
|
시장보고서
상품코드
1849930
엔드포인트 보안 : 시장 점유율 분석, 산업 동향, 통계, 성장 예측(2025-2030년)Endpoint Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
엔드포인트 보안 시장 규모는 2025년에 210억 2,000만 달러, 2030년에는 357억 5,000만 달러에 이를 것으로 추정되며, 예측 기간(2025-2030년)의 CAGR은 11.20%를 나타낼 전망입니다.

왕성한 수요의 배경으로는 원격 워크와 하이브리드 워크로의 꾸준한 변화, BYOD(Bring-your-own-device) 정책의 확대, 랜섬웨어 아즈아 서비스의 툴킷의 고도화가 있습니다. 기업은 또한 정보기술 네트워크와 운영기술 네트워크의 경계를 모호하게 하는 IoT(Internet of Things)의 발자취 확대에 직면하고 있으며, 중요한 산업 자산이 지금까지 오피스 기기를 대상으로 한 것과 같은 위협에 노출되어 있습니다. 따라서 클라우드 전달 제어, 제로 트러스트 액세스 정책 및 AI 중심의 행동 분석은 최신 엔드포인트 보호 전략의 기본 구성 요소가 되고 있습니다. 플랫폼 제공업체는 칩 레벨 보안 기능을 통합하고 엔드포인트 보호 플랫폼(EPP) 및 엔드포인트 감지 및 대응(EDR) 기능을 보안 액세스 서비스 에지(SASE) 제품에 번들하여 분산된 사용자에 대한 정책 적용을 단순화함으로써 대응합니다.
세계의 엔드포인트 보안 시장 동향 및 인사이트
BYOD와 모바일 워크포스 급증
BYOD 정책은 전통적인 방화벽 밖에 있는 약 47억 대의 모바일 엔드포인트를 공개하여 기업 데이터와 개인용 앱을 분리하는 모바일 기기 관리 도구의 도입을 빠르게 진행하고 있습니다. 아이덴티티 침해는 현재 공격의 70%에서 볼 수 있기 때문에 기업은 네트워크 액세스를 허용하기 전에 장치의 자세를 확인하는 제로 트러스트 프레임워크에 기울고 있습니다. 경영진은 사이버 보안을 이사회 수준의 우선순위로 파악하고 있으며, 91%가 컴플라이언스가 아닌 전략적 자산이라고 응답합니다. 최신 엔드포인트 제품군에 내장된 AI 기능은 실시간 행동 분석을 수행하고 다양한 장치 생태계 전반에 걸쳐 위험한 행동을 신고합니다.
랜섬웨어 아즈 어 서비스 고도화
서비스 기반 랜섬웨어는 진입 장벽을 낮추고 2024년 초에 감염이 50% 급증하는 계기가 되었습니다. 헬스케어 침해는 현재 평균 1,010만 달러에 이르기 때문에 병원은 엔드포인트와 네트워크의 텔레메트리를 상관시키는 확장 검지·대응 플랫폼의 도입을 강요하고 있습니다. 이중, 삼중의 공갈 수법은 백업도 표적으로 하기 때문에 기업은 데이터 복구 계획을 재조정할 필요가 있습니다. 애널리스트는 랜섬웨어 피해액이 2031년까지 연간 2,650억 달러 이상에 달할 것으로 예상하고 있으며, 프로액티브 엔드포인트 수비에 더 많은 비용이 듭니다.
SOC 및 사고 대응 팀의 기술 부족
세계적으로 300만 명의 사이버 전문가가 부족하여 최고 정보 보안 책임자의 약 절반이 적용 범위의 격차에 불안을 겪고 있습니다. 이에 따라 MDR(Managed Detection and Response)의 도입이 가속화되고 있으며 2025년까지 절반의 조직이 24시간 365일 모니터링을 아웃소싱할 것으로 예측됩니다. 경고를 트리거하고 캡슐화 작업을 스크립팅하는 자동화 및 AI 도구는 인적 자원 파이프라인이 개선될 때까지 실용적인 일시적인 것으로 간주됩니다.
