
|
시장보고서
상품코드
1690161
네트워크 암호화 - 시장 점유율 분석, 산업 동향, 통계, 성장 예측(2025-2030년)Network Encryption - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
네트워크 암호화 시장 규모는 2025년에 52억 4,000만 달러, 2030년에는 78억 5,000만 달러에 달할 것으로 예측됩니다. 예측 기간(2025-2030년) CAGR은 8.43%를 나타낼 전망입니다.

네트워크 암호화의 성장은 주로 조직의 데이터 보안과 프라이버시에 대한 관심 증가로 인한 것입니다.
주요 하이라이트
- 인터넷의 성장, 클라우드 컴퓨팅, 사이버 공격 증가로 보다 안전한 데이터 통신 및 스토리지의 필요성이 높아지고 있으며, 일반 데이터 보호 규칙(GDPR(EU 개인정보보호규정))이나 지불 카드 산업 데이터 보안 기준(PCI DSS) 등 정부 규제 증가로 인해 조직은 안전한 데이터 전송 방법을 도입할 필요가 있어 네트워크 암호화의 성장을 더욱 촉진하고 있습니다.
- 게다가 다양한 최종사용자 산업이 사물인터넷(IoT) 기반 솔루션을 업무에 채용하게 된 것으로, IoT 네트워크상에서 전송되는 데이터를 보호하기 위한 암호화의 요구가 높아져 시장의 성장을 지원하고 있습니다.
- 네트워크 암호화 산업이 성장한 것은 새로운 암호화 알고리즘이나 보다 뛰어난 암호화 소프트웨어가 만들어졌기 때문입니다.
- 암호화 솔루션의 도입은 특히 IT 리소스가 적은 기업의 경우 어려운 비용이 많이 드는 경우가 있습니다. 일부 조직에서는 암호화 솔루션을 구매하고 설정하는 비용과 이를 사용하고 유지 관리할 직원을 교육하는 데 드는 비용이 사용하지 않는 이유가 될 수 있습니다. 또한 암호화 알고리즘에 따라서는 기술적인 문제가 있어 기업 네트워크에 적합하지 않은 것도 있습니다.
- 시장 성장에 영향을 미치는 가장 중요한 요인은 네트워크 보안 침해 증가, 많은 조직의 클라우드 기술 이용 증가, 더 나은 데이터 보호를 위해 시시각각 변화하는 규제 기준을 충족시키는 필요성 증가입니다.
- COVID-19의 유행은 네트워크 암호화 시장에 큰 영향을 끼쳤습니다. 그리고 원격 데스크톱 솔루션이 필요했습니다. 이로 인해 네트워크 암호화 제품 및 서비스에 대한 수요가 급증하고 산업 성장을 뒷받침했습니다.
네트워크 암호화 시장 동향
통신 및 IT 부문이 시장에서 큰 점유율을 차지할 전망
- 세계의 IT 및 통신산업이 네트워크 암호화를 추진하는 주요인으로는 클라우드 이용의 확대, 광통신에 대한 투자 증가, 네트워크 데이터 유출 증가, 정부의 엄격한 규제 등을 들 수 있습니다.
- 게다가 사설망 채택 확대, 네트워크 자동화 동향, 5G 네트워크 구축은 네트워크 트래픽이 크게 증가하고 보다 첨단 보안 조치가 필요할 것으로 예상됩니다. 네트워크 암호화는 이러한 네트워크에서 기밀 데이터의 안전을 보호하고 새로운 비즈니스 기회를 열 것입니다.
- VIAVISION에 따르면 2023년 4월 현재 미국의 503개 도시로 5G 네트워크에 가장 많이 액세스하고 있으며 356개 도시에서 5G를 사용할 수 있는 중국이 2위를 차지하고 있습니다.
