
|
시장보고서
상품코드
1639361
북미의 IoT 보안 - 시장 점유율 분석, 산업 동향과 통계, 성장 예측(2025-2030년)North America IoT Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
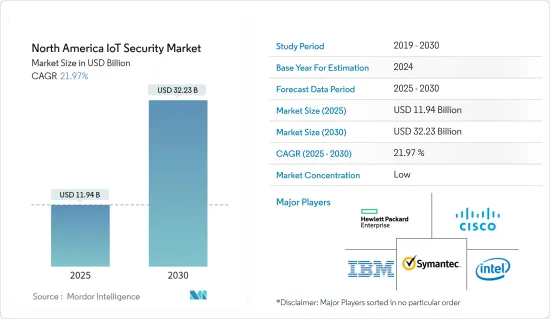
북미 IoT 보안 시장 규모는 2025년 119억 4,000만 달러로 추정되며, 예측 기간 중(2025-2030년) CAGR은 21.97%로, 2030년에는 322억 3,000만 달러에 이를 것으로 예측됩니다.

주요 하이라이트
- 새로운 비즈니스 모델과 용도는 장치 비용 절감과 함께 IoT 채택을 촉진하여 그 결과 연결된 기계, 웨어러블, 자동차, 미터, 소비자 전자 제품 등의 연결 장치 수가 증가하고 있습니다.
- 소비자를 위한 IoT 장치에 대한 공격은 확산되고 있으며, 제조 산업과 유사한 산업에서 혼란의 가능성이 위협을 더욱 심각하게 만들고 있습니다. 미국과 캐나다의 다양한 최종 사용자 산업은 지난 몇 년 동안 상당한 보안 공격에 직면해 있습니다. IoT 보안은 기업, 소비자, 규제 당국에 중요한 관심 분야가 되고 있습니다. 이러한 주목을 받고 세계에서 IoT 기반 솔루션을 제공하는 기업들은 이러한 솔루션의 보안 측면에 많은 투자를 하고 있습니다.
- 예를 들어, 2022년 10월, 클라우드 애플리케이션 모니터링 보안 플랫폼을 제공하는 Datadog, Inc.는 Cloud Security Management의 일반 제공을 선언했습니다. 이 제품은 클라우드 보안 포스처 관리(CSPM), 클라우드 워크로드 보안(CWS), 경고, 인시던트 관리 및 보고 기능을 단일 플랫폼에 통합하여 DevOps 팀과 보안 팀이 구성 오류를 식별합니다. 그런 다음 위협을 감지하고 클라우드 네이티브 용도을 보호할 수 있습니다.
- 또한 연결 장치에 대한 의존도가 높아지면 연결 장치의 안전을 유지할 필요가 있습니다. 이 커다란 성장은 산업 생태계의 발전에 산업이 주력하게 되었고 3GPP 셀룰러 IoT 기술의 표준화에 의해 초래될 것으로 예상됩니다.
- 인터넷에 연결된 장치가 증가함에 따라 사이버 세계에서는 새로운 위협과 공격의 발생과 출현이 크게 증가할 것으로 예상됩니다. IoT 장치는 데이터 도난, 스푸핑, 피싱 공격, DDoS 공격(서비스 거부 공격) 등 다양한 네트워크 공격에 특히 취약합니다. 이들은 랜섬웨어 공격 및 기타 심각한 데이터 유출과 같은 다양한 사이버 보안 관련 위협으로 이어질 수 있으며, 기업은 복구에 상당한 비용과 노력을 소비하게 됩니다.
- 그러나 장치 간의 복잡화는 유비쿼터스 법의 부족과 함께 예측 기간 동안 전체 시장 성장을 제한할 수 있는 주요 우려사항일 수 있습니다.
- COVID-19가 시작된 이래 IoT 공격이 증가하고 있기 때문에 세계 각국은 몇 가지 예방책을 실시했습니다. 지역사회가 자택 대기를 요구하고 학교가 폐쇄되는 가운데, 여러 조직이 직원의 자택근무를 인정하는 방법을 발견했습니다. 그 결과, 비디오 커뮤니케이션 플랫폼의 도입이 증가했습니다. 게다가 COVID-19 이후의 기간에는 특히 주요 시장 진출 기업들이 비용 효율적인 클라우드 기반과 하이브리드의 다양한 솔루션을 도입함으로써 시장은 큰 성장 기회를 목격할 것으로 예상됩니다.
