
|
시장보고서
상품코드
1636602
정보 권한 관리(IRM) 시장 : 점유율 분석, 산업 동향 및 통계, 성장 예측(2025-2030년)Information Rights Management - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
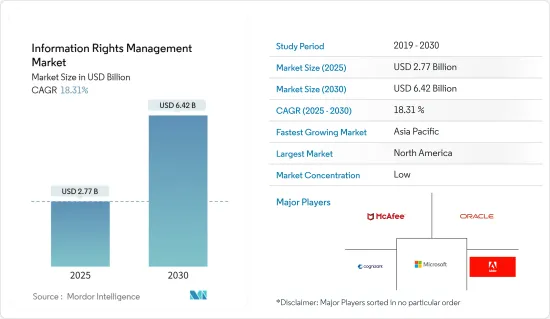
정보 권한 관리 시장 규모는 2025년에 27억 7,000만 달러로 추정되고, 예측기간 중(2025-2030년) CAGR은 18.31%로 전망되며, 2030년에는 64억 2,000만 달러에 달할 것으로 예측되고 있습니다.

세계 기업들은 비즈니스 프로세스의 디지털화를 통해 비즈니스 정보를 전달하기 위해 온라인 플랫폼을 활용하고 있으며 문서 보안 목적으로 암호화된 액세스 권한이 필요하기 때문에 IRM 소프트웨어 시장 공급업체에게 비즈니스 기회를 제공합니다.
주요 하이라이트
- IRM은 액세스 제어를 수행하기 위해 파일을 암호화하는 경우가 많으며 문서가 암호화된 후 특정 작업을 허용 및 거부하기 위해 추가 IRM 규칙을 사용할 수 있습니다. 이로 인해 사용자는 문서 내의 자료를 볼 수 있으며 복사하거나 붙여 넣을 수 없게 됩니다. 또한 문서의 인쇄, 편집 및 스크린샷 촬영은 IRM 규칙에 의해 금지될 수 있습니다. 이는 기업이 고급 증권으로 정보 파일을 공유할 수 있도록 하기 위해 IRM 솔루션 시장 도입의 원동력이 되고 있습니다.
- IRM은 디지털 저작권 관리의 서브세트이며, 기업이 DRM 도구를 채택하는 이유는 디지털 미디어 자산이 암호화 프로그램의 사용에 의해 보호되고 특정 개인, 시간 또는 장치에 대한 액세스가 제한되며 컨텐츠 설치 또는 개봉 횟수에 제한이 부과되기 때문입니다. DRM 소재는 일반적으로 기업 설계자가 기밀 데이터를 보호하기 위해 제품 설계서 및 M&A(합병 및 인수) 프로세스에서 사용됩니다. 효율적인 디지털 저작권 관리 소프트웨어를 통해 기업은 규제 의무를 준수하면서 새로운 캠페인과 제품 개념을 신속하게 시작할 수 있습니다.
- 또한 경쟁사에 의한 기업 비밀이나 지적 재산 취득을 저지할 수도 있습니다. 제약회사를 생각해봅시다. 예를 들어, 이러한 IRM 도구는 신약의 특허를 다루고 있지만, IRM 컨트롤이 없기 때문에 경쟁자에게 유용한 정보를 훔칠 수 있습니다. 또한 내부 조사 중 은행에 관한 개인 정보가 공개되어 시장에서 은행의 지위가 손상될 수 있습니다. 이와 같이 다양한 최종사용자 산업에서 IRM이 활용되고 있는 것이 시장 성장 수요를 창출하고 있습니다.
- 표준 관행이 없는 것은 조직이 정보 적정 관리 도구를 채택할 때 직면하는 주요 문제 중 하나입니다. 전략의 통일성 부족, 문서의 디지털화, 절차의 자동화, 증가하는 양의 관리, 정보 접근의 보호, 정보 사일로의 감소, 레거시 시스템과의 통합, 저품질 데이터의 제거 등이 정보 관리의 일반적인 어려움입니다.
- COVID-19의 대유행으로 세계 많은 사람들이 온라인으로 전환하여 장기적인 디지털 변환이 가속화되었습니다. 몇몇 사람들이 재택근무를 시작했고, 가정에서 인터넷에 접속할 수 있는 아이들이 온라인으로 수업을 받기 시작했고, 수많은 기업들이 디지털 비즈니스 모델을 적응시켜 사업을 계속해 일정 수입원을 확보했습니다. 한편, 연구자들은 인공지능(AI)을 사용하여 바이러스를 해명하고 백신 탐색을 가속화했습니다. 팬데믹의 확장을 '감시 및 추적'하기 위한 모바일 애플리케이션이 만들어졌으며, 온라인 컨텐츠의 양이 증가함에 따라 다양한 최종 사용자로부터 IRM 소프트웨어에 대한 수요가 증가하고 있습니다.
