
|
시장보고서
상품코드
1901403
ID 및 액세스 관리 시장 : 제공 제품별, 기술별, 유형별, 신원 유형별, 전개 유형별, 업계별, 지역별 - 예측(-2030년)Identity and Access Management Market by Technology (Access Management, Identity Governance & Administration, Privileged Access Management ), Type, Identity Type, Deployment Mode, Vertical - Global Forecast to 2030 |
||||||
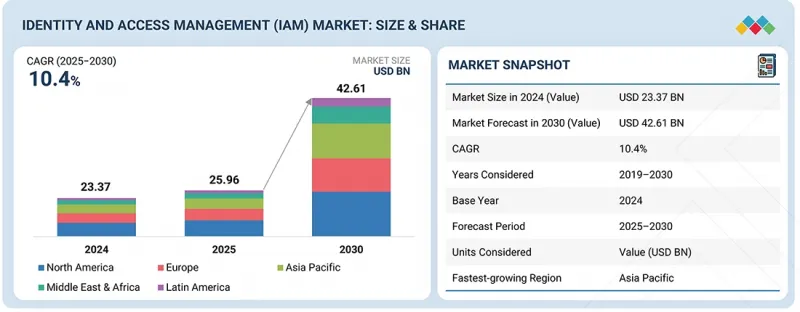
ID 및 액세스 관리(IAM) 시장 규모는 예측 기간 중에 CAGR 10.4%로 성장하여 2025년 259억 6,000만 달러에서 2030년까지 426억 1,000만 달러에 이를 전망입니다.클라우드 컴퓨팅, 제로 트러스트 프레임워크, AI를 활용한 액세스 제어 도입 확대에 의해 적응형 인증, 실시간 위협 감지, 원활한 사용자 프로비저닝이 가능해져, IAM는 변혁을 이루고 있습니다.AI에 의한 이상 감지와 리스크 기반 액세스 제어는 부정 액세스 인시던트를 85% 이상 삭감해, 조직 보안과 컴플라이언스 강화에 기여 하고 있습니다.
| 조사 범위 | |
|---|---|
| 조사 대상 기간 | 2019-2030년 |
| 기준 연도 | 2024년 |
| 예측 기간 | 2025-2030년 |
| 대상 단위 | 가치( 100만 달러/10억 달러) |
| 부문 | 제공 제품별, 기술별, 유형별, 신원 유형별, 전개 유형별, 업계별, 지역별 |
| 대상 지역 | 북미, 유럽, 아시아태평양, 중동 및 아프리카 및 라틴아메리카 |
동시에 다단계 인증(MFA), 싱글 사인온(SSO), 권한 접근 관리(PAM) 솔루션의 도입 확대는 접근 거버넌스 강화, 안전한 온보딩 촉진, 기업 전반의 디지털 전환을 촉진하고 있습니다. 그러나 데이터 프라이버시, 내부자 위협, 잘못된 접근 정책에 대한 우려가 커지면서 광범위한 도입에 대한 주저함이 생겨나고 있습니다. 복잡한 규제 요건과 IAM 모범 사례에 대한 직원들의 인식 부족도 대규모 도입을 더욱 제한하고 있습니다.

소매 및 전자상거래 부문은 계정 탈취, 크리덴셜 스터핑, 내부 위협 증가, 고객 및 직원의 원활한 접근에 대한 수요 증가로 인해 IAM 시장에서 가장 빠른 성장세를 보이고 있습니다. 예를 들어, 전자상거래 플랫폼의 경우 2024년 부정 액세스로 인해 영향을 받은 거래가 평균 2.1%에 달하고, 업계 기준의 20배 이상에 달했습니다. 부정 로그인 시도와 침해된 인증정보가 급증한 것이 그 배경입니다. 한편, 북미 소매업체의 60% 이상이 액세스 관련 보안 사고가 전년 대비 증가했다고 답해 MFA(다단계 인증), SSO(싱글 사인온), AI를 활용한 액세스 분석 도입을 촉진하고 있습니다. 동시에 소비자와 직원은 마찰 없는 로그인 경험과 안전한 원격 액세스를 원하고 있으며, 소매업체는 적응형 인증, 행동 생체 인식, 중앙 집중식 액세스 거버넌스 솔루션에 투자해야 하는 상황에 직면해 있습니다.
IAM 시장의 하이브리드 도입 방식은 On-Premise 제어와 클라우드의 확장성 및 비용 효율성을 결합한 유연성을 원하는 조직에 의해 빠르게 확산되고 있습니다. 하이브리드 IAM 솔루션을 통해 기업은 레거시 시스템과 최신 SaaS 용도에 대한 액세스를 중앙에서 관리할 수 있으며, 일관된 보안 정책과 중앙 집중식 거버넌스를 보장할 수 있습니다. 최근 업계 보고서에 따르면, 하이브리드 IAM 아키텍처 도입 후 78% 이상의 조직에서 액세스 관리 효율성이 개선된 것으로 나타났습니다. 이들 솔루션은 적응형 인증, MFA, SSO를 원활하게 도입할 수 있는 동시에 클라우드 환경으로의 단계적 전환을 지원하기 때문에 On-Premise 전용이나 클라우드 전용 구축보다 범용성이 높다고 할 수 있습니다.
북미는 성숙한 규제 환경, 선진적인 접근 제어의 조기 도입, 강력한 사이버 보안 투자에 힘입어 2025년 IAM 시장에서 가장 큰 점유율을 차지할 것으로 예측됩니다. 연방 및 주정부 차원의 제로 트러스트 프레임워크 추진 정책, NIST 및 GDPR(EU 개인정보보호규정) 준수 표준 준수, 은행, 의료, 소매, 정부 부문의 엔터프라이즈급 IAM 도입은 안전한 액세스, 상호운용성, 위험 감소를 강화합니다. 또한, 광범위한 클라우드 도입, 확립된 IAM 벤더 생태계, 민관 협력을 통한 협력적 노력으로 조직과 사용자 네트워크 전반에 걸쳐 강력한 ID 거버넌스, 안전한 원격 액세스, 확장 가능한 인증 인프라를 보장하고 있습니다.
한편, 아시아태평양에서는 디지털 전환의 가속화, 인터넷 및 모바일 보급률 확대, 정부 주도의 강력한 디지털 ID 이니셔티브에 힘입어 빠른 성장이 예상됩니다. 인도, 일본, 중국, 싱가포르 등의 국가들은 보안 강화와 시민 및 고객 경험 향상을 위해 생체인증, 아이덴티티 페더레이션, 대규모 디지털 ID 프레임워크를 우선적으로 도입하고 있습니다. 하이브리드 업무 환경에서의 안전한 액세스에 대한 수요 증가, 클라우드 도입 증가, AI를 활용한 신원 확인 및 사기 방지를 위한 투자, BFSI(은행, 금융, 보험), 소매, 의료, 정부, IT 및 ITeS(정보 기술 및 IT 관련 서비스) 부문에서 IAM의 확장을 촉진하고 있습니다. 추진하고 있습니다.
