
|
시장보고서
상품코드
1851020
보안 정보 및 이벤트 관리(SIEM) 시장 : 점유율 분석, 산업 동향, 통계, 성장 예측(2025-2030년)Security Information And Event Management (SIEM) - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
세계 보안 정보 및 이벤트 관리(SIEM) 시장은 2025년에 107억 8,000만 달러, 2030년에는 191억 3,000만 달러에 이르고, CAGR 12.16%로 성장할 것으로 예측됩니다.

클라우드 워크로드 텔레메트리의 급증, 엄격한 규제의 의무화, 급속한 벤더 통합이 주요 성장 요인입니다. 대기업은 공격 대상이 확대됨에 따라 로그 수집을 계속 확대하고 중소기업은 클라우드 네이티브 소비 모델을 통해 시장에 진입합니다. 북미 수요는 SOX와 PCI DSS의 규칙에 의해 뒷받침되며, 유럽 지출은 NIS2와 DORA에 대응하여 가속화되고 있습니다. 벤더의 로드맵은 현재 AI를 활용한 분석, 통합 데이터 파이프라인, 간소화된 라이선싱을 중심으로 전개되고 있으며, 2024년 Cisco에 의한 Splunk의 획기적인 인수에 이어 리프레시 사이클에 박차를 가하는 테마가 되고 있습니다.
세계 보안 정보 및 이벤트 관리(SIEM) 시장 동향 및 통찰
보안 원격 측정의 급격한 성장
기업은 엔드포인트, 클라우드 서비스 및 운영 기술에서 매일 테라바이트 단위의 로그를 생성합니다. 그 양은 기존의 인제스트 모델에 부담을 주면서 위협을 발견하기 위한 풍부한 컨텍스트를 풀어 놓고 있습니다. CPFL Energia는 비용 관리를 위해 고가의 이벤트를 데이터 레이크로 라우팅하는 최신 SIEM을 통해 50,000대 이상의 스마트 그리드 장치를 모니터링합니다. 클라우드 네이티브의 탄력성은 인시던트 급증 시 버스트 처리를 가능하게 하며, 선택적 유지는 스토리지 요금을 예측 가능한 상태로 유지합니다. 저가의 객체 스토리지와 쿼리 가능한 메타데이터를 통합한 공급업체는 커버 범위와 비용의 균형을 맞추는 고객으로부터 지원을 받고 있습니다.
증가하는 규제 벌칙과 감사
유럽의 NIS2는 중요한 서비스를 제공하는 사업자에게 인시던트 재구축을 위해 이벤트를 기록, 모니터링 및 유지해야 하며 보안 예산을 IT 지출의 9.0%로 밀어 올리고 있습니다. 금융 업계에서 DORA는 실시간 감지 및 보고를 의무화하고 있습니다. 뱅크 레이미는 감사 증거 작성에 특화된 SIEM 업그레이드 후 오감지를 70% 줄였습니다. 의료 제공업체는 HIPAA 위반으로 인한 벌금에 직면하고 있으며, 이 금액은 평균 488만 달러에 달할 전망입니다.
높은 총 소유 비용
전통적인 이벤트별 라이선스는 보안 맹점을 낳기 때문에 구매자는 인제스트에 상한을 설정해야 합니다. 하드웨어 관세로 인해 2024년에는 어플라이언스 비용이 20%나 상승하여 예산이 압박됩니다. 스토리지, 이글레스, 프리미엄 애널리틱스를 위한 숨겨진 클라우드 요금은 처음 도입하는 사용자를 놀라게 합니다. 공급업체는 현재 예측 가능성을 회복하기 위해 파이프라인의 오프로드 계층과 정액제 가격을 추진하고 있습니다.
부문 분석
2024년 SIEM 시장 점유율은 On-Premise형이 55.75%를 차지했습니다. 이 부문은 엄격한 데이터 주권 정책에 얽매이는 업계에서 계속 지지를 받고 있지만, 하드웨어 비용의 상승과 기술 부족의 심각화에 따라 성장이 둔화되고 있습니다. 클라우드 코호트는 CAGR 13.40%로 성장하여 탄력적인 스케일링 및 종량 과금을 통해 고급 애널리틱스에 대한 액세스를 확대합니다. 하이브리드 설계는 브리지 역할을 하며 규제 대상 데이터를 로컬 노드에 배치하면서 원격 측정 데이터를 클라우드의 저비용 객체 스토리지로 스트리밍합니다.