북미의 IoT 보안 시장 동향
데이터 유출 건수 증가가 시장을 견인할 것으로 예측
- 인터넷에 접속되는 디바이스 증가에 따라 사이버 세계에서는 새로운 위협이나 공격의 발생·출현이 증가할 것으로 예상되고 있습니다. 이것은 지난 몇 년 동안 북미의 다양한 최종 사용자 산업에서 데이터 침해가 증가함에 따라 분명합니다. 이러한 공격은 비즈니스 시스템과 개인을 직접 표적으로 삼아 엄청난 금전적/개인적 손실을 초래할 수 있습니다. 그 때문에 데이터 침해의 영향을 받기 쉬운 소비자용 디바이스에 대한 IoT 보안의 필요성이 높아지고 있다
- 또한 의료, 제조, 은행/금융서비스/보험(BFSI), 자동차 등 다양한 최종 사용자 산업에서 데이터 유출이 증가함에 따라 사이버 공격으로부터 연결 장치를 보호하는 IoT 보안 솔루션의 필요성이 커지고 있습니다. 예를 들어 Identity Theft Resource Center의 ITRC 2022 Annual Data Breach Report에 따르면 미국에서 2022년 데이터 유출 건수는 1802건이었습니다. 미국의 데이터 유출 건수는 2005년 157건에서 2022년 1802건으로 크게 증가하고 있습니다.
- 또한 클라우드 서비스는 IoT 수요로 인한 높은 채용률을 경험하고 있습니다. 이와 같이 다양한 업종에서 클라우드 시스템의 이용이 증가하고 있기 때문에 데이터 유출에 대한 시스템 취약성이 높아지고 있습니다. 많은 공급자가 여러 솔루션을 제공하므로 통합된 보안 플랫폼에 대한 요구가 커지고 있습니다. IoT 보안은 장치와 통신, 데이터 스토리지, 수명 주기 솔루션에 배포할 수 있습니다.
- 또한 사이버 공격으로부터 기업을 보호하기 위한 정부의 이니셔티브이 증가하고 있기 때문에 시장은 더욱 성장할 것으로 예상됩니다. 예를 들어, 바이든 정부는 2023년 7월 인터넷 연결 장비와 관련된 수많은 보안 위험으로부터 미국인을 보호하기 위해 사물 인터넷(IoT) 사이버 보안 표시 프로그램을 시작했습니다. 이 프로그램 '미국 사이버 트러스트 마크'는 미국인이 사이버 공격에 대한 강력한 사이버 보안 보호를 포함한 인터넷 연결 장비를 확실하게 구입할 수 있도록 하기 위한 것입니다.
미국이 시장을 독점할 전망
- 미국과 미국의 IoT 보안 시장 성장의 주요 중요 요인은 첨단 기술 채택률 증가, 사이버 공격 증가, 일본의 연결 장치 수 증가입니다. 이 나라는 IoT 배포에서 지배적인 지역 중 하나입니다. 기타 요인으로는 이 지역의 디지털화와 IoT 보안 지출 증가가 있습니다.
- 또한 이 지역에는 Symantec Corporation, IBM Corporation, FireEye Inc., Palo Alto Networks Inc.와 같은 중요한 IoT 보안 공급업체가 있습니다. 벤더 각사는 제품 혁신을 강화함으로써 제품 포트폴리오와 시장에서의 존재감을 높이고 있습니다. 예를 들어, 2022년 3월, 네트워크 방화벽 공급업체인 Palo Alto Networks는 Amazon Web Services와 제휴하여 새로운 Palo Alto Networks Cloud NGFW for AWS를 발표했다고 밝혔습니다.
- 또한 2022년 5월에는 전자 용도의 모든 부문에서 고객에게 서비스를 제공하는 세계 반도체 공급업체인 STMicroelectronics가 ST 인증 파트너인 Microsoft와의 협업에 대해 자세히 설명했습니다. 그 목적은 새로운 Internet-of-Things 용도의 보안을 강화하는 것입니다. ST는 초저전력 STM32U5 마이크로컨트롤러와 Microsoft Azure RTOS &IoT Middleware를 결합하고, 특히 임베디드 시스템을 위한 Arm Trusted Firmware-M(TF-M) 보안 서비스의 인증 보안 구현을 수행합니다.
- 또한 미국에서는 사이버 위협이 증가하고 있습니다. Identity Theft Resource Center에 따르면, 이 나라의 평균 침해 건수는 지난 몇 년간 약간 증가했습니다. 2022년 10월, 바이든-해리스 정권은 미국의 사이버 방어 개선에 중점을 두고 국가 사이버 보안을 강화하고 보호하기 위한 적극적인 조치를 취하기 위한 종합적인 접근 방식을 구축했습니다.
