
|
시장보고서
상품코드
1881238
CIAM(소비자 ID 및 액세스 관리) 시장 : 솔루션별, 서비스별, 인증 유형별, 업계별, 예측(-2030년)Consumer Identity and Access Management (CIAM) Market by Solutions (Identity Administration, PII Management & Analytics, Access Management, Fraud Detection), Services, Authentication Type, and Vertical - Global Forecast to 2030 |
||||||
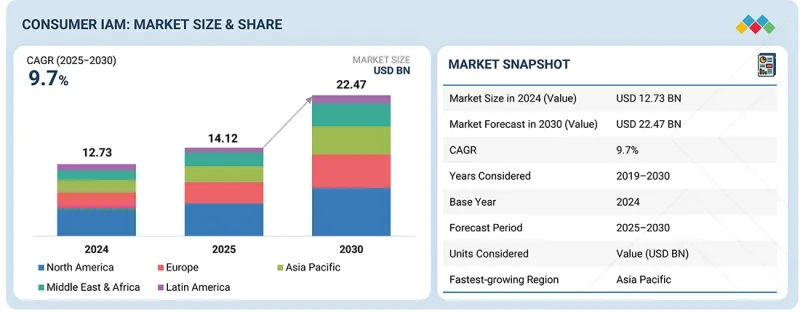
세계 CIAM(소비자 ID 및 액세스 관리) 시장 규모는 2025년 141억 2,000만 달러, 2030년까지 224억 7,000만 달러에 이를 것으로 예측되며, 예측 기간에 CAGR 9.7%로 성장할 것으로 예상됩니다.
| 조사 범위 | |
|---|---|
| 조사 기간 | 2019-2030년 |
| 기준 연도 | 2024년 |
| 예측 기간 | 2025-2030년 |
| 단위 | 100만/10억 달러 |
| 부문 | 제공, 조직 규모, 산업, 지역 |
| 대상 지역 | 북미, 유럽, 아시아태평양 및 기타 지역 |
CIAM(소비자 ID 및 액세스 관리)의 채택은 보험 및 리스크 관리 요건에 따라 점차 추진되고 있습니다. 조직은 진화하는 사이버 규제 준수, 내양자 보상 기준 대응, 잠재적인 책임 경감, 기밀성이 높고 중요한 데이터의 장기적인 보호를 확보하고 향후 양자 기술을 활용한 사이버 공격 및 침해에 대한 노출을 줄이는 것을 목표로 하고 있습니다.

업계별로 BFSI 부문은 가장 큰 시장 점유율을 차지합니다.
BFSI 부서는 디지털 뱅킹과 모바일 결제의 시작, 고객 데이터의 안전한 취급에 관한 규제 요건에 따라 CIAM(소비자 ID 및 액세스 관리)시장에서 가장 큰 업계가 되고 있습니다. 금융기관은 GDPR(EU 개인정보보호규정), PSD2, KYC/AML 요건 등의 틀에 대한 준거를 확보하면서 ID 도난, 부정행위, 무단 액세스에 대항하기 위해 CIAM(소비자 ID 및 액세스 관리) 플랫폼에 대한 의존도를 높이고 있습니다. 2024년 IBM Security 보고서에 따르면 금융 서비스 부서는 전 세계 데이터 침해의 18%를 차지하고 있으며, 취약점이 높아졌습니다. 은행 및 핀테크 기업은 적응 인증, AI 기반 행동 분석, 생체 인증을 통합하여 원활하고 안전한 사용자 경험을 제공합니다. 예를 들어, HSBC는 Ping Identity의 CIAM(소비자 ID 및 액세스 관리) 솔루션을 채택하여 고객 ID 관리를 중앙 집중화하고 디지털 채널 전반에 걸친 다중 요소 인증을 강화하고 컴플라이언스와 고객 신뢰를 모두 향상 시켰습니다. BFSI 부문에서 개방형 뱅킹과 디지털 변환에 대한 지속적인 노력은 전 세계 금융 네트워크 전반에 걸쳐 CIAL을 마찰 없는 컴플라이언스를 준수하는 확장 가능한 ID 생태계를 실현하는 데 필수적입니다.
서비스 부문이 예측 기간에 가장 높은 성장률을 보여줄 전망입니다.
서비스 부문은 CIAM(소비자 ID 및 액세스 관리) 시장에서 가장 빠르게 성장하는 카테고리이며, 전문가 중심의 도입과 지속적인 플랫폼 최적화에 대한 기업 수요 증가가 이를 촉진하고 있습니다. 여기에는 통합, 배포, 지원 및 유지보수, 컨설팅 서비스가 포함되어 원활한 채택, 시스템 상호 운용성, 규제 준수를 보장합니다. 조직이 레거시 ID 시스템을 현대화함에 따라 클라우드와 하이브리드 인프라 간의 전문적인 통합 요구가 크게 증가하고 있습니다. 지속적인 유지보수 서비스는 진화하는 보안 위협에 대응하고 대규모 고객 데이터베이스를 효율적으로 관리하는 데 필수적입니다. 예를 들어, CIAM(소비자 ID 및 액세스 관리) 플랫폼을 채택한 기업은 인증 프레임워크의 커스터마이징과 위협의 실시간 모니터링을 관리 서비스 제공업체에 위탁하는 경우가 많습니다. BFSI, 소매 및 의료 부문의 급속한 디지털 변환은 확장 가능하고 안전하며 지속적으로 관리되는 CIAM(소비자 ID 및 액세스 관리) 서비스에 대한 수요를 더욱 가속화하고 있습니다.
"지역별로는 북미가 최대 시장 규모를 차지할 것으로 추정됩니다."