- 스마트 공장, 지능형 교통 시스템, 5세대 이후의 휴대폰 네트워크, 사물 인터넷, 분산형 대장 기술, 양자 안전 통신 등의 새로운 ICT 기술에는 다양한 위협과 위험에 대처하기 위한 기술적·조직적 대책이 필요합니다.
- 5G 기술의 도입으로 네트워크에 연결되는 사물 인터넷(IoT) 장치는 아마 증가하고 해커가 보다 광범위하고 성공적인 공격을 할 수 있는 새로운 기회가 펼쳐집니다. Ericsson에 따르면 모바일 데이터 트래픽의 총량은 2023년 월간 26EB에서 2029년월73EB로 증가하고 CAGR 19%로 성장할 것으로 예상됩니다. 이러한 모든 요인은 통신 공급업체의 네트워크 자동화 범위를 확대하고 조사 시장 수요를 부추기고 있습니다.
- 또한, 세계 보안 서비스의 혁신적인 확대와 채택은 네트워크 암호화 기술 수요를 더욱 끌어 올리고 있습니다. 통신에 대한 위협은 레거시 기술이 있는 산업에서 전형적인 IP 기반 위협의 조합으로 인해 발생합니다. 5G 기술이 발전함에 따라 위협의 표면이 확대되고 공격자는 더 많은 기회를 얻을 수 있습니다. 이를 통해 통신사의 사이버 보안팀은 새로운 위협과 방어할 경고 증가에 직면하면서도 공격자의 한 걸음 앞서기 위해 새로운 기술과 자동화를 활용하여 워크플로를 간소화하는 방법을 모색하고 있습니다.
북미가 큰 시장 점유율을 차지할 전망
- 북미는 기술적으로 설비가 갖추어진 지역입니다.미국이나 캐나다와 같은 신흥 경제 제국이 큰 시장 점유율을 차지하고 있어 모든 규모의 기업이 정부의 규칙이나 규제에 따르기 위한 적절한 플랫폼이 갖추어져 있습니다.
- 북미 정부는 기밀 데이터를 전송 중에 보호할 것을 요구하는 규칙을 마련하고 있습니다.
- 또한 2023년 9월 양자 안전 암호의 세계 리더 중 하나인 Arqit Quantum Inc.와 디지털 인프라를 위한 세계의 신뢰할 수 있는 사이버 보안 전문가인 Exclusive Networks North America는 Arqit의 자체 대칭 키 합의 플랫폼에 대한 합의를 발표했습니다. Networks의 벤더와 채널 파트너의 포트폴리오는 양자 컴퓨팅에 의한 리스크를 포함한 현재와 장래의 사이버 위협으로부터 보호하는 Arqit의 기술을 제공할 수 있습니다.
- 이 지역의 하이테크 산업이 지속적으로 성장함에 따라 네트워크 암호화 솔루션에 대한 수요가 증가하고 있습니다. 기업은 또한 네트워크를 암호화하기 위한 보다 선진적인 방법을 개발하기 위한 연구개발에도 자금을 지출하고 있습니다.
- 최근 개정된 EARN IT법이 성립하면 강력한 암호화는 불안정한 지반에 놓이게 되지만, 암호화 데이터에 대한 합법적 액세스법(LAEDA)은 수백만 명의 사람들이 개인과 국가의 안보를 위해 매일 이용하고 있는 툴을 직접 공격하는 것입니다.
네트워크 암호화 산업 개요
네트워크 암호화 시장은 세분화되어 있으며, 다수의 진출기업이 활동하고 있습니다. Ltd., Viasat Inc., Raytheon Technologies Corporation, Securosys SA., Packetlight Networks는 현재 시장에 존재하며 합병, 인수, 협업, 제품 혁신과 같은 전략적 이니셔티브를 취하는 주요 기업의 일부입니다.