부문 분석
엔드포인트 검지·대응 제품은 CAGR 15.8%로 확대되어 레거시 바이러스 대책 툴을 가볍게 능가하고 있습니다. 조직은 제로데이 악용에 스포트라이트를 적용하는 행동 분석을 선호하는 반면, 방화벽/UTM 어플라이언스는 기존 네트워크 장비와의 깊은 통합으로 20.02%의 매출 점유율을 유지하고 있습니다. 또한 사내에 보안 운영 센터를 구축하는 것보다 전문 지식을 대여하는 매니지드 디테크션 & 리스폰스 구독도 대두하고 있습니다.
GDPR(EU 개인정보보호규정) 및 NIS2와 같은 규칙이 데이터 보호 관리의 입증을 요구하기 때문에 규제 모니터링은 암호화 및 데이터 유출 방지 모듈에 활력을 주고 있습니다. 패치 관리 유틸리티는 보안 업데이트가 평균 97일에 제공되며 공격 대상이 노출되기 때문에 지출을 모으고 있습니다. 악성 소프트웨어를 차단하는 용도 제어 도구는 기업 네트워크의 개인 장치의 섀도우 IT 위험을 억제하는 데 도움이 됩니다.
클라우드 플랫폼은 2024년 엔드포인트 보안 시장 규모의 58.04%를 차지했으며, 2030년까지 매년 15.2%의 성장이 예상됩니다. 중앙 집중화된 정책 엔진은 전 세계적으로 분산된 기기로의 배포를 가속화하고 AI 모델에 대량의 데이터를 실시간으로 제공합니다. 하이브리드 아키텍처는 데이터 주권 규칙 및 전문 운영 기술 제약에 직면하는 기업들에게 인기가 있습니다.
현지 처리가 의무화되고 있는 방어 및 중요 인프라 분야에서는 On-Premise의 도입이 뿌리깊습니다. 이러한 경우에도 많은 팀이 SASE 오버레이를 채택하여 Software-Defined Networking과 클라우드 제공 보안을 결합하여 관리를 단순화합니다. 클라우드에 통합된 EDR 애널리틱스는 체류 시간을 단축하고 평균 응답 시간 통계를 향상시킵니다.
엔드포인트 보안 시장은 솔루션 유형(안티바이러스/안티멀웨어, 방화벽/UTM 등), 배포 형태(On-Premise, 클라우드, 하이브리드), 조직 규모(대기업, 중소기업), 최종 사용자 업계(은행, 금융서비스 및 보험(BFSI), 정부 기관, 방위, 건강/생명 과학 등), 지역별로 분류됩니다. 시장 예측은 금액(달러)으로 제공됩니다.
지역 분석
북미는 2024년 33.5%의 매출 점유율을 유지했습니다. 풍부한 보안 예산, 고급 위협 환경 및 조기 AI 도입이 지속적인 업그레이드에 박차를 가하고 있습니다. 정부의 클라우드 보안 프로그램과 공급업체의 치밀한 네트워크가 혁신의 선순환을 창출하고 있습니다.
유럽의 기세는 2024년 10월 NIS2 지침의 완전 시행에 연결되었습니다. 이 지침에 따라 16만 개 이상의 조직이 인증된 엔드포인트 컨트롤을 도입하지 않으면 최대 1,000만 유로의 제재금을 부과하게 됩니다. 이 규제를 통해 중요한 인프라, 제조업, 디지털 서비스 제공업체 수요는 높은 수준으로 추세되고 있습니다.
아시아태평양은 CAGR 12.4%로 가장 빠르게 성장하는 지역입니다. 이 지역의 각국은 사이버 내성의 프레임워크에 투자에 힘을 쏟고 있으며, 통신사업자나 금융기관을 노린 저명한 공격에 의해 경영진의 초점이 첨예화되고 있습니다. 중국의 보안팀은 API에 대한 노출을 가장 우려하고 있으며 27%가 악성코드보다 우선합니다. 일본, 한국, 호주 및 ASEAN 국가에서는 정부의 자금 지원과 현지 공급업체의 생태계를 통해 도입이 가속화되고 있습니다.
중동 및 아프리카에서는 사이버 보험료 상승과 프라이버시 법의 강화가 은행과 에너지 사업자에게 엔드포인트 관리의 업그레이드를 촉구하고 있습니다. 라틴아메리카에서는 소매업과 디지털 뱅킹 기업을 중심으로 기존의 On-Premise 환경을 뛰어넘는 클라우드의 도입이 진행되고 있습니다.