주요 조사 대상 내역
IAM 시장의 주요 벤더로는 Microsoft (US), Ping Identity (US), IBM (US), Okta (US), Oracle (US), SailPoint (US), Saviynt (US), CyberArk (US), Thales (France), Akamai Technologies (US), OpenText (Canada), Entrust (US), Duo Security (US), HID Global (US), Evidian (France), RSA Security (US), Avatier (US), ManageEngine (US), SecureAuth (US), EmpowerID (US), Simeio (US), One Identity (US), FusionAuth (US), Auth0 (US), IDnow (Germany), Zuora (US), Signzy (India), Civic Technologies (US), Trusona (US), Beyond Identity (US), Delinea (US), Optimal IdM (US), Netwrix (US), Aquera (US), Cerby (US), Traxion (Netherlands), Radiant Logic (US), Elimity (Belgium), Oleria(US), Veza (US), Bravura Security (Canada), Fischer Identity (US), Lumos (US), Omada (Denmark), OpenIAM (US), Pathlock (US), Tuebora (US), Rippling (US) 등이 있습니다.
IAM 시장의 주요 기업들에 대한 상세한 경쟁 분석, 기업 프로파일, 최근 동향, 주요 시장 전략 등의 정보를 정리하여 전해드립니다.
조사 범위
본 보고서에서는 IAM 시장을 제공 내용(솔루션 및 서비스), 기술(액세스 관리, ID 거버넌스 및 관리(IGA), 권한 접근 관리(PAM), 기타), 유형(직원용 IAM, 소비자 IAM, B2B용 IAM), ID 유형(인간 ID와 비인간 ID), 도입 형태(클라우드, On-Premise, 하이브리드), 산업별(은행, 금융, 보험, 여행, 금융, 보험, 여행사) 등으로 분류하여 조사 분석하였습니다. 인간 아이덴티티와 비인간 아이덴티티), 도입 형태(클라우드, On-Premise, 하이브리드), 산업별(은행-금융-보험(BFSI), 여행-관광-숙박, 의료, 소매-전자상거래, IT-IT서비스, 교육, 정부-국방, 기타)로 시장을 세분화하여 시장 규모를 예측했습니다. 시장을 세분화하여 규모를 예측했습니다.
주요 시장 진입업체에 대한 상세한 경쟁 분석, 기업 프로파일, 제품 및 사업 제공에 대한 주요 관찰 사항, 최근 동향, 주요 시장 전략 등을 조사하여 전해드립니다.
본 보고서 구매의 주요 이점
이 보고서는 시장 리더와 신규 시장 진출기업에게 전체 IAM 시장과 그 하위 부문의 수익 규모에 대한 가장 정확한 추정치를 제공합니다. 이를 통해 이해관계자들은 경쟁 구도를 이해하고, 자사의 포지셔닝을 강화하거나 적절한 시장 진출 전략을 수립하는 데 도움이 되는 귀중한 통찰력을 얻을 수 있습니다. 또한, 시장 동향을 파악하고 주요 시장 성장 촉진요인, 시장 성장 억제요인 및 과제와 기회에 대한 정보를 제공합니다.
자주 묻는 질문
목차
제1장 서론
제2장 주요 요약
제3장 프리미엄 인사이트
제4장 시장 개요
- 시장 역학
- 미충족 요구와 공백
- 연결된 시장과 분야간 기회
- Tier1/2/3 참여 기업의 전략적 움직임
제5장 업계 동향
- Porter의 Five Forces 분석
- 거시경제 지표
- 밸류체인 분석
- 생태계 분석
- 가격 분석
- 무역 분석
- 주요 컨퍼런스 및 이벤트
- 고객의 비즈니스에 영향을 미치는 동향과 혼란
- 투자 및 자금조달 시나리오
- ID 및 액세스 관리 시장 프레임워크
- 신원과 액세스 관리 진화
- 사례 연구 분석
- 2025년 미국 관세의 영향-ID 및 액세스 관리 솔루션 시장
제6장 기술 진보, AI에 의한 영향, 특허, 혁신, 그리고 향후 응용
- 주요 신기술
- 보완적 기술
- 기술/제품 로드맵
- 특허 분석
- 향후 응용
- AI/생성형 AI가 ID 및 액세스 관리 시장에 미치는 영향
- 성공 사례와 실세계에의 응용
제7장 규제 상황
- 지역 규제와 컴플라이언스
- 규제기관, 정부기관 및 기타 조직
- 업계표준
제8장 소비자 동향과 구매 행동
- 의사결정 프로세스
- 구입자 이해관계자와 구입 평가 기준
- 채택 장벽과 내부 과제
- 다양한 최종 이용 산업 미충족 요구
- 시장 수익성
제9장 ID 및 액세스 관리 시장(제공 제품별)
- 솔루션
- 서비스
제10장 ID 및 액세스 관리 시장(기술별)
- 액세스 관리
- 신원 거버넌스 및 관리(IGA)
- 특권 액세스 관리(PAM)
- 기타
제11장 ID 및 액세스 관리 시장(유형별)
- 노동력 IAM
- 소비자 IAM
- B2B IAM
제12장 ID 및 액세스 관리 시장(신원 유형별)
- 인간 신원
- 비인간 신원
제13장 ID 및 액세스 관리 시장(전개 유형별)
- 클라우드
- On-Premise
- 하이브리드
제14장 ID 및 액세스 관리 시장(업계별)
- 은행, 금융서비스 및 보험(BFSI)
- 여행, 관광 및 호스피탈리티
- 건강 관리
- 소매 및 전자상거래
- IT/ITES
- 교육
- 정부 및 방위
- 기타
제15장 ID 및 액세스 관리 시장(지역별)
- 북미
- 북미 : ID 및 액세스 관리 시장 성장 촉진요인
- 미국
- 캐나다
- 유럽
- 유럽 : ID 및 액세스 관리 시장 성장 촉진요인
- 영국
- 독일
- 프랑스
- 이탈리아
- 기타
- 아시아태평양
- 아시아태평양 : ID 및 액세스 관리 시장 성장 촉진요인
- 중국
- 일본
- 인도
- 기타
- 중동 및 아프리카
- 중동 및 아프리카 : ID 및 액세스 관리 시장 성장 촉진요인
- GCC
- 남아프리카공화국
- 기타
- 라틴아메리카
- 라틴아메리카 : ID 및 액세스 관리 시장 성장 촉진요인
- 브라질
- 멕시코
- 기타
제16장 경쟁 구도
- 개요
- 주요 시장 진출기업의 전략/강점
- 매출 분석
- 시장 점유율 분석
- 브랜드 비교
- 기업 평가와 재무 지표
- 기업 평가 매트릭스 : 주요 시장 진출기업, 2024년
- 기업 평가 매트릭스 : 스타트업/중소기업, 2024년
- 경쟁 시나리오와 동향
제17장 기업 개요
- 주요 시장 진출기업
- MICROSOFT
- PING IDENTITY
- IBM
- OKTA
- ORACLE
- SAILPOINT
- SAVIYNT
- CYBERARK
- THALES
- AKAMAI TECHNOLOGIES
- OPENTEXT
- ENTRUST
- DUO SECURITY
- HID GLOBAL
- EVIDIAN
- 기타 주요 기업
- RSA SECURITY
- AVATIER
- MANAGEENGINE
- SECUREAUTH
- EMPOWERID
- SIMEIO
- ONE IDENTITY
- FUSIONAUTH
- AUTH0
- IDNOW
- ZUORA
- SIGNZY
- CIVIC TECHNOLOGIES
- TRUSONA
- BEYOND IDENTITY
- DELINEA
- OPTIMAL IDM
- NETWRIX
- AQUERA
- CERBY
- TRAXION
- RADIANT LOGIC
- ELIMITY
- OLERIA
- VEZA
- BRAVURA SECURITY
- FISCHER IDENTITY
- LUMOS
- OMADA
- OPENIAM
- PATHLOCK
- TUEBORA
- RIPPLING
제18장 조사 방법
제19장 부록
LSH 26.01.15The identity and access management (IAM) market is projected to grow from USD 25.96 billion in 2025 to USD 42.61 billion by 2030 at a compound annual growth rate (CAGR) of 10.4% during the forecast period. The increasing adoption of cloud computing, zero-trust frameworks, and AI-powered access controls is transforming IAM by enabling adaptive authentication, real-time threat detection, and seamless user provisioning. AI-driven anomaly detection and risk-based access controls are helping reduce unauthorized access incidents by over 85%, thus enhancing organizational security and compliance.