클라우드 채택으로 업그레이드 사이클은 수년간 어플라이언스 업데이트에서 지속적인 기능 제공으로 전환됩니다. Siemens는 위협 인텔리전스 상관을 위해 클라우드에서 이벤트를 풍부하게 하면서 구내에서 OT 파서를 실행하는 하이브리드 패턴을 사용합니다. 라이선스가 데이터 사용량으로 이동함에 따라 구매자는 각 도입 옵션에서 SIEM 시장 규모의 투명성을 얻을 수 있습니다. 공급업체의 통합으로 노후화된 On-Premise 스택에서 하이퍼스케일러가 호스팅하는 최신 SaaS 제품으로의 전환이 가속화되었습니다.
2024년 레거시 플랫폼의 판매 점유율은 46.20%에 달하지만, 쿼리 성능 및 규칙 튜닝이 데이터 규모에 따라 감소함에 따라 레거시 플랫폼의 지위는 감소합니다. 차세대 클라우드 네이티브 엔진의 CAGR은 18.10%로 아키텍처 유형 중 가장 빠른 것으로 예측됩니다. 이러한 시스템은 스토리지를 컴퓨팅에서 분리하고 주입 중에 머신러닝을 통합하여 평균 감지 시간을 단축합니다.
Palo Alto Networks는 QRadar SaaS를 Cortex XSIAM에 통합하여 인수 후 첫 분기에 9,000만 달러 이상을 기록했습니다. 오픈소스 스택은 예산의 틈새 시장을 열지만 깊은 엔지니어링 기술이 필요합니다. 마이그레이션 유틸리티와 호환성 레이어는 기존 규칙 구문에서 스키마 온 리드 모델로의 마이그레이션을 용이하게 합니다. SIEM 시장은 원격 측정을 이벤트 스트림이 아닌 빅 데이터로 취급하는 아키텍처를 지원합니다.
SIEM 시장 보고서는 도입(On-Premise, 기타), SIEM 아키텍처(기존 SIEM, 차세대 SIEM, 기타), 구성 요소(플랫폼/소프트웨어, 전문 서비스, 관리 SIEM 서비스(MSSP)), 조직 규모(중소기업, 대기업), 최종 사용자 업계(은행, 금융서비스 및 보험(BFSI), 산업, 전자상거래)
지역 분석
북미는 2024년 SIEM 시장 수익의 39.20%를 차지했으며, 성숙한 정보 유출 통지 법규와 높은 사이버 보험료에 의해 지원되고 있습니다. 이사회가 보안관리를 수탁자 위험과 연결하기 때문에 예산 배분은 계속 견고합니다. 이 지역의 클라우드 구축과 AI의 초기 도입은 지역의 리더십을 강화합니다. 기초가 포화 상태에 있음에도 불구하고, 통합된 관측 가능성에 대한 업셀은 성장률이 1자리대 중반을 유지하고 있습니다.
아시아태평양의 CAGR은 11.80%로 세계에서 가장 빠른 것으로 예측됩니다. 중국의 다단계 보호 제도와 인도의 디지털 개인 데이터 보호법이 중요 정보 인프라의 로깅 의무화에 박차를 가합니다. 국내 클라우드 벤더는 현지화 규정을 충족하기 위해 세계 SIEM 기업와 제휴했습니다. 일본 콩그로말리트는 주권과 능력의 균형을 맞추면서 원시 이벤트를 도쿄 리전에 저장하고 분석을 세계 클라우드로 아웃소싱하는 하이브리드 SIEM을 선호합니다.
유럽은 GDPR(EU 개인정보보호규정)과 NIS2를 배경으로 큰 이해 관계를 유지하고 있습니다. 이사회는 감시 부족에 대해 전 세계 매출의 2%에 달하는 벌금에 직면하여 투자의 동기부여가 되고 있습니다. 데이터 주권은 OVHcloud와 독일 텔레콤과 같은 지역 클라우드를 선호합니다. 디지털 운영 탄력성 법(Digital Operational Resilience Act)은 금융 업계에서 실시간 위협 감지를 의무화하여 SIEM에 대한 수요를 높이고 있습니다.