- GSMA Intelligence에 따르면 2025년 말까지 북미의 산업용 및 소비자용 사물의 인터넷 접속 총수는 약 54억으로 증가할 것으로 예측되고 있습니다. 2019년 북미의 IoT 연결 총수는 28억 접속에 달했습니다. 이 지역의 산업용 및 소비자용 사물의 인터넷 접속의 총수가 이와 같이 대폭 증가하는 것으로, 시장 전체의 성장 기회가 크게 촉진될 것으로 예측됩니다.
북미의 IoT 보안 산업 개요
북미의 IoT 보안 시장 경쟁 구도은 이 지역 전체에 다수의 지역 진출기업이 존재하기 때문에 부문화가 특징입니다. 이러한 시장 진출 기업은 다양한 산업에 대응하는 혁신적인 솔루션을 도입하는 움직임을 강화하고 있습니다. 게다가 이 시장에서는 시장에서의 존재감을 높이는 것을 목적으로 한 제휴와 인수가 현저하게 증가하고 있습니다.
2022년 12월, 사이버 보안 솔루션 제공업체인 Check Point Software Technologies Ltd.(Check Point Software Technologies Ltd.)는 Check Point Quantum 사이버 보안 플랫폼의 향상된 기능인 Check Point Quantum Titan을 발표했습니다. Quantum Titan은 딥러닝과 인공지능(AI)의 파워를 활용한 3개의 소프트웨어 블레이드를 통합한 것으로, 선진적 DNS(Domain Name System Exploits)와 피싱 공격에 대한 선진적 위협 방어를 실현하는 것 외에도 자율 IoT 보안도 설명합니다. 체크포인트의 Quantum Titan은 IoT 디바이스 감지 기능과 IoT 디바이스를 보호하기 위한 제로 트러스트 위협 방어 프로파일의 자동 적용 기능을 제공합니다.
Palo Alto Networks는 2022년 12월 의료기기용으로 설계된 종합적인 제로 트러스트 보안 솔루션인 Medical IoT Security를 발표했습니다. 이 솔루션을 통해 의료 조직은 새로운 커넥티드 기술을 안전하고 신속하게 구축하고 관리할 수 있습니다. 사이버 보안에 대한 제로 트러스트 방식은 모든 사용자와 장치를 지속적으로 검증하는 데 중점을 두어 조직의 보안 프레임워크 내에서 암시적 신뢰를 제거합니다.
기타 혜택
- 엑셀 형식 시장 예측(ME) 시트
- 3개월간의 애널리스트 서포트
목차
제1장 서론
- 조사의 전제조건과 시장 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 인사이트
- 시장 개요
- 산업의 매력 - Porter's Five Forces 분석
- 신규 참가업체의 위협
- 구매자/소비자의 협상력
- 공급기업의 협상력
- 대체품의 위협
- 경쟁 기업 간 경쟁 관계의 강도
- 산업 밸류체인 분석
- 시장에 대한 COVID-19의 영향 평가
제5장 시장 역학
- 시장 성장 촉진요인
- 데이터 유출 증가
- 스마트 시티의 출현
- 시장 성장 억제요인
- 디바이스 간의 복잡화와 유비쿼터스 법제의 부족
제6장 시장 세분화
- 보안 유형
- 네트워크 보안
- 엔드포인트 보안
- 솔루션
- 소프트웨어
- 서비스
- 최종 사용자 산업
- 자동차
- 의료
- 정부기관
- 제조업
- 에너지 및 전력
- 소매업
- BFSI
- 기타
- 지역
- 미국
- 캐나다
제7장 경쟁 구도
- 기업 프로파일
- Symantec Corporation
- IBM Corporation
- Check Point Software Technologies Ltd.
- Intel Corporation
- Hewlett Packard Enterprise Company
- Cisco Systems Inc.
- Fortinet Inc.
- Trustwave Holdings
- AT&T Inc.
- Palo Alto Networks Inc.
제8장 투자 분석
제9장 시장 기회와 앞으로의 동향
KTH 25.02.07The North America IoT Security Market size is estimated at USD 11.94 billion in 2025, and is expected to reach USD 32.23 billion by 2030, at a CAGR of 21.97% during the forecast period (2025-2030).