기타 혜택 :
- 엑셀 형식 시장 예측(ME) 시트
- 3개월간의 애널리스트 지원
목차
제1장 서론
- 조사 전제조건과 시장 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 상황
- 시장 개요
- 시장 성장 촉진요인
- BYOD와 모바일 근로자의 급증
- ransomware-as-a-service의 고도화
- OT 네트워크 전체에 걸친 IoT 엔드포인트의 급증
- 엣지에서의 SASE 번들 EPP/EDR의 채용 확대
- OEM이 통합한 칩 레벨의 보안 IP
- 인정 EDR에 대한 사이버 보험료 할인
- 시장 성장 억제요인
- SOC 및 사고 대응 팀의 스킬 부족
- 중소기업의 예산 제약
- 지속적인 엔드포인트 텔레메트리에 대한 프라이버시 반발 증가
- 타사 보안 에이전트 공급망 위험
- 업계 밸류체인 분석
- 규제 상황
- 기술의 전망
- 업계의 매력 - Porter's Five Forces 분석
- 공급기업의 협상력
- 구매자의 협상력
- 신규 참가업체의 위협
- 대체품의 위협
- 경쟁 기업 간 경쟁 관계
- 거시 경제 요인이 시장에 미치는 영향
제5장 시장 규모와 성장 예측(금액관)
- 솔루션 유형별
- 바이러스 백신/악성코드 방지
- 방화벽/통합 위협 관리(UTM)
- 엔드포인트 탐지 및 대응(EDR)
- 관리형 탐지 및 대응(MDR)
- 암호화 및 데이터 유출 방지
- 패치 및 구성 관리
- 애플리케이션 및 기기 제어
- 기타
- 배포 모드별
- On-Premise
- 클라우드
- 하이브리드
- 조직 규모별
- 대기업
- 중소기업
- 최종 사용자 업계별
- BFSI
- 정부 및 방위
- 헬스케어 및 생명과학
- 제조
- 에너지 및 유틸리티
- 소매업 및 전자상거래
- IT 및 통신
- 교육
- 기타 최종 사용자 산업
- 지역별
- 북미
- 미국
- 캐나다
- 멕시코
- 남미
- 브라질
- 아르헨티나
- 칠레
- 기타 남미
- 유럽
- 독일
- 영국
- 프랑스
- 이탈리아
- 스페인
- 러시아
- 기타 유럽
- 아시아태평양
- 중국
- 인도
- 일본
- 한국
- 호주
- 싱가포르
- 말레이시아
- 기타 아시아태평양
- 중동 및 아프리카
- 중동
- 아랍에미리트(UAE)
- 사우디아라비아
- 튀르키예
- 기타 중동
- 아프리카
- 남아프리카
- 나이지리아
- 기타 아프리카
- 북미
제6장 경쟁 구도
- 시장 집중도
- 전략적 동향
- 시장 점유율 분석
- 기업 프로파일
- Trend Micro Inc.
- CrowdStrike Holdings Inc.
- SentinelOne Inc.
- Sophos Ltd.
- Bitdefender LLC
- ESET Spol. s ro
- Kaspersky Lab JSC
- Trellix(Musarubra US LLC)
- OpenText(Cybersecurity & Carbonite Unit)
- WatchGuard Technologies Inc.
- Fortinet Inc.
- Cisco Systems Inc.
- Palo Alto Networks Inc.
- Broadcom Inc.(Symantec Endpoint)
- Microsoft Corporation(Defender for Endpoint)
- Deep Instinct Ltd
- Cybereason Inc.
- BlackBerry Ltd(Cylance)
- Malwarebytes Inc.
- AhnLab Inc.
- F-Secure Corp.
- Elastic NV(Security)
- ReaQta BV(IBM)
- Comodo Security Solutions Inc.
- Seqrite(Quick Heal Technologies)
제7장 시장 기회와 미래 동향
- 백스페이스 및 미충족 수요(Unmet Needs) 평가
The Endpoint Security Market size is estimated at USD 21.02 billion in 2025, and is expected to reach USD 35.75 billion by 2030, at a CAGR of 11.20% during the forecast period (2025-2030).
