
|
시장보고서
상품코드
1850147
유럽의 IoT 보안 시장 : 점유율 분석, 산업 동향, 통계, 성장 예측(2025-2030년)Europe IoT Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
유럽의 IoT 보안 시장 규모는 2025년에 76억 6,000만 달러, 2030년에는 201억 1,000만 달러에 이르고, CAGR은 21.3%를 기록할 전망입니다.

커넥티드 디바이스에 대한 사이버 공격 증가, 엄격한 규제의 의무화, 제조업에 있어서의 Industrie 4.0 솔루션의 급속한 채택이 결합되어, 특수한 보안 플랫폼에의 지출이 가속하고 있습니다. 수요는 운영 기술을 보호하는 네트워크 중심의 방어에 집중하고 양자 안전 암호에 대한 투자는 장기적인 탄력성의 우선 순위를 나타냅니다. 하이브리드 클라우드 에지에 대한 보안 애널리틱스를 제공하는 공급업체는 데이터 주권에 대한 규칙과 확장 가능한 위협 인텔리전스의 필요성의 균형을 유지하면서 기업의 지지를 모으고 있습니다. 틈새 신흥기업이나 반도체 기업와의 경쟁 격화로 기존 기업은 특히 AI를 활용한 감지 및 보안 요소 설계에 특화된 능력을 획득할 필요가 있습니다.
유럽의 IoT 보안 시장 동향과 통찰
IoT 엔드포인트 급증으로 공격 대상 확대
유럽 기업들은 2024년 동안 수백만대의 센서, 게이트웨이, 로봇 유닛을 추가해 IoT에 초점을 맞춘 공격을 107% 급증시켰습니다. 제조업에서는 500건이 넘는 랜섬웨어 사고가 발생하여 개별 생산 라인이 중단되어 비용이 많이 드는 다운타임을 강요했습니다. 레거시 브라운필드 머신이 IP 기반 네트워크와 통합됨에 따라 기존 테두리가 무너지고 CISO는 확장 가능한 제로 트러스트 에이전트와 보안 장치 관리 오버레이를 도입해야합니다. 따라서 펌웨어 무결성을 원격으로 강제하고 비정상적인 동작을 감지하는 엔드포인트 보호 플랫폼에 대한 수요가 유럽의 IoT 보안 시장 전반에 걸쳐 증가하고 있습니다. 운영 처리량에 영향을 미치지 않고 이기종 장치를 모니터링할 수 있는 공급업체는 Industrie 4.0 채택 기업간 경쟁 우위를 확보합니다.
EU 전역에서 데이터 보호 의무화로 보안 지출 가속
NIS2 지령은 2024년 10월부터 발효되어 유럽의 약 35만 조직에 정보 유출 보고 의무와 리스크 관리 의무를 확대했습니다. 사이버 탄력성 법의 동시 시행은 제조업체가 설계 단계부터 보안을 통합하고 소프트웨어 부품표를 유지하도록 의무화하고 위반하는 경우 최대 1,500만 유로의 벌금을 부과합니다. 프랑스의 의료기관 및 통신사업자는 2024년에 발생한 수백만 건의 데이터 유출 사건을 받았으며, 이미 ANSSI의 엄격한 감사를 받고 있습니다. 컴플라이언스의 긴급성은 관리된 감지, 취약성 관리 및 공급망 평가 솔루션에 대한 즉각적인 예산 재분배에 반영되어 유럽 IoT 보안 시장의 단기 성장을 가속하고 있습니다.
이기종 장치 간의 단편적 보안 표준
ETSI EN 303 645는 기본 비밀번호 삭제와 같은 기본 제어를 정의하지만, 각 섹터마다 다른 프레임워크 및 국가의 인증 시스템이 복잡해지고 있습니다. 최근 예정된 EU 사이버 보안 인증 체계는 커먼크라이테리아를 기반으로 하면서도 새로운 보증 클래스를 도입하고 있기 때문에 중소기업은 중복 심사나 급등하는 컨설턴트료에 시달리게 됩니다. SMESEC 프로젝트에 따르면 현재 공격의 43%가 중소기업을 대상으로 하고 있으며, 디바이스 포트폴리오는 소비자 및 산업용 범주에 걸쳐 있기 때문에 대규모 보안의 도입이 늦어지고 있습니다.