| Scope of the Report | |
|---|---|
| Years Considered for the Study | 2019-2030 |
| Base Year | 2024 |
| Forecast Period | 2025-2030 |
| Units Considered | Value (USD Million/USD Billion) |
| Segments | Offering, Technology, Type, Identity Type, Deployment Mode, Vertical, and Region |
| Regions covered | North America, Europe, Asia Pacific, Middle East & Africa, and Latin America |
Simultaneously, the growing implementation of multi-factor authentication (MFA), single sign-on (SSO), and privileged access management (PAM) solutions is strengthening access governance, facilitating secure onboarding, and driving digital transformation across enterprises. However, rising concerns over data privacy, insider threats, and misconfigured access policies are creating hesitation in broader adoption. Complex regulatory requirements and a lack of employee awareness about IAM best practices further constrain large-scale deployment.
"By vertical, the retail & e-commerce segment is projected to register the highest CAGR during the forecast period"
The retail and e-commerce sector is experiencing the fastest growth within the IAM market due to rising instances of account takeovers, credential stuffing, and insider threats, alongside growing demands for seamless customer and employee access. For example, e-commerce platforms reported an average of 2.1% of transactions impacted by unauthorized access in 2024, over twenty times the industry benchmark, with fraudulent login attempts and compromised credentials surging. Meanwhile, over 60% of retailers in North America noted year-on-year increases in access-related security incidents, driving adoption of MFA, SSO, and AI-powered access analytics. Simultaneously, consumers and employees demand frictionless login experiences and secure remote access, prompting retailers to invest in adaptive authentication, behavioral biometrics, and centralized access governance solutions.
"By deployment mode, the hybrid segment is projected to exhibit the highest CAGR during the forecast period"
The IAM market's hybrid deployment mode is experiencing rapid adoption as organizations seek the flexibility of combining on-premises control with cloud scalability and cost efficiency. Hybrid IAM solutions allow enterprises to manage access across both legacy systems and modern SaaS applications, ensuring consistent security policies and centralized governance. According to a recent industry report, over 78% of organizations observed improved access management efficiency after implementing hybrid IAM architectures. These solutions also enable the seamless adoption of adaptive authentication, MFA, and SSO, while supporting a gradual migration to cloud environments, making them more versatile than purely on-premises or cloud-only deployments.
"North America is estimated to have the largest market share in 2025, and Asia Pacific is expected to witness the fastest growth rate during the forecast period"
North America is estimated to hold the largest share of the IAM market in 2025, driven by a mature regulatory environment, early adoption of advanced access controls, and strong cybersecurity investment. Federal and state initiatives promoting zero-trust frameworks, compliance with NIST and GDPR-aligned standards, and enterprise-grade IAM deployments across banking, healthcare, retail, and government sectors have strengthened secure access, interoperability, and risk mitigation. Additionally, widespread cloud adoption, established IAM vendor ecosystems, and coordinated public-private collaborations ensure robust identity governance, secure remote access, and scalable authentication infrastructure across organizations and user networks.
Meanwhile, the Asia Pacific region is expected to witness rapid growth, driven by accelerated digital transformation, expanding internet and mobile penetration, and strong government-led digital identity initiatives. Countries such as India, Japan, China, and Singapore are prioritizing biometric authentication, identity federation, and large-scale digital ID frameworks to strengthen security and improve citizen and customer experiences. Rising demand for secure access in hybrid work environments, increasing cloud adoption, and investments in AI-powered identity verification and fraud prevention are fueling IAM expansion across BFSI, retail, healthcare, government, and IT & ITeS sectors.
Breakdown of Primaries
The study draws insights from various industry experts, including component suppliers, Tier 1 companies, and OEMs. The break-up of the primaries is as follows:
- By Company Type: Tier 1 - 40%, Tier 2 - 35%, and Tier 3 - 25%
- By Designation: C-Level Executives - 35%, Managerial and Other Levels - 65%
- By Region: North America - 15%, Europe - 25%, Asia Pacific - 30%, Middle East & Africa - 20%, Latin America - 10%
Major vendors in the IAM market include Microsoft (US), Ping Identity (US), IBM (US), Okta (US), Oracle (US), SailPoint (US), Saviynt (US), CyberArk (US), Thales (France), Akamai Technologies (US), OpenText (Canada), Entrust (US), Duo Security (US), HID Global (US), Evidian (France), RSA Security (US), Avatier (US), ManageEngine (US), SecureAuth (US), EmpowerID (US), Simeio (US), One Identity (US), FusionAuth (US), Auth0 (US), IDnow (Germany), Zuora (US), Signzy (India), Civic Technologies (US), Trusona (US), Beyond Identity (US), Delinea (US), Optimal IdM (US), Netwrix (US), Aquera (US), Cerby (US), Traxion (Netherlands), Radiant Logic (US), Elimity (Belgium), Oleria(US), Veza (US), Bravura Security (Canada), Fischer Identity (US), Lumos (US), Omada (Denmark), OpenIAM (US), Pathlock (US), Tuebora (US), and Rippling (US).
The study includes an in-depth competitive analysis of the key players in the IAM market, their company profiles, recent developments, and key market strategies.
