
|
시장보고서
상품코드
1642059
물리적 ID 및 액세스 관리(PIAM) 소프트웨어 시장 : 시장 점유율 분석, 산업 동향 및 통계, 성장 예측(2025-2030년)Physical Identity and Access Management (PIAM) Software - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
물리적 ID 및 액세스 관리(PIAM) 소프트웨어 시장 규모는 2025년에 9억 8,000만 달러로 추정되고, 예측 기간(2025-2030년)의 CAGR은 14.22%로 전망되며, 2030년에는 19억 1,000만 달러에 달할 것으로 예측됩니다.

주요 하이라이트
- PIAM 솔루션은 IT 전문가가 보유한 물리적 보안 문제를 극복하는 데 필요한 기능과 특성을 제공할 수 있기 때문에 IT 부문에서는 네트워크화된 장치가 증가하고 물리적 보안 시스템을 구축, 배포 및 관리하는 기업에 영향을 주고 시장을 크게 견인하고 있습니다.
- 물리적 ID 및 액세스 관리(PIAM) 소프트웨어를 통해 조직은 직원, 계약자, 공급업체 등의 ID 라이프사이클을 관리할 수 있습니다. 따라서 물리적 ID 및 액세스 관리(PIAM)에 대한 전반적인 수요는 컴플라이언스 의무화, 온프레미스 방문자와 같은 대체 사용자 집단 관리에 대한 요구가 높아지고 시기적절하고 안전한 액세스의 중요성에 따라 증가하고 있습니다. 또한 네트워크와 디지털 자산의 보안은 모든 비즈니스에 필수적이었습니다. 해커는 데이터 유출을 범할 뿐만 아니라 종종 네트워크 및 시설의 기밀 부분에 액세스할 수 있는 조직 내 개인도 시장 성장에 박차를 가하고 있습니다.
- 공항 통근자 수가 증가함에 따라 특히 일반인이 출입할 수 없는 장소의 보안에 대한 우려가 높아져 PIAM 시장에 절호의 기회를 제공합니다. PIAM 소프트웨어를 통해 공항 당국은 ID의 수명주기를 더 잘 관리할 수 있습니다. PIAM이 제공하는 이점은 운영 비용 절감, 보안, 고객 서비스, 연속성, 미래성 등입니다. 이러한 요인들도 예측 기간 동안 PIAM 시장을 견인할 것으로 기대됩니다.
- 또한, 다양한 중요한 진출기업들이 시장 내에서 신제품을 발표하고 있습니다. 예를 들어, 2022년 5월, Microsoft는 신원 및 액세스 관리 솔루션의 신제품 제품군인 Entra의 도입을 선언했습니다. 이 제품군은 주로 Azure AD와 같은 기존 도구 외에도 두 가지 새로운 제품 카테고리, 즉 클라우드 인프라 인타이틀먼트 관리(CIEM) 및 분산 ID 확인을 포함합니다. 사용자에게 Entra 제품군은 주로 보안 팀이 멀티클라우드 환경에서 권한을 관리하고 발견할 수 있도록 하여 모든 앱과 리소스에 대한 액세스를 보호하고 엔드 투 엔드에서 디지털 ID를 보호할 수 있도록 설계되었습니다.
- 그러나 타사 클라우드 소스에 저장된 데이터의 보안 관련 문제가 급증하고 있기 때문에 예측 기간 동안 전체 시장 성장이 억제될 수 있습니다.
- 물리적 정체성과 액세스 관리 시장은 COVID-19 보급의 영향이 최소화될 것으로 예상됩니다. 소비자는 소비를 유지하고 더 많은 물자를 재고할 가능성이 높습니다. ID 확인이 새로운 디지털 라이프의 초석이 되고 있는 가운데, 조직이 탄력성을 유지하기 위해 보안과 안전한 ID 확인에 주력하는 것은 임박한 과제가 되고 있습니다. COVID-19는 규모가 크거나 작지만 모든 기업 유형에 있어 이를 중심으로 삼았습니다. 그러나 의료 산업에서는 디지털화가 급속히 진행되고 있습니다. 기존 의료 서비스는 디지털 변환에 압력을 가하고 있습니다. 게다가 새로운 진출기업이 디지털 퍼스트의 새로운 솔루션을 제공할 기회를 잡고 있습니다. 이로 인해 의료 ID 및 액세스 관리(IAM) 솔루션에 대한 수요가 증가하고 있습니다.