기타 혜택 :
- 엑셀 형식 시장 예측(ME) 시트
- 3개월간의 애널리스트 서포트
목차
제1장 서론
- 조사의 전제조건과 시장의 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 상황
- 시장 개요
- 시장 성장 촉진요인
- 보안 원격 측정 볼륨의 기하급수적 증가
- 규제 당국에 의한 벌칙과 감사 빈도 증가
- 기업 워크로드의 클라우드화와 하이브리드화의 가속
- AI/ML을 도입한 분석으로 S/N비를 개선
- 보안 데이터 파이프라인 계층의 출현으로 SIEM의 TCO 감소
- 공급업체 메가딜(Cisco-Splunk, Exabeam-LogRhythm) 트리거 리프레시 사이클
- 시장 성장 억제요인
- 높은 총 소유 비용과 라이선스의 복잡성
- 숙련된 SOC 애널리스트의 부족
- 중앙 로그 집계에 있어서의 데이터 주권 장벽
- XDR/SOAR 플랫폼과의 중복으로 예산 승인이 지연
- 중요한 규제 틀의 평가
- 밸류체인 분석
- 기술의 전망
- Porter's Five Forces
- 공급기업의 협상력
- 구매자의 협상력
- 신규 참가업체의 위협
- 대체품의 위협
- 경쟁 기업간 경쟁 관계
- 주요 이해관계자의 영향 평가
- 주요 이용 사례와 사례 연구
- 시장의 거시경제 요인에 미치는 영향
- 투자분석
제5장 시장 세분화
- 전개별
- On-Premise
- 클라우드
- 하이브리드
- SIEM 아키텍처별
- 레거시/기존 SIEM
- 클라우드 네이티브/차세대 SIEM
- 오픈소스 SIEM
- 구성요소별
- 플랫폼/소프트웨어
- 전문 서비스
- 매니지드 SIEM 서비스(MSSP)
- 조직 규모별
- 중소기업
- 대기업
- 최종 사용자 업계별
- 은행, 금융서비스 및 보험(BFSI)
- 소매 및 전자상거래
- 정부 및 방위
- 헬스케어 및 생명과학
- 제조업
- 에너지 및 유틸리티
- 텔레콤과 IT
- 기타
- 용도별
- 위협 감지 및 분석
- 컴플라이언스 및 감사 관리
- 인시던트 응답과 법의학
- 로그 관리 및 리포팅
- 클라우드 워크로드 보안 모니터링
- IoT/OT 보안 감시
- 지역별
- 북미
- 미국
- 캐나다
- 멕시코
- 남미
- 브라질
- 아르헨티나
- 기타 남미
- 유럽
- 영국
- 독일
- 프랑스
- 이탈리아
- 스페인
- 북유럽 국가
- 기타 유럽
- 중동 및 아프리카
- 중동
- 사우디아라비아
- 아랍에미리트(UAE)
- 튀르키예
- 기타 중동
- 아프리카
- 남아프리카
- 이집트
- 나이지리아
- 기타 아프리카
- 아시아태평양
- 중국
- 인도
- 일본
- 한국
- ASEAN
- 호주
- 뉴질랜드
- 기타 아시아태평양
- 북미
제6장 경쟁 구도
- 시장 집중도
- 전략적 동향
- 시장 점유율 분석
- 기업 프로파일
- Cisco Systems, Inc.(Splunk)
- International Business Machines Corporation
- Microsoft Corporation(Azure Sentinel)
- Google LLC(Chronicle Security Operations)
- Fortinet, Inc.
- LogRhythm, Inc.
- Exabeam, Inc.
- Rapid7, Inc.
- OpenText Corporation(ArcSight)
- RSA Security LLC
- Securonix, Inc.
- CrowdStrike Holdings, Inc.
- Elastic NV
- ATandT Cybersecurity(AlienVault)
- Micro Focus International plc
- SolarWinds Corporation
- Graylog, Inc.
- Logpoint A/S
- ManageEngine(Zoho Corp.)