Research Coverage
The report segments the IAM market and forecasts its size based on offering (solutions and services), technology (access management, identity governance and administration (IGA), privileged access management (PAM), and others), type (workforce IAM, consumer IAM, and B2B IAM), identity type (human identity and non-human identity), deployment mode (cloud, on-premises, and hybrid), and vertical (BFSI, travel, tourism and hospitality, healthcare, retail and e-commerce, IT & ITeS, education, government & defense, and others).
The study also includes an in-depth competitive analysis of the market's key players, their company profiles, key observations related to product and business offerings, recent developments, and key market strategies.
Key Benefits of Buying the Report
The report will help market leaders/new entrants with information on the closest approximations of revenue numbers for the overall IAM market and its subsegments. This report will help stakeholders understand the competitive landscape and gain valuable insights to better position their businesses and plan suitable go-to-market strategies. The report also helps stakeholders understand the market pulse and provides information on key market drivers, restraints, challenges, and opportunities.
The report provides insights into the following pointers:
- Analysis of key drivers (rising instances of security breaches and identity-related fraud; growing awareness about compliance management; cloud-centric transformation fuels need for unified access; increasing need for identity access management solutions for IoT; growing adoption of IAM solutions by SMEs), restraints (lack of identity standards and budgetary constraints in deploying IAM solutions; privacy concerns in IAM adoption; complexity in integrating IAM with legacy systems), opportunities (cultural shift from traditional IAM to CIAM; proliferation of cloud-based IAM solutions and services and growing adoption of hybrid cloud model; increasing integration of technologies into IAM; rising demand for AI-driven and adaptive authentication solutions), and challenges (scarcity of skilled cybersecurity professionals among enterprises; difficulties addressing complexity of advanced threats; interoperability and integration issues across diverse IT environments)
- Product Development/Innovation: Detailed insights into upcoming technologies, research & development activities, and new product & service launches in the IAM market
- Market Development: Comprehensive information about lucrative markets - analysis of the IAM market across varied regions
- Market Diversification: Exhaustive information about new products & services, untapped geographies, recent developments, and investments in the IAM market
- Competitive Assessment: In-depth assessment of market shares, growth strategies, and service offerings of leading players in the IAM market, including Microsoft (US), Ping Identity (US), IBM (US), Okta (US), and Oracle (US).
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 STUDY OBJECTIVES
- 1.2 MARKET DEFINITION
- 1.3 STUDY SCOPE AND SEGMENTATION
- 1.3.1 MARKET SEGMENTATION
- 1.3.2 INCLUSIONS & EXCLUSIONS
- 1.3.3 YEARS CONSIDERED
- 1.3.4 CURRENCY CONSIDERED
- 1.3.5 STAKEHOLDERS
- 1.3.6 SUMMARY OF CHANGES
2 EXECUTIVE SUMMARY
- 2.1 MARKET HIGHLIGHTS AND KEY INSIGHTS
- 2.2 KEY MARKET PARTICIPANTS: MAPPING OF STRATEGIC DEVELOPMENTS
- 2.3 DISRUPTIVE TRENDS SHAPING MARKET
- 2.4 HIGH-GROWTH SEGMENTS
- 2.5 SNAPSHOT: GLOBAL MARKET SIZE, GROWTH RATE, AND FORECAST
3 PREMIUM INSIGHTS
- 3.1 ATTRACTIVE OPPORTUNITIES FOR PLAYERS IN IDENTITY AND ACCESS MANAGEMENT MARKET
- 3.2 IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING
- 3.3 IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE
- 3.4 IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE
- 3.5 IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY
- 3.6 IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE
- 3.7 IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE
- 3.8 IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE
- 3.9 IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL
- 3.10 IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION
4 MARKET OVERVIEW
- 4.1 INTRODUCTION
- 4.2 MARKET DYNAMICS
- 4.2.1 DRIVERS
- 4.2.1.1 Rising instances of security breaches and identity-related fraud
- 4.2.1.2 Growth in awareness about compliance management
- 4.2.1.3 Cloud-centric transformation fuels need for unified access control
- 4.2.1.4 Increase in need for identity access management solutions for IoT
- 4.2.1.5 Growing adoption of IAM solutions by SMEs
- 4.2.2 RESTRAINTS
- 4.2.2.1 Lack of identity standards and budgetary constraints in deploying IAM solutions
- 4.2.2.2 Privacy concerns in IAM adoption
- 4.2.2.3 Complexity in integrating IAM with legacy systems
- 4.2.3 OPPORTUNITIES