물리적 ID 및 액세스 관리(PIAM) 소프트웨어 시장 동향
정부 기관과 법률 사무소 부문이 높은 속도로 성장
- 물리적 및 논리적 보안 인프라에 분산된 ID 확인 및 관련 영역을 실시간으로 관리하는 것이 매우 중요합니다. 따라서 물리적 ID 및 액세스 관리를 통해 ID 관리의 효율화와 자동화를 실현하면 이러한 사일로화를 억제할 수 있습니다. BASEL II 및 GLBA와 같은 다양한 규정은 규정 준수 관점에서 정착되어 있으며 예측 기간 동안 PIAM 시장에 긍정적 영향을 미칠 가능성이 높습니다.
- 은행 및 기타 금융기관은 적절한 보안 조치를 취하도록 모니터링의 눈을 돌리고 있습니다. 위협 증가에 직면한 금융기관의 경우, 첨단 비디오 모니터링 기능은 몇 가지 중요한 이점을 제공하지만, 부정 행위 방지는 큰 장점이며 조사된 시장에 큰 성장 기회를 창출하고 있습니다.
- 게다가 많은 은행과 금융기관들은 고객이 신뢰할 수 있는 귀중하고 기밀성이 높은 금융자산을 안전하게 보호하는 것이 중요하다는 것을 인식하고 있습니다. 따라서 이러한 조직의 대부분은 수익, 영업 비용, 명성 등에 부정적인 영향을 미칠 수 있는 보안 저하를 방지하기 위해 첨단 기술에 투자하고 있습니다. PIAM 솔루션은 여러 가지 이기종 보안 시스템과 비보안 시스템에서 데이터를 검색, 저장, 분석하고 보고서를 작성하고 비즈니스 사례를 안전하게 구축할 수 있도록 지원하며 위협 및 비용 절감 가능성에 대한 실용적인 인텔리전스를 제공합니다.
- 또한, 이 시장은 비즈니스를 개선하고 고객에게 도달하고 다양한 용도의 요구 사항을 충족하는 존재감을 높이는 전략의 일환으로 주요 기업에 의한 여러 합병, 인수, 투자가 이루어지고 있습니다. 예를 들어, 2022년 5월, 신뢰할 수 있는 ID 확인, 결제, 데이터 보호의 세계 리더인 Entrust는 두바이를 기반으로 하는 사이버 보안에 특화된 부가가치 유통업체인 CyberKnight와의 새로운 판매 제휴를 발표하여 보안 전문가가 컴플라이언스에 대응하고 사이버 위협 관리를 간소화할 수 있도록 했습니다.
- Identity Theft Resource Center에 따르면 작년 상반기에 미국에서 발생한 총 데이터 누출 수는 약 817건이었습니다. 한편, 동시기에 5,300만 명 이상의 개인이 데이터 유출, 데이터 침해, 데이터 노출을 포함한 데이터 침해에 큰 영향을 받았습니다. 이러한 경우 증가는 시장 성장을 크게 밀어 올릴 것으로 예상됩니다.
유럽이 큰 시장 점유율을 차지할 전망
- 유럽은 BFSI, 의료, 정부 등의 최종 사용자 산업에서 PIAM 소프트웨어의 채용이 증가하고 있기 때문에 시장 조사에서 큰 점유율을 차지할 것으로 예상됩니다. 많은 기업들은 제품과 기술의 확대, 컴플라이언스의 의무화, 대체 사용자 집단의 실현에 대한 요구 증가, 보안과 적시의 액세스의 중시 등에 의해 물리적 ID 및 액세스 관리(PIAM)의 약정을 도입하고 있습니다.
- EU는 또한 10년 말까지 디지털 ID를 사용할 것으로 예상되는 사용자 수의 목표를 설정했습니다. 2021년 3월 9일 유럽위원회 커뮤니케이션 '2030 Digital Compass : the European Way for the Digital Decade'는 EU가 2030년까지 디지털 마이그레이션을 성공시킬 수 있다는 비전을 보여주었습니다. 디지털 나침반 계획에서 회원국은 2030년까지 시민의 80%가 디지털 ID를 사용하도록 하고 시장 성장을 크게 촉진할 것으로 기대되고 있습니다.
- 게다가 이 시장에서는 비즈니스를 개선하고 고객에게 도달하고 다양한 용도의 요구사항을 충족하는 존재감을 높이는 전략의 일환으로 주요 기업에 의한 중요한 인수, 합병, 투자가 이루어지고 있습니다. 이 지역 내에서의 이러한 활동의 활성화는 시장 전체의 성장을 비약적으로 증대시키는 것으로 예상됩니다.