- Hewlett Packard Enterprise Company
제7장 시장 기회와 장래의 전망
SHW 25.11.11The global SIEM market stood at USD 10.78 billion in 2025 and is forecast to climb to USD 19.13 billion by 2030, advancing at a 12.16% CAGR.
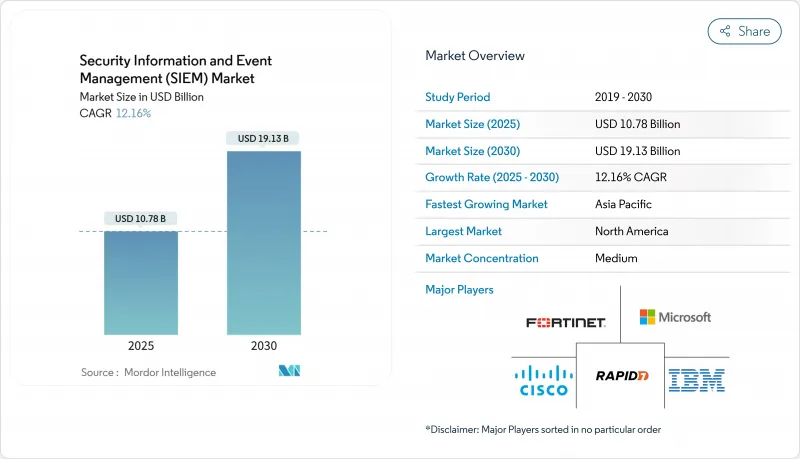
A surge in cloud workload telemetry, strict regulatory mandates, and rapid vendor consolidation are the primary growth catalysts. Large enterprises continue to expand log ingestion as attack surfaces widen, while small and medium-sized businesses enter the market through cloud-native consumption models. North American demand is buoyed by SOX and PCI DSS rules, whereas European spending accelerates in response to NIS2 and DORA. Vendor roadmaps now revolve around AI-powered analytics, unified data pipelines, and simplified licensing, themes that spur refresh cycles following Cisco's landmark acquisition of Splunk in 2024.
Global Security Information And Event Management (SIEM) Market Trends and Insights
Exponential growth of security telemetry
Enterprises generate terabytes of logs each day from endpoints, cloud services, and operational technology. The volume strains traditional ingestion models yet unlocks richer context for threat hunting. CPFL Energia monitors more than 50,000 smart-grid devices through a modern SIEM that routes high-value events to a data lake for cost control. Cloud-native elasticity permits burst processing during incident spikes, and selective retention keeps storage fees predictable. Vendors that integrate low-cost object storage with query¬able metadata gain traction as customers balance coverage and cost.
Escalating regulatory penalties and audits
Europe's NIS2 obliges operators of essential services to log, monitor, and retain events for incident reconstruction, pushing security budgets up to 9.0% of IT spending. In finance, DORA compels real-time detection and reporting. Bank Leumi lowered false positives by 70% after a SIEM upgrade tailored to audit evidence generation. Health providers face HIPAA-driven breach fines that now average USD 4.88 million, a cost that underscores the need for continuous monitoring.
High total cost of ownership
Traditional per-event licenses force buyers to cap ingestion, creating security blind spots. Hardware tariffs raised appliance costs by as much as 20% during 2024, adding budget strain. Hidden cloud fees for storage, egress, and premium analytics surprise first-time adopters. Vendors now push pipeline off-load tiers and flat-rate pricing to restore predictability.
Other drivers and restraints analyzed in the detailed report include:
- Accelerated cloud and hybrid adoption
- AI and ML-driven analytics
- Shortage of skilled SOC analysts
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
On-premise deployments held 55.75% of SIEM market share in 2024. The segment remains favored by industries bound to strict data-sovereignty policies, yet growth is subdued as hardware costs rise and skills shortages deepen. The cloud cohort advances at 13.40% CAGR, propelled by elastic scaling and pay-as-you-go fees that widen access to advanced analytics. Hybrid designs act as a bridge, placing regulated data on local nodes while streaming telemetry to low-cost object storage in the cloud.
Cloud adoption shifts upgrade cycles from multi-year appliance refreshes to continuous feature delivery. Siemens uses a hybrid pattern that runs OT parsers on premises while enriching events in the cloud for threat intelligence correlation. As licensing shifts to data usage, buyers gain transparency on the SIEM market size for each deployment choice. Vendor consolidation accelerates moves away from aging on-prem stacks toward modern SaaS offerings hosted by hyperscalers.