- 4.2.3.1 Cultural shift from traditional IAM to customer identity and access management
- 4.2.3.2 Proliferation of cloud-based IAM solutions and services and growing adoption of hybrid cloud model
- 4.2.3.3 Increase in integration of technologies into IAM
- 4.2.3.4 Rise in demand for AI-driven and adaptive authentication solutions
- 4.2.4 CHALLENGES
- 4.2.4.1 Scarcity of skilled cybersecurity professionals among enterprises
- 4.2.4.2 Difficulties addressing complexity of advanced threats
- 4.2.4.3 Interoperability and integration issues across diverse IT environments
- 4.2.1 DRIVERS
- 4.3 UNMET NEEDS AND WHITE SPACES
- 4.4 INTERCONNECTED MARKETS AND CROSS-SECTOR OPPORTUNITIES
- 4.4.1 INTERCONNECTED MARKETS
- 4.4.2 CROSS SECTOR OPPORTUNITIES
- 4.5 STRATEGIC MOVES BY TIER -1/2/3 PLAYERS
- 4.5.1 TIER 1 PLAYERS (MARKET LEADERS)
- 4.5.1.1 Palo Alto Networks
- 4.5.1.2 Ping Identity
- 4.5.1.3 SailPoint
- 4.5.1.4 CyberArk
- 4.5.2 TIER 2 PLAYERS (STRONG CHALLENGERS)
- 4.5.2.1 Saviynt
- 4.5.2.2 Delinea (Thycotic + Centrify Merger)
- 4.5.2.3 Okta
- 4.5.3 TIER 3 PLAYERS (SPECIALISTS & EMERGING ENTRANTS)
- 4.5.3.1 Zilla
- 4.5.3.2 Princeps
- 4.5.4 CROSS-TIER STRATEGIC PATTERNS
- 4.5.5 MARKET IMPLICATIONS
- 4.5.5.1 Consolidation Pressure on Tier-3 Vendors
- 4.5.5.2 Acceleration Imperative for Tier-2 Challengers
- 4.5.5.3 Increased Complexity for Customers
- 4.5.5.4 Integration Burden Driving Platform Adoption
- 4.5.6 STRATEGIC TRENDS
- 4.5.6.1 Cloud-native and SaaS-first IAM solutions
- 4.5.6.2 Zero trust and adaptive security adoption
- 4.5.6.3 Integration of identity governance and PAM
- 4.5.1 TIER 1 PLAYERS (MARKET LEADERS)
5 INDUSTRY TRENDS
- 5.1 PORTER'S FIVE FORCES ANALYSIS
- 5.1.1 THREAT OF NEW ENTRANTS
- 5.1.2 BARGAINING POWER OF SUPPLIERS
- 5.1.3 BARGAINING POWER OF BUYERS
- 5.1.4 THREAT OF SUBSTITUTES
- 5.1.5 INTENSITY OF COMPETITIVE RIVALRY
- 5.2 MACROECONOMIC INDICATORS
- 5.2.1 INTRODUCTION
- 5.2.2 GDP TRENDS AND FORECAST
- 5.2.3 TRENDS IN GLOBAL ICT INDUSTRY
- 5.2.4 TRENDS IN GLOBAL CYBERSECURITY INDUSTRY
- 5.3 VALUE CHAIN ANALYSIS
- 5.3.1 OFFERINGS
- 5.3.2 PLANNING & DESIGNING
- 5.3.3 INFRASTRUCTURE DEPLOYMENT
- 5.3.4 SYSTEM INTEGRATION
- 5.3.5 CONSULTATION
- 5.3.6 END USERS
- 5.4 ECOSYSTEM ANALYSIS
- 5.5 PRICING ANALYSIS
- 5.5.1 AVERAGE SELLING PRICE OF KEY PLAYERS, BY OFFERING
- 5.5.2 INDICATIVE PRICING ANALYSIS, BY KEY PLAYERS
- 5.6 TRADE ANALYSIS
- 5.6.1 IMPORT SCENARIO (HS CODE 8471)
- 5.6.1.1 Overview of import values
- 5.6.1.2 Country-specific trends
- 5.6.1.3 Implications and conclusion
- 5.6.2 EXPORT SCENARIO (HS CODE 8471)
- 5.6.2.1 Overview of export values
- 5.6.2.2 Country-specific trends
- 5.6.2.3 Implications and conclusion
- 5.6.1 IMPORT SCENARIO (HS CODE 8471)
- 5.7 KEY CONFERENCES & EVENTS
- 5.8 TRENDS AND DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- 5.9 INVESTMENT AND FUNDING SCENARIO
- 5.10 IDENTITY AND ACCESS MANAGEMENT MARKET FRAMEWORK
- 5.10.1 AUTHENTICATION SERVICES
- 5.10.2 USER MANAGEMENT SERVICES
- 5.10.3 AUTHORIZATION SERVICES
- 5.10.4 DIRECTORY SERVICES
- 5.10.5 GOVERNANCE FRAMEWORK
- 5.10.6 REPORTING & ANALYTICS
- 5.11 EVOLUTION OF IDENTITY AND ACCESS MANAGEMENT
- 5.11.1 EARLY BEGINNINGS
- 5.11.2 20TH CENTURY DEVELOPMENTS
- 5.11.3 DIGITAL IDENTITY EMERGENCE
- 5.11.4 INTERNET AND DIGITAL REVOLUTION
- 5.11.5 CLOUD AND MANAGED SERVICES
- 5.11.6 DECENTRALIZATION AND ADVANCED TECHNOLOGIES
- 5.11.7 MODERN DEVELOPMENTS AND FUTURE OUTLOOK
- 5.12 CASE STUDY ANALYSIS
- 5.12.1 PAMEIJER ADOPTED PING IDENTITY PLATFORM TO ACHIEVE SINGLE SIGN-ON (SSO) AND MULTI-FACTOR AUTHENTICATION (MFA) FOR EMPLOYEES AND CLIENTS
- 5.12.2 T-MOBILE ADOPTED OKTA IDENTITY CLOUD TO CONCENTRATE ON STRATEGIC GOALS SUCH AS CUTTING COSTS AND IMPROVING CUSTOMER SERVICE
- 5.12.3 WWK ESTABLISHED FORGEROCK-BASED SINGLE SIGN-ON FOR IMPROVED SERVICE AND SECURITY
- 5.12.4 AVANCER HELPED COMMUNITY HOSPITAL WITH SELF-SERVICE ADMINISTRATIVE IT FEATURES TO HELP AUTOMATE ACCESS GOVERNANCE
- 5.12.5 CAREPOINT HEALTH ENHANCES SECURITY AND BOOSTS PRODUCTIVITY WITH MICROSOFT AZURE AD
- 5.12.6 HORIZON REGIONAL HOSPITAL STRENGTHENS CYBERSECURITY AND ENSURES HIPAA COMPLIANCE WITH PALO ALTO NETWORKS
- 5.13 IMPACT OF 2025 US TARIFF - IDENTITY AND ACCESS MANAGEMENT SOLUTIONS MARKET
- 5.13.1 INTRODUCTION
- 5.13.2 KEY TARIFF RATES
- 5.13.3 PRICE IMPACT ANALYSIS
- 5.13.4 IMPACT ON COUNTRY/REGION
- 5.13.4.1 North America
- 5.13.4.2 Europe
- 5.13.4.3 Asia Pacific
- 5.13.5 IMPACT ON END-USE INDUSTRIES
6 TECHNOLOGICAL ADVANCEMENTS, AI-DRIVEN IMPACT, PATENTS, INNOVATIONS, AND FUTURE APPLICATIONS
- 6.1 KEY EMERGING TECHNOLOGIES
- 6.1.1 BIOMETRIC AUTHENTICATION
- 6.1.1.1 Facial recognition
- 6.1.1.2 Finger-vein recognition
- 6.1.1.3 Voice recognition
- 6.1.2 SINGLE SIGN-ON (SSO)
- 6.1.3 MULTI-FACTOR AUTHENTICATION (MFA)
- 6.1.4 IOT AUTHENTICATION