정보 권한 관리 시장 동향
BFSI 업계가 큰 점유율을 차지할 전망
- 은행/금융서비스/보험(BFSI) 업계는 데이터 유출에 가장 취약하며 정보의 기밀성을 위해 BFSI 기업은 보호되어야 합니다. 은행은 고객과 관련된 다양한 재무 및 개인 데이터를 보유하고 있으며, 액세스 권한이 있는 사람이라면 누구나 모든 정보에 액세스할 수 있습니다. 금융기술 개발은 전신송금, 신용카드 및 직불카드, 온라인뱅킹, 모바일 결제 등 여러 획기적인 진보를 만들어 왔습니다. 은행은 이러한 변화에 맞추어 시스템을 변경하고 신기술을 도입하면서도 지속적인 보안을 확보하기 위해 업무를 변혁해야 했습니다.
- 따라서 은행과 금융 기관이 보안 위험을 완화하고 외부 관계자와 협력할 수 있기 때문에 IRM 수요가 높아질 것으로 예상됩니다. Seclore의 엔터프라이즈 디지털 저작권 관리(EDRM)와 같은 기업은 기업 내외에서 공유되는 정보의 종단 간 보호를 보장합니다. 모바일 뱅킹 고객 수가 증가하고 있습니다. 서비스 제공업체는 온라인 미디어를 이용하여 무단 액세스로부터 보호해야 하는 고객별 민감한 데이터가 필요한 서비스를 사용자에게 제공할 수 있도록 하여 세계 시장을 견인하고 있습니다.
- 대금융자를 원하는 기업은 은행이 신용 위험을 분석하기 위해 재무정보, 사업전략, 수익 예측 등의 개인정보를 은행에 보내야 합니다. 신용 분석가는 데이터를 검토하고 최적의 대출 금리 및 기타 대출 조건을 계산합니다. 이 데이터에는 기업에 대한 매우 민감한 정보가 포함되어 있습니다. 따라서 은행 내에서 이를 관리하는 여러 팀 중 하나가 보안 침해 위협에 노출되어 조직 내 IRM 도구가 필요합니다.
- 게다가 아웃소싱, 클라우드 컴퓨팅, BYOD(Bring-your-own-device), 파일 공유, 외부와의 협업이 비즈니스를 수행하는데 있어서 일반적으로 되고 있는 현재, 기밀 정보는 정기적으로 제3자에게 제공되어 보호되지 않는 경우가 많습니다. 데이터 유출의 위험은 사내 외부와의 관계 수준이 높을수록 높아집니다.
- 디지털 전환을 통해 BFSI 산업의 일부 시장 기업은 데이터를 위한 높은 보안 플랫폼을 제공하기 위해 신기술을 혁신하고 IRM 시장에 기회를 창출하고 있습니다. 예를 들어, 2023년 1월 HDFC 은행은 데이터 환경 근대화, 애플리케이션 포트폴리오 혁신, Microsoft 클라우드를 이용한 보안 확보를 통해 비즈니스 가치를 극대화하는 것을 목표로 디지털 변환의 다음 단계에서 Microsoft와 협력했습니다.
북미가 시장을 독점할 전망
- 북미, 특히 미국의 디지털 미디어 컨텐츠 소비와 기업의 디지털화는 현지 기술 발전의 급속한 도입으로 엄청나게 증가하고 있습니다.
- 인터넷 가속화와 디지털 미디어 액세스를 지원하는 장치 증가로 소비자는 언제 어디서나 미디어 컨텐츠에 액세스할 수 있는 자유도가 높아지고 있습니다. 이러한 동향은 IRM 솔루션 도입에서 이 지역의 우위성을 높일 것으로 예상됩니다.
- 이 나라의 모바일 인터넷 이용은 눈부시게 늘고 있으며 모바일 무선 연결의 수가 가장 많습니다. 태블릿, 스마트폰, 클라이언트의 인터넷 의존도가 증가함에 따라 디지털 저작권 관리 솔루션의 사용이 필수적입니다. 기업이 무선 기술에 대한 투자가 증가함에 따라 미국과 캐나다에서 신뢰할 수 있는 IRM 솔루션을 제공하기 위해 활동하는 IRM 시장 기업이 지원하는 IRM 솔루션에 대한 요구가 커지고 있습니다.
