
|
시장보고서
상품코드
1911763
하드웨어 방화벽 시장 : 점유율 분석, 업계 동향, 통계, 성장 예측(2026-2031년)Hardware Firewall - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2026 - 2031) |
||||||
하드웨어 방화벽 시장은 2025년 228억 7,000만 달러로 평가되었으며, 2026년 252억 8,000만 달러, 2031년까지 416억 2,000만 달러에 이를 것으로 예측됩니다. 예측기간(2026년-2031년)에 CAGR은 10.52%를 나타낼 전망입니다.
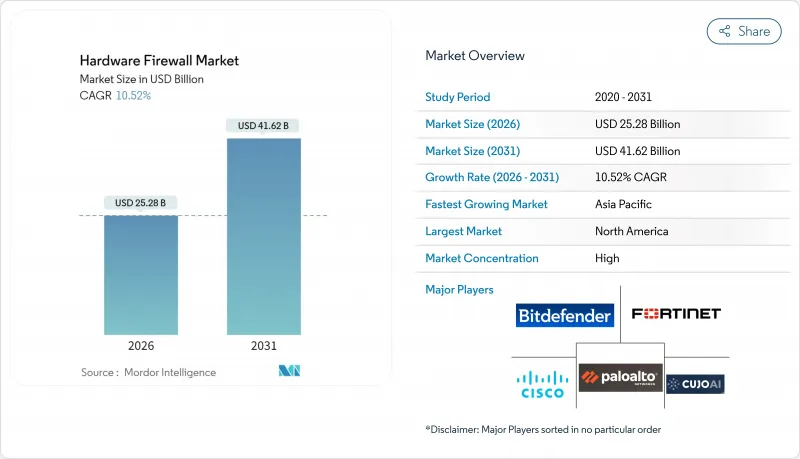
수요의 가속 요인으로는 연방 정부 및 중요 인프라 네트워크에서 제로 트러스트 요구 사항 도입, 엣지 컴퓨팅의 보급, 5G 네트워크의 고급화, 전체 데이터 흐름의 90%를 초과할 때까지 증가한 암호화 트래픽의 양이 포함됩니다. 장치/시스템 하드웨어가 수익의 대부분을 차지하고 있지만, 기업이 자본 구매에서 성과 기반 계약으로 전환함에 따라 관리 서비스의 성장이 가속화되고 있습니다. 대기업은 테라비트급 어플라이언스의 갱신 주기를 견인하고 중소기업은 단순화된 통합 위협 플랫폼을 채택하여 점진적인 성장을 가속합니다. 지역별로는 북미가 선두를 유지하고 있는 한편, 중국, 인도, ASEAN 회원국이 규제 프레임워크을 세계의 사이버 보안 기준에 정합시키는 가운데, 아시아태평양이 가장 급속한 확대를 기록하고 있습니다.
세계 하드웨어 방화벽 시장 동향과 인사이트
다각적 사이버 공격의 고도화가 진행되고 ASIC 가속형 검사의 필요성이 높아지고 있습니다.
위협 액터는 현재 랜섬웨어, 공급망 공격, 국가 지원 운영을 결합하여 CPU 중심 검사 엔진을 압도하고 있습니다. CISA는 2024년에 1,132건의 알려진 악용 취약점을 기록했으며 2023년 대비 23% 증가했습니다. 하드웨어 어플라이언스에 내장된 전용 ASIC은 암호화 트래픽을 회선 속도로 처리하여 지연 없이 실시간 위협 완화를 가능하게 합니다. 포티넷의 SP5 ASIC 플랫폼은 3.2Tbps의 처리량과 서브마이크로초 단위의 검사 지연을 실현하여 실리콘 수준에서 보안 성능의 획기적인 향상을 보여줍니다. 이러한 칩에 통합된 머신러닝 추론 기능은 서명 기반 엔진에서 감지할 수 없는 제로 데이 공격의 행동 감지를 지원합니다. NIST의 사이버 보안 프레임워크 2.0은 중요 인프라 보호를 위한 하드웨어 가속 제어를 명시적으로 언급합니다.