북미는 급속한 디지털 변환, 강력한 규제 집행, 안전하고 원활한 고객 ID 경험에 대한 수요가 증가함에 따라 CIAM(소비자 ID 및 액세스 관리) 솔루션의 가장 큰 시장입니다. 이 지역에서는 ID 사기 문제가 심각해지고 있으며, 미국 연방거래위원회(FTC) 보고서에 따르면 2024년에는 110만 건이 넘는 ID 도난 사건이 발생하고 있으며, 이는 금융, 소매, 의료 부문에서 지속적인 위협을 반영하고 있습니다. 조직은 이러한 위험을 완화하면서 고객의 편의성을 높이기 위해 적응 인증, 생체 인증 및 행동 분석을 특징으로 하는 AI에 의해 강화된 CIAM(소비자 ID 및 액세스 관리) 솔루션의 채택을 가속화하고 있습니다.
이 보고서는 전 세계 CIAM(소비자 ID 및 액세스 관리) 시장에 대한 조사 분석을 통해 주요 촉진요인 및 억제요인, 경쟁 구도, 미래 동향 등의 정보를 제공합니다.
자주 묻는 질문
목차
제1장 서론
제2장 주요 요약
제3장 중요한 인사이트
- CIAM(소비자 ID 및 액세스 관리) 시장의 기업에게 매력적인 기회
- CIAM(소비자 ID 및 액세스 관리) 시장 : 제공별
- CIAM(소비자 ID 및 액세스 관리) 시장 : 솔루션별
- CIAM(소비자 ID 및 액세스 관리) 시장 : 서비스별
- CIAM(소비자 ID 및 액세스 관리) 시장 : 전개 방식별
- CIAM(소비자 ID 및 액세스 관리) 시장 : 인증 유형별
- CIAM(소비자 ID 및 액세스 관리) 시장 : 조직 규모별
- CIAM(소비자 ID 및 액세스 관리) 시장 : 업계별
- CIAM(소비자 ID 및 액세스 관리) 시장 : 지역별
제4장 시장 개요와 업계 동향
- 소개
- 시장 역학
- 성장 촉진요인
- 억제요인
- 기회
- 과제
- 연계 시장 및 교차 산업 기회
- BFSI
- 접객
- 의료
- 소매 및 E-Commerce
- 통신
- Tier 1/2/3 기업의 전략적 움직임
제5장 업계 동향
- Porter's Five Forces 분석
- 거시경제지표
- 소개
- GDP의 동향과 예측
- 세계 ICT 업계 동향
- 세계 사이버 보안 업계 동향
- 밸류체인 분석
- 생태계 분석
- 가격 설정 분석
- 주요 기업의 평균 판매 가격 동향 : 인증 유형별
- 참고 가격 분석 : 벤더별
- 무역 분석
- 수입 시나리오(HS 코드 8471)
- 수출 시나리오(HS 코드 8471)
- 고객사업에 영향을 주는 동향과 혼란
- 주요 컨퍼런스 및 이벤트(2025년-2026년)
- 투자 및 자금조달 시나리오
- 사례 연구 분석
- 2025년 미국 관세의 영향 - CIAM(소비자 ID 및 액세스 관리) 시장
- 소개
- 주요 관세율
- 가격의 영향 분석
- 국가/지역에 미치는 영향
- 업계
제6장 전략적 변혁 : 특허, 디지털, AI 채택
- 주요 신기술
- AI/머신러닝
- 생체인증
- 블록체인
- 보완 기술
- 클라우드 컴퓨팅
- 애플리케이션 프로그래밍 인터페이스(API)
- 인증
- 기술/제품 로드맵
- 특허 분석
- 미래의 용도
- AI에 의한 본인 확인과 행동 인증
- 패스워드리스 인증 생태계
- 분산형 ID와 검증 가능한 자격 정보
- 프라이버시 보호 동의와 데이터 거버넌스
- IoT·엣지 베이스 환경용 CIAM(소비자 ID 및 액세스 관리)
- 생성형 AI
- CIAM(소비자 ID 및 액세스 관리) 시장의 주요 이용 사례와 시장의 장래성
- 주요 이용 사례
- CIAM(소비자 ID 및 액세스 관리) 시장의 모범 사례
- CIAM(소비자 ID 및 액세스 관리)의 AI 도입 사례 연구
- 상호접속된 인접 생태계와 시장 기업에 미치는 영향
- CIAM(소비자 ID 및 액세스 관리) 솔루션 시장에서 생성형 AI 채택에 대한 고객의 준비 상황
제7장 규제 상황
제8장 소비자 정세와 구매 행동
- 의사결정 프로세스
- 주요 이해관계자와 구매 기준
- 채택 장벽과 내부 과제
- 다양한 최종 이용 산업으로부터의 미충족 요구
제9장 CIAM(소비자 ID 및 액세스 관리) 시장 : 제공별
- 소개
- 솔루션
- 서비스
제10장 CIAM(소비자 ID 및 액세스 관리) 시장 : 인증 유형별
- 소개
- MFA
- SSO
- 패스워드리스 인증
제11장 CIAM(소비자 ID 및 액세스 관리) 시장 : 전개 방식별
- 소개
- 클라우드
- On-Premise
- 하이브리드
제12장 CIAM(소비자 ID 및 액세스 관리) 시장 : 조직 규모별
- 소개
- 중소기업
- 대기업
제13장 CIAM(소비자 ID 및 액세스 관리) 시장 : 업계별
- 소개
- BFSI
- 접객
- 의료
- 소매 및 E-Commerce
- 통신
- 교육
- 정부
- 에너지·유틸리티
- 제조
- I게이밍
- 기타 산업
제14장 CIAM(소비자 ID 및 액세스 관리) 시장 : 지역별
- 소개
- 북미
- 미국
- 캐나다
- 유럽
- 영국
- 독일
- 프랑스
- 이탈리아
- 기타 유럽
- 아시아태평양
- 중국
- 일본
- 인도
- 싱가포르
- 기타 아시아태평양
- 중동 및 아프리카
- GCC
- 남아프리카
- 기타 중동 및 아프리카
- 라틴아메리카
- 브라질
- 멕시코
- 기타 라틴아메리카
제15장 경쟁 구도
- 개요
- 주요 진입기업의 전략/강점
- 수익 분석
- 시장 점유율 분석
- 브랜드 비교
- IBM
- OKTA
- SAP
- MICROSOFT
- PING IDENTITY
- 기업 평가 및 재무 지표
- 기업 평가 매트릭스 : 주요 기업(2024년)
- 기업 평가 매트릭스 : 스타트업/중소기업(2024년)
- 경쟁 시나리오와 동향
제16장 기업 프로파일
- 주요 기업
- IBM
- OKTA
- SAP
- MICROSOFT
- PING IDENTITY
- THALES
- BROADCOM
- AWS
- SALESFORCE
- OPENTEXT
- AKAMAI TECHNOLOGIES
- DELOITTE
- HID GLOBAL
- CYBERARK
- NEVIS SECURITY
- 기타 주요 기업
- SIMEIO SOLUTIONS
- UBISECURE
- ONELOGIN
- SECUREAUTH
- LOGINRADIUS
- OMADA IDENTITY
- WSO2
- WIDASCONCEPTS
- FUSIONAUTH
- TRANSMIT SECURITY
- IDNOW
- MINIORANGE
- STRIVACITY
제17장 조사 방법
제18장 부록
SHW 25.12.11The global consumer IAM market size is projected to grow from USD 14.12 billion in 2025 to USD 22.47 billion by 2030 at a Compound Annual Growth Rate (CAGR) of 9.7% during the forecast period.