- 예를 들어, 유럽의 다국적 정보 기술 서비스 컨설팅 기업인 Atos는 작년 10월 Evidian IDaaS Access & Governance의 도입으로 아이덴티티 및 액세스 관리(IAM) 사이버 보안 서비스의 확대를 선언했습니다. 이 새로운 솔루션은 기존의 액세스 관리 기능(Evidian IDaaS Access) 외에도 온프레미스, 클라우드 기반 및 XaaS 애플리케이션을 관리하기 위한 전반적인 목적으로 필수적인 ID 거버넌스 및 관리 기능을 제공합니다.
- 작년 5월에는 영국에서 가장 적극적인 투자자 중 한 명인 Maven Capital Partners가 ID 및 액세스 관리(IAM) 서비스 전문 공급업체인 ProofID에 1,500만 달러의 투자를 표명했습니다. Maven의 투자를 통해 ProofID는 Ping Identity와의 파트너십을 지속적으로 확장하고 다른 IAM 공급업체와 보완적인 파트너십을 구축함으로써 보다 광범위한 IAM 솔루션을 제공할 수 있게 되어 성장 의욕을 높일 수 있습니다. 이 투자는 또한 회사의 인수 전략을 지원하여 영업, 마케팅 및 기술 자원에 대한 추가 투자를 가능하게 합니다.
물리적 ID 및 액세스 관리(PIAM) 소프트웨어 산업 개요
AlertEnterprise, HID Global 등 주요 기업은 PIAM 소프트웨어 시장 경쟁을 지배하고 있습니다. 전반적으로 산업 내 경쟁 기업 간의 적대적인 관계는 높으며 벤더는 고객의 새로운 요구에 맞는 제품과 서비스를 제공하는 지속적인 혁신을 추진하고 있습니다. 전략적 파트너십, 합병, 제휴 및 인수를 통해 시장에 진출하는 기업은 골격을 강화하고 고객에게 더 나은 솔루션과 제품을 제공합니다.
- 2023년 2월-AlertEnterprise, Inc.는 OpenAI ChatGPT를 탑재한 최초의 Guardian AI Chatbot 출시를 밝혔습니다. Guardian AI Chatbot은 OpenAI가 만든 세계적으로 유명한 GPT-3 플랫폼으로 개발되었습니다. 이는 신속한 질문과 프롬프트에서 보안 운영자에게 가장 중요한 물리적 액세스 및 보안에 대한 인사이트를 즉시 제공하도록 설계되었습니다.
기타 혜택
- 엑셀 형식 시장 예측(ME) 시트
- 3개월의 애널리스트 서포트
목차
제1장 서론
- 조사의 전제조건 및 시장 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 인사이트
- 시장 개요
- 시장 성장 촉진요인 및 시장 성장 억제요인의 채용
- 시장 성장 촉진요인
- 정부로부터의 컴플라이언스 의무
- 현장 방문자와 계약자의 관리
- 시장 성장 억제요인
- 제3자(클라우드)에 저장된 데이터의 보안
- 산업 밸류체인 분석
- 산업의 매력-Porter's Five Forces 분석
- 공급기업의 협상력
- 구매자 및 소비자의 협상력
- 신규 진입업자의 위협
- 대체품의 위협
- 경쟁 기업간 경쟁 관계의 강도
- 시장에 대한 COVID-19의 영향의 평가
- 규제의 영향
제5장 시장 세분화
- 유형별
- 소프트웨어
- 서비스
- 조직 규모별
- 중소기업(SME)
- 대기업
- 최종 사용자 산업별
- BFSI
- 항공우주 및 방위
- 정부기관 및 법률 사무소
- IT 및 통신
- 의료
- 교육
- 에너지 및 유틸리티
- 기타
- 지역
- 북미
- 유럽
- 아시아태평양
- 라틴아메리카
- 중동 및 아프리카
제6장 경쟁 구도
- 기업 프로파일
- HID Global Corporation
- AlertEnterprise Inc.
- IDCUBE Identification Systems(P) Ltd
- Micro Focus International PLC
- Amazon Web Services Inc.
- Convergint Technologies LLC
- WIPRO Ltd
- Acces Security Corporation
- IBM Corporation
- SAASPASS Inc.
제7장 투자 분석
제8장 시장의 미래
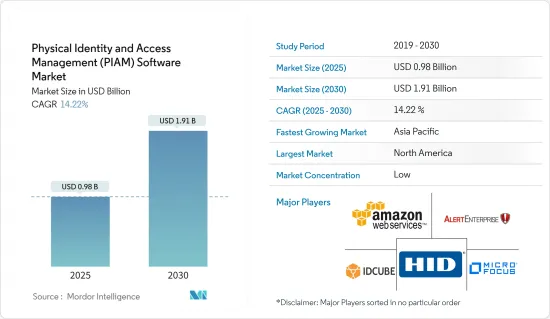
AJY 25.02.20The Physical Identity and Access Management Software Market size is estimated at USD 0.98 billion in 2025, and is expected to reach USD 1.91 billion by 2030, at a CAGR of 14.22% during the forecast period (2025-2030).
