
|
시장보고서
상품코드
1822601
자동차 사이버 보안 시장 : 기회, 성장 촉진요인, 산업 동향 분석, 예측(2025-2034년)Automotive Cybersecurity Market Opportunity, Growth Drivers, Industry Trend Analysis, and Forecast 2025 - 2034 |
||||||
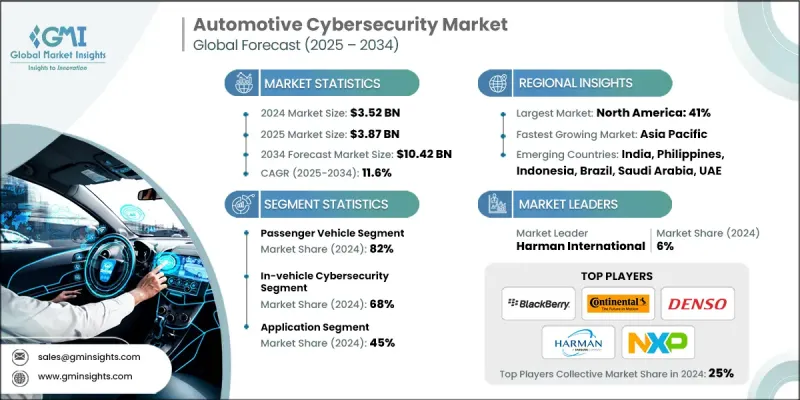
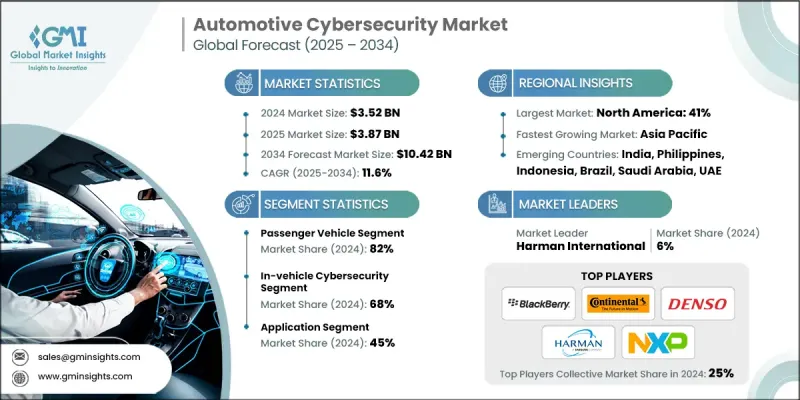
세계 자동차 사이버 보안 시장은 2024년 35억 2,000만 달러로 평가되었습니다. Global Market Insights Inc.가 발행한 최신 보고서에 따르면 이 시장은 2025년 38억 7,000만 달러, 2034년에는 104억 2,000만 달러에 달하고, CAGR 11.6%를 보일 것으로 예측됩니다.
자동차가 V2X(Vehicle-to-everything) 통신 및 임베디드 인포테인먼트 시스템을 통해 점점 연결됨에 따라 해커의 공격 대상이 크게 확대되고 있습니다. 이러한 이유로 자동차 제조업체는 실시간 데이터 교환, 차량 네트워크 및 디지털 시스템을 보호하기 위한 견고한 사이버 보안 솔루션에 투자하고 있습니다.
| 시장 범위 | |
|---|---|
| 시작 연도 | 2024년 |
| 예측 연도 | 2025-2034년 |
| 시장 규모 | 35억 2,000만 달러 |
| 예측 금액 | 104억 2,000만 달러 |
| CAGR | 11.6% |
승용차 수요 증가
자동차 사이버 보안 시장의 승용차 부문은 커넥티드카, 인포테인먼트 시스템, 자율주행 기술의 급속한 성장으로 2024년 지속 가능한 점유율을 유지했습니다. 소비자들이 보다 스마트하고 안전하며 디지털화된 운전 경험을 기대하는 가운데 자동차 제조업체는 승용차에 고급 사이버 보안 프로토콜을 직접 통합하고 있습니다.