| Scope of the Report | |
|---|---|
| Years Considered for the Study | 2019-2030 |
| Base Year | 2024 |
| Forecast Period | 2025-2030 |
| Units Considered | Value (USD Million/USD Billion) |
| Segments | By Offering, Organization Size, Vertical, and Region |
| Regions covered | North America, Europe, Asia Pacific, and Rest of the World |
The adoption of CIAM is increasingly driven by insurance and risk management requirements, as organizations aim to comply with evolving cyber regulations, satisfy quantum-resilient coverage standards, mitigate potential liabilities, and ensure the long-term protection of sensitive and critical data, thereby reducing exposure to future quantum-enabled cyberattacks and breaches.
"By vertical, the BFSI segment accounts for the largest market share."
The BFSI sector represents the largest vertical in the Consumer Identity and Access Management (CIAM) market, driven by the rise of digital banking, mobile payments, and regulatory mandates for secure customer data handling. Financial institutions are increasingly relying on CIAM platforms to combat identity theft, fraud, and unauthorized access, while ensuring compliance with frameworks such as GDPR, PSD2, and KYC/AML requirements. According to a 2024 IBM Security report, the financial services sector accounts for 18% of all data breaches globally, underscoring its heightened vulnerability. Banks and fintech firms are integrating adaptive authentication, AI-based behavioral analytics, and biometric verification to deliver seamless yet secure user experiences. For instance, HSBC adopted Ping Identity's CIAM solution to centralize customer identity management and strengthen multi-factor authentication across digital channels, improving both compliance and customer trust. The BFSI sector's continued push toward open banking and digital transformation makes CIAM indispensable for enabling frictionless, compliant, and scalable identity ecosystems across global financial networks.
.
By offering, the services segment is expected to account for the highest growth rate during the forecast period."
The services segment is the fastest-growing category in the CIAM market, driven by increasing demand from enterprises for expert-led implementation and continuous platform optimization. It includes integration & deployment, support & maintenance, and consulting services, which ensure smooth adoption, system interoperability, and regulatory compliance. As organizations modernize their legacy identity systems, the need for professional integration with cloud and hybrid infrastructures has increased significantly. Ongoing maintenance services are crucial for addressing evolving security threats and efficiently managing large-scale customer databases. For example, enterprises adopting CIAM platforms often rely on managed service providers to customize authentication frameworks and monitor real-time threats. The rapid digital transformation across the BFSI, retail, and healthcare sectors further accelerates the demand for scalable, secure, and continuously managed CIAM services.
"By region, North America is estimated to account for the largest market size."
North America remains the largest market for CIAM solutions, driven by rapid digital transformation, strong regulatory enforcement, and a growing need for secure and seamless customer identity experiences. The region faces an escalating identity fraud problem, with the US Federal Trade Commission (FTC) reporting over 1.1 million identity theft cases in 2024, reflecting sustained threats across financial, retail, and healthcare sectors. Organizations are increasingly adopting AI-enhanced CIAM solutions that feature adaptive authentication, biometric verification, and behavioral analytics to mitigate these risks while enhancing customer convenience. For instance, Wells Fargo deployed an AI-powered CIAM framework to strengthen fraud detection and reduce account takeover incidents across digital banking channels. The widespread use of cloud-based CIAM services, supported by high enterprise cloud maturity in the US and Canada, continues to fuel growth as businesses transition to passwordless, compliance-ready identity systems. Furthermore, privacy regulations such as CCPA and Quebec's Law 25 are compelling enterprises to invest in solutions that ensure transparency, consent management, and regulatory adherence, solidifying North America's leadership in the CIAM landscape.
Breakdown of primaries
The study draws insights from a range of industry experts, including component suppliers, Tier 1 companies, and OEMs. The break-up of the primaries is as follows:
- By Company Type: Tier 1 - 43%, Tier 2 - 36%, and Tier 3 - 21%
- By Designation: C-level Executives - 58%, Directors - 32% and Other Levels - 10%
- By Region: North America - 55%, Asia Pacific - 12%, Europe - 19%, Middle East and Africa - 9%, Latin America - 5%
The key players in the consumer IAM market include are IBM (US), Okta (US), SAP (US), Microsoft (US), Ping Identity (US), Thales (France), Broadcom (US), AWS (US), Salesforce (US), OpenText (Canada), Akamai Technology (US), Deloitte (UK), HID Global (US), CyberArk (US), Nevis Security (Switzerland), Simeio Solutions (US), Ubisecure (Finland), OneLogin (US), SecureAuth (US), LoginRadius (Canada), IDology (US), Omada Identity (Denmark), WSO2 (US), WidasConcepts (Germany), FusionAuth (US), Transmit Security (Israel), IDnow (Germany), MiniOrange (US), Strivacity (US), and others.