연방 및 중요 인프라 네트워크에 대한 정부의 제로 트러스트 의무화
대통령령 14028호는 98억 달러의 현대화 자금을 배경으로 2024 회계 연도까지 미국 연방 기관이 제로 트러스트 아키텍처를 채택할 것을 의무화하고 있습니다. 이 지침은 지속적인 검증, 마이크로세그먼테이션 및 암호화 트래픽 분석이 가능한 고처리량 어플라이언스의 대량 조달을 추진하고 있습니다. 방위계약 분야에서도 병행하여 의무화가 진행되고 CMMC 2.0에서는 22만사공급업체에게 레벨 3 준거를 위한 하드웨어 방화벽이 요구됩니다. 유럽의 NIS2 지령도 중요한 서비스에 동등한 보호 조치를 부과하고 대서양을 가로지르는 수요 증가를 가져오고 있습니다. 하드웨어 어플라이언스는 정부 규제 네트워크 내에서 단순한 옵션 경계 방어 장치에서 필수 집행 노드로 변모하고 있습니다.
방화벽 아즈 어 서비스로의 급속한 전환은 On-Premise 하드웨어 수요를 파괴합니다.
클라우드 제공 보안 모델은 마찰이 없는 확장성을 요구하는 조직에서 On-Premise 장비에 대한 수요를 침식합니다. Zscaler사의 2024년도 실적은 연간 35%의 수익 성장을 나타내며 하드웨어 소유를 필요로 하지 않는 서비스형 솔루션에 대한 수요 증가를 뒷받침하고 있습니다. IT 직원이 제한된 중견 기업은 관리형 방화벽에 기울이는 반면 성능 및 데이터 주권 요구 사항 때문에 많은 기업은 여전히 On-Premise 하드웨어에 의존하고 있습니다. 그러므로 하드웨어 방화벽 시장은 양극화된 미래를 맞이하고 서비스 모델이 저-중가격대 수요를 흡수하는 한편, 고성능 요구는 어플라이언스 중심으로 남아있을 것입니다.
부문 분석
2025년 시점에서 기업의 암호화 트래픽 검사를 위한 ASIC 기반 처리량 우선순위로 디바이스/시스템 하드웨어가 하드웨어 방화벽 시장의 63.12%를 차지했습니다. 그러나 서비스는 12.72%의 연평균 복합 성장률(CAGR)로 급성장하고 있으며 조직이 설정, 모니터링, 사고 대응을 벤더 운영 센터에 아웃소싱하고 있기 때문입니다. 서비스 분야의 하드웨어 방화벽 시장 규모는 성과 기반 계약이 자본 지출을 대체함으로써 2031년까지 두배로 될 전망입니다. 대기업은 섀시 기반 장비를 계속 업데이트하지만 중소기업은 인력 부족을 피할 수 있는 공급업체 관리 솔루션을 점점 더 선택하고 있습니다.
제로 트러스트 아키텍처를 채택한 기업은 하드웨어 어플라이언스를 적용 노드로 도입하여 관리형 감지 및 대응 구독을 오버레이합니다. 포티넷은 지원 서비스 수익을 전년 대비 23% 증가시켜 관리형 서비스의 꾸준한 보급을 보여줍니다. AI 가속 어플라이언스 주변의 통합 복잡성은 전문 서비스에 대한 수요를 더욱 높여줍니다. 5G 마이크로사이트가 널리 사용되고 있는 동안, 설치 및 수명 주기 계약은 서비스 제공업체에게 중요한 수익원이 될 것입니다.
2025년 시점에서 하드웨어 방화벽 시장의 68.12%를 대기업이 차지하고 있어 은행, 통신사업자, 하이퍼스케일 클라우드 프로바이더에 있어서의 세계의 갱신 사이클을 반영하고 있습니다. 중소기업은 절대적인 지출액이야말로 작은 것, 12.94%의 연평균 복합 성장률(CAGR)로 그 차이를 해마다 줄이고 있습니다. 중소기업용 하드웨어 방화벽 시장 규모는 관리 부담을 줄이는 클라우드 관리 콘솔과 초기 비용을 구독 지출로 전환하는 공급업체 금융의 혜택을 받고 있습니다.