Key Highlights
- The emerging business models and applications, coupled with the reducing device costs, have been instrumental in driving the adoption of IoT, consequently, the number of connected devices, such as connected machines, wearables, cars, meters, and consumer electronics.
- Attacks on consumer IoT devices are prevalent, and the overall possibility of disruption in manufacturing and similar industries makes the threat more serious. Various end-user industries in the United States and Canada have faced considerable security attacks in various industries in the past few years. IoT security is becoming a significant focus area for businesses, consumers, and regulators. Following such increasing prominence, enterprises that are offering IoT-based solutions worldwide are investing heavily in the security aspect of these solutions.
- For instance, in October 2022, Datadog, Inc., the monitoring and security platform for cloud applications, declared the general availability of Cloud Security Management. This product brings together capabilities from Cloud Security Posture Management (CSPM), Cloud Workload Security (CWS), alerting, incident management, and reporting in a single platform to enable DevOps and Security teams to identify misconfigurations, detect threats, and secure cloud-native applications.
- Moreover, the increasing dependency on connected devices is creating the need to keep the connected devices secure. This significant growth is anticipated to be driven by the growing industry focus on deploying a connected ecosystem as well as the standardization of 3GPP cellular IoT technologies.
- With the growing number of devices connected to the Internet, the cyber world is anticipated to witness a significant rise in the occurrence and emergence of new threats and attacks. IoT devices are particularly vulnerable to various network attacks, such as data theft, spoofing, phishing attacks, and DDoS attacks (denial of service attacks). These can lead to various cybersecurity-related threats like ransomware attacks and other serious data breaches that can take businesses a lot of money and effort to recover from.
- However, the growing complexity among devices, coupled with the lack of ubiquitous legislation, could be a major matter of concern that can limit the overall market's growth throughout the forecast period.
- Since the beginning of COVID-19, there has been an increase in IoT attacks, and hence, countries worldwide have implemented several preventive measures. With communities being asked to stay at home and schools being closed, multiple organizations have found a way to allow their employees to work from their homes. This has resulted in a rise in the adoption of video communication platforms. Moreover, during the post-COVID-19 period, the market is expected to witness significant growth opportunities, especially due to the introduction of various cost-effective cloud-based and hybrid solutions by the leading major market participants.
North America IoT Security Market Trends
Increasing Number of Data Breaches is Anticipated to Drive the Market
- With the increase in the number of devices connected to the Internet, the cyber world is expected to witness a rise in the occurrence and emergence of new threats and attacks. This is evident by the growth in data breaches across the North America region in various end-user verticals over the past few years. These attacks, which directly target business systems and individuals, may potentially lead to enormous financial and personal losses. Thus fueling the need for IoT security for consumer devices that are highly susceptible to data breaches.
- Moreover, the growth in data breaches across the region in various end-user industries, such as healthcare, manufacturing, BFSI, automotive, etc., is driving the need for IoT security solutions to protect their connected devices from cyberattacks. For instance, according to the ITRC 2022 Annual Data Breach Report by Identity Theft Resource Center, the number of data compromises in the United States was 1802 cases in 2022. The number of data compromises in the United States significantly increased from 157 cases in 2005 to 1802 cases in 2022.
- Further, cloud services are experiencing high adoption rates owing to the demand for IoT. This increasing use of cloud systems across various verticals has increased the vulnerabilities of these systems to data breaches. With many providers offering multiple solutions, the need for a uniform security platform is rising. IoT security can be deployed for devices and communication, data storage, and lifecycle solutions.
- Additionally, the market is further expected to grow due to the increasing government initiatives to protect businesses from cyberattacks. For instance, in July 2023, The Biden administration launched an Internet of Things (IoT) cybersecurity labeling program to protect Americans against the myriad security risks associated with internet-connected devices. The program, "U.S. Cyber Trust Mark," aims to help Americans ensure they are buying internet-connected devices that include strong cybersecurity protections against cyberattacks.
United States is Expected to Dominate the Market
- The major crucial factors for the growth of the IoT security market in the United States are the high adoption of advanced technologies, increasing cyberattacks, and a growing number of connected devices in the country. The country is one of the dominant regions for IoT deployment. Other factors include the growth in digitalization and IoT security spending in the region.
- Moreover, the region houses significant IoT Security vendors, including Symantec Corporation, IBM Corporation, FireEye Inc., and Palo Alto Networks Inc., among others. The vendors are strengthening their product portfolio and market presence by boosting their product innovation. For instance, in March 2022, Palo Alto Networks, a provider of network firewalls, declared that it has teamed up with Amazon Web Services to unveil the new Palo Alto Networks Cloud NGFW for AWS, a managed Next-Generation Firewall (NGFW) service designed to simplify securing AWS deployments, allowing organizations to speed their pace of innovation while remaining highly secure.