The study includes an in-depth competitive analysis of the key players in the consumer IAM market, their company profiles, recent developments, and key market strategies.
Research Coverage
The report segments the consumer IAM market and forecasts its size By Offering: Solutions (Identity Administration, PII Management and Analytics, Access Management, Fraud Detection, Others), Services (Integration and Deployment, Support and Maintenance, Consulting), By Authentication Type: Multi Factor Authentication, SSO, Passwordless Authentication, By Deployment Mode: Cloud, On-premises, Hybrid, By Organization Size: SMBs, Large Enterprises, By Vertical: BFSI, Hospitality, Healthcare, Retail and E-commerce, Telecommunications, Education, Government, Energy and Utilities, Manufacturing, iGaming, Other Verticals, and Region (North America, Europe, Asia Pacific, Middle East & Africa, and Latin America). The study also includes an in-depth competitive analysis of the market's key players, their company profiles, key observations related to product and business offerings, recent developments, and key market strategies.
Key Benefits of Buying the Report
The report will help market leaders and new entrants with information on the closest approximations of the revenue numbers for the overall Consumer IAM market and its subsegments. It will also help stakeholders understand the competitive landscape and gain more insights into better positioning their businesses and plan suitable go-to-market strategies. The report also helps stakeholders understand the market pulse and provides information on key market drivers, restraints, challenges, and opportunities.
The report provides insights into the following pointers:
- Analysis of key drivers (Rising security breaches and cyberattacks, Growing demand for frictionless customer experiences, Rising identity theft and fraud, Increasing concern about access privileges, Growing emphasis on stringent regulatory compliance, Rise of AI and Machine Learning in Identity Verification), restraints (Lack of identity standards and budgetary constraints, High cost of deployment and maintenance for large enterprise), opportunities (Lack of identity standards and budgetary constraints, High cost of deployment and maintenance for large enterprise), and challenges (Scarcity of skilled cybersecurity professionals, Difficulties in addressing complexity of advanced threats).
- Product Development/Innovation: Detailed insights on upcoming technologies, research & development activities, and product & service launches in the consumer IAM market.
- Market Development: Comprehensive information about lucrative markets - the report analyzes the consumer IAM market across varied regions.
- Market Diversification: Exhaustive information about new products & services, untapped geographies, recent developments, and investments in the consumer IAM market.
- Competitive Assessment: In-depth assessment of market shares, growth strategies, and service offerings of leading players such as IBM (US), Okta (US), SAP (US), Microsoft (US), Ping Identity (US), Thales (France), Broadcom (US), AWS (US), Salesforce (US), OpenText (Canada), Akamai Technology (US), Deloitte (UK), HID Global (US), CyberArk (US), Nevis Security (Switzerland), Simeio Solutions (US), Ubisecure (Finland), OneLogin (US), SecureAuth (US), LoginRadius (Canada), IDlogy (US), Omada Identity (Denmark), WSO2 (US), WidasConcepts (Germany), FusionAuth (US), Transmit Security (Israel), IDnow (Germany), MiniOrange (US), and Strivacity (US).
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 STUDY OBJECTIVES
- 1.2 MARKET DEFINITION
- 1.2.1 INCLUSIONS AND EXCLUSIONS
- 1.3 MARKET SCOPE
- 1.3.1 MARKET SEGMENTATION
- 1.4 YEARS CONSIDERED
- 1.5 CURRENCY CONSIDERED
- 1.6 STAKEHOLDERS
- 1.7 SUMMARY OF CHANGES
2 EXECUTIVE SUMMARY
- 2.1 KEY INSIGHTS AND MARKET HIGHLIGHTS
- 2.2 KEY MARKET PARTICIPANTS: MAPPING OF STRATEGIC DEVELOPMENTS
- 2.3 DISRUPTIVE TRENDS SHAPING MARKET
- 2.4 HIGH-GROWTH SEGMENTS
- 2.5 SNAPSHOT: GLOBAL SIZE AND GROWTH TRENDS
3 PREMIUM INSIGHTS