정부 보조금과 사이버 보험 의무화로 인해 중소기업은 컴플라이언스 체제로의 전환을 더욱 촉진하고 있습니다. 영국 사이버 보안 침해 조사(2024년)에 따르면 중소기업의 75%가 적어도 하나의 방화벽을 도입하고 있으며, 조기 도입 기업을 넘어 보급이 진행되고 있습니다. 공급업체는 제한된 내부 전문 지식을 지원하므로 간소화된 정책 템플릿과 자동 업데이트 기능을 번들로 제공하고 채널 파트너는 턴키 보호를 제공하기 위해 방화벽과 광대역 회선을 패키징합니다.
지역별 분석
북미는 2025년 하드웨어 방화벽 시장 수익의 38.20%를 차지했습니다. 이것은 연방 정부의 사이버 보안 지출 650억 달러와 집중하는 기술 분야 수요에 의해 지원됩니다. 미국의 중요한 인프라 사업자는 CISA의 성과 목표에 부합하기 위해 갱신 주기를 가속화하고 있으며 캐나다는 디지털 헌장을 통한 공공 부문 투자를 확대하고 있습니다. 멕시코 공장에서는 USMCA의 국경을 넘어 하드웨어 유통의 원활화에 따라 방화벽을 인더스트리 4.0 라인에 통합하고 있습니다.
아시아태평양은 2031년까지 12.44%라는 가장 빠른 지역 CAGR을 기록할 것으로 예상됩니다. 중국은 데이터 보안법을 시행하고 국내외 기업에 인증된 네트워크 장비의 채택을 의무화하고 있습니다. 인도는 2025년까지 1조 달러 규모의 디지털 경제를 목표로 내세워 안전한 광대역과 데이터센터 정비를 위한 인센티브를 투입하고 있습니다. 일본의 Society 5.0은 5G와 엣지 컴퓨팅을 추진하고, 연결된 공장이나 스마트 시티망 전체에 마이크로 방화벽 도입을 필요로 합니다. 한국의 K-Digital New Deal은 클라우드보다 On-Premise 보호를 선호하는 사이버 물리적 인프라에 자금을 제공합니다.
유럽에서는 데이터 주권과 하드웨어에 의한 강제를 중시하는 GDPR(EU 개인정보보호규정) 및 NIS2 규정 준수 요건으로 꾸준히 성장하고 있습니다. 독일 인더스트리 4.0과 프랑스 클라우드 주권 프로그램은 현지 검사 포인트에 대한 기업 지출을 촉진하고 있습니다. 영국의 국가 사이버 전략은 브레그지트 이후에도 계속되어 국내 보안 벤더가 정부 계약을 획득하는 기반을 마련하고 있습니다. 중동 및 아프리카은 늦어지면서 사우디아라비아의 '비전 2030'과 UAE의 디지털 국가 로드맵이 통신사업자 수준의 보호를 우선하는 가속화를 하고 있습니다. 아프리카의 핀텍 보급은 패킷 손실이 수익 손실에 직결되는 모바일 머니 플랫폼의 구매를 촉진합니다.