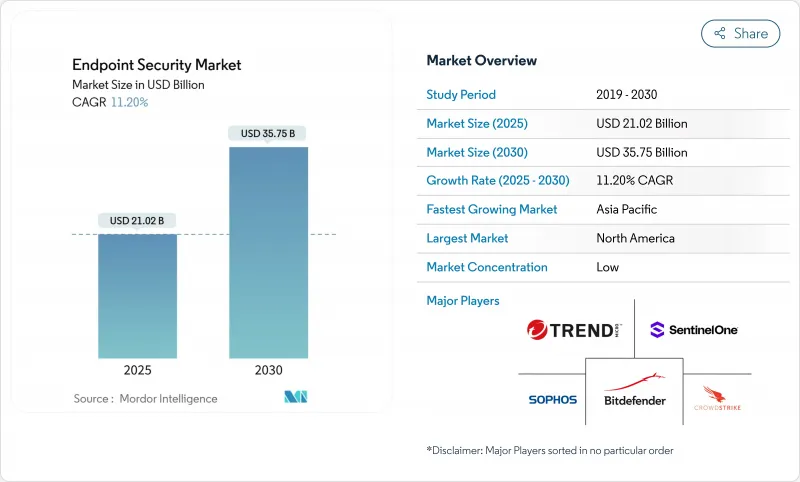
Strong demand stems from the steady shift toward remote and hybrid work, the expansion of bring-your-own-device (BYOD) policies, and the growing sophistication of ransomware-as-a-service toolkits. Enterprises also face an expanding Internet-of-Things (IoT) footprint that blurs the line between information-technology and operational-technology networks, exposing critical industrial assets to the same threats historically aimed at office devices. Cloud-delivered controls, zero-trust access policies, and AI-driven behavioural analytics are therefore becoming default components of modern endpoint protection strategies. Platform providers are responding by embedding chip-level security features and bundling endpoint protection platform (EPP) and endpoint detection and response (EDR) capabilities into secure-access-service-edge (SASE) offerings to simplify policy enforcement across distributed users.
Global Endpoint Security Market Trends and Insights
Surge in BYOD and Mobile Workforce
BYOD policies have exposed roughly 4.7 billion mobile endpoints that sit outside traditional firewalls, prompting rapid deployment of mobile-device-management tools that partition corporate data from personal apps. Identity compromise now appears in 70% of attacks, so firms lean on zero-trust frameworks that verify device posture before allowing network access. Executives increasingly view cybersecurity as a board-level priority, with 91% describing it as a strategic asset rather than a compliance exercise. AI features embedded in modern endpoint suites perform real-time behavioural analysis to flag risky actions across a diverse device ecosystem.
Escalating Sophistication of Ransomware-as-a-Service
Service-based ransomware lowered the barrier to entry, triggering a 50% spike in infections during early 2024. Healthcare breaches now cost USD 10.1 million on average, forcing hospitals to adopt extended-detection-and-response platforms that correlate endpoint and network telemetry. Double- and triple-extortion tactics also target backups, compelling enterprises to redesign data-recovery plans. Analysts expect ransomware damage to surpass USD 265 billion annually by 2031, funnelling more spend into proactive endpoint defences.
Skill Shortage in SOC and Incident-Response Teams
The global deficit of 3 million cyber professionals leaves roughly half of chief information security officers anxious about coverage gaps. Managed-detection-and-response (MDR) uptake is therefore accelerating, with half of organizations expected to outsource 24/7 monitoring by 2025. Automation and AI tools that triage alerts and script containment actions are seen as practical stopgaps until the workforce pipeline improves.
Other drivers and restraints analyzed in the detailed report include:
- Proliferation of IoT Endpoints Across OT Networks
- Wider Adoption of SASE Bundling EPP/EDR at Edge
- Budget Constraints Among SMBs
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Endpoint detection and response products are expanding at 15.8% CAGR, easily eclipsing legacy antivirus tools. Organizations favour behaviour analytics that spotlight zero-day exploits, while firewall/UTM appliances retain 20.02% revenue share thanks to deep integration with existing network gear. Managed-detection-and-response subscriptions are also gaining ground as firms lease expertise rather than build internal security operations centres.