- 3.1 ATTRACTIVE OPPORTUNITIES FOR PLAYERS IN CONSUMER IAM MARKET
- 3.2 CONSUMER IAM MARKET, BY OFFERING
- 3.3 CONSUMER IAM MARKET, BY SOLUTION
- 3.4 CONSUMER IAM MARKET, BY SERVICE
- 3.5 CONSUMER IAM MARKET, BY DEPLOYMENT MODE
- 3.6 CONSUMER IAM MARKET, BY AUTHENTICATION TYPE
- 3.7 CONSUMER IAM MARKET, BY ORGANIZATION SIZE
- 3.8 CONSUMER IAM MARKET, BY VERTICAL
- 3.9 CONSUMER IAM MARKET, BY REGION
4 MARKET OVERVIEW AND INDUSTRY TRENDS
- 4.1 INTRODUCTION
- 4.2 MARKET DYNAMICS
- 4.2.1 DRIVERS
- 4.2.1.1 Rising security breaches and cyberattacks
- 4.2.1.2 Growing demand for frictionless customer experiences
- 4.2.1.3 Rising identity theft and fraud
- 4.2.1.4 Increasing concern about access privileges
- 4.2.1.5 Growing emphasis on stringent regulatory compliance
- 4.2.1.6 Rise of AI and machine learning in identity verification
- 4.2.2 RESTRAINTS
- 4.2.2.1 Lack of identity standards and budgetary constraints
- 4.2.2.2 High cost of deployment and maintenance for large enterprise
- 4.2.3 OPPORTUNITIES
- 4.2.3.1 High volume of online transactions
- 4.2.3.2 Gradual shift from traditional IAM to consumer IAM
- 4.2.3.3 Proliferation of cloud-based consumer IAM solutions and services
- 4.2.4 CHALLENGES
- 4.2.4.1 Scarcity of skilled cybersecurity professionals
- 4.2.4.2 Difficulties in addressing complexity of advanced threats
- 4.2.1 DRIVERS
- 4.3 INTERCONNECTED MARKETS AND CROSS-SECTOR OPPORTUNITIES
- 4.3.1 BFSI
- 4.3.2 HOSPITALITY
- 4.3.3 HEALTHCARE
- 4.3.4 RETAIL AND E-COMMERCE
- 4.3.5 TELECOMMUNICATIONS
- 4.4 STRATEGIC MOVES BY TIER -1/2/3 PLAYERS
5 INDUSTRY TRENDS
- 5.1 PORTER'S FIVE FORCES ANALYSIS
- 5.1.1 THREAT OF NEW ENTRANTS
- 5.1.2 BARGAINING POWER OF SUPPLIERS
- 5.1.3 BARGAINING POWER OF BUYERS
- 5.1.4 THREAT OF SUBSTITUTES
- 5.1.5 INTENSITY OF COMPETITIVE RIVALRY
- 5.2 MACROECONOMIC INDICATORS
- 5.2.1 INTRODUCTION
- 5.2.2 GDP TRENDS AND FORECAST
- 5.2.3 TRENDS IN GLOBAL ICT INDUSTRY
- 5.2.4 TRENDS IN GLOBAL CYBERSECURITY INDUSTRY
- 5.3 VALUE CHAIN ANALYSIS
- 5.4 ECOSYSTEM ANALYSIS
- 5.5 PRICING ANALYSIS
- 5.5.1 AVERAGE SELLING PRICE TREND OF KEY PLAYERS, BY AUTHENTICATION TYPE
- 5.5.2 INDICATIVE PRICING ANALYSIS, BY VENDOR
- 5.6 TRADE ANALYSIS
- 5.6.1 IMPORT SCENARIO (HS CODE 8471)
- 5.6.2 EXPORT SCENARIO (HS CODE 8471)
- 5.7 TRENDS AND DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- 5.8 KEY CONFERENCES AND EVENTS, 2025-2026
- 5.9 INVESTMENT AND FUNDING SCENARIO
- 5.10 CASE STUDY ANALYSIS
- 5.10.1 FRANKLINCOVEY OPTIMIZED CUSTOMER INTERACTIONS AND DATA PRIVACY WITH SAP CIAM SOLUTIONS
- 5.10.2 THALES CIAM SOLUTION HELPED A.S.R. UNIFY CUSTOMER EXPERIENCE AND ENHANCE SECURITY
- 5.10.3 NEVIS SECURITY HELPED SWISSCOM ENHANCE CORPORATE CUSTOMER EXPERIENCE WITH CIAM SOLUTION
- 5.10.4 SIMEIO AND PING IDENTITY EMPOWERED GLOBAL TRANSPORTATION PROVIDER WITH MODERN CIAM
- 5.11 IMPACT OF 2025 US TARIFF - CONSUMER IAM MARKET
- 5.11.1 INTRODUCTION
- 5.11.2 KEY TARIFF RATES
- 5.11.3 PRICE IMPACT ANALYSIS
- 5.11.4 IMPACT ON COUNTRY/REGION
- 5.11.4.1 North America
- 5.11.4.1.1 US
- 5.11.4.1.2 Canada
- 5.11.4.1.3 Mexico
- 5.11.4.2 Europe
- 5.11.4.2.1 Germany
- 5.11.4.2.2 France
- 5.11.4.2.3 UK
- 5.11.4.3 APAC
- 5.11.4.3.1 China
- 5.11.4.3.2 Japan
- 5.11.4.3.3 India
- 5.11.4.1 North America
- 5.11.5 INDUSTRIES
6 STRATEGIC DISRUPTIONS: PATENTS, DIGITAL, AND AI ADOPTION
- 6.1 KEY EMERGING TECHNOLOGIES
- 6.1.1 AI/ML
- 6.1.2 BIOMETRIC
- 6.1.3 BLOCKCHAIN
- 6.2 COMPLEMENTARY TECHNOLOGIES
- 6.2.1 CLOUD COMPUTING
- 6.2.2 APPLICATION PROGRAMMING INTERFACES (APIS)
- 6.2.3 AUTHENTICATION
- 6.3 TECHNOLOGY/PRODUCT ROADMAP
- 6.4 PATENT ANALYSIS
- 6.5 FUTURE APPLICATIONS
- 6.5.1 AI-DRIVEN IDENTITY VERIFICATION AND BEHAVIORAL AUTHENTICATION
- 6.5.2 PASSWORDLESS AUTHENTICATION ECOSYSTEMS
- 6.5.3 DECENTRALIZED IDENTITY AND VERIFIABLE CREDENTIALS
- 6.5.4 PRIVACY-PRESERVING CONSENT AND DATA GOVERNANCE
- 6.5.5 CIAM FOR IOT AND EDGE-BASED ENVIRONMENTS
- 6.6 GENERATIVE AI
- 6.6.1 TOP USE CASES AND MARKET POTENTIAL IN CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET
- 6.6.2 TOP USE CASES
- 6.6.3 BEST PRACTICES IN CONSUMER IAM MARKET