기타 혜택 :
- 엑셀 형식 시장 예측(ME) 시트
- 애널리스트에 의한 3개월간의 지원
자주 묻는 질문
목차
제1장 서론
- 조사의 전제조건과 시장의 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 상황
- 시장 개요
- 시장 성장 촉진요인
- 다각적 사이버 공격의 고도화에 수반해, ASIC 가속 기반 패킷 검사 수요 확대
- 연방 정부 및 중요 인프라 네트워크에 대한 정부의 제로 트러스트 보안 의무화
- 분산형 마이크로 방화벽 노드를 필요로 하는 엣지 컴퓨팅과 5G 고밀도화
- 국내 어플라이언스 생산을 촉진하는 리쇼어링 장려책과 관세
- SD-WAN에 의한 MPLS의 대체가 하드웨어 NGFW의 갱신 사이클을 촉진
- AI 코프로세서의 비용 저하에 의해 중견 시장용 테라비트급 어플라이언스 도입
- 시장 성장 억제요인
- Firewall-as-a-Service(FWaaS)로의 급속한 이행이 On-Premise 하드웨어 수요 잠식
- 네트워크 처리용 반도체(NPU 등) 공급망 변동성
- 개인정보 보호 강화로 인한 암호화 트래픽 검사 한계
- 높은 처리량 기기의 에너지 비용 상승
- 업계 밸류체인 분석
- 규제 상황
- 기술의 전망
- Porter's Five Forces 분석
- 공급기업의 협상력
- 구매자의 협상력
- 신규 참가업체의 위협
- 대체품의 위협
- 경쟁 기업간 경쟁 관계
제5장 시장 규모와 성장 예측
- 구성요소별
- 기기 및 시스템
- 서비스(설치, 서포트, 관리)
- 조직 규모별
- 중소기업(SME)
- 대기업
- 최종 사용자 업계별
- BFSI
- 헬스케어
- 제조업
- 정부 및 방위
- IT 및 통신
- 소매업 및 전자상거래
- 교육
- 방화벽유형별
- 패킷 필터링 방화벽
- 회로 레벨 게이트웨이
- 애플리케이션 수준 / 프록시 방화벽
- 통합 위협 관리(UTM)
- 차세대 방화벽(NGFW)
- AI 가속 및 테라비트급 방화벽
- 지역별
- 북미
- 미국
- 캐나다
- 멕시코
- 남미
- 브라질
- 아르헨티나
- 기타 남미
- 유럽
- 영국
- 독일
- 프랑스
- 이탈리아
- 스페인
- 네덜란드
- 기타 유럽
- 아시아태평양
- 중국
- 일본
- 한국
- 인도
- ASEAN
- 기타 아시아태평양
- 중동 및 아프리카
- 중동
- 사우디아라비아
- 아랍에미리트(UAE)
- 튀르키예
- 기타 중동
- 아프리카
- 남아프리카
- 나이지리아
- 케냐
- 기타 아프리카
- 중동
- 북미
제6장 경쟁 구도
- 시장 집중도
- 전략적 동향
- 시장 점유율 분석
- 기업 프로파일
- Fortinet Inc.
- Palo Alto Networks Inc.
- Cisco Systems Inc.
- Check Point Software Technologies Ltd.
- Juniper Networks Inc.
- Huawei Technologies Co. Ltd.
- Barracuda Networks Inc.
- SonicWall Inc.
- WatchGuard Technologies Inc.
- Sophos Ltd.
- F5 Inc.
- Forcepoint LLC
- Hillstone Networks Co. Ltd.
- TopSec Technology Group Inc.
- AhnLab Inc.
- Ubiquiti Inc.
- Netgate(Electric Sheep Fencing LLC)
- CUJO LLC
- Bitdefender SRL
- Zscaler Inc.
- Array Networks Inc.
- Sangfor Technologies Inc.
- Stormshield(Airbus CyberSecurity)
제7장 시장 기회와 장래의 전망
SHW 26.01.28The hardware firewall market was valued at USD 22.87 billion in 2025 and estimated to grow from USD 25.28 billion in 2026 to reach USD 41.62 billion by 2031, at a CAGR of 10.52% during the forecast period (2026-2031).
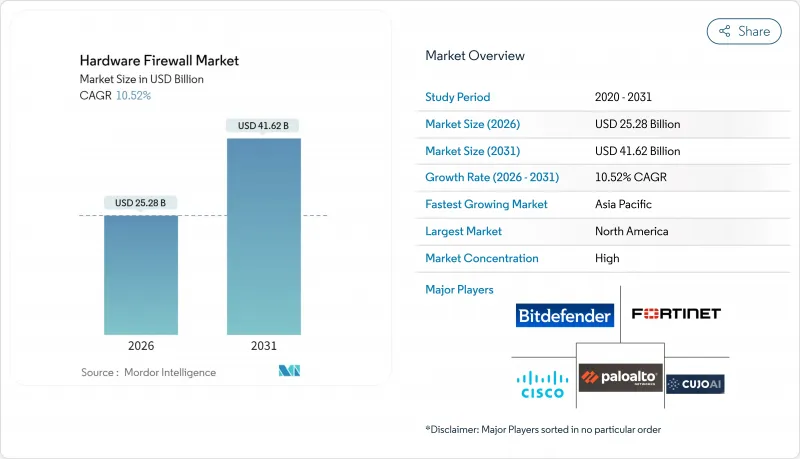
Accelerated demand arises from zero-trust mandates in federal and critical-infrastructure networks, edge-computing adoption, 5G densification, and the growing volume of encrypted traffic that now exceeds 90% of total data flows. Device/System hardware continues to dominate revenues, yet managed services expand faster as enterprises substitute capital purchases with outcome-based contracts. Large enterprises drive refresh cycles for terabit-class appliances, while SMEs fuel incremental growth by adopting simplified unified-threat platforms. Regionally, North America retains the lead, but Asia-Pacific registers the quickest expansion as China, India, and ASEAN members align regulatory frameworks with global cybersecurity norms.