차량용 사이버 보안 채택 확대
차량용 사이버 보안 분야는 전자제어장치(ECU), 인포테인먼트 시스템, 텔레매틱스 및 차량 네트워크를 외부 위협으로부터 보호하는 데 중점을 두고 있으며, 2024년에 큰 점유율을 차지했습니다. 자동차가 모바일 컴퓨터처럼 작동하기 때문에 차량 탑재 사이버 보안은 실시간 위협 감지, 안전한 통신 및 데이터 무결성을 보장합니다. OEM은 현재 소프트웨어 방화벽, 침입 감지 시스템, 암호화를 차량의 하드웨어 및 소프트웨어 스택에 직접 통합하여 처음부터 보안을 설계하고 있습니다.
주목할만한 용도
자동차 사이버 보안 시장의 용도 부문은 텔레매틱스 및 인포테인먼트에서 ADAS(첨단 운전 지원 시스템) 및 파워트레인 제어에 이르기까지 2024년에 현저한 수익을 올렸습니다. 최신 자동차는 자동차의 모든 디지털 터치 포인트를 보호해야 합니다. 차량 아키텍처가 복잡해짐에 따라 사이버 보안 용도는 각 시스템에 맞게 조정되어 엔드 투 엔드 보호를 보장합니다.
유리한 지역으로 상승하는 북미
북미 자동차 사이버 보안 시장은 강력한 규제 뒤 방패, 기술에 익숙한 소비자, 사이버 보안과 자동차의 주요 혁신자의 존재로 2024년에 강력한 성장을 유지했습니다. 미국에서는 이동성 솔루션에 사이버 내성을 통합하려고합니다. 미국 사이버 보안 행정 명령과 같은 규제 프레임 워크와 데이터 프라이버시에 대한 소비자 의식이 높아짐에 따라 자동차 제조업체는 견고한 차량 보안 시스템에 대한 투자를 가속화하고 있습니다. 또한 OEM과 주요 하이테크 기업간의 제휴는 차량 보안 프로토콜의 새로운 혁신을 뒷받침하고 있습니다.
자동차 사이버 보안 시장의 주요 기업은 Karamba Security, Lear, Harman International, Denso, Upstream Security, NXP, Blackberry, Aptiv, Continental, Intertek입니다.
자동차 사이버 보안 시장의 각 회사는 커넥티드 자동차와 자율 주행 차량의 새로운 위협에 대응하는 최첨단 보안 솔루션을 개발하기 위해 광범위한 조사 개발을 통해 혁신에 주력하고 있습니다. 자동차 제조업체, 기술 제공업체, 규제기관과의 전략적 제휴 및 협력 관계로 제품 통합 및 컴플라이언스가 가속화되고 있습니다. 많은 기업들이 차량의 안전성을 높이기 위해 실시간 위협 감지 시스템과 AI 주도의 사이버 보안 프레임워크에 많은 투자를 하고 있습니다. 인수 및 합작 투자를 통해 세계 비즈니스 거점을 확장하는 것도 새로운 시장과 고객 부문을 얻는 일반적인 전략입니다.