Regulatory scrutiny is breathing life into encryption and data-loss-prevention modules as rules such as GDPR and NIS2 demand demonstrable data-protection controls. Patch-management utilities attract spend because security updates still average a 97-day rollout window, leaving attack surfaces exposed. Application-control tools that block unauthorized software help limit shadow-IT risks for personal devices on corporate networks.
Cloud platforms already command 58.04% of the endpoint security market size in 2024 and will compound 15.2% annually to 2030. Centralized policy engines accelerate rollout across globally distributed devices and feed AI models with large data volumes in real time. Hybrid architectures remain popular for firms facing data-sovereignty rules or specialist operational-technology constraints.
On-premises deployments persist in defence and critical-infrastructure verticals where local processing is mandated. Even there, many teams adopt SASE overlays that couple software-defined networking with cloud-delivered security to simplify administration. Integrated EDR analytics in the cloud reduce dwell time and enhance mean-time-to-respond statistics.
Endpoint Security Market is Segmented by Solution Type (Antivirus/Anti-malware, Firewall/UTM, and More), Deployment Mode (On-Premises, Cloud, and Hybrid), Organization Size (Large Enterprises and Small and Medium-Sized Enterprises), End-User Industry (BFSI, Government and Defense, Healthcare and Life Sciences, and More), and Geography. The Market Forecasts are Provided in Terms of Value (USD).
Geography Analysis
North America maintained 33.5% revenue share in 2024. Deep security budgets, an advanced threat landscape, and early AI adoption fuel ongoing upgrades. Government cloud-security programs and a dense network of vendors create a virtuous innovation cycle.
Europe's momentum is tied to the full enforcement of the NIS2 directive in October 2024, which compels more than 160,000 organizations to deploy certified endpoint controls or face fines up to EUR 10 million. The regulation keeps demand high across critical infrastructure, manufacturing, and digital services providers.
Asia-Pacific is the fastest-growing territory at 12.4% CAGR. Nations across the region pour investment into cyber-resilience frameworks, and high-profile attacks on telecoms and financial institutions have sharpened executive focus. Chinese security teams rank API exposure as their top concern, with 27% putting it ahead of malware. Government funding and local vendor ecosystems accelerate adoption across Japan, South Korea, Australia, and the ASEAN bloc.
The Middle East and Africa notice rising cyber-insurance premiums and tougher privacy laws, nudging banks and energy operators to upgrade endpoint controls. Latin America expands cloud deployments that leapfrog legacy on-premises estates, particularly in retail and digital-banking firms.
- Trend Micro Inc.
- CrowdStrike Holdings Inc.
- SentinelOne Inc.
- Sophos Ltd.
- Bitdefender LLC
- ESET Spol. s r.o.
- Kaspersky Lab JSC
- Trellix (Musarubra US LLC)
- OpenText (Cybersecurity & Carbonite Unit)
- WatchGuard Technologies Inc.
- Fortinet Inc.
- Cisco Systems Inc.
- Palo Alto Networks Inc.
- Broadcom Inc. (Symantec Endpoint)
- Microsoft Corporation (Defender for Endpoint)
- Deep Instinct Ltd
- Cybereason Inc.
- BlackBerry Ltd (Cylance)
- Malwarebytes Inc.
- AhnLab Inc.
- F-Secure Corp.
- Elastic NV (Security)
- ReaQta BV (IBM)
- Comodo Security Solutions Inc.