Legacy platforms represented 46.20% revenue share in 2024, yet they lose ground as query performance and rule tuning falter under data scale. Next-generation cloud-native engines are forecast to rise at 18.10% CAGR, the fastest among architectural types. These systems decouple storage from compute and embed machine learning at ingestion, reducing mean time to detect.
Palo Alto Networks folded QRadar SaaS into Cortex XSIAM and booked more than USD 90 million in the first post-deal quarter. Open-source stacks carve a budget niche but demand deep engineering skills. Migration utilities and compatibility layers ease the shift from traditional rule syntax to schema-on-read models. The SIEM market aligns behind architectures that treat telemetry as big data rather than event streams.
The SIEM Market Report Segments the Industry by Deployment (On-Premise, and More), SIEM Architecture ( Traditional SIEM, Next-Gen SIEM, and More), Component (Platform / Software, Professional Services, and Managed SIEM Services (MSSP)), Organization Size (Small and Medium Enterprises, and Large Enterprises), End-User Industry (Banking, Financial Services and Insurance (BFSI), Retail and E-Commerce, and More), and Geography.
Geography Analysis
North America accounted for 39.20% of the SIEM market revenue in 2024, underpinned by mature breach notification statutes and high cyber insurance premiums. Budget allocations remain robust as boards tie security controls to fiduciary risk. The region's cloud adoption and early AI experimentation reinforce its leadership. Despite a saturated base, upsell to integrated observability keeps growth in mid-single digits.
Asia-Pacific is projected to post 11.80% CAGR, the fastest globally. China's Multi-Level Protection Scheme and India's Digital Personal Data Protection Act spur mandatory logging for critical information infrastructure. Domestic cloud vendors team with global SIEM players to satisfy localisation rules. Japanese conglomerates favour hybrid SIEM that parks raw events in Tokyo regions while outsourcing analytics to global clouds, balancing sovereignty and capability.
Europe maintains a sizeable stake on the back of GDPR and the incoming NIS2. Boards face fines reaching 2% of global turnover for monitoring lapses, incentivising investment. Data sovereignty drives preference for regional clouds such as OVHcloud and Deutsche Telekom. The Digital Operational Resilience Act imposes real-time threat detection in finance, fuelling premium SIEM demand.
- Cisco Systems, Inc. (Splunk)
- International Business Machines Corporation
- Microsoft Corporation (Azure Sentinel)
- Google LLC (Chronicle Security Operations)
- Fortinet, Inc.
- LogRhythm, Inc.
- Exabeam, Inc.
- Rapid7, Inc.
- OpenText Corporation (ArcSight)
- RSA Security LLC
- Securonix, Inc.
- CrowdStrike Holdings, Inc.
- Elastic N.V.
- ATandT Cybersecurity (AlienVault)
- Micro Focus International plc
- SolarWinds Corporation
- Graylog, Inc.
- Logpoint A/S
- ManageEngine (Zoho Corp.)