목차
제1장 조사 방법
- 조사 디자인
- 조사 접근
- 데이터 수집 방법
- GMI 독자적인 AI 시스템
- AI를 활용한 조사 강화
- 소스 일관성 프로토콜
- AI의 정밀도 지표
- 기본 추정과 계산
- 기준연도 계산
- 예측 모델
- 시장 예측의 주요 동향
- 정량화된 시장 영향 분석
- 성장 파라미터 예측에 대한 수학적 영향
- 시나리오 분석 프레임워크
- 1차 조사와 검증
- 1차 정보의 일부(단, 이것에 한정되는 것은 아니다)
- 데이터 마이닝 소스
- 2차
- 유료소스
- 공개 정보원
- 지역별 정보원
- 2차
- 조사의 궤적과 신뢰도 점수
- 조사 트레일의 구성요소:
- 스코어링 컴포넌트
- 조사의 투명성에 관한 보충
- 소스 기여 프레임워크
- 품질 보증 지표
- 신뢰에 대한 헌신
제2장 주요 요약
제3장 업계 인사이트
- 생태계 분석
- 공급자의 상황
- 자동차 OEM
- 사이버 보안 솔루션 제공업체
- 클라우드 서비스 제공업체
- Tier 1 공급업체
- 기술 인테그레이터
- 최종 용도
- 이익률 분석
- 비용 구조
- 각 단계에서의 부가가치
- 밸류체인에 영향을 주는 요인
- 혁신
- 공급자의 상황
- 업계에 미치는 영향요인
- 성장 촉진요인
- 커넥티드카의 도입 확대
- 자동차 제조업체에 대한 엄격한 사이버 보안 규제
- 차량 아키텍처의 복잡화
- 무선 업데이트의 보급
- 업계의 잠재적 위험 및 과제
- 사이버 보안 솔루션 구현의 비용 제약
- 레거시 시스템 통합
- 시장 기회
- 커넥티드카의 보급 확대
- 소프트웨어 정의 차량으로의 전환
- 규제의 추진과 컴플라이언스 기준
- EV와 자율주행차 확대
- 성장 촉진요인
- 규제 상황
- 북미
- 유럽
- 아시아태평양
- 라틴아메리카
- 중동 및 아프리카
- Porter's Five Forces 분석
- PESTEL 분석
- 기술과 혁신의 상황
- 현재의 기술 동향
- 기존의 보안 접근법과 한계
- 차세대 보안 아키텍처
- 자동차 개발 프로세스와의 통합
- 신흥기술
- 인공지능과 머신러닝의 용도
- 행동 분석과 이상 검출
- 안전한 차량 통신을 위한 블록체인
- 양자 컴퓨팅이 암호에 미치는 영향
- 제로 트러스트 보안 아키텍처
- 자동차 시스템 전략의 구현
- 네트워크 세분화과 마이크로 세분화
- 아이덴티티 및 액세스 관리(IAM) 솔루션
- 소프트웨어 정의 차량(SDV)의 보안
- 보안 바이 디자인의 원칙
- 지속적인 보안 감시
- 동적 보안 정책 관리
- 미래의 기술 혁신(2025-2034)
- 양자 내성 암호 구현
- 6G 네트워크의 보안 요건
- 엣지 컴퓨팅의 보안 과제
- 자율주행차의 보안 진화
- 기술 준비 레벨(TRL) 평가
- 현재의 기술 성숙도 분석
- 상업화의 타임라인 예측
- 투자요건과 ROI분석
- 현재의 기술 동향
- 특허 분석
- 가격 동향과 경제 분석
- 비용 분석 및 ROI 평가
- 사이버 보안 투자 분석
- CSMS 도입 비용 평가
- 인시던트 비용 영향 분석
- 지역에 따른 비용의 차이
- 비용 최적화 전략
- 재무위험평가
- 위협 인텔리전스 및 공격 분석
- 현재의 위협 상황의 평가
- 공격 벡터의 분류 및 분석
- 중대한 시스템의 취약성
- 고급 지속적 위협(APT) 분석
- 사고 대응과 포렌식 기능
- 위협 인텔리전스 공유와 연계
- 이용 사례
- 투자 상황과 자금 조달 분석
- 비용편익분석
- 최상의 시나리오
제4장 경쟁 구도
- 소개
- 기업의 시장 점유율 분석
- 북미
- 유럽
- 아시아태평양
- 라틴아메리카
- 중동 및 아프리카
- 주요 시장 기업의 경쟁 분석
- 경쟁 포지셔닝 매트릭스
- 전략적 전망 매트릭스
- 주요 발전
- 합병과 인수
- 파트너십 및 협업
- 신제품 발매
- 확장계획과 자금조달
제5장 시장 추정 및 예측 : 차량별, 2021-2034
- 주요 동향
- 승용차
- 해치백
- 세단
- SUV
- 상용차
- 소형차(LCV)
- 중형차(MCV)
- 대형차(HCV)
제6장 시장 추정 및 예측 : 보안별, 2021-2034
- 주요 동향
- 응용
- 네트워크
- 종점
제7장 시장 추정 및 예측 : 전개 모드별, 2021-2034
- 주요 동향
- 클라우드 기반
- On-Premise
- 하이브리드
제8장 시장 추정 및 예측 : 용도별, 2021-2034
- 주요 동향
- ADAS와 안전성
- 바디 컨트롤과 쾌적성
- 인포테인먼트
- 텔레매틱스
- 파워트레인 시스템
- 통신 시스템
제9장 시장 추정 및 예측 : 형태별, 2021-2034
- 주요 동향
- 차재 사이버 보안
- 외부 클라우드 사이버 보안
제10장 시장 추정 및 예측 : 지역별, 2021-2034
- 주요 동향
- 북미
- 미국
- 캐나다
- 유럽
- 독일
- 영국
- 프랑스
- 이탈리아
- 스페인
- 러시아
- 북유럽 국가
- 아시아태평양
- 중국
- 인도