Global Hardware Firewall Market Trends and Insights
Increasing Sophistication of Multi-Vector Cyber-Attacks Necessitating ASIC-Accelerated Inspection
Threat actors now combine ransomware, supply-chain exploits, and state-sponsored operations, overwhelming CPU-centric inspection engines. CISA documented 1,132 known exploited vulnerabilities in 2024, a 23% rise over 2023. Dedicated ASICs embedded in hardware appliances process encrypted traffic at line rate, enabling real-time threat mitigation without introducing latency. Fortinet's SP5 ASIC platform reaches 3.2 Tbps throughput with sub-microsecond inspection delays, exemplifying the leap in silicon-level security performance. Machine-learning inference integrated inside these chips supports behavioral detection of zero-day attacks that signature-based engines miss. NIST's Cybersecurity Framework 2.0 explicitly references hardware-accelerated controls for critical-infrastructure protection.
Government Zero-Trust Mandates for Federal and Critical-Infrastructure Networks
Executive Order 14028 obliges U.S. federal agencies to adopt zero-trust architectures by fiscal 2024, backed by USD 9.8 billion in modernization funding. The directive drives bulk procurement of high-throughput appliances capable of continuous verification, micro-segmentation, and encrypted-traffic analytics. Parallel mandates arise in defense contracting, where CMMC 2.0 requires hardware firewalls for Level 3 compliance across 220,000 suppliers. Europe's NIS2 Directive imposes comparable safeguards on essential services, broadening demand across the Atlantic. Hardware appliances have shifted from optional perimeter guards to indispensable enforcement nodes within government-regulated networks.
Rapid Shift to Firewall-as-a-Service Cannibalizing On-Premises Hardware Demand
Cloud-delivered security models erode demand for on-premise boxes among organizations seeking frictionless scalability. Zscaler's 2024 results showed 35% annual revenue growth, underscoring appetite for service-based offerings that eliminate hardware ownership. Mid-market firms with lean IT staff gravitate toward managed firewalls, although performance and data-sovereignty requirements still anchor many enterprises to on-prem hardware. The hardware firewall market therefore faces a bifurcated future where service models absorb low-to-mid range demand while high-performance needs remain appliance-centric.
Other drivers and restraints analyzed in the detailed report include:
- Edge-Computing and 5G Densification Requiring Distributed Micro-Firewall Nodes
- SD-WAN Replacement of MPLS Driving Hardware NGFW Refresh Cycles
- Supply-Chain Volatility for Network-Processing Chips
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Device/System hardware commanded 63.12% of the hardware firewall market in 2025 as enterprises prioritized ASIC-based throughput for encrypted-traffic inspection. Services, however, race ahead at a 12.72% CAGR as organizations outsource configuration, monitoring, and incident response to vendor-run centers. The hardware firewall market size for Services is on track to double by 2031 as outcome-based contracts displace capital expenditures. Large enterprises continue to refresh chassis-based boxes, but SMEs increasingly prefer vendor-hosted management that sidesteps staffing shortages.
Enterprises embracing zero-trust architectures deploy hardware appliances as enforcement nodes, then overlay managed detection and response subscriptions. Fortinet grew support-services revenue 23% year over year, signaling steady managed-services uptake. Integration complexity around AI-accelerated appliances further elevates demand for professional services. As 5G micro-sites proliferate, installation and lifecycle contracts will remain critical revenue anchors for service providers.