- Hewlett Packard Enterprise Company
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Exponential growth of security telemetry volumes
- 4.2.2 Escalating regulatory penalties and audit frequency
- 4.2.3 Accelerated cloud and hybrid adoption of enterprise workloads
- 4.2.4 AI/ML-infused analytics improve signal-to-noise ratios
- 4.2.5 Emergence of security-data-pipeline layer reduces SIEM TCO
- 4.2.6 Vendor mega-deals (Cisco-Splunk, Exabeam-LogRhythm) trigger refresh cycles
- 4.3 Market Restraints
- 4.3.1 High total cost of ownership and licensing complexity
- 4.3.2 Shortage of skilled SOC analysts
- 4.3.3 Data-sovereignty barriers to central log aggregation
- 4.3.4 Overlap with XDR/SOAR platforms delays budget approval
- 4.4 Evaluation of Critical Regulatory Framework
- 4.5 Value Chain Analysis
- 4.6 Technological Outlook
- 4.7 Porter's Five Forces
- 4.7.1 Bargaining Power of Suppliers
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Threat of New Entrants
- 4.7.4 Threat of Substitutes
- 4.7.5 Competitive Rivalry
- 4.8 Impact Assessment of Key Stakeholders
- 4.9 Key Use Cases and Case Studies
- 4.10 Impact on Macroeconomic Factors of the Market
- 4.11 Investment Analysis
5 MARKET SEGMENTATION
- 5.1 By Deployment
- 5.1.1 On-premise
- 5.1.2 Cloud
- 5.1.3 Hybrid
- 5.2 By SIEM Architecture
- 5.2.1 Legacy / Traditional SIEM
- 5.2.2 Cloud-native / Next-Gen SIEM
- 5.2.3 Open-source SIEM
- 5.3 By Component
- 5.3.1 Platform / Software
- 5.3.2 Professional Services
- 5.3.3 Managed SIEM Services (MSSP)
- 5.4 By Organization Size
- 5.4.1 Small and Medium Enterprises
- 5.4.2 Large Enterprises
- 5.5 By End-user Industry
- 5.5.1 Banking, Financial Services and Insurance (BFSI)
- 5.5.2 Retail and E-commerce
- 5.5.3 Government and Defense
- 5.5.4 Healthcare and Life Sciences
- 5.5.5 Manufacturing
- 5.5.6 Energy and Utilities
- 5.5.7 Telecom and IT
- 5.5.8 Others
- 5.6 By Application
- 5.6.1 Threat Detection and Analytics
- 5.6.2 Compliance and Audit Management
- 5.6.3 Incident Response and Forensics
- 5.6.4 Log Management and Reporting
- 5.6.5 Cloud-Workload Security Monitoring
- 5.6.6 IoT / OT Security Monitoring
- 5.7 By Geography
- 5.7.1 North America
- 5.7.1.1 United States
- 5.7.1.2 Canada
- 5.7.1.3 Mexico
- 5.7.2 South America
- 5.7.2.1 Brazil
- 5.7.2.2 Argentina
- 5.7.2.3 Rest of South America
- 5.7.3 Europe
- 5.7.3.1 United Kingdom
- 5.7.3.2 Germany
- 5.7.3.3 France
- 5.7.3.4 Italy
- 5.7.3.5 Spain
- 5.7.3.6 Nordics
- 5.7.3.7 Rest of Europe
- 5.7.4 Middle East and Africa
- 5.7.4.1 Middle East
- 5.7.4.1.1 Saudi Arabia
- 5.7.4.1.2 United Arab Emirates
- 5.7.4.1.3 Turkey
- 5.7.4.1.4 Rest of Middle East
- 5.7.4.2 Africa
- 5.7.4.2.1 South Africa
- 5.7.4.2.2 Egypt
- 5.7.4.2.3 Nigeria
- 5.7.4.2.4 Rest of Africa
- 5.7.5 Asia-Pacific
- 5.7.5.1 China
- 5.7.5.2 India
- 5.7.5.3 Japan
- 5.7.5.4 South Korea
- 5.7.5.5 ASEAN
- 5.7.5.6 Australia
- 5.7.5.7 New Zealand
- 5.7.5.8 Rest of Asia-Pacific
- 5.7.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 Cisco Systems, Inc. (Splunk)
- 6.4.2 International Business Machines Corporation
- 6.4.3 Microsoft Corporation (Azure Sentinel)
- 6.4.4 Google LLC (Chronicle Security Operations)
- 6.4.5 Fortinet, Inc.
- 6.4.6 LogRhythm, Inc.
- 6.4.7 Exabeam, Inc.
- 6.4.8 Rapid7, Inc.
- 6.4.9 OpenText Corporation (ArcSight)
- 6.4.10 RSA Security LLC
- 6.4.11 Securonix, Inc.
- 6.4.12 CrowdStrike Holdings, Inc.
- 6.4.13 Elastic N.V.
- 6.4.14 ATandT Cybersecurity (AlienVault)
- 6.4.15 Micro Focus International plc
- 6.4.16 SolarWinds Corporation
- 6.4.17 Graylog, Inc.
- 6.4.18 Logpoint A/S
- 6.4.19 ManageEngine (Zoho Corp.)
- 6.4.20 Hewlett Packard Enterprise Company
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-need Assessment



