2023년 2월, Atos는 사설 5G 네트워크의 도입을 검토하고 있는 기업, 통합된 자동화를 실현하려고 하는 통신 사업자에게, 새로운 「5Guard」시큐리티의 제공을 개시한다고 발표했습니다. 보안을 위해 보안 오케스트레이션을 실시했습니다. Managed Detection and Response(MDR) 플랫폼이 있어 잠재적인 위협을 거의 실시간으로 감지 및 대응함으로써 5G 네트워크 요소, 용도, 워크로드의 보안을 향상시키고 있습니다.
2023년 1월, 디지털 인프라를 제조하는 Equinix는 클라우드 서비스를 제조하는 Aviatrics와 협력하여 기업 환경을 위한 고성능 암호화를 실현했습니다. 패브릭을 활용한 이 솔루션의 조합을 통해 클라우드에 가장 빠르고 안전한 연결을 제공하여 여러 클라우드에서 어떤 일이 발생하는지 확인할 수 있습니다.
기타 혜택
- 엑셀 형식 시장 예측(ME) 시트
- 3개월간의 애널리스트 서포트
목차
제1장 서론
- 조사의 전제조건과 시장 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 인사이트
- 시장 개요
- 산업의 매력 - Porter's Five Forces 분석
- 공급기업의 협상력
- 구매자의 협상력
- 신규 참가업체의 위협
- 대체품의 위협
- 경쟁 기업간 경쟁 관계의 강도
- 시장에 대한 COVID-19의 영향 평가
제5장 시장 역학
- 시장 성장 촉진요인
- 네트워크 보안 침해 증가
- 다수의 조직에 의한 클라우드 기술의 채용 증가
- 시장의 과제
- 네트워크 암호화 솔루션의 도입 비용의 높이
제6장 시장 세분화
- 도입 유형별
- 클라우드
- 온프레미스
- 컴포넌트별
- 하드웨어
- 솔루션 & 서비스
- 조직 규모별
- 중소기업
- 대기업
- 최종 사용자 산업별
- 통신 및 IT
- BFSI
- 정부기관
- 미디어&엔터테인먼트
- 기타
- 지역별
- 북미
- 유럽
- 아시아태평양
- 라틴아메리카
- 중동 및 아프리카
제7장 경쟁 구도
- 기업 프로파일
- Thales Trusted Cyber Technologies
- ATMedia Gmbh
- Atos SE
- Juniper Networks Inc.
- Certes Networks Inc.
- Senetas Corporation Ltd.
- Viasat Inc.
- Raytheon Technologies Corporation
- Securosys SA
- Packetlight Networks
- Rohde & Schwarz Cybersecurity GmbH
- Colt Technology Services Group Ltd.
- Ciena Corporation
제8장 투자 분석
제9장 시장의 미래
SHW 25.05.09The Network Encryption Market size is estimated at USD 5.24 billion in 2025, and is expected to reach USD 7.85 billion by 2030, at a CAGR of greater than 8.43% during the forecast period (2025-2030).
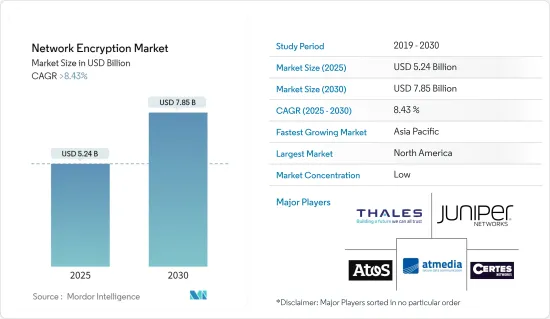
The growth of network encryption is primarily attributed to the increasing concern for data security and privacy in organizations.
Key Highlights
- The growth of the internet, cloud computing, and the increasing number of cyberattacks have led to the need for more secure data communication and storage. Additionally, increasing government regulations, such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS), require organizations to implement secure data transmission methods, further driving the growth of network encryption.
- Furthermore, the growth in adopting Internet of Things (IoT)-based solutions by the various end-user industries in their operations has increased the need for encryption to secure data transmitted over IoT networks, supporting market growth.