- 이 지역의 데이터 해킹 동향에 대응하여 보다 엄격한 규제 프레임워크이 등장해 기업은 고객 데이터의 취급방법에 대해 보다 책임을 지고 있습니다. 헬스케어 업계에서는 HIPAA, 금융 업계에서는 PCI DSS 등 프라이버시 및 데이터 보호에 관한 법률이 몇 가지 도입되고 있습니다. IRM은 파일에 대한 액세스 및 배포와 같은 작업을 추적할 수 있으므로 철저한 감사 추적을 자동으로 제공할 수 있으며 법규에 대한 규정 준수를 제공할 수 있습니다.
- 연구개발 지식, 기업 비밀, 지적 재산 데이터는 직원과 같은 내부 위협에 취약합니다. 예를 들어, 부서 간의 데이터는 기밀이며 기업 재무와 관련된 데이터 전송은 전자 메일에 암호 보호 파일을 포함하여 IRM 도구를 통해 조직의 특정 구성원으로 제한할 수 있습니다.
정보 권한 관리 업계 개요
여러 IRM 솔루션 제공업체가 있기 때문에 Information Rights Management 시장 경쟁 구도이 단편화되고 있습니다. 시장 기업은 시장에서의 존재감을 높이기 위해 다양한 최종 사용자 기업과 파트너십을 맺고 협력하고 있습니다. 각 회사는 또한 시장에서 혁신적인 솔루션과 서비스를 제공하기 위해 노력하고 있습니다.
Oracle은 2023년 9월 네트워크 및 데이터 보안에 대한 새로운 개방형 표준에 대한 참여 이니셔티브를 발표했습니다.
2022년 9월 Microsoft는 Microsoft 365 애플리케이션 및 서비스에 대한 정보 라이츠 관리(IRM) 요소를 개발했습니다. 사용자 회사는 중요한 전자 메일 및 문서를 보호하기 위해 Azure RMS의 사용을 시작할 수 있습니다. 이 정보 보안 시스템은 Microsoft Exchange 및 SharePoint와 같은 서버와 Excel, Microsoft Word와 같은 클라이언트 프로그램과도 연결하여 모든 파일 형식을 보호할 수 있습니다.
기타 혜택 :
- 엑셀 형식 시장 예측(ME) 시트
- 3개월의 애널리스트 서포트
목차
제1장 서론
- 조사의 전제조건 및 시장 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 역학
- 시장 개요
- 시장 성장 촉진요인
- BYOD 동향과 기업 모빌리티의 채용 확대, 엄격한 규제와 컴플라이언스
- 다양한 산업별 디지털 저작권 관리 솔루션 채용
- 비즈니스 프로세스의 급속한 디지털화와 인터넷 이용 증가
- 시장 성장 억제요인
- 디지털 컨텐츠의 보안에 관한 표준화의 부족
- 업계의 매력-Porter's Five Forces 분석
- 공급기업의 협상력
- 구매자 및 소비자의 협상력
- 신규 참가업체의 위협
- 대체품의 위협
- 경쟁 기업간 경쟁 관계의 강도
- 시장에 대한 COVID-19의 영향 평가
제5장 시장 세분화
- 조직 규모별
- 중소기업
- 대기업
- 전개 형태별
- 온클라우드
- 온프레미스
- 최종 사용자 업계별
- BFSI
- 헬스케어
- 미디어 및 엔터테인먼트
- 교육 및 조사
- 정부 및 공공기관
- IT 및 통신
- 기타 최종 사용자 산업(법률 및 행정기관, 제조업)
- 지역별
- 북미
- 유럽
- 아시아
- 호주 및 뉴질랜드
- 라틴아메리카
- 중동 및 아프리카
제6장 경쟁 구도
- 기업 프로파일
- Microsoft Corporation
- McAfee, LLC
- Cognizant Technology Solutions Corporation(assetServ)
- Adobe Inc.
- Oracle Corporation
- Bynder BV
- Nextlabs, Inc.
- Intralinks, Inc.
- Citrix Systems, Inc.
- Seclore Technology Private Limited
- Locklizard Limited
- Vaultize Technologies
제7장 투자 분석
제8장 시장 기회 및 향후 동향
AJY 25.02.12The Information Rights Management Market size is estimated at USD 2.77 billion in 2025, and is expected to reach USD 6.42 billion by 2030, at a CAGR of 18.31% during the forecast period (2025-2030).