부문 분석
네트워크 보안의 2024년 매출은 38.6%에 달했고 산업용 트래픽을 분리하고 최소 권한 세분화를 수행하는 데 기본적인 역할을 하는 것으로 나타났습니다. Modbus, PROFINET 및 OPC UA를 위해 조정된 깊은 패킷 검사 엔진은 IT-OT 백본의 수평 이동 위험을 줄입니다. 연결성 방어 유럽의 IoT 보안 시장 규모에서 프로토콜을 인식하는 위협 분석은 공장 바닥에서 자율 이동 로봇을 연결하는 5G 사설망과 병행하여 성장할 것으로 예측됩니다. 클라우드 보안은 현재 시장 규모가 작고 기업이 데이터 파이프라인을 하이퍼스케일 클라우드 및 주권 지역 클라우드로 전환함에 따라 CAGR 21.5%로 성장합니다. 제로 트러스트 네트워킹과 클라우드 네이티브 방화벽을 통합한 SASE(Secure Access Service Edge) 제품은 2025년 조달 로드맵의 상위 순위를 차지하며 클라우드 보안은 2030년까지 수익 격차를 줄일 수 있습니다.
스마트 카메라, 웨어러블 센서, 지속적인 소프트웨어 무결성 검증을 필요로 하는 마이크로서비스의 보급에 따라 엔드포인트 보안 및 용도 보안에 대한 수요가 증가하고 있습니다. 또한 PFU(Physical Unclonable Function: 물리적으로 암호화할 수 없는 기능) 등의 내장형 또는 칩 레벨 제어가 새로운 자동차 및 헬스케어 기기에 탑재되어 유럽 공통 중요 프로젝트(IPCEI)의 공동출자에 의한 반도체 프로그램이 보급을 뒷받침하고 있습니다. 이러한 레이어에 걸쳐 종합적인 포트폴리오를 제공하는 공급업체는 유럽의 IoT 보안 시장에서 더 큰 슬라이스를 획득할 것으로 보입니다.
2024년 총 지출액의 66.5%는 소프트웨어가 차지하며, 이는 수십만대의 디바이스로 확장 가능한 라이선스 기반의 애널리틱스 엔진을 기업이 선호하기 때문입니다. 비정상적인 감지, 펌웨어 업데이트의 안전한 오케스트레이션, 암호화 키 수명주기 관리는 종종 Kubernetes 클러스터에 배포하기 쉬운 컨테이너화된 모듈로 제공됩니다. 결과적으로 위협 인텔리전스 피드 및 취약성 스캐너를 통합 콘솔에 패키징한 플랫폼 공급업체는 유럽의 IoT 보안 시장 규모 전반에 걸쳐 높은 업데이트율을 유지하고 있습니다.
그러나 사내 전문가가 없는 중소기업은 위협 조사, 사고 대응, 컴플라이언스 보고서를 아웃소싱하기 때문에 서비스 CAGR은 가장 빠른 22.8%로 성장을 지속하고 있습니다. Managed Security Service Provider(MSSP)는 24시간 365일 모니터링, 침입 테스트, 법규 갭 평가를 엄격한 자본 예산으로 매력적인 구독 모델에 번들로 제공합니다. 복잡한 브라운필드 환경 내에서 서로 다른 보안 관리를 통합하고 사이버 탄력성 법률 준수를 문서화할 수 있는 공급업체에 속하지 않는 컨설턴트는 유럽의 IoT 보안 업계에서 지속적인 수요가 예상됩니다. 하드웨어 매출은 지속적으로 견고하며 신뢰할 수 있는 플랫폼 모듈과 위험이 높은 의료용 임플란트 및 자동차 ECU에 의무화된 보안 요소를 지원합니다.