- 6.1.5 DECENTRALIZED IDENTITY (DID) AND SELF-SOVEREIGN IDENTITY (SSI)
- 6.1.1 BIOMETRIC AUTHENTICATION
- 6.2 COMPLEMENTARY TECHNOLOGIES
- 6.2.1 USER AND ENTITY BEHAVIOR ANALYTICS (UEBA)
- 6.2.2 ZERO TRUST SECURITY FRAMEWORK
- 6.2.3 ARTIFICIAL INTELLIGENCE AND MACHINE LEARNING (AI/ML) IN IAM
- 6.3 TECHNOLOGY/PRODUCT ROADMAP
- 6.3.1 SHORT-TERM (2025-2027) | FOUNDATION & EARLY COMMERCIALIZATION
- 6.3.2 MID-TERM (2027-2030) | SCALING, INTEGRATION & INTELLIGENT AUTOMATION
- 6.3.3 LONG-TERM (2030-2035+) | HYPER-AUTOMATION, QUANTUM READINESS & IDENTITY CONVERGENCE
- 6.4 PATENT ANALYSIS
- 6.5 FUTURE APPLICATIONS
- 6.5.1 AI-POWERED CONTEXTUAL ACCESS INTELLIGENCE
- 6.5.2 NEXT-GENERATION PASSWORDLESS & BIOMETRIC AUTHENTICATION
- 6.5.3 ZERO TRUST & CONTINUOUS AUTHENTICATION
- 6.5.4 DECENTRALIZED IDENTITY & BLOCKCHAIN IAM
- 6.5.5 IDENTITY GOVERNANCE FOR HYBRID/CLOUD ENVIRONMENTS
- 6.6 IMPACT OF AI/GEN AI ON IDENTITY AND ACCESS MANAGEMENT MARKET
- 6.6.1 BEST PRACTICES IN IDENTITY AND ACCESS MANAGEMENT MARKET
- 6.6.2 CASE STUDIES OF AI IMPLEMENTATION IN IDENTITY AND ACCESS MANAGEMENT MARKET
- 6.6.3 INTERCONNECTED ADJACENT ECOSYSTEM AND IMPACT ON MARKET PLAYERS
- 6.6.4 CLIENTS' READINESS TO ADOPT GENERATIVE AI IN IDENTITY AND ACCESS MANAGEMENT MARKET
- 6.7 SUCCESS STORIES AND REAL-WORLD APPLICATIONS
- 6.7.1 OKTA: ADAPTIVE ACCESS & MFA DEPLOYMENT
- 6.7.2 MICROSOFT: ENTRA VERIFIED ID AT CONDATIS
7 REGULATORY LANDSCAPE
- 7.1 REGIONAL REGULATIONS AND COMPLIANCE
- 7.1.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- 7.1.2 INDUSTRY STANDARDS
8 CONSUMER LANDSCAPE & BUYER BEHAVIOR
- 8.1 DECISION-MAKING PROCESS
- 8.2 BUYER STAKEHOLDERS AND BUYING EVALUATION CRITERIA
- 8.2.1 KEY STAKEHOLDERS IN BUYING PROCESS
- 8.2.2 BUYING CRITERIA
- 8.3 ADOPTION BARRIERS & INTERNAL CHALLENGES
- 8.4 UNMET NEEDS IN VARIOUS END-USE INDUSTRIES
- 8.5 MARKET PROFITABILITY
- 8.5.1 REVENUE POTENTIAL
- 8.5.2 COST DYNAMICS
- 8.5.3 MARGIN OPPORTUNITIES IN KEY APPLICATIONS
9 IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING
- 9.1 INTRODUCTION
- 9.1.1 OFFERING: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 9.2 SOLUTIONS
- 9.2.1 RISING ADOPTION OF UNIFIED IDENTITY GOVERNANCE AND ZERO-TRUST FRAMEWORKS FUELS IAM MARKET EXPANSION
- 9.3 SERVICES
- 9.3.1 GROWING ENTERPRISE NEED FOR EXPERTISE AND CONTINUOUS IDENTITY OPERATIONS PROPEL MARKET GROWTH
- 9.3.2 PROFESSIONAL SERVICES
- 9.3.2.1 Surging demand for specialized IAM consulting to bolster market growth
- 9.3.2.1.1 Integration & deployment
- 9.3.2.1.2 Support & Maintenance
- 9.3.2.1.3 Consulting
- 9.3.2.1 Surging demand for specialized IAM consulting to bolster market growth
- 9.3.3 MANAGED IAM SERVICES
- 9.3.3.1 Rising need for 24/7 identity oversight and zero-trust enforcement to fuel market expansion
10 IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY
- 10.1 INTRODUCTION
- 10.1.1 TECHNOLOGY: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 10.2 ACCESS MANAGEMENT
- 10.2.1 RISING NEED FOR SECURE AND SEAMLESS ACCESS CONTROLS TO DRIVE MARKET EXPANSION
- 10.2.1.1 Authentication & Access Control
- 10.2.1.2 Credential & Directory Services
- 10.2.1.3 Authorization
- 10.2.1.4 Session & Identity Federation
- 10.2.1 RISING NEED FOR SECURE AND SEAMLESS ACCESS CONTROLS TO DRIVE MARKET EXPANSION
- 10.3 IDENTITY GOVERNANCE & ADMINISTRATION (IGA)
- 10.3.1 INCREASING DIGITAL THREATS CATALYZING SECURE AND ADAPTIVE AUTHENTICATION SOLUTIONS
- 10.3.1.1 Identity Lifecycle Management
- 10.3.1.2 Governance & Compliance
- 10.3.1.3 Role & Entitlement Management
- 10.3.1.4 Analytics & Reporting
- 10.3.1 INCREASING DIGITAL THREATS CATALYZING SECURE AND ADAPTIVE AUTHENTICATION SOLUTIONS
- 10.4 PRIVILEGED ACCESS MANAGEMENT (PAM)
- 10.4.1 INCREASING THREATS FROM PRIVILEGED MISUSE TO DRIVE MARKET GROWTH
- 10.4.1.1 Credential Vaulting
- 10.4.1.2 Session Management & Recording
- 10.4.1.3 Just-In-Time (JIT) Privileged Access
- 10.4.1.4 Endpoint Privilege Management (EPM)
- 10.4.1.5 Privilege Analytics & Threat Detection
- 10.4.1 INCREASING THREATS FROM PRIVILEGED MISUSE TO DRIVE MARKET GROWTH
- 10.5 OTHER TECHNOLOGIES
11 IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE
- 11.1 INTRODUCTION
- 11.1.1 TYPE: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 11.2 WORKFORCE IAM
- 11.2.1 AI-DRIVEN WORKFORCE IDENTITY SECURITY TO STRENGTHEN ENTERPRISE RESILIENCE DRIVES MARKET
- 11.3 CONSUMER IAM
- 11.3.1 FRICTIONLESS, PRIVACY-FIRST CUSTOMER IDENTITY MANAGEMENT TO FUEL MARKET GROWTH
- 11.4 B2B IAM
- 11.4.1 FEDERATED B2B IDENTITY CONTROL TO STRENGTHEN ECOSYSTEM SECURITY
12 IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE
- 12.1 INTRODUCTION
- 12.1.1 IDENTITY TYPE: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 12.2 HUMAN IDENTITY
- 12.2.1 FRICTIONLESS, ZERO-TRUST IDENTITY CONTROL FOR MODERN WORKFORCE AND CUSTOMERS
- 12.3 NON-HUMAN IDENTITY
- 12.3.1 ZERO-TRUST IDENTITY MANAGEMENT FOR WORKLOADS, DEVICES, AND AUTOMATED SYSTEMS