Key Highlights
- Since PIAM solutions can provide the required features and functions to overcome the IT professional's physical security challenges, there is an increased number of networked devices in the fields of IT that influenced the firms to establish or deploy and manage physical security systems, driving the market significantly.
- The physical identity and access management (PIAM) software allows organizations to manage the identity lifecycle, such as employees, contractors, and vendors. Hence, the overall demand for physical identity and access management (PIAM) is increasing due to compliance mandates, a growing desire to manage alternative user populations (like on-premises visitors), and an emphasis on timely and secure access. Moreover, securing networks and digital assets became necessary for every business. Hackers do not only commit data breaches but, many a time, also individuals within an organization who have access to sensitive parts of networks or facilities, fueling the market growth.
- An increase in the number of commuters at the airport led to a rise in security concerns, especially for the areas that are restricted to everyday people, thus offering an excellent opportunity for the PIAM market. PIAM software allows the airport authority to manage the identity life cycle better. The benefits provided by PIAM include a reduction in operational costs, security, customer service, continuity, future proof, etc. These factors are also expected to drive the PIAM market during the forecast period.
- Moreover, various vital significant players are launching new products within the market. For instance, in May 2022, Microsoft declared the introduction of Entra, a new product family of identity and access management solutions. The family mainly includes existing tools like Azure AD alongside two new product categories, i.e., Cloud Infrastructure Entitlement Management (CIEM) and Decentralized Identity. For users, the Entra product family is primarily designed to protect access to any app or resource by allowing security teams to manage and discover permissions in multi-cloud environments so they can secure digital identities from end to end.
- However, the surge in the security-related issues of data stored with third-party cloud sources might restrain the market's overall growth throughout the forecast period.
- The physical identity and access management market is expected to see a minimal impact of COVID-19 spread. Consumers are likely to keep their consumption and stock more supplies. As identity is becoming the cornerstone of the new digital life, it became imminent for organizations to focus on security and secure identities to stay resilient. COVID-19 made this even more central for all company types, regardless of size. However, the healthcare industry is seeing a rapid digitization rate. The pressure is on existing health services for digital transformation. In addition, new players are grabbing the opportunity to bring forward new digital-first solutions. It drives the demand for healthcare identity and access management (IAM) solutions.
Physical Identity and Access Management (PIAM) Software Market Trends
Government and Legal Firm Segment to grow at a higher pace
- Real-time management of identities and related areas dispersed across physical and logical security infrastructure became crucial. Therefore, creating efficiencies and automation in identity management through physical access and identity management may help curb such silos. Various regulations, such as BASEL II and GLBA, have become fixtures from a compliance standpoint and are likely to influence the PIAM market during the forecast period positively.
- Banks and other financial institutes are under increasing scrutiny to ensure they have the appropriate security measures in place, especially in the wake of numerous high-profile data breaches that have taken place over the last few years. Although advanced video surveillance capabilities offer several key advantages to financial institutions facing rising threats, preventing fraud is a major benefactor, creating significant growth opportunities for the studied market.
- Moreover, many banks and financial institutions have recognized the critical need to secure the valuable and sensitive financial assets their customers trust to keep them safe. Hence, most of these organizations have invested in advanced technologies to prevent lapses in security, which may negatively impact their revenues, operating costs, reputation, and much more. PIAM solutions capture, store, and analyze data from multiple disparate security and non-security systems to create reports that help securely build a business case and offer actionable intelligence about threats and potential cost savings.
- Moreover, the market is witnessing several mergers, acquisitions, and investments by key players as part of its strategy to improve business and their presence to reach customers and meet their requirements for various applications. For instance, in May 2022, Entrust, a global leader in trusted identity, payments, and data protection, announced its new distribution partnership with CyberKnight, a Dubai-based cybersecurity-focused value-added distributor, empowering security professionals to address compliance and simplify cyber threat management.
- As per Identity Theft Resource Center, in the first half of the last year, the total number of data compromises in the United States came in at around 817 cases. Meanwhile, over the same time, more than 53 million individuals were highly affected by data compromises involving data leakage, data breaches, and data exposure. A rise in such cases will significantly augment the market growth immensely.