- 일본
- 호주
- 한국
- 필리핀
- 인도네시아
- 라틴아메리카
- 브라질
- 멕시코
- 아르헨티나
- 중동 및 아프리카
- 남아프리카
- 사우디아라비아
- 아랍에미리트(UAE)
제11장 기업 프로파일
- 세계 기업
- Argus Cyber Security
- Blackberry
- Bosch
- BT Group
- Cisco Systems
- Continental
- Denso
- ESCRYPT
- Harman International
- Intel
- Irdeto Automotive
- Karamba Security
- Lear Corporation
- Microsoft
- NXP Semiconductors
- Symantec
- Trillium Secure
- Vector Informatik
- 지역 기업
- Aptiv
- Eneos Cyber Solutions
- Intertek
- OneLayer
- SafeRide Technologies
- Tuxera Automotive
- 신규 기업
- Arilou Technologies
- AutoCrypt
- GuardKnox
- Karamba Security
- Keen Security Lab
- Upstream Security
The global automotive cybersecurity market was estimated at USD 3.52 billion in 2024. The market is expected to grow from USD 3.87 billion in 2025 to USD 10.42 billion by 2034 at a CAGR of 11.6%, according to latest report published by Global Market Insights Inc.
As vehicles become increasingly connected via V2X (vehicle-to-everything) communications and embedded infotainment systems, the attack surface for hackers grows significantly. This pushes automakers to invest in robust cybersecurity solutions to protect real-time data exchange, vehicle networks, and digital systems.
| Market Scope | |
|---|---|
| Start Year | 2024 |
| Forecast Year | 2025-2034 |
| Start Value | $3.52 Billion |
| Forecast Value | $10.42 Billion |
| CAGR | 11.6% |
Rising demand in Passenger Vehicle
The passenger vehicle segment in the automotive cybersecurity market held sustainable share in 2024, owing to the rapid growth of connected cars, infotainment systems, and autonomous driving technologies. As consumers expect smarter, safer, and more digital driving experiences, automakers are integrating advanced cybersecurity protocols directly into passenger vehicles.
Growing Adoption of In-Vehicle Cybersecurity
In-vehicle cybersecurity segment held substantial share in 2024 driven by the focus on safeguarding electronic control units (ECUs), infotainment systems, telematics, and vehicle networks from external threats. As vehicles increasingly function like mobile computers, in-vehicle cybersecurity ensures real-time threat detection, secure communication, and data integrity. OEMs are now designing security from the ground up, embedding software firewalls, intrusion detection systems, and encryption directly into vehicle hardware and software stacks.