- 6.6.4 CASE STUDIES OF AI IMPLEMENTATION IN CIAM
- 6.6.5 INTERCONNECTED ADJACENT ECOSYSTEM AND IMPACT ON MARKET PLAYERS
- 6.6.5.1 Identity and Access Management (CIAM)
- 6.6.5.2 Blockchain
- 6.6.5.3 Internet of Things (IoT)
- 6.6.5.4 Cloud Computing
- 6.6.5.5 Big Data Analytics
- 6.6.5.6 Cybersecurity
- 6.6.6 CLIENTS' READINESS TO ADOPT GENERATIVE AI IN CIAM SOLUTIONS MARKET
7 REGULATORY LANDSCAPE
- 7.1 REGIONAL REGULATIONS AND COMPLIANCE
- 7.1.1 INDUSTRY STANDARDS
8 CONSUMER LANDSCAPE & BUYER BEHAVIOR
- 8.1 DECISION-MAKING PROCESS
- 8.2 KEY STAKEHOLDERS AND BUYING CRITERIA
- 8.2.1 KEY STAKEHOLDERS IN BUYING PROCESS
- 8.2.2 BUYING CRITERIA
- 8.3 ADOPTION BARRIERS & INTERNAL CHALLENGES
- 8.4 UNMET NEEDS FROM VARIOUS END-USE INDUSTRIES
9 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING
- 9.1 INTRODUCTION
- 9.1.1 OFFERING: CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 9.2 SOLUTIONS
- 9.2.1 CIAM SOLUTIONS TO OFFER PERSONALIZED EXPERIENCES AND ENHANCE CUSTOMER SATISFACTION
- 9.2.2 IDENTITY ADMINISTRATION
- 9.2.3 PII MANAGEMENT AND ANALYTICS
- 9.2.4 ACCESS MANAGEMENT
- 9.2.5 FRAUD DETECTION
- 9.2.6 OTHER SOLUTIONS
- 9.3 SERVICES
- 9.3.1 SERVICES TO ENSURE SEAMLESS DEPLOYMENT AND MAINTENANCE OF CIAM AMONG BUSINESSES
- 9.3.2 INTEGRATION AND DEPLOYMENT
- 9.3.2.1 Need for Expert Integration and Deployment Services for Robust IAM and Enhanced Security to drive market
- 9.3.3 SUPPORT AND MAINTENANCE
- 9.3.3.1 Support and maintenance services to help guarantee safe and effective CIAM operations
- 9.3.4 CONSULTING
- 9.3.4.1 Consulting services to help safeguard client information and optimize access control
10 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET, BY AUTHENTICATION TYPE
- 10.1 INTRODUCTION
- 10.1.1 AUTHENTICATION TYPE: CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 10.2 MFA
- 10.2.1 NEED TO COMPLY WITH REGULATORY NORMS AND SECURE CONFIDENTIAL DATA NETWORK TO DRIVE MARKET
- 10.3 SSO
- 10.3.1 SSO TO STREAMLINE USER AUTHENTICATION ACROSS ALL APPLICATIONS, SAVING SIGNIFICANT TIME
- 10.4 PASSWORDLESS AUTHENTICATION
- 10.4.1 PASSWORDLESS AUTHENTICATION USES UNIQUE BIOMETRIC ATTRIBUTES AND ELIMINATES NEED TO REMEMBER PASSWORDS
11 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE
- 11.1 INTRODUCTION
- 11.1.1 DEPLOYMENT MODE: CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 11.2 CLOUD
- 11.2.1 ROBUST SECURITY MEASURES AND CONTINUOUS UPDATES TO ENSURE IDENTITY MANAGEMENT REMAINS SECURE AND UP-TO-DATE
- 11.3 ON-PREMISES
- 11.3.1 ON-PREMISE MODEL APPEALS TO ORGANIZATIONS SEEKING MAXIMUM UPTIME AND RELIABILITY
- 11.4 HYBRID
- 11.4.1 DEMAND FOR BUSINESS CONTINUITY AND FAILOVER, SUPPORTED BY HYBRID CIAM'S CLOUD-ON-PREM REDUNDANCY
12 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET, BY ORGANIZATION SIZE
- 12.1 INTRODUCTION
- 12.1.1 ORGANIZATION SIZE: CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 12.1.2 ORGANIZATION SIZE: CHALLENGES AND BENEFITS
- 12.2 SMBS
- 12.2.1 BUDGET CONSTRAINTS TO RESTRAIN ADOPTION OF CIAM SOLUTIONS AMONG SMALL BUSINESSES
- 12.2.2 LOWER MID-MARKET
- 12.2.3 MID-MARKET
- 12.3 LARGE ENTERPRISES
- 12.3.1 REAL-TIME DATA ACCESS, RISK DETECTION, AND COMPLIANCE SOLUTIONS PREFERRED BY LARGER BUSINESSES
13 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL
- 13.1 INTRODUCTION
- 13.1.1 VERTICAL: CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 13.2 BFSI
- 13.2.1 NEED FOR VALUABLE CUSTOMER INSIGHTS, STRONG SECURITY MEASURES, AND REGULATORY COMPLIANCE
- 13.2.2 BANKING
- 13.2.2.1 Need to safeguard sensitive information and ensure security compliance
- 13.2.3 FINANCIAL SERVICES
- 13.2.3.1 Need for robust identity management and enhancing user satisfaction
- 13.2.4 INSURANCE
- 13.2.4.1 Demand for enhanced security and customer experience
- 13.3 HOSPITALITY
- 13.3.1 NEED FOR ENHANCED SECURITY, IMPROVED CUSTOMER EXPERIENCE, AND STREAMLINED OPERATIONS IN HOSPITALITY
- 13.4 HEALTHCARE
- 13.4.1 DEMAND FOR ENHANCED SECURITY, COMPLIANCE, AND PATIENT EXPERIENCE IN HEALTHCARE
- 13.5 RETAIL & ECOMMERCE
