
|
시장보고서
상품코드
1889164
커넥티드카 보안 시장 : 용도별, 전기자동차 유형별, 형태별, 보안 유형별, 솔루션 유형별, 지역별 예측Connected Car Security Market by Type (Endpoint, Application, Network, Security), Solution (Software & Hardware), Application (TCU, Infotainment, ADAS, Communication Modules), Form (In-vehicle, External Cloud), EV Type & Region - Global Forecast to 2032 |
||||||
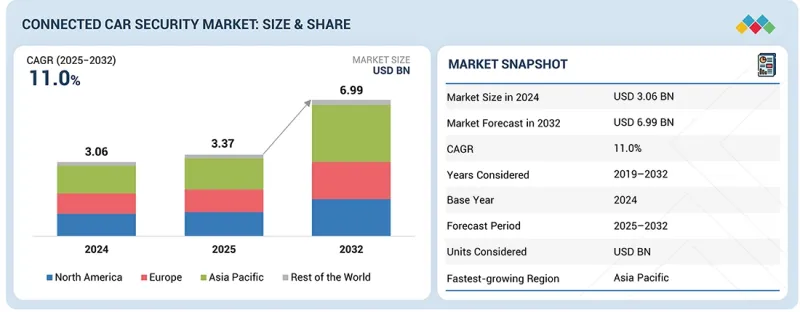
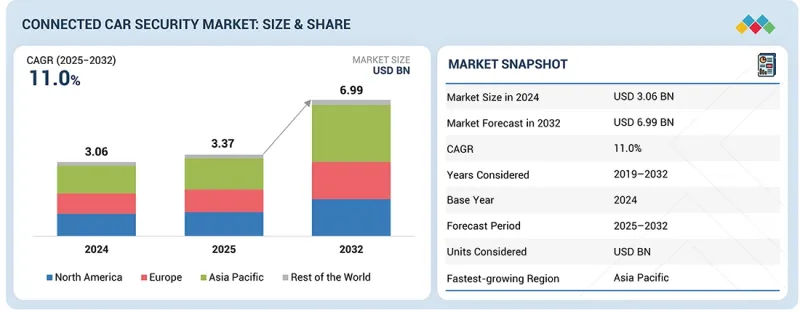
커넥티드카 보안 시장의 규모는 2025년 33억 7,000만 달러에서 2032년까지 69억 9,000만 달러에 이를 것으로 예측되며, 2025년부터 2032년까지의 CAGR은 11.0%로 전망됩니다.
시장의 성장은 소프트웨어 정의 차량(SDV)의 빠른 보급, 무선(OTA) 업데이트 기능, V2X 통신, 차량의 ECU, 텔레매틱스 유닛, 클라우드 플랫폼을 목표로 하는 사이버 보안 위협 증가로 인해 발생합니다.
| 조사 범위 | |
|---|---|
| 조사 대상 기간 | 2019-2032년 |
| 기준연도 | 2024년 |
| 예측 기간 | 2025-2032년 |
| 대상 단위 | 10억 달러 |
| 부문 | 용도별, 전기자동차 유형별, 형태별, 보안 유형별, 솔루션 유형별, 지역별 |
| 대상 지역 | 아시아태평양, 유럽, 북미 및 기타 지역 |
UNECE WP.29 CSMS, ISO/SAE 21434, 미국 NHTSA 사이버 보안 지침, 중국의 자동차 데이터 보안 규정 등의 규정에 따라 자동차 제조업체는 보안 게이트웨이, IDS/IPS, 하드웨어 보안 모듈, 암호화 통신 프레임워크의 채택을 강요받고 있습니다. 게다가 전기자동차로의 전환과 커넥티드 ADAS 기능의 보급으로 사이버 보안의 복잡성이 증가하고 있으며, 인포테인먼트, 텔레매틱스, 자율주행 스택에 대한 다층 보호가 필요합니다. 아시아태평양에서의 특히 중국의 주요 공헌 외에도 유럽과 북미의 투자 증가가 결합되어 첨단 커넥티드카 보안 아키텍처의 세계적인 채택이 가속화되고 있습니다.
자동차 보안 솔루션의 이점은 전자제어장치(ECU), 도메인 컨트롤러, 텔레매틱스 시스템의 복잡성이 추진되면서 주목받고 있습니다. 이들은 무단 액세스 및 시스템 작동을 방지하기 위해 내장형 보호가 필요합니다. UNECE WP.29, ISO/SAE 21434 및 중국의 자동차 데이터 보안 규정에 따른 컴플라이언스 요구사항으로 자동차 제조업체는 자동차 아키텍처 내에 보안 게이트웨이, 하드웨어 보안 모듈(HSM) 및 침입 탐지 시스템의 도입을 가속화하고 있습니다. 연결 ADAS, 디지털 조종석 및 V2X 통신이 중급 차량에서 고급 차량 모델로 표준화됨에 따라 차량 보안은 내부 네트워크, OTA 소프트웨어 및 데이터 흐름을 보호하는 핵심 방어 계층이 됩니다. 이러한 지속적인 규제와 기술적 추진으로 자동차 솔루션은 시장에서 가장 큰 수익을 창출하는 부문으로 자리매김하고 있습니다.