Application to Gain Traction
The application segment in automotive cybersecurity market generated notable revenues in 2024 fueled by telematics and infotainment to ADAS (Advanced Driver Assistance Systems) and powertrain control. Every digital touchpoint inside a modern vehicle needs protection. As the complexity of vehicle architecture grows, cybersecurity applications are being tailored to each system, ensuring end-to-end protection.
North America to Emerge as a Lucrative Region
North America automotive cybersecurity market held robust growth in 2024 driven by strong regulatory backing, tech-savvy consumers, and the presence of leading cybersecurity and automotive innovators. The U.S. sets embedding cyber resilience in mobility solutions. With regulatory frameworks like the U.S. Cybersecurity Executive Order and rising consumer awareness around data privacy, automakers are accelerating investments in robust in-vehicle security systems. Additionally, partnerships between OEMs and major tech firms are fueling new breakthroughs in vehicle security protocols.
Major players in the automotive cybersecurity market are Karamba Security, Lear, Harman International, Denso, Upstream Security, NXP, Blackberry, Aptiv, Continental, Intertek.
Companies in the automotive cybersecurity market are focusing on innovation through extensive R&D to develop cutting-edge security solutions that address emerging threats in connected and autonomous vehicles. Strategic partnerships and collaborations with automakers, technology providers, and regulatory bodies are accelerating product integration and compliance. Many players are investing heavily in real-time threat detection systems and AI-driven cybersecurity frameworks to enhance vehicle safety. Expanding their global footprint through acquisitions and joint ventures is another common tactic to capture new markets and customer segments.
Table of Contents
Chapter 1 Methodology
- 1.1 Research design
- 1.1.1 Research approach
- 1.1.2 Data collection methods
- 1.1.3 GMI proprietary AI system
- 1.1.3.1 AI-Powered research enhancement
- 1.1.3.2 Source consistency protocol
- 1.1.3.3 AI accuracy metrics
- 1.2 Base estimates and calculations
- 1.2.1 Base year calculation
- 1.3 Forecast model
- 1.3.1 Key trends for market estimates
- 1.3.2 Quantified market impact analysis
- 1.3.2.1 Mathematical impact of growth parameters on forecast
- 1.3.3 Scenario Analysis Framework
- 1.4 Primary research & validation
- 1.5 Some of the primary sources (but not limited to)
- 1.6 Data mining sources
- 1.6.1 Secondary
- 1.6.1.1 Paid Sources
- 1.6.1.2 Public Sources
- 1.6.1.3 Sources, by region
- 1.6.1 Secondary
- 1.7 Research Trail & Confidence Scoring
- 1.7.1 Research Trail Components:
- 1.7.2 Scoring Components
- 1.8 Research transparency addendum
- 1.8.1 Source attribution framework
- 1.8.2 Quality assurance metrics
- 1.8.3 Our commitment to trust
Chapter 2 Executive Summary
- 2.1 Industry 3600 synopsis, 2021 - 2034
- 2.2 Key market trends
- 2.2.1 Regional
- 2.2.2 Vehicle
- 2.2.3 Security
- 2.2.4 Form
- 2.2.5 Application
- 2.2.6 Deployment Mode
- 2.3 TAM Analysis, 2025-2034
- 2.4 CXO perspectives: Strategic imperatives