13 IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT TYPE
- 13.1 INTRODUCTION
- 13.1.1 DEPLOYMENT MODE: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 13.2 CLOUD
- 13.2.1 FLEXIBLE, COST-EFFICIENT CLOUD IAM ADOPTION ACROSS ENTERPRISES TO DRIVE MARKET
- 13.3 ON-PREMISES
- 13.3.1 SECURE, CUSTOMIZABLE ON-PREMISES IDENTITY INFRASTRUCTURE ADOPTION TO PROPEL MARKET GROWTH
- 13.4 HYBRID
- 13.4.1 HYBRID IDENTITY MODERNIZATION AND CROSS-ENVIRONMENT ACCESS CONTROL TO DRIVE MARKET
14 IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL
- 14.1 INTRODUCTION
- 14.1.1 VERTICAL: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 14.2 BFSI
- 14.2.1 ELEVATING IDENTITY RESILIENCE TO ENSURE COMPLIANCE AND DRIVE SEAMLESS BANKING ADOPTION
- 14.3 TRAVEL, TOURISM, AND HOSPITALITY
- 14.3.1 SECURE, FRICTIONLESS IDENTITY EXPERIENCES TO TRANSFORM GLOBAL TRAVEL AND HOSPITALITY
- 14.4 HEALTHCARE
- 14.4.1 ENABLING SECURE, INTEROPERABLE, AND DIGITIZED CARE EXPERIENCES TO DRIVE MARKET
- 14.5 RETAIL & E-COMMERCE
- 14.5.1 ADVANCING OMNICHANNEL COMMERCE WITH TRUSTED, PERSONALIZED DIGITAL IDENTITY JOURNEYS
- 14.6 IT & ITES
- 14.6.1 DIGITAL-FIRST IT OPERATIONS REQUIRE STRONG IDENTITY GOVERNANCE TO FUEL GROWTH
- 14.7 EDUCATION
- 14.7.1 EVOLVING LEARNING ECOSYSTEMS DEMAND STRONG, SEAMLESS IDENTITY EXPERIENCES
- 14.8 GOVERNMENT & DEFENSE
- 14.8.1 DEFENSE-GRADE IDENTITY SECURITY TO SAFEGUARD NATIONAL SYSTEMS AND DRIVE MARKET
- 14.9 OTHER VERTICALS
15 IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION
- 15.1 INTRODUCTION
- 15.2 NORTH AMERICA
- 15.2.1 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 15.2.2 US
- 15.2.2.1 Technology advancement and presence of key players to fuel market growth
- 15.2.3 CANADA
- 15.2.3.1 Rapid adoption of advanced AI- and ML-based identity verification solutions to boost growth
- 15.3 EUROPE
- 15.3.1 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 15.3.2 UK
- 15.3.2.1 Advancing IAM adoption through regulatory alignment and zero-trust transformation
- 15.3.3 GERMANY
- 15.3.3.1 Strong regulatory framework and industrial digitalization driving IAM market growth
- 15.3.4 FRANCE
- 15.3.4.1 Government digital identity initiatives and cybersecurity reforms accelerating IAM adoption
- 15.3.5 ITALY
- 15.3.5.1 Expansion of digital public services and regulatory modernization fueling IAM market growth
- 15.3.6 REST OF EUROPE
- 15.4 ASIA PACIFIC
- 15.4.1 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 15.4.2 CHINA
- 15.4.2.1 Expanding digital economy and national cybersecurity framework accelerating IAM adoption
- 15.4.3 JAPAN
- 15.4.3.1 Government digital initiatives and enterprise modernization driving IAM market growth
- 15.4.4 INDIA
- 15.4.4.1 National digital identity programs and enterprise adoption driving IAM growth
- 15.4.5 REST OF ASIA PACIFIC
- 15.5 MIDDLE EAST & AFRICA
- 15.5.1 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 15.5.2 GCC
- 15.5.2.1 Spike in demand for secure IAM solutions to support market growth
- 15.5.2.2 KSA
- 15.5.2.3 UAE
- 15.5.2.4 Rest of GCC countries
- 15.5.3 SOUTH AFRICA
- 15.5.3.1 Rising demand for advanced identity and access management solutions
- 15.5.4 REST OF MIDDLE EAST & AFRICA
- 15.6 LATIN AMERICA
- 15.6.1 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 15.6.2 BRAZIL
- 15.6.2.1 Advancing identity and access management for secure, interoperable services
- 15.6.3 MEXICO
- 15.6.3.1 Expanding identity and access management for secure digital service
- 15.6.4 REST OF LATIN AMERICA
16 COMPETITIVE LANDSCAPE
- 16.1 OVERVIEW
- 16.2 KEY PLAYER STRATEGIES/RIGHT TO WIN
- 16.3 REVENUE ANALYSIS
- 16.4 MARKET SHARE ANALYSIS
- 16.5 BRAND COMPARISON
- 16.5.1 MICROSOFT
- 16.5.2 OKTA
- 16.5.3 PING IDENTITY
- 16.5.4 IBM
- 16.5.5 ORACLE
- 16.6 COMPANY VALUATION AND FINANCIAL METRICS
- 16.6.1 COMPANY VALUATION
- 16.6.2 FINANCIAL METRICS
- 16.7 COMPANY EVALUATION MATRIX: KEY PLAYERS, 2024
- 16.7.1 STARS
- 16.7.2 EMERGING LEADERS
- 16.7.3 PERVASIVE PLAYERS
- 16.7.4 PARTICIPANTS
- 16.7.5 COMPANY FOOTPRINT: KEY PLAYERS
- 16.7.5.1 Company footprint
- 16.7.5.2 Regional footprint
- 16.7.5.3 Deployment mode footprint
- 16.7.5.4 Technology footprint
- 16.7.5.5 Vertical footprint
- 16.8 COMPANY EVALUATION MATRIX: STARTUPS/SMES, 2024
- 16.8.1 PROGRESSIVE COMPANIES
- 16.8.2 RESPONSIVE COMPANIES
- 16.8.3 DYNAMIC COMPANIES
- 16.8.4 STARTING BLOCKS
- 16.8.5 COMPETITIVE BENCHMARKING: STARTUPS/SMES
- 16.8.5.1 Detailed list of key startups/SMEs
- 16.8.5.2 Competitive benchmarking of key startups/SMEs
- 16.8.5.2.1 Regional footprint
- 16.8.5.2.2 Deployment mode footprint
- 16.8.5.2.3 Technology footprint
- 16.8.5.2.4 Vertical footprint
- 16.9 COMPETITIVE SCENARIO AND TRENDS
- 16.9.1 PRODUCT LAUNCHES/ENHANCEMENTS
- 16.9.2 DEALS
17 COMPANY PROFILES
- 17.1 KEY PLAYERS
- 17.1.1 MICROSOFT