- Seqrite (Quick Heal Technologies)
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Surge in BYOD and mobile workforce
- 4.2.2 Escalating sophistication of ransomware-as-a-service
- 4.2.3 Proliferation of IoT endpoints across OT networks
- 4.2.4 Wider adoption of SASE bundling EPP/EDR at edge
- 4.2.5 Chip-level security IP integrated by OEMs
- 4.2.6 Cyber-insurance premium discounts for certified EDR
- 4.3 Market Restraints
- 4.3.1 Skill shortage in SOC & incident-response teams
- 4.3.2 Budget constraints among SMBs
- 4.3.3 Rising privacy backlash against continuous endpoint telemetry
- 4.3.4 Supply-chain risk of third-party security agents
- 4.4 Industry Value Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Industry Attractiveness - Porter's Five Forces Analysis
- 4.7.1 Bargaining Power of Suppliers
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Threat of New Entrants
- 4.7.4 Threat of Substitutes
- 4.7.5 Intensity of Competitive Rivalry
- 4.8 Impact of Macroeconomic Factors on the Market
5 MARKET SIZE AND GROWTH FORECASTS (VALUES)
- 5.1 By Solution Type
- 5.1.1 Antivirus / Anti-malware
- 5.1.2 Firewall / UTM
- 5.1.3 Endpoint Detection and Response (EDR)
- 5.1.4 Managed Detection and Response (MDR)
- 5.1.5 Encryption and Data Loss Prevention
- 5.1.6 Patch and Configuration Management
- 5.1.7 Application and Device Control
- 5.1.8 Others
- 5.2 By Deployment Mode
- 5.2.1 On-premises
- 5.2.2 Cloud
- 5.2.3 Hybrid
- 5.3 By Organization Size
- 5.3.1 Large Enterprises
- 5.3.2 Small and Medium-sized Enterprises (SME)
- 5.4 By End-user Industry
- 5.4.1 BFSI
- 5.4.2 Government and Defense
- 5.4.3 Healthcare and Life Sciences
- 5.4.4 Manufacturing
- 5.4.5 Energy and Utilities
- 5.4.6 Retail and e-Commerce
- 5.4.7 IT and Telecom
- 5.4.8 Education
- 5.4.9 Other End-User Industries
- 5.5 By Geography
- 5.5.1 North America
- 5.5.1.1 United States
- 5.5.1.2 Canada
- 5.5.1.3 Mexico
- 5.5.2 South America
- 5.5.2.1 Brazil
- 5.5.2.2 Argentina
- 5.5.2.3 Chile
- 5.5.2.4 Rest of South America
- 5.5.3 Europe
- 5.5.3.1 Germany
- 5.5.3.2 United Kingdom
- 5.5.3.3 France
- 5.5.3.4 Italy
- 5.5.3.5 Spain
- 5.5.3.6 Russia
- 5.5.3.7 Rest of Europe
- 5.5.4 Asia-Pacific
- 5.5.4.1 China
- 5.5.4.2 India
- 5.5.4.3 Japan
- 5.5.4.4 South Korea
- 5.5.4.5 Australia
- 5.5.4.6 Singapore
- 5.5.4.7 Malaysia
- 5.5.4.8 Rest of Asia-Pacific
- 5.5.5 Middle East and Africa
- 5.5.5.1 Middle East
- 5.5.5.1.1 United Arab Emirates
- 5.5.5.1.2 Saudi Arabia
- 5.5.5.1.3 Turkey
- 5.5.5.1.4 Rest of Middle East
- 5.5.5.2 Africa
- 5.5.5.2.1 South Africa
- 5.5.5.2.2 Nigeria
- 5.5.5.2.3 Rest of Africa
- 5.5.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share, Products and Services, Recent Developments)
- 6.4.1 Trend Micro Inc.
- 6.4.2 CrowdStrike Holdings Inc.
- 6.4.3 SentinelOne Inc.
- 6.4.4 Sophos Ltd.
- 6.4.5 Bitdefender LLC
- 6.4.6 ESET Spol. s r.o.
- 6.4.7 Kaspersky Lab JSC
- 6.4.8 Trellix (Musarubra US LLC)
- 6.4.9 OpenText (Cybersecurity & Carbonite Unit)
- 6.4.10 WatchGuard Technologies Inc.
- 6.4.11 Fortinet Inc.
- 6.4.12 Cisco Systems Inc.
- 6.4.13 Palo Alto Networks Inc.
- 6.4.14 Broadcom Inc. (Symantec Endpoint)
- 6.4.15 Microsoft Corporation (Defender for Endpoint)
- 6.4.16 Deep Instinct Ltd
- 6.4.17 Cybereason Inc.
- 6.4.18 BlackBerry Ltd (Cylance)
- 6.4.19 Malwarebytes Inc.
- 6.4.20 AhnLab Inc.
- 6.4.21 F-Secure Corp.
- 6.4.22 Elastic NV (Security)
- 6.4.23 ReaQta BV (IBM)
- 6.4.24 Comodo Security Solutions Inc.
- 6.4.25 Seqrite (Quick Heal Technologies)
7 MARKET OPPORTUNITIES AND FUTURE TRENDS
- 7.1 White-Space and Unmet-Need Assessment



