- 2.4.1 Executive decision points
- 2.4.2 Critical success factors
- 2.5 Future outlook and strategic recommendations
Chapter 3 Industry Insights
- 3.1 Industry ecosystem analysis
- 3.1.1 Supplier landscape
- 3.1.1.1 Automotive OEM
- 3.1.1.2 Cybersecurity solution providers
- 3.1.1.3 Cloud service providers
- 3.1.1.4 Tier 1 Suppliers
- 3.1.1.5 Technology integrators
- 3.1.1.6 End use
- 3.1.2 Profit margin analysis
- 3.1.3 Cost structure
- 3.1.4 Value addition at each stage
- 3.1.5 Factor affecting the value chain
- 3.1.6 Disruptions
- 3.1.1 Supplier landscape
- 3.2 Industry impact forces
- 3.2.1 Growth drivers
- 3.2.1.1 Growing connected vehicle adoption
- 3.2.1.2 Strict cybersecurity regulations for automotive manufacturers
- 3.2.1.3 Growing complexity of vehicle architecture
- 3.2.1.4 Proliferation of Over-the-Air Updates
- 3.2.2 Industry pitfalls and challenges
- 3.2.2.1 Cost constraints in the implementation of cybersecurity solutions
- 3.2.2.2 Legacy system integration
- 3.2.3 Market opportunities
- 3.2.3.1 Rising connected vehicle adoption
- 3.2.3.2 Shift toward software-defined vehicles
- 3.2.3.3 Regulatory push and compliance standards
- 3.2.3.4 Expansion of EVs and autonomous vehicles
- 3.2.1 Growth drivers
- 3.3 Regulatory landscape
- 3.3.1 North America
- 3.3.2 Europe
- 3.3.3 Asia Pacific
- 3.3.4 Latin America
- 3.3.5 Middle East & Africa
- 3.4 Porter's analysis
- 3.5 PESTEL analysis
- 3.6 Technology and Innovation landscape
- 3.6.1 Current technological trends
- 3.6.1.1 Traditional security approaches and limitations
- 3.6.1.2 Next-generation security architecture
- 3.6.1.3 Integration with automotive development processes
- 3.6.2 Emerging technologies
- 3.6.2.1 Artificial intelligence and machine learning applications
- 3.6.2.2 Behavioral analytics and anomaly detection
- 3.6.2.3 Blockchain for secure vehicle communications
- 3.6.2.4 Quantum computing impact on cryptography
- 3.6.3 Zero trust security architecture
- 3.6.3.1 Implementation of strategies for automotive systems
- 3.6.3.2 Network segmentation and micro-segmentation
- 3.6.3.3 Identity and access management (IAM) solutions
- 3.6.4 Software-defined vehicle (SDV) security
- 3.6.4.1 Security-by-design principles
- 3.6.4.2 Continuous security monitoring
- 3.6.4.3 Dynamic security policy management
- 3.6.5 Future technology disruptions (2025-2034)
- 3.6.5.1 Quantum-resistant cryptography implementation
- 3.6.5.2 6G network security requirements
- 3.6.5.3 Edge computing security challenges
- 3.6.5.4 Autonomous vehicle security evolution
- 3.6.6 Technology Readiness Level (TRL) Assessment
- 3.6.6.1 Current technology maturity analysis
- 3.6.6.2 Commercialization timeline projections
- 3.6.6.3 Investment requirements and ROI analysis
- 3.6.1 Current technological trends
- 3.7 Patent analysis
- 3.8 Pricing trends and economic analysis
- 3.9 Cost Analysis and ROI Assessment
- 3.9.1 Cybersecurity investment analysis
- 3.9.2 CSMS implementation cost assessment
- 3.9.3 Incident cost impact analysis
- 3.9.4 Regional cost variations
- 3.9.5 Cost optimization strategies
- 3.9.6 Financial risk assessment
- 3.10 Threat intelligence and attack analysis