- The network encryption industry has grown because new encryption algorithms and better encryption software have been made. For example, using encryption algorithms that quantum computers can't break is becoming more important because quantum computers could break traditional encryption methods.
- Putting encryption solutions into place can be hard and expensive, especially for businesses with few IT resources. For some organizations, the cost of buying and setting up encryption solutions and training staff to use and maintain them can be a reason not to use them. Also, some encryption algorithms may have technical problems that make them unsuitable for s networks. Such factors are expected to challenge the market's growth during the forecast period.
- The most important factors affecting the market's growth are the growing number of network security breaches, the increasing use of cloud technologies by many organizations, and the growing need to meet ever-changing regulatory standards for better data protection.
- The COVID-19 pandemic significantly affected the network encryption market. As the trend toward working from home grew, there was more demand for secure remote work solutions. With more people working from home, there was a need for secure and reliable virtual private networks (VPNs) and remote desktop solutions to protect sensitive corporate data. This led to a surge in demand for network encryption products and services, boosting growth in the industry. Additionally, businesses increased their investment in cybersecurity to address the rise in cyber-attacks and security breaches related to the pandemic.
Network Encryption Market Trends
Telecom and IT Sector is Expected to Hold a Significant Share of the Market
- Some of the main things pushing the IT and telecom industries worldwide to use network encryption are the growing use of the cloud, increasing investment in optical communication, growing network data breaches, and strict government regulations.
- Furthermore, the growing adoption of a private network, trends in network automation, and the rollout of 5G networks are expected to significantly increase network traffic, requiring more advanced security measures. Network encryption will keep sensitive data safe on these networks, opening up new business opportunities.
- According to VIAVISION, as of April 2023, with the highest 5G network access, it was available in 503 cities in the United States; with 5G availability in 356 cities, China followed in second.
- Emerging ICT technologies such as smart factories, intelligent transportation systems, the 5th generation of cellular networks and beyond, the Internet of Things, distributed ledger technologies, and quantum-safe communication need technical and organizational measures to address various threats and risks.
- The deployment of 5G technology will probably lead to increased Internet of Things (IoT) devices connected to networks, opening up new chances for hackers to conduct more extensive and sophisticated assaults. According to Ericsson, Total mobile data traffic is expected to grow from 26 EB per month in 2023 to 73 EB per month in 2029, growing at a CAGR of 19 percent. All these factors are expanding the scope of network automation among telecom vendors, fueling the demand in the studied market.
- Furthermore, the innovation expansion launch and adoption of security services across the globe have further boosted the demand for network encryption techniques. Threats against telecommunications result from a combination of typical IP-based threats in an industry with legacy technology. As 5G technology advances, the threat surface will only expand, giving attackers more opportunities. This leaves cybersecurity teams at telecom companies looking for ways to leverage new technology and automation to streamline workflows to stay ahead of attackers in the face of new threats and an increasing number of alerts to triage.
North America is Expected to Hold Significant Market Share
- North America is a well-equipped region in terms of technology. It has a significant market share because of developed economies like the United States and Canada, and it has the right platforms for businesses of all sizes to follow government rules and regulations.
- The government of North America has put in place rules that require sensitive data to be protected while in transit. This has driven the need for network encryption solutions to meet these regulatory requirements.
- Furthermore, in September 2023, Arqit Quantum Inc., one of the global leaders in quantum-safe encryption, and Exclusive Networks North America, a global trusted cybersecurity specialist for digital infrastructure, announced an agreement for Arqit's unique Symmetric Key Agreement Platform. Joining Networks' portfolio of vendors and channel partners can provide Arqit's technology that protects against current and future cyber threats, including the risk from quantum computing.
- As the tech industry in the region continues to grow, there is more demand for network encryption solutions. This is because cloud computing is becoming more popular, and organizations want to protect sensitive data while it is being sent to and from the cloud. The companies also spend money on research and development to develop more advanced ways to encrypt networks. This investment is contributing to the growth of the industry.