Large enterprises held 68.12% of the hardware firewall market share in 2025, reflecting global refresh cycles among banks, telcos, and hyperscale cloud providers. SMEs, though smaller in absolute spend, post a 12.94% CAGR that narrows the gap each year. The hardware firewall market size attributable to SMEs benefits from cloud-managed consoles that reduce administrative overhead and from vendor financing that converts upfront costs into subscription outlays.
Government grants and cyber-insurance mandates further pull SMEs into compliance regimes. The U.K. Cyber Security Breaches Survey 2024 found that 75% of SMEs now deploy at least one firewall, demonstrating penetration beyond early adopters. Vendors bundle simplified policy templates and automated updates to meet limited in-house expertise, while channel partners package firewalls with broadband circuits for turnkey protection.
The Hardware Firewall Market Report is Segmented by Component (Device/System and Services), Organization Size (SMEs and Large Enterprises), End-User Industry (BFSI, Healthcare, Manufacturing, Government and Defense, and More), Firewall Type (Packet-Filtering, Circuit-Level Gateways, Application-Level/Proxy, UTM, NGFW, and AI-Accelerated), and Geography. The Market Forecasts are Provided in Terms of Value (USD).
Geography Analysis
North America held 38.20% of hardware firewall market revenue in 2025, buoyed by USD 65 billion in federal cybersecurity spending and concentrated technology-sector demand. U.S. critical-infrastructure operators accelerate refresh cycles to align with CISA performance goals, while Canada expands public-sector investment through its Digital Charter. Mexican factories integrate firewalls into Industry 4.0 lines as the USMCA eases cross-border hardware flows.
Asia-Pacific records the fastest regional CAGR at 12.44% through 2031. China enforces its Data Security Law, obliging foreign and domestic firms to adopt certified network gear. India targets a USD 1 trillion digital economy by 2025, channeling incentives toward secure broadband and data-center build-outs. Japan's Society 5.0 pushes 5G and edge-computing, necessitating micro-firewall deployments across connected factories and smart-city grids. South Korea's K-Digital New Deal funds cyber-physical infrastructure that prefers on-premise protection over cloud.
Europe grows steadily on GDPR and NIS2 compliance requirements that emphasize data-sovereignty and hardware enforcement. Germany's Industry 4.0 and France's cloud-sovereignty programs propel enterprise spending on local inspection points. The U.K. National Cyber Strategy extends after Brexit, positioning domestic security vendors for government contracts. Middle East and Africa trails but accelerates as Saudi Arabia's Vision 2030 and the UAE's digital-nation roadmaps prioritize telecom-grade protection. African fintech adoption fuels purchases for mobile money platforms where packet loss equates to revenue loss.
- Fortinet Inc.
- Palo Alto Networks Inc.
- Cisco Systems Inc.
- Check Point Software Technologies Ltd.
- Juniper Networks Inc.
- Huawei Technologies Co. Ltd.
- Barracuda Networks Inc.
- SonicWall Inc.
- WatchGuard Technologies Inc.
- Sophos Ltd.
- F5 Inc.
- Forcepoint LLC
- Hillstone Networks Co. Ltd.
- TopSec Technology Group Inc.
- AhnLab Inc.
- Ubiquiti Inc.
- Netgate (Electric Sheep Fencing LLC)
- CUJO LLC
- Bitdefender SRL
- Zscaler Inc.
- Array Networks Inc.
- Sangfor Technologies Inc.