- 3.10.1 Current threat landscape assessment
- 3.10.2 Attack vector classification and analysis
- 3.10.3 Critical system vulnerabilities
- 3.10.4 Advanced persistent threat (APT) analysis
- 3.10.5 Incident response and forensics capabilities
- 3.10.6 Threat intelligence sharing and collaboration
- 3.11 Use cases
- 3.12 Investment landscape and funding analysis
- 3.13 Cost-benefit analysis
- 3.14 Best-case scenario
Chapter 4 Competitive Landscape, 2024
- 4.1 Introduction
- 4.2 Company market share analysis
- 4.2.1 North America
- 4.2.2 Europe
- 4.2.3 Asia Pacific
- 4.2.4 LATAM
- 4.2.5 MEA
- 4.3 Competitive analysis of major market players
- 4.4 Competitive positioning matrix
- 4.5 Strategic outlook matrix
- 4.6 Key developments
- 4.6.1 Mergers & acquisitions
- 4.6.2 Partnerships & collaborations
- 4.6.3 New Product Launches
- 4.6.4 Expansion Plans and funding
Chapter 5 Market Estimates & Forecast, By Vehicle, 2021 - 2034 ($Bn)
- 5.1 Key trends
- 5.2 Passenger vehicles
- 5.2.1 Hatchback
- 5.2.2 Sedan
- 5.2.3 SUV
- 5.3 Commercial vehicle
- 5.3.1 Light commercial vehicle (LCVs)
- 5.3.2 Medium commercial vehicle (MCVs)
- 5.3.3 Heavy commercial vehicle (HCVs)
Chapter 6 Market Estimates & Forecast, By Security, 2021 - 2034 ($Bn)
- 6.1 Key trends
- 6.2 Application
- 6.3 Network
- 6.4 Endpoint
Chapter 7 Market Estimates & Forecast, By Deployment Mode, 2021 - 2034 ($Bn)
- 7.1 Key trends
- 7.2 Cloud-based
- 7.3 On-premises
- 7.4 Hybrid
Chapter 8 Market Estimates & Forecast, By Application, 2021 - 2034 ($Bn)
- 8.1 Key trends
- 8.2 ADAS & safety
- 8.3 Body control & comfort
- 8.4 Infotainment
- 8.5 Telematics
- 8.6 Powertrain systems
- 8.7 Communication systems
Chapter 9 Market Estimates & Forecast, By Form, 2021 - 2034 ($Bn)
- 9.1 Key trends
- 9.2 In-vehicle cybersecurity
- 9.3 External cloud cybersecurity
Chapter 10 Market Estimates & Forecast, By Region, 2021 - 2034 ($Bn)
- 10.1 Key trends
- 10.2 North America
- 10.2.1 US
- 10.2.2 Canada
- 10.3 Europe
- 10.3.1 Germany
- 10.3.2 UK
- 10.3.3 France
- 10.3.4 Italy
- 10.3.5 Spain
- 10.3.6 Russia
- 10.3.7 Nordics
- 10.4 Asia Pacific
- 10.4.1 China
- 10.4.2 India
- 10.4.3 Japan
- 10.4.4 Australia
- 10.4.5 South Korea
- 10.4.6 Philippines
- 10.4.7 Indonesia
- 10.5 Latin America
- 10.5.1 Brazil
- 10.5.2 Mexico
- 10.5.3 Argentina
- 10.6 MEA
- 10.6.1 South Africa
- 10.6.2 Saudi Arabia
- 10.6.3 UAE
Chapter 11 Company Profiles
- 11.1 Global Players
- 11.1.1 Argus Cyber Security
- 11.1.2 Blackberry
- 11.1.3 Bosch
- 11.1.4 BT Group
- 11.1.5 Cisco Systems
- 11.1.6 Continental
- 11.1.7 Denso
- 11.1.8 ESCRYPT
- 11.1.9 Harman International
- 11.1.10 Intel
- 11.1.11 Irdeto Automotive
- 11.1.12 Karamba Security
- 11.1.13 Lear Corporation
- 11.1.14 Microsoft
- 11.1.15 NXP Semiconductors
- 11.1.16 Symantec
- 11.1.17 Trillium Secure
- 11.1.18 Vector Informatik
- 11.2 Regional Players
- 11.2.1 Aptiv
- 11.2.2 Eneos Cyber Solutions
- 11.2.3 Intertek
- 11.2.4 OneLayer
- 11.2.5 SafeRide Technologies
- 11.2.6 Tuxera Automotive
- 11.3 Emerging Players
- 11.3.1 Arilou Technologies
- 11.3.2 AutoCrypt
- 11.3.3 GuardKnox
- 11.3.4 Karamba Security
- 11.3.5 Keen Security Lab
- 11.3.6 Upstream Security



