- Also, in May 2022, STMicroelectronics, a global semiconductor provider serving customers across the spectrum of electronics applications, revealed the details of its collaboration with Microsoft, an ST-authorized partner. The aim was to strengthen the security of emerging Internet-of-things applications. ST is combining its ultra-low-power STM32U5 microcontrollers with Microsoft Azure RTOS & IoT Middleware as well as a certified secure implementation of the Arm Trusted Firmware -M (TF-M) secure services, especially for embedded systems.
- Moreover, the United States is experiencing an increasing number of cyber threats. According to the Identity Theft Resource Center, the average number of breaches in the country has increased marginally over the past few years. In October 2022, The Biden-Harris Administration brought a significant focus to improving the United States' cyber defenses, building a comprehensive approach to take aggressive action to strengthen and safeguard the nation's cybersecurity.
- As per GSMA Intelligence, the total number of industrial and consumer Internet of Things connections in North America is forecast to grow to around 5.4 billion by the end of the year 2025. In 2019, the total number of IoT connections in North America amounted to 2.8 billion connections. Such a significant rise in the overall count of the industrial and consumer Internet of Things connections within the region is expected to propel the market's overall growth opportunities significantly.
North America IoT Security Industry Overview
The competitive landscape of the North American IoT Security Market is characterized by fragmentation due to the presence of numerous regional players across the region. These market participants are increasingly introducing innovative solutions to cater to various industries. Furthermore, the market is experiencing a notable increase in collaborations and acquisitions aimed at enhancing its market presence.
In December 2022, Check Point Software Technologies Ltd., a cybersecurity solutions provider, unveiled Check Point Quantum Titan, an enhancement to the Check Point Quantum cyber security platform. The Quantum Titan release incorporates three software blades that harness the power of deep learning and artificial intelligence (AI) to offer advanced threat prevention against sophisticated domain name system exploits (DNS) and phishing attacks, as well as autonomous IoT security. With Check Point Quantum Titan, the platform now includes IoT device discovery and the automatic application of zero-trust threat prevention profiles to safeguard IoT devices.
In December 2022, Palo Alto Networks introduced Medical IoT Security, a comprehensive Zero Trust security solution designed for medical devices. This solution enables healthcare organizations to securely and rapidly deploy and manage new connected technologies. The zero-trust approach to cybersecurity focuses on continuously verifying every user and device, thereby eliminating implicit trust within the organization's security framework.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Attractiveness - Porter's Five Forces Analysis
- 4.2.1 Threat of New Entrants
- 4.2.2 Bargaining Power of Buyers/Consumers
- 4.2.3 Bargaining Power of Suppliers
- 4.2.4 Threat of Substitute Products
- 4.2.5 Intensity of Competitive Rivalry
- 4.3 Industry Value Chain Analysis
- 4.4 Assessment of Impact of Covid-19 on the Market
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Increasing Number of Data Breaches
- 5.1.2 Emergence of Smart Cities
- 5.2 Market Restraints
- 5.2.1 Growing Complexity among Devices, coupled with the Lack of Ubiquitous Legislation
6 MARKET SEGMENTATION
- 6.1 Type of Security
- 6.1.1 Network Security
- 6.1.2 End-point Security
- 6.2 Solution
- 6.2.1 Software
- 6.2.2 Services
- 6.3 End-user Industry
- 6.3.1 Automotive
- 6.3.2 Healthcare
- 6.3.3 Government
- 6.3.4 Manufacturing
- 6.3.5 Energy and Power
- 6.3.6 Retail
- 6.3.7 BFSI
- 6.3.8 Others End-user Industries
- 6.4 Geography
- 6.4.1 United States
- 6.4.2 Canada
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 Symantec Corporation
- 7.1.2 IBM Corporation
- 7.1.3 Check Point Software Technologies Ltd.
- 7.1.4 Intel Corporation
- 7.1.5 Hewlett Packard Enterprise Company
- 7.1.6 Cisco Systems Inc.
- 7.1.7 Fortinet Inc.
- 7.1.8 Trustwave Holdings
- 7.1.9 AT&T Inc.
- 7.1.10 Palo Alto Networks Inc.



















