its software composition analysis product to help businesses monitor, scan, and secure the open-source parts of their applications.
Software Composition Analysis Industry Overview
The software composition analysis market is moderately competitive and consists of several major players. In terms of market share, a few of these players currently dominate the market. To stay ahead of the competition and expand their global reach, influential companies use mergers and acquisitions as well as product innovation.
In January 2023, Apona Security, a security solutions provider that helps enterprises and managed service providers (MSPs) manage data and improve security across their patented product suites, will launch Apona, a software composition analysis (SCA) tool that detects vulnerabilities in libraries and code, including code fragments. This new security solution tries to fix the security problems caused by OSS reuse. It does this by closely analyzing security holes with highly effective proprietary technologies and helping businesses stay compliant and safe.
In September 2022, Palo Alto Networks released the first context-aware software composition analysis (SCA) tool to help developers secure open-source software components. Palo Alto Networks' position as the industry leader in cloud-native security is reinforced by introducing SCA into Prisma Cloud. Traditional SCA solutions are stand-alone products that can create many alarms but lack the runtime context to aid in problem identification and resolution. SCA would let developers and security teams find and prioritize known vulnerabilities that affect the application lifecycle of the Prisma Cloud platform.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Attractiveness- Porter's Five Forces Analysis
- 4.2.1 Bargaining Power of Buyers/Consumers
- 4.2.2 Bargaining Power of Suppliers
- 4.2.3 Threat of New Entrants
- 4.2.4 Threat of Substitute Products
- 4.2.5 Intensity of Competitive Rivalry
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Commercial and IoT-based Software Products' Dependence on Open-Source Codes
- 5.1.2 Strict Laws & Regulations and Growing Levels of Threats and Risks in Open-Source Codes
- 5.2 Market Restraints
- 5.2.1 Shortage of Technical Expertise Amongst the Enterprise Workforce
- 5.2.2 Smooth Services and Agility Due to Devops Repress the Growth
- 5.3 Industry Value Chain Analysis
- 5.4 Assessment of Impact of COVID-19 on the Industry
6 MARKET SEGMENTATION
- 6.1 By Component
- 6.1.1 Solution
- 6.1.2 Services
- 6.2 By Deployment Mode
- 6.2.1 Cloud
- 6.2.2 On-premises
- 6.3 By Industry Vertical
- 6.3.1 IT & Telecom
- 6.3.2 BFSI
- 6.3.3 Retail & E-Commerce
- 6.3.4 Government
- 6.3.5 Other Industry Verticals (Healthcare, Automotive)
- 6.4 Geography
- 6.4.1 North America
- 6.4.2 Europe
- 6.4.3 Asia-Pacific
- 6.4.4 Latin America
- 6.4.5 Middle East and Africa
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 Synopsys, Inc.
- 7.1.2 Sonatype Inc.
- 7.1.3 WhiteHat Security, Inc.
- 7.1.4 Veracode Inc.
- 7.1.5 WhiteSource Software Inc.
- 7.1.6 Flexera Inc.
- 7.1.7 Contrast Security, Inc.
- 7.1.8 NexB, Inc
- 7.1.9 Dahua Technology Co., Ltd.
- 7.1.10 SourceClear Inc.
- 7.1.11 Rogue Wave Software