Enterprises worldwide are increasingly using online platforms to communicate their business information due to the digitalization of business processes, which need encrypted access rights for security purposes of the document, creating an opportunity for the IRM software market vendors.
Key Highlights
- IRM frequently encrypts files to impose access controls, and extra IRM rules can be used to allow/deny specific actions after a document has been encrypted. This can result in a user only being able to view material from a document, not copy or paste it. In other circumstances, users may be prohibited by the IRM rule from printing, editing, or taking screenshots of the document. This drives the market adoption of IRM solutions because it enables a company to share information files with advanced securities.
- IRM is a subset of Digital Right Management, and companies are adopting DRM tools because, through this, digital media assets are protected by the use of an encryption program, which limits access to particular individuals, times, or devices and imposes a limit on the number of times the content can be installed or opened. DRM material is typically used by corporations to protect confidential data, especially during product design papers and M&A (merger and acquisition) processes. With efficient digital rights management software, a firm may quickly launch new campaigns and product concepts while keeping in compliance with regulatory obligations.
- It can stop competitors from obtaining trade secrets or intellectual property. Consider a pharmaceutical organization. For instance, these IRM tools may be working on a patent for a new medicine, but the absence of IRM controls may allow a rival to steal useful informations. Additionally, private information about a bank under investigation internally might be made public, harming the bank's standing in the market. This road application of IRM across various end-user industries creates a demand for market growth.
- The absence of standard practices is one of the main issues organizations face with adopting information-proper management tools. Lack of uniformity in strategy, digitization documents, automating procedures, managing the growing volume, safeguarding information access, reducing information silos, integrating with legacy systems, and removing low-quality data are common information management difficulties.
- The COVID-19 pandemic caused many worldwide to move online, accelerating a long-term digital transformation. Several people began working from home, children with at-home Internet connections started attending classes online, and numerous businesses adapted digital business models to continue operating and keep certain revenue streams. In the meantime, researchers used artificial intelligence (AI) to underastand the virus and hasten the search for a vaccine. Mobile applications were created to help "monitor and trace" the growth of the pandemic, which has increased the demand for IRM software across various end users due to an increase in the volume of online content.
Information Rights Management Market Trends
BFSI Industry is Expected to Hold Significant Share
- The banking, financial services, and insurance (BFSI) industry is most vulnerable to data loss, and due to the sensitive nature of the information, BFSI firms must be protected. Banks have various financial and personal data about their clients; anyone with access rights can access all that information. Financial technology development has produced several breakthroughs and advancements, including wire transfers, credit/debit cards, online banking, and mobile payments. Banks have had to modify their systems to suit these changes and transform their operations to ensure sustained security while introducing new technologies.
- Hence, the demand for IRM is expected to increase as it will enable banking and financial institutions to mitigate security risks and collaborate with external parties. Players such as Seclore's enterprise digital rights management (EDRM) ensure end-to-end protection of information shared within and outside the enterprise. The number of mobile banking customers is increasing. Service providers use the online medium to enable users to have services requiring confidential data specific to the customers, which need to be secured from unauthorized access, driving the market worldwide.
- Businesses seeking large loans must send the bank their private information, including financial information, business strategies, and revenue projections, for the bank to analyze credit risk. Credit analysts examine the data to calculate the optimal lending rate of interest and other loan terms. It contains extremely sensitive information about a company. Thus, any of the multiple teams managing it within the bank have the threat of a security breach, which requires IRM tools in the organization.
- Additionally, sensitive information is regularly provided to third parties, frequently without protection, in an age where outsourcing, cloud computing, bring-your-own-device (BYOD), file-sharing, and collaboration with external parties are common in conducting business. The risk of data leaking increases with the level of external engagement within the company, which creates a demand for IRM tools in the BFSIs because it would be helpful
- Due to digital transformation, several BFSI industry market players are innovating new technology to provide a high-security platform for Data, which is creating an opportunity for the IRM market. For instance, in January 2023, HDFC Bank collaborated with Microsoft on the next stage of its digital transformation journey with the goal of maximizing business value through modernizing the data landscape, transforming the application portfolio, and securing the company with Microsoft Cloud.
North America is Expected to Dominate the Market
- The consumption of digital media content and the digitization of enterprises in North America, especially in the United States, is increasing tremendously, owing to the rapid adoption of technological advancements in the region.