Europe is Expected to Hold a Significant Market Share
- Europe is expected to hold a significant share of the market studied due to the growing adoption of PIAM software from end-user industries, such as BFSI, healthcare, and the government. Many businesses are implementing physical identity and access management (PIAM) arrangements due to product and technology expansion, compliance mandates, a greater desire to achieve substitute user populations, and a strong emphasis on security and timely access.
- The EU also set targets for the number of users as it expects to use digital identities by the decade's end. The Commission communication '2030 Digital Compass: the European Way for the Digital Decade' of 9 March 2021 set out a vision of the EU successfully achieving a digital transition by 2030. In the Digital Compass plan, member states are expected to ensure that 80% of citizens will use digital identities by 2030, significantly fueling the market growth.
- Moreover, the market is witnessing crucial acquisitions, mergers, and investments by key players as part of its strategy to improve business and their presence to reach customers and meet their requirements for various applications. A rise in such activities within the region will exponentially augment the overall market's growth.
- For instance, in October last year, Atos, a European multinational information technology service and consulting company, declared the extension of its Identity and Access Management (IAM) cybersecurity offering with the introduction of Evidian IDaaS Access & Governance. This new solution delivers essential identity governance and administration functions - in addition to the existing access management features (Evidian IDaaS Access) - with the overall objective of managing on-premises, cloud-based and as-a-Service applications.
- Also, in May last year, Maven Capital Partners, one of the UK's most active investors, declared a USD 15 million investment in ProofID, a specialist provider of identity and access management (IAM) services. The investment from Maven would allow the business to boost its growth ambitions by continuing to grow the partnership with Ping Identity and build complementary partnerships with other IAM vendors, enabling ProofID to deliver broader IAM solutions. The investment would also assist the company's acquisition strategy and allow further investment in its sales, marketing, and technical resources.
Physical Identity and Access Management (PIAM) Software Industry Overview
Some key players, such as AlertEnterprise, HID Global, etc., govern the competition in the PIAM software market. Overall, the competitive rivalry within the industry is high, pushing the vendors to make continued innovations in product and service offerings targeted toward the customers' emerging needs. Through strategic partnerships, mergers, collaborations, and acquisitions, the companies operating in the market can maintain their foothold, providing better solutions and products to their customers.
- February 2023 - AlertEnterprise, Inc. revealed the launch of its first-ever Guardian AI Chatbot powered by OpenAI ChatGPT. The Guardian AI Chatbot is developed with the world-renowned GPT-3 platform created by OpenAI. It is designed to instantly deliver security operators the physical access and security insights that matter most with quick questions and prompts.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Introduction to Market Drivers and Restraints
- 4.3 Market Drivers
- 4.3.1 Compliance Mandates from Governments
- 4.3.2 Management of On-site Visitors and Contractors
- 4.4 Market Restraints
- 4.4.1 Security of Data Stored with Third Party (Cloud)
- 4.5 Industry Value Chain Analysis
- 4.6 Industry Attractiveness - Porter's Five Forces Analysis
- 4.6.1 Bargaining Power of Suppliers
- 4.6.2 Bargaining Power of Buyers/Consumers
- 4.6.3 Threat of New Entrants
- 4.6.4 Threat of Substitute Products
- 4.6.5 Intensity of Competitive Rivalry
- 4.7 Assessment of COVID-19 Impact on the Market
- 4.8 Regulatory Implications
5 MARKET SEGMENTATION
- 5.1 By Type
- 5.1.1 Software
- 5.1.2 Services
- 5.2 By Organization Size
- 5.2.1 Small and Medium Enterprises (SMEs)
- 5.2.2 Large Enterprises
- 5.3 By End-user Industry
- 5.3.1 BFSI
- 5.3.2 Aerospace and Defense
- 5.3.3 Government and Legal Firm
- 5.3.4 IT and Telecom
- 5.3.5 Healthcare
- 5.3.6 Education
- 5.3.7 Energy and Utilities
- 5.3.8 Other End-user Industries
- 5.4 Geography
- 5.4.1 North America
- 5.4.2 Europe
- 5.4.3 Asia-Pacific
- 5.4.4 Latin America
- 5.4.5 Middle East & Africa
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles
- 6.1.1 HID Global Corporation
- 6.1.2 AlertEnterprise Inc.
- 6.1.3 IDCUBE Identification Systems (P) Ltd
- 6.1.4 Micro Focus International PLC
- 6.1.5 Amazon Web Services Inc.
- 6.1.6 Convergint Technologies LLC
- 6.1.7 WIPRO Ltd
- 6.1.8 Acces Security Corporation
- 6.1.9 IBM Corporation
- 6.1.10 SAASPASS Inc.