- 13.5.1 NEED FOR ENHANCED PERSONALIZATION, ADVANCED SECURITY, AND COMPLIANCE WITH DATA PRIVACY REGULATIONS IN ECOMMERCE
- 13.6 TELECOMMUNICATIONS
- 13.6.1 NEED FOR SECURITY, COMPLIANCE, AND SEAMLESS USER EXPERIENCES IN TELECOMMUNICATIONS
- 13.7 EDUCATION
- 13.7.1 NEED TO SAFEGUARD STUDENT DATA AND ENSURE PRIVACY ON EDUCATIONAL PLATFORMS
- 13.8 GOVERNMENT
- 13.8.1 NEED FOR ENHANCED SECURITY, REGULATORY COMPLIANCE, AND SEAMLESS USER EXPERIENCE AMONG GOVERNMENT AGENCIES
- 13.9 ENERGY & UTILITIES
- 13.9.1 DEMAND FOR ENHANCED SECURITY AND CUSTOMER EXPERIENCE IN ENERGY & UTILITIES
- 13.10 MANUFACTURING
- 13.10.1 NEED FOR ENHANCED SECURITY, EFFICIENCY, AND CUSTOMER INSIGHTS IN MANUFACTURING VERTICAL
- 13.11 IGAMING
- 13.11.1 DEMAND FOR ENHANCED SECURITY AND USER EXPERIENCE ON GAMING PLATFORMS AND SOFTWARE
- 13.12 OTHER VERTICALS
14 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION
- 14.1 INTRODUCTION
- 14.2 NORTH AMERICA
- 14.2.1 US
- 14.2.1.1 Cybercrime threats, regulatory compliance, and technological innovation to fuel market
- 14.2.2 CANADA
- 14.2.2.1 Government initiatives and rigorous data protection laws to foster market growth
- 14.2.1 US
- 14.3 EUROPE
- 14.3.1 UK
- 14.3.1.1 Economic strength, consumer expectations, and regulatory compliance to drive market
- 14.3.2 GERMANY
- 14.3.2.1 Technological growth, regulatory compliance, and cybersecurity concerns to propel market
- 14.3.3 FRANCE
- 14.3.3.1 Growing focus on combating fraud, regulatory compliance, and digital transformation to boost market growth
- 14.3.4 ITALY
- 14.3.4.1 Government initiatives and investment in cybersecurity to drive market
- 14.3.5 REST OF EUROPE
- 14.3.5.1 Norway
- 14.3.5.2 Switzerland
- 14.3.1 UK
- 14.4 ASIA PACIFIC
- 14.4.1 CHINA
- 14.4.1.1 Digital transformation, regulatory measures, and technological advancements to enhance market growth
- 14.4.2 JAPAN
- 14.4.2.1 Rise in security breaches and digital transformation to drive market
- 14.4.3 INDIA
- 14.4.3.1 Increase in security breaches and digital transformation to fuel demand for CIAM solutions
- 14.4.4 SINGAPORE
- 14.4.4.1 Greater focus on digital transformation, enhanced data security, and financial crime prevention to fuel demand for CIAM solutions
- 14.4.5 REST OF ASIA PACIFIC
- 14.4.1 CHINA
- 14.5 MIDDLE EAST & AFRICA
- 14.5.1 GCC
- 14.5.1.1 KSA
- 14.5.1.1.1 Robust legal frameworks and increasing cyber awareness to propel demand for CIAM solutions
- 14.5.1.2 UAE
- 14.5.1.2.1 Advanced technology adoption and heightened cybersecurity needs to propel demand for CIAM solutions
- 14.5.1.3 Rest of GCC countries
- 14.5.1.1 KSA
- 14.5.2 SOUTH AFRICA
- 14.5.2.1 Stringent regulatory requirements, escalating cybercrime threats, and rapid digitization of financial services to propel market
- 14.5.3 REST OF MIDDLE EAST & AFRICA
- 14.5.1 GCC
- 14.6 LATIN AMERICA
- 14.6.1 BRAZIL
- 14.6.1.1 Accelerated digitalization and rising cybercrime to propel demand for CIAM solutions
- 14.6.2 MEXICO
- 14.6.2.1 Increased digitalization and rising instances of identity theft to fuel market
- 14.6.3 REST OF LATIN AMERICA
- 14.6.1 BRAZIL
15 COMPETITIVE LANDSCAPE
- 15.1 OVERVIEW
- 15.2 KEY PLAYER STRATEGIES/RIGHT TO WIN
- 15.3 REVENUE ANALYSIS
- 15.4 MARKET SHARE ANALYSIS
- 15.5 BRAND COMPARISON
- 15.5.1 IBM
- 15.5.2 OKTA
- 15.5.3 SAP
- 15.5.4 MICROSOFT
- 15.5.5 PING IDENTITY
- 15.6 COMPANY VALUATION AND FINANCIAL METRICS
- 15.6.1 COMPANY VALUATION
- 15.6.2 FINANCIAL METRICS
- 15.7 COMPANY EVALUATION MATRIX: KEY PLAYERS, 2024
- 15.7.1 STARS
- 15.7.2 EMERGING LEADERS
- 15.7.3 PERVASIVE PLAYERS
- 15.7.4 PARTICIPANTS
- 15.7.5 COMPANY FOOTPRINT: KEY PLAYERS
- 15.7.5.1 Company footprint
- 15.7.5.2 Offering footprint
- 15.7.5.3 Authentication type footprint
- 15.7.5.4 Vertical footprint
- 15.7.5.5 Regional footprint
- 15.8 COMPANY EVALUATION MATRIX: STARTUPS/SMES, 2024
- 15.8.1 PROGRESSIVE COMPANIES
- 15.8.2 RESPONSIVE COMPANIES
- 15.8.3 DYNAMIC COMPANIES
- 15.8.4 STARTING BLOCKS
- 15.8.5 COMPETITIVE BENCHMARKING: STARTUPS/SMES
- 15.8.5.1 Detailed list of key startups/SMEs
- 15.8.5.2 Competitive benchmarking of key startups/SMEs