기타 혜택 :
- 엑셀 형식 시장 예측(ME) 시트
- 3개월간의 애널리스트 서포트
목차
제1장 서론
- 조사의 전제조건과 시장의 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 상황
- 시장 개요
- 시장 성장 촉진요인
- IoT 엔드포인트 증가에 의해 공격 대상 영역이 확대
- EU 전체의 데이터 보호 의무에 의해 보안 지출이 가속
- 스마트 팩토리에서 산업 IoT의 급속한 도입
- 중요 인프라에 대한 고급 사이버 공격
- 양자 내성 암호화 기술 개발 추진
- 호라이즌 유럽과 국가조성금에 의한 중소기업의 보안 강화에의 보조
- 시장 성장 억제요인
- 이기종 기기 간의 보안 표준의 단편화
- 기존 브라운필드 자산의 높은 통합 비용
- 유럽의 중소기업에서 IoT 보안 인력 부족
- 보안 요소 출시를 지연시키는 반도체 공급망 병목 현상
- 밸류체인 분석
- 규제 상황
- 기술의 전망
- Porter's Five Forces 분석
- 공급기업의 협상력
- 구매자의 협상력
- 신규 참가업체의 위협
- 대체품의 위협
- 경쟁 기업간 경쟁 관계
- 거시 경제 동향이 시장에 미치는 영향 평가
제5장 시장 규모와 성장 예측
- 보안 유형별
- 네트워크 보안
- 엔드포인트 보안
- 용도 보안
- 클라우드 보안
- 임베디드/칩 레벨 보안
- 기타 틈새 보안 유형
- 솔루션별
- 하드웨어
- 소프트웨어
- 서비스
- 전개 모드별
- On-Premise
- 클라우드
- 최종 사용자 업계별
- 자동차 및 운송
- 헬스케어 및 생명과학
- 정부 및 방위
- 제조업과 산업
- 에너지 및 유틸리티
- 기타 최종 사용자 산업
- 국가별
- 독일
- 영국
- 프랑스
- 이탈리아
- 스페인
- 기타 유럽
제6장 경쟁 구도
- 시장 집중도
- 전략적 동향
- 시장 점유율 분석
- 기업 프로파일
- Cisco Systems Inc.
- IBM Corporation
- Thales DIS(Gemalto)
- Fortinet Inc.
- Infineon Technologies AG
- Intel Corporation
- Sophos Group PLC
- Palo Alto Networks Inc.
- Hewlett Packard Enterprise Co.
- Broadcom Inc.(Symantec)
- Trend Micro Inc.
- Check Point Software Technologies Ltd.
- Kaspersky Lab
- ARM Ltd.
- Atos SE
- Siemens Digital Industries Software
- Avast PLC
- NXP Semiconductors NV
- Device Authority Ltd.
- Secure Thingz Ltd.
제7장 시장 기회와 장래의 전망
SHW 25.11.17The Europe IoT Security market size is valued at USD 7.66 billion in 2025 and is forecast to reach USD 20.11 billion by 2030, registering a 21.3% CAGR.
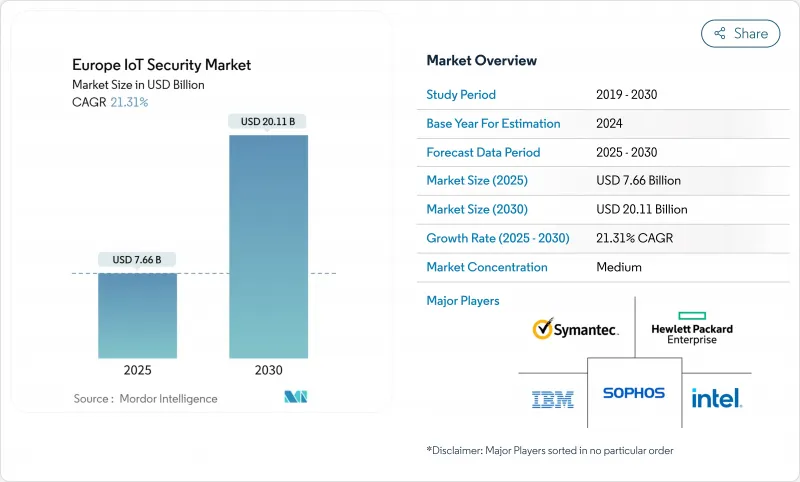
Rising cyber-attacks on connected devices, stringent regulatory mandates and fast adoption of Industrie 4.0 solutions in manufacturing combine to accelerate spending on specialised security platforms. Demand concentrates on network-centric defences that safeguard operational technology, while quantum-safe cryptography investments signal long-term resilience priorities. Vendors offering hybrid cloud-edge security analytics gain traction as enterprises balance data-sovereignty rules with the need for scalable threat intelligence. Intensifying competition from niche start-ups and semiconductor players is prompting incumbents to acquire specialised capabilities, especially around AI-driven detection and secure-element design.