- The increasing speed of internet speeds, coupled with the increase in the number of devices supporting access to digital media, has increased the freedom of consumers to access media content anywhere and anytime. Such trends are expected to boost the region's dominance in adopting IRM solutions.
- Mobile internet usage in the country has grown tremendously, with the greatest number of mobile wireless connections. The use of digital rights management solutions is now essential due to the increase of tablets, smartphones, and client internet dependence. Due to the increase in wireless technology investments by businesses, there would be a greater need for IRM solutions supported by IRM market players working to present trustworthy IRM solutions in the US and Canada.
- A more stringent regulatory framework has emerged in response to the region's current trend of data hacks, and businesses are more accountable for how client data is handled. Several privacy and data protection legislation have been introduced, including HIPAA in the healthcare business and PCI DSS in the finance industry. Because IRM can track actions such as file access and distribution, it can automatically provide a thorough audit trail, enabling it to offer regulatory compliance.
- Research and development knowledge, trade secrets, and intellectual property data are vulnerable to insider threats, which include employees and other internal staff. For instance, inter-department data are confidential, and data transfer related to the financials of the company can be restricted to certain members of the organization through the IRM tool by including password protection files in e-mails, which is driving the market in the United States because many large corporates have their head offices in the region.
Information Rights Management Industry Overview
The competitive landscape of the information rights management market is fragmented owing to the presence of several IRM solution providers. The market players are extending partnerships and collaborating with several companies in different end-users to boost their market presence. The companies are also making efforts to provide innovative solutions and offerings in the market.
In September 2023 - Oracle announced its participation initiative to a new open standard on network and data security, which will help organizations to better secure their data in distributed IT environments by providing them with collective enforcement of shared security policies, enabling networks to reinforce the security architecture organizations have been using without changing existing applications and networks.
In September 2022, Microsoft developed the information rights management (IRM) elements of Microsoft 365 applications and services, which could be used after the rights management service (RMS) has been activated. The user company may begin utilizing Azure RMS to protect crucial emails and documents. This information security system could protect all file formats, which also connects with servers like Microsoft Exchange and SharePoint and client programs like Excel, Microsoft Word, and others.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Increasing Adoption of BYOD Trends and Enterprise Mobility, and Stringent Regulations and Compliance
- 4.2.2 Adoption of Digital Rights Management Solutions Across Various End-user Verticals
- 4.2.3 Rapid Digitization of Business Process Coupled With Increase in Internet Usage
- 4.3 Market Restraints
- 4.3.1 Lack of Standardization for Security of Digital Content
- 4.4 Industry Attractiveness - Porter's Five Forces Analysis
- 4.4.1 Bargaining Power of Suppliers
- 4.4.2 Bargaining Power of Buyers/Consumers
- 4.4.3 Threat of New Entrants
- 4.4.4 Threat of Substitute Products
- 4.4.5 Intensity of Competitive Rivalry
- 4.5 Assessment of Impact of Covid-19 on the Market
5 MARKET SEGMENTATION
- 5.1 By Size of the Organization
- 5.1.1 Small and Medium Enterprises
- 5.1.2 Large Enterprises
- 5.2 By Deployment Mode
- 5.2.1 On-Cloud
- 5.2.2 On-Premise
- 5.3 By End-user Industry
- 5.3.1 BFSI
- 5.3.2 Healthcare
- 5.3.3 Media and Entertainment
- 5.3.4 Education and Research
- 5.3.5 Government and Public Institutions
- 5.3.6 IT & Telecom
- 5.3.7 Other End-user Industries (Law and Order Agencies, Manufacturing)
- 5.4 By Geography
- 5.4.1 North America
- 5.4.2 Europe
- 5.4.3 Asia
- 5.4.4 Australia and New Zealand
- 5.4.5 Latin America
- 5.4.6 Middle East and Africa
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles
- 6.1.1 Microsoft Corporation
- 6.1.2 McAfee, LLC
- 6.1.3 Cognizant Technology Solutions Corporation (assetServ)
- 6.1.4 Adobe Inc.
- 6.1.5 Oracle Corporation
- 6.1.6 Bynder B.V.
- 6.1.7 Nextlabs, Inc.
- 6.1.8 Intralinks, Inc.
- 6.1.9 Citrix Systems, Inc.
- 6.1.10 Seclore Technology Private Limited
- 6.1.11 Locklizard Limited
- 6.1.12 Vaultize Technologies