- Stormshield (Airbus CyberSecurity)
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Increasing sophistication of multi-vector cyber-attacks necessitating ASIC-accelerated inspection
- 4.2.2 Government zero-trust mandates for federal and critical-infrastructure networks
- 4.2.3 Edge-computing and 5G densification requiring distributed micro-firewall nodes
- 4.2.4 Reshoring incentives and tariffs spurring domestic appliance production
- 4.2.5 SD-WAN replacement of MPLS driving hardware NGFW refresh cycles
- 4.2.6 Falling AI-coprocessor costs enabling mid-market terabit-class appliances
- 4.3 Market Restraints
- 4.3.1 Rapid shift to Firewall-as-a-Service cannibalising on-prem hardware demand
- 4.3.2 Supply-chain volatility for network-processing chips
- 4.3.3 Privacy-driven limits on encrypted-traffic inspection
- 4.3.4 Rising energy costs of high-throughput appliances
- 4.4 Industry Value Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Porter's Five Forces Analysis
- 4.7.1 Bargaining Power of Suppliers
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Threat of New Entrants
- 4.7.4 Threat of Substitute Products
- 4.7.5 Intensity of Competitive Rivalry
5 MARKET SIZE AND GROWTH FORECASTS (VALUE)
- 5.1 By Component
- 5.1.1 Device / System
- 5.1.2 Services (Installation, Support, Managed)
- 5.2 By Organization Size
- 5.2.1 Small and Medium-sized Enterprises (SMEs)
- 5.2.2 Large Enterprises
- 5.3 By End-user Industry
- 5.3.1 BFSI
- 5.3.2 Healthcare
- 5.3.3 Manufacturing
- 5.3.4 Government and Defense
- 5.3.5 IT and Telecom
- 5.3.6 Retail and E-commerce
- 5.3.7 Education
- 5.4 By Firewall Type
- 5.4.1 Packet-Filtering Firewalls
- 5.4.2 Circuit-Level Gateways
- 5.4.3 Application-Level / Proxy Firewalls
- 5.4.4 Unified Threat Management (UTM)
- 5.4.5 Next-Generation Firewalls (NGFW)
- 5.4.6 AI-Accelerated / Terabit-class Firewalls
- 5.5 By Geography
- 5.5.1 North America
- 5.5.1.1 United States
- 5.5.1.2 Canada
- 5.5.1.3 Mexico
- 5.5.2 South America
- 5.5.2.1 Brazil
- 5.5.2.2 Argentina
- 5.5.2.3 Rest of South America
- 5.5.3 Europe
- 5.5.3.1 United Kingdom
- 5.5.3.2 Germany
- 5.5.3.3 France
- 5.5.3.4 Italy
- 5.5.3.5 Spain
- 5.5.3.6 Netherlands
- 5.5.3.7 Rest of Europe
- 5.5.4 Asia-Pacific
- 5.5.4.1 China
- 5.5.4.2 Japan
- 5.5.4.3 South Korea
- 5.5.4.4 India
- 5.5.4.5 ASEAN
- 5.5.4.6 Rest of Asia-Pacific
- 5.5.5 Middle East and Africa
- 5.5.5.1 Middle East
- 5.5.5.1.1 Saudi Arabia
- 5.5.5.1.2 United Arab Emirates
- 5.5.5.1.3 Turkey
- 5.5.5.1.4 Rest of Middle East
- 5.5.5.2 Africa
- 5.5.5.2.1 South Africa
- 5.5.5.2.2 Nigeria
- 5.5.5.2.3 Kenya
- 5.5.5.2.4 Rest of Africa
- 5.5.5.1 Middle East
- 5.5.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 Fortinet Inc.
- 6.4.2 Palo Alto Networks Inc.
- 6.4.3 Cisco Systems Inc.
- 6.4.4 Check Point Software Technologies Ltd.
- 6.4.5 Juniper Networks Inc.
- 6.4.6 Huawei Technologies Co. Ltd.
- 6.4.7 Barracuda Networks Inc.
- 6.4.8 SonicWall Inc.
- 6.4.9 WatchGuard Technologies Inc.
- 6.4.10 Sophos Ltd.
- 6.4.11 F5 Inc.
- 6.4.12 Forcepoint LLC
- 6.4.13 Hillstone Networks Co. Ltd.
- 6.4.14 TopSec Technology Group Inc.
- 6.4.15 AhnLab Inc.
- 6.4.16 Ubiquiti Inc.
- 6.4.17 Netgate (Electric Sheep Fencing LLC)
- 6.4.18 CUJO LLC
- 6.4.19 Bitdefender SRL
- 6.4.20 Zscaler Inc.
- 6.4.21 Array Networks Inc.
- 6.4.22 Sangfor Technologies Inc.
- 6.4.23 Stormshield (Airbus CyberSecurity)
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-need Assessment


