Europe IoT Security Market Trends and Insights
Proliferation of IoT Endpoints Enlarging Attack Surface
European enterprises added millions of sensors, gateways and robotics units during 2024, driving a 107% spike in IoT-focused attacks. Manufacturing recorded more than 500 ransomware incidents that disrupted discrete production lines and forced costly downtime. Legacy brownfield machinery integrating with IP-based networks dissolves traditional perimeters, compelling CISOs to deploy scalable zero-trust agents and secured device-management overlays. Demand for endpoint protection platforms that remotely enforce firmware integrity and detect anomalous behaviour therefore rises across the Europe IoT Security market. Vendors that can monitor heterogeneous devices without impacting operational throughput gain competitive advantage among Industrie 4.0 adopters.
EU-wide Data-Protection Mandates Accelerating Security Spend
The NIS2 Directive, effective from October 2024, extended breach-reporting and risk-management obligations to about 350,000 European organisations. Parallel enactment of the Cyber Resilience Act compels manufacturers to embed security-by-design and maintain software bills of materials, with fines reaching EUR 15 million. Healthcare and telecom operators in France already face active audits by ANSSI following several multi-million-record breaches during 2024. Compliance urgency is translating into immediate budget reallocations toward managed detection, vulnerability management and supply-chain assessment solutions, fuelling short-term growth across the Europe IoT Security market.
Fragmented Security Standards Across Heterogeneous Devices
While ETSI EN 303 645 defines baseline controls such as removal of default passwords, differing sectoral frameworks and national certification schemes add layers of complexity. The forthcoming EU Cybersecurity Certification Scheme builds on Common Criteria but introduces new assurance classes, leaving SMEs juggling overlapping audits and spiralling consultancy fees. The SMESEC project found that 43% of attacks now target small businesses whose device portfolios span consumer and industrial categories, delaying large-scale security roll-outs.
Other drivers and restraints analyzed in the detailed report include:
- Rapid Industrial-IoT Adoption in Smart Factories
- Sophisticated Cyber-Attacks on Critical Infrastructure
- High Integration Cost for Legacy Brown-Field Assets
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Network Security generated 38.6% revenue in 2024, underlining its foundational role in isolating industrial traffic and enforcing least-privilege segmentation. Deep-packet inspection engines tuned for Modbus, PROFINET and OPC UA mitigate lateral movement risks across converged IT-OT backbones. Inside the Europe IoT Security market size for connectivity defences, protocol-aware threat analytics are expected to grow parallel to 5G private networks that connect autonomous mobile robots on factory floors. Cloud Security, although smaller today, grows at 21.5% CAGR as enterprises shift data pipelines to hyperscale and sovereign regional clouds. Secure access service edge (SASE) offerings that converge zero-trust networking and cloud-native firewalls rank high on 2025 procurement roadmaps, positioning Cloud Security to narrow the revenue gap before 2030.
Demand for Endpoint and Application Security follows the proliferation of smart cameras, wearable sensors and micro-services that require continuous software-integrity validation. Embedded or chip-level controls such as physically unclonable functions (PUFs) appear in new automotive and healthcare devices, with semiconductor programmes co-funded under the Important Project of Common European Interest (IPCEI) fuelling uptake. Vendors delivering holistic portfolios across these layers will capture a larger slice of the Europe IoT Security market.
Software accounted for 66.5% of total spending in 2024 because enterprises prefer licence-based analytics engines that scale across hundreds of thousands of devices. Behavioural anomaly detection, secure orchestration of firmware updates and cryptographic key-lifecycle management are increasingly delivered as containerised modules easy to deploy in Kubernetes clusters. Consequently, platform suppliers that package threat intelligence feeds and vulnerability scanners within a unified console retain high renewal rates across the Europe IoT Security market size.
Services, however, post the fastest 22.8% CAGR as SMEs lacking in-house specialists outsource threat hunting, incident response and compliance reporting. Managed security service providers (MSSPs) bundle 24X7 monitoring, penetration testing and regulatory gap assessments into subscription models attractive under tight capital budgets. Vendor-agnostic consultants that can integrate disparate security controls inside complex brownfield environments and document Cyber Resilience Act compliance are poised for sustained demand within the Europe IoT Security industry. Hardware sales remain steadier, anchored by trusted-platform modules and secure elements mandated for high-risk medical implants and automotive ECUs.