- While the recently amended EARN IT Act would leave strong encryption on unstable ground if passed into law, The Lawful Access to Encrypted Data Act (LAEDA) is a direct assault on the tool millions of people rely on for personal and national security each day.
Network Encryption Industry Overview
The network encryption market is fragmented, with several players operating. The major players with a prominent share in the market are focusing on expanding their customer base across foreign countries by leveraging strategic collaborative initiatives to increase their market share and profitability. Thales Trusted Cyber Technologies, Atos SE, Juniper Networks, Inc., Certes Networks, Inc., Senetas Corporation Ltd., Viasat Inc., Raytheon Technologies Corporation, Securosys SA., and Packetlight Networks are some of the major players present in the current market and undergoing strategic initiatives such as mergers, acquisitions, collaboration, product innovation, and others.
In February 2023, Atos announced the launch of its new '5Guard' security offering for organizations looking to deploy private 5G networks and for telecom operators looking to enable integrated, automated. They orchestrated security to protect and defend their assets and customers. Atos'product portfolio is Atos'encryption solutions (Trustway), identity and access management software; public critical infrastructure solutions (IDnomic); and Atos Managed Detection and Response (MDR) platform that elevates the security of 5G network elements, applications, and workloads by detecting and responding to potential threats in near real-time.
In January 2023, Equinix, a company that makes digital infrastructure, worked with Aviatrix, which makes cloud services, to make high-performance encryption for enterprise environments. This partnership will make the Aviatrix Edge software available in over 25 of Equinix's global business exchange data centers. The combined solution, which uses Equinix's Network Edge and Equinix Fabric, gives you the fastest, most secure connection to the cloud to see what's happening in multiple clouds.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Attractiveness - Porter's Five Forces Analysis
- 4.2.1 Bargaining Power of Suppliers
- 4.2.2 Bargaining Power of Buyers
- 4.2.3 Threat of New Entrants
- 4.2.4 Threat of Substitute Products
- 4.2.5 Intensity of Competitive Rivalry
- 4.3 Assessment of the Impact of COVID-19 on the Market
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Increasing Number of Network Security Breaches
- 5.1.2 Increasing Adoption of Cloud Technologies by Numerous Organizations
- 5.2 Market Challenges
- 5.2.1 High Implementation Cost of Network Encryption Solutions
6 MARKET SEGMENTATION
- 6.1 By Deployment Type
- 6.1.1 Cloud
- 6.1.2 On-premise
- 6.2 By Component
- 6.2.1 Hardware
- 6.2.2 Solutions & Services
- 6.3 By Organization Size
- 6.3.1 Small and Medium-sized Enterprises
- 6.3.2 Large-sized Enterprises
- 6.4 By End-user Industry
- 6.4.1 Telecom & IT
- 6.4.2 BFSI
- 6.4.3 Government
- 6.4.4 Media & Entertainment
- 6.4.5 Other End-user Industries
- 6.5 By Geography
- 6.5.1 North America
- 6.5.2 Europe
- 6.5.3 Asia Pacific
- 6.5.4 Latin America
- 6.5.5 Middle East and Africa
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 Thales Trusted Cyber Technologies
- 7.1.2 ATMedia Gmbh
- 7.1.3 Atos SE
- 7.1.4 Juniper Networks Inc.
- 7.1.5 Certes Networks Inc.
- 7.1.6 Senetas Corporation Ltd.
- 7.1.7 Viasat Inc.
- 7.1.8 Raytheon Technologies Corporation
- 7.1.9 Securosys SA
- 7.1.10 Packetlight Networks
- 7.1.11 Rohde & Schwarz Cybersecurity GmbH
- 7.1.12 Colt Technology Services Group Ltd.
- 7.1.13 Ciena Corporation