- 17.1.1.1 Business overview
- 17.1.1.2 Products/Solutions/Services offered
- 17.1.1.3 Recent developments
- 17.1.1.3.1 Product launches/enhancements
- 17.1.1.3.2 Deals
- 17.1.1.4 MnM view
- 17.1.1.4.1 Key strengths
- 17.1.1.4.2 Strategic choices
- 17.1.1.4.3 Weaknesses and competitive threats
- 17.1.2 PING IDENTITY
- 17.1.2.1 Business overview
- 17.1.2.2 Products/Solutions/Services offered
- 17.1.2.3 Recent developments
- 17.1.2.3.1 Product launches/enhancements
- 17.1.2.3.2 Deals
- 17.1.2.3.3 Expansions
- 17.1.2.4 MnM view
- 17.1.2.4.1 Key strengths
- 17.1.2.4.2 Strategic choices
- 17.1.2.4.3 Weaknesses and competitive threats
- 17.1.3 IBM
- 17.1.3.1 Business overview
- 17.1.3.2 Products/Solutions/Services offered
- 17.1.3.3 Recent developments
- 17.1.3.3.1 Product launches/enhancements
- 17.1.3.3.2 Deals
- 17.1.3.4 MnM view
- 17.1.3.4.1 Key strengths
- 17.1.3.4.2 Strategic choices
- 17.1.3.4.3 Weaknesses and competitive threats
- 17.1.4 OKTA
- 17.1.4.1 Business overview
- 17.1.4.2 Products/Solutions/Services offered
- 17.1.4.3 Recent developments
- 17.1.4.3.1 Product launches/enhancements
- 17.1.4.3.2 Deals
- 17.1.4.3.3 Expansions
- 17.1.4.4 MnM view
- 17.1.4.4.1 Key strengths
- 17.1.4.4.2 Strategic choices
- 17.1.4.4.3 Weaknesses and competitive threats
- 17.1.5 ORACLE
- 17.1.5.1 Business overview
- 17.1.5.2 Products/Solutions/Services offered
- 17.1.5.3 Recent developments
- 17.1.5.3.1 Product launches/enhancements
- 17.1.5.3.2 Deals
- 17.1.5.4 MnM view
- 17.1.5.4.1 Key strengths
- 17.1.5.4.2 Strategic choices
- 17.1.5.4.3 Weaknesses and competitive threats
- 17.1.6 SAILPOINT
- 17.1.6.1 Business overview
- 17.1.6.2 Products/Solutions/Services offered
- 17.1.6.3 Recent developments
- 17.1.6.3.1 Product launches/enhancements
- 17.1.6.3.2 Deals
- 17.1.6.3.3 Expansions
- 17.1.7 SAVIYNT
- 17.1.7.1 Business overview
- 17.1.7.2 Products/Solutions/Services offered
- 17.1.7.3 Recent developments
- 17.1.7.3.1 Product launches/enhancements
- 17.1.7.3.2 Deals
- 17.1.7.3.3 Expansions
- 17.1.8 CYBERARK
- 17.1.8.1 Business overview
- 17.1.8.2 Products/Solutions/Services offered
- 17.1.8.3 Recent developments
- 17.1.8.3.1 Product launches/enhancements
- 17.1.8.3.2 Deals
- 17.1.8.3.3 Expansions
- 17.1.9 THALES
- 17.1.9.1 Business overview
- 17.1.9.2 Products/Solutions/Services offered
- 17.1.9.3 Recent developments
- 17.1.9.3.1 Product launches/enhancements
- 17.1.9.3.2 Deals
- 17.1.9.3.3 Expansions
- 17.1.10 AKAMAI TECHNOLOGIES
- 17.1.10.1 Business overview
- 17.1.10.2 Products/Solutions/Services offered
- 17.1.10.3 Recent developments
- 17.1.10.3.1 Product launches/enhancements
- 17.1.10.3.2 Deals
- 17.1.10.3.3 Expansions
- 17.1.11 OPENTEXT
- 17.1.11.1 Business overview
- 17.1.11.2 Products/Solutions/Services offered
- 17.1.11.3 Recent developments
- 17.1.11.3.1 Product launches/enhancements
- 17.1.11.3.2 Deals
- 17.1.11.3.3 Expansions
- 17.1.12 ENTRUST
- 17.1.12.1 Business overview
- 17.1.12.2 Products/Solutions/Services offered
- 17.1.12.3 Recent developments
- 17.1.12.3.1 Product launches/enhancements
- 17.1.12.3.2 Deals
- 17.1.13 DUO SECURITY
- 17.1.13.1 Business overview
- 17.1.13.2 Products/Solutions/Services offered
- 17.1.13.3 Recent developments
- 17.1.13.3.1 Product launches/enhancements
- 17.1.14 HID GLOBAL
- 17.1.14.1 Business overview
- 17.1.14.2 Products/Solutions/Services offered
- 17.1.14.3 Recent developments
- 17.1.14.3.1 Product launches/enhancements
- 17.1.14.3.2 Deals
- 17.1.14.3.3 Expansions
- 17.1.15 EVIDIAN
- 17.1.15.1 Business overview
- 17.1.15.2 Products/Solutions/Services offered
- 17.1.15.3 Recent developments
- 17.1.15.3.1 Product launches/enhancements
- 17.1.15.3.2 Deals
- 17.1.1 MICROSOFT
- 17.2 OTHER KEY PLAYERS
- 17.2.1 RSA SECURITY
- 17.2.2 AVATIER
- 17.2.3 MANAGEENGINE
- 17.2.4 SECUREAUTH
- 17.2.5 EMPOWERID
- 17.2.6 SIMEIO
- 17.2.7 ONE IDENTITY
- 17.2.8 FUSIONAUTH
- 17.2.9 AUTH0
- 17.2.10 IDNOW
- 17.2.11 ZUORA
- 17.2.12 SIGNZY
- 17.2.13 CIVIC TECHNOLOGIES
- 17.2.14 TRUSONA
- 17.2.15 BEYOND IDENTITY
- 17.2.16 DELINEA
- 17.2.17 OPTIMAL IDM
- 17.2.18 NETWRIX
- 17.2.19 AQUERA
- 17.2.20 CERBY
- 17.2.21 TRAXION
- 17.2.22 RADIANT LOGIC
- 17.2.23 ELIMITY
- 17.2.24 OLERIA
- 17.2.25 VEZA
- 17.2.26 BRAVURA SECURITY
- 17.2.27 FISCHER IDENTITY
- 17.2.28 LUMOS
- 17.2.29 OMADA
- 17.2.30 OPENIAM
- 17.2.31 PATHLOCK
- 17.2.32 TUEBORA
- 17.2.33 RIPPLING
18 RESEARCH METHODOLOGY
- 18.1 RESEARCH DATA
- 18.1.1 SECONDARY DATA
- 18.1.2 PRIMARY DATA
- 18.1.2.1 Breakdown of primary profiles
- 18.1.2.2 Key industry insights
- 18.2 MARKET SIZE ESTIMATION
- 18.2.1 REVENUE ESTIMATES
- 18.3 DATA TRIANGULATION
- 18.4 FACTOR ANALYSIS
- 18.5 RESEARCH ASSUMPTIONS
- 18.6 RESEARCH LIMITATIONS
19 APPENDIX
- 19.1 DISCUSSION GUIDE
- 19.2 KNOWLEDGESTORE: MARKETSANDMARKETS' SUBSCRIPTION PORTAL
- 19.3 CUSTOMIZATION OPTIONS
- 19.4 RELATED REPORTS
- 19.5 AUTHOR DETAILS



