The Europe IoT Security Market Report is Segmented by Security Type (Network Security, Endpoint Security, Application Security, and More), Solution (Hardware, Software, and Services), Deployment Mode (On-Premise and Cloud), End-User Industry (Automotive and Transportation, Healthcare and Life Sciences, Government and Defence, and More), and Country. The Market Forecasts are Provided in Terms of Value (USD).
List of Companies Covered in this Report:
- Cisco Systems Inc.
- IBM Corporation
- Thales DIS (Gemalto)
- Fortinet Inc.
- Infineon Technologies AG
- Intel Corporation
- Sophos Group PLC
- Palo Alto Networks Inc.
- Hewlett Packard Enterprise Co.
- Broadcom Inc. (Symantec)
- Trend Micro Inc.
- Check Point Software Technologies Ltd.
- Kaspersky Lab
- ARM Ltd.
- Atos SE
- Siemens Digital Industries Software
- Avast PLC
- NXP Semiconductors N.V.
- Device Authority Ltd.
- Secure Thingz Ltd.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Proliferation of IoT endpoints enlarging attack surface
- 4.2.2 EU-wide data-protection mandates accelerating security spend
- 4.2.3 Rapid industrial-IoT adoption in smart factories
- 4.2.4 Sophisticated cyber-attacks on critical infrastructure
- 4.2.5 Post-quantum-ready cryptography initiatives
- 4.2.6 Horizon Europe and national grants subsidising SME security upgrades
- 4.3 Market Restraints
- 4.3.1 Fragmented security standards across heterogeneous devices
- 4.3.2 High integration cost for legacy brown-field assets
- 4.3.3 Scarcity of IoT-security talent in European SMBs
- 4.3.4 Semiconductor supply-chain bottlenecks delaying secure-element roll-outs
- 4.4 Value Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Porter's Five Forces Analysis
- 4.7.1 Bargaining Power of Suppliers
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Threat of New Entrants
- 4.7.4 Threat of Substitutes
- 4.7.5 Intensity of Competitive Rivalry
- 4.8 Assessment of the Impact of Macroeconomic Trends on the Market
5 MARKET SIZE AND GROWTH FORECASTS (VALUE)
- 5.1 By Security Type
- 5.1.1 Network Security
- 5.1.2 Endpoint Security
- 5.1.3 Application Security
- 5.1.4 Cloud Security
- 5.1.5 Embedded/Chip-level Security
- 5.1.6 Other Niche Security Types
- 5.2 By Solution
- 5.2.1 Hardware
- 5.2.2 Software
- 5.2.3 Services
- 5.3 By Deployment Mode
- 5.3.1 On-Premise
- 5.3.2 Cloud
- 5.4 By End-User Industry
- 5.4.1 Automotive and Transportation
- 5.4.2 Healthcare and Life Sciences
- 5.4.3 Government and Defence
- 5.4.4 Manufacturing and Industrial
- 5.4.5 Energy and Utilities
- 5.4.6 Other End-User Industries
- 5.5 By Country
- 5.5.1 Germany
- 5.5.2 United Kingdom
- 5.5.3 France
- 5.5.4 Italy
- 5.5.5 Spain
- 5.5.6 Rest of Europe
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 Cisco Systems Inc.
- 6.4.2 IBM Corporation
- 6.4.3 Thales DIS (Gemalto)
- 6.4.4 Fortinet Inc.
- 6.4.5 Infineon Technologies AG
- 6.4.6 Intel Corporation
- 6.4.7 Sophos Group PLC
- 6.4.8 Palo Alto Networks Inc.
- 6.4.9 Hewlett Packard Enterprise Co.
- 6.4.10 Broadcom Inc. (Symantec)
- 6.4.11 Trend Micro Inc.
- 6.4.12 Check Point Software Technologies Ltd.
- 6.4.13 Kaspersky Lab
- 6.4.14 ARM Ltd.
- 6.4.15 Atos SE
- 6.4.16 Siemens Digital Industries Software
- 6.4.17 Avast PLC
- 6.4.18 NXP Semiconductors N.V.
- 6.4.19 Device Authority Ltd.
- 6.4.20 Secure Thingz Ltd.
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-Need Assessment



