- 15.9 COMPETITIVE SCENARIO AND TRENDS
- 15.9.1 PRODUCT LAUNCHES/ENHANCEMENTS
- 15.9.2 DEALS
16 COMPANY PROFILES
- 16.1 KEY PLAYERS
- 16.1.1 IBM
- 16.1.1.1 Business overview
- 16.1.1.2 Products/Solutions/Services offered
- 16.1.1.3 Recent developments
- 16.1.1.3.1 Deals
- 16.1.1.4 MnM view
- 16.1.1.4.1 Key strengths
- 16.1.1.4.2 Strategic choices
- 16.1.1.4.3 Weaknesses and competitive threats
- 16.1.2 OKTA
- 16.1.2.1 Business overview
- 16.1.2.2 Products/Solutions/Services offered
- 16.1.2.3 Recent developments
- 16.1.2.3.1 Product launches/enhancements
- 16.1.2.3.2 Deals
- 16.1.2.4 MnM view
- 16.1.2.4.1 Key strengths
- 16.1.2.4.2 Strategic choices
- 16.1.2.4.3 Weaknesses and competitive threats
- 16.1.3 SAP
- 16.1.3.1 Business overview
- 16.1.3.2 Products/Solutions/Services offered
- 16.1.3.3 Recent developments
- 16.1.3.3.1 Deals
- 16.1.3.4 MnM view
- 16.1.3.4.1 Key strengths
- 16.1.3.4.2 Strategic choices
- 16.1.3.4.3 Weaknesses and competitive threats
- 16.1.4 MICROSOFT
- 16.1.4.1 Business overview
- 16.1.4.2 Products/Solutions/Services offered
- 16.1.4.3 MnM view
- 16.1.4.3.1 Key strengths
- 16.1.4.3.2 Strategic choices
- 16.1.4.3.3 Weaknesses and competitive threats
- 16.1.5 PING IDENTITY
- 16.1.5.1 Business overview
- 16.1.5.2 Products/Solutions/Services offered
- 16.1.5.3 Recent developments
- 16.1.5.3.1 Product launches/enhancements
- 16.1.5.3.2 Deals
- 16.1.5.4 MnM view
- 16.1.5.4.1 Key strengths
- 16.1.5.4.2 Strategic choices
- 16.1.5.4.3 Weaknesses and competitive threats
- 16.1.6 THALES
- 16.1.6.1 Business overview
- 16.1.6.2 Products/Solutions/Services offered
- 16.1.6.3 Recent developments
- 16.1.6.3.1 Product launches/enhancements
- 16.1.6.3.2 Deals
- 16.1.6.3.3 Expansions
- 16.1.7 BROADCOM
- 16.1.7.1 Business overview
- 16.1.7.2 Products/Solutions/Services offered
- 16.1.8 AWS
- 16.1.8.1 Business overview
- 16.1.8.2 Products/Solutions/Services offered
- 16.1.8.3 Recent developments
- 16.1.8.3.1 Deals
- 16.1.9 SALESFORCE
- 16.1.9.1 Business overview
- 16.1.9.2 Products/Solutions/Services offered
- 16.1.9.3 Recent developments
- 16.1.9.3.1 Deals
- 16.1.10 OPENTEXT
- 16.1.10.1 Business overview
- 16.1.10.2 Products/Solutions/Services offered
- 16.1.10.3 Recent developments
- 16.1.10.3.1 Product launches/enhancements
- 16.1.10.3.2 Deals
- 16.1.11 AKAMAI TECHNOLOGIES
- 16.1.11.1 Business overview
- 16.1.11.2 Products/Solutions/Services offered
- 16.1.12 DELOITTE
- 16.1.12.1 Business overview
- 16.1.12.2 Products/Solutions/Services offered
- 16.1.12.3 Recent developments
- 16.1.12.3.1 Deals
- 16.1.13 HID GLOBAL
- 16.1.13.1 Business overview
- 16.1.13.2 Products/Solutions/Services offered
- 16.1.13.3 Recent developments
- 16.1.13.3.1 Deals
- 16.1.14 CYBERARK
- 16.1.14.1 Business overview
- 16.1.14.2 Products/Solutions/Services offered
- 16.1.14.3 Recent developments
- 16.1.14.3.1 Product launches/enhancements
- 16.1.14.3.2 Deals
- 16.1.15 NEVIS SECURITY
- 16.1.15.1 Business overview
- 16.1.15.2 Products/Solutions/Services offered
- 16.1.15.3 Recent developments
- 16.1.15.3.1 Deals
- 16.1.1 IBM
- 16.2 OTHER KEY PLAYERS
- 16.2.1 SIMEIO SOLUTIONS
- 16.2.2 UBISECURE
- 16.2.3 ONELOGIN
- 16.2.4 SECUREAUTH
- 16.2.5 LOGINRADIUS
- 16.2.6 OMADA IDENTITY
- 16.2.7 WSO2
- 16.2.8 WIDASCONCEPTS
- 16.2.9 FUSIONAUTH
- 16.2.10 TRANSMIT SECURITY
- 16.2.11 IDNOW
- 16.2.12 MINIORANGE
- 16.2.13 STRIVACITY
17 RESEARCH METHODOLOGY
- 17.1 RESEARCH DATA
- 17.1.1 SECONDARY DATA
- 17.1.1.1 Key data from secondary sources
- 17.1.2 PRIMARY DATA
- 17.1.2.1 Key data from primary sources
- 17.1.2.2 Breakup of primary profiles
- 17.1.2.3 Key industry insights
- 17.1.1 SECONDARY DATA
- 17.2 DATA TRIANGULATION
- 17.3 MARKET SIZE ESTIMATION
- 17.3.1 TOP-DOWN APPROACH
- 17.3.2 BOTTOM-UP APPROACH
- 17.3.3 MARKET ESTIMATION APPROACHES
- 17.4 MARKET FORECAST
- 17.5 RESEARCH ASSUMPTIONS
- 17.6 RESEARCH LIMITATIONS
18 APPENDIX
- 18.1 DISCUSSION GUIDE
- 18.2 KNOWLEDGESTORE: MARKETSANDMARKETS' SUBSCRIPTION PORTAL
- 18.3 CUSTOMIZATION OPTIONS
- 18.4 RELATED REPORTS
- 18.5 AUTHOR DETAILS



