하드웨어 기반 솔루션의 채택은 ECU 수준에서 안전한 데이터 처리, 암호화 키 저장 및 실시간 위협 대책을 실현하는 변조 저항 아키텍처로의 산업 변화에 따라 급속도로 확대되고 있습니다. TPM, HSM, 보안 마이크로컨트롤러, 암호화 가속기 등의 구성 요소는 안전성이 매우 중요한 ADAS 시스템, 고성능 컴퓨팅 유닛 및 자율주행 플랫폼을 보호하는 데 필수적입니다. 차량 펌웨어와 통신 버스를 대상으로 사이버 보안 위협이 증가함에 따라 OEM은 보다 강력한 인증과 암호화를 실현하기 위해 하드웨어 기반 신뢰 모델의 도입을 가속화하고 있습니다. SDV(소프트웨어 정의 차량)의 보급 확대와 안전한 조닝 아키텍처의 필요성으로 인해 수요가 더욱 가속화되고 통합 비용이 높음에도 불구하고 하드웨어 기반 솔루션이 가장 성장률이 높은 부문이 되었습니다.
아시아태평양에서는 중국, 일본, 한국, 인도의 커넥티드 모빌리티 및 자율주행 모빌리티 에코시스템의 빠른 확대를 배경으로 강력한 성장이 예상됩니다. 중국은 자동차 데이터 보안 규제의 엄격한 시행을 통해 이 기세를 견인하고 있으며, BYD, NIO, XPeng, Zeekr, SAIC 등의 자동차 제조업체에 대해 암호화된 차내 통신, 보안 OTA 플랫폼, 임베디드 IDS/IPS 솔루션의 채용을 의무화하고 있습니다. 일본과 한국에서는 UNECE WP.29 CSMS 프레임워크에 따른 도입이 진행되고 있으며, 견고한 텔레매틱스 네트워크와 고급차 또는 대중차 부문을 불문하고 높은 커넥티드카 보급률이 이를 지원하고 있습니다. EV의 급속한 보급, 강력한 5G 전개, 정부 주도의 사이버 보안 컴플라이언스로 아시아태평양은 지속적으로 커다란 신규 수익 기회를 창출해 커넥티드카 보안 시장에서 가장 성장이 빠른 지역으로 자리잡고 있습니다.
- 회사별 : OEM 10%, Tier 1 회사 90%
- 직책별 : C레벨 임원 60%, 임원 30%, 기타 10%
- 지역별 : 북미 40%, 유럽 50%, 아시아태평양 10%
참고 : 기타에는 판매 관리자 및 제품 관리자 등이 포함됩니다.
커넥티드카 보안 시장은 NXP Semiconductors(네덜란드), AUMOVIO SE(독일), Harman International(미국), Vector Informatik GmbH(독일), BlackBerry Limited(캐나다), Thales(프랑스), ARM Limited(영국), WirelessCar(스웨덴), Astemo Ltd. 테크놀로지스(미국) 등의 대기업이 지배하고 있습니다. 이 회사들은 커넥티드카 보안 시장에서의 입지를 강화하기 위해 포트폴리오를 확대하고 있습니다.
조사 대상
이 보고서는 보안 유형(엔드포인트 보안, 애플리케이션 보안, 네트워크 보안, 클라우드 보안), 용도(텔레매틱스 제어 유닛(TCU), 인포테인먼트 시스템, ADAS 및 자율주행 시스템, 통신 모듈), 전기자동차유형(BEV, PHEV, HEV, FCEV), 솔루션유형(소프트웨어 기반 솔루션, 하드웨어 기반 솔루션), 형태(차재 솔루션, 외부 클라우드 서비스), 지역(북미, 아시아태평양, 유럽, 기타 세계 지역)별로 분석했습니다. 주요 커넥티드카 보안 시장에서 주요 기업의 경쟁 구도와 기업 프로파일을 다룹니다.
본 조사에서는 주요 시장 기업의 상세한 경쟁 분석, 기업 프로파일, 제품 및 사업 제공에 관한 주요 관찰 사항, 최근 동향, 주요 시장 전략에 대해서도 다룹니다.
보고서 구매의 주요 이점
- 본 보고서는 커넥티드카 보안 시장 및 그 하위 부문에서 수익 수치의 최상의 근사치에 대한 정보를 제공하여 시장 리더와 신규 진출기업을 지원합니다.
- 본 보고서는 이해관계자 여러분이 경쟁 구도를 이해하고 보다 깊은 인사이트를 얻음으로써 자사의 비즈니스를 보다 적절히 자리매김하고 적절한 시장 진출 전략을 수립하도록 합니다.
- 또한 이해관계자가 시장 동향을 파악하고 주요 시장 성장 촉진요인, 제약, 과제, 기회에 대한 정보를 제공합니다.
- 본 보고서는 커넥티드카 보안 시장의 현재 및 미래 가격 동향에 대한 이해관계자의 이해를 높이는 데에도 도움이 됩니다.
이 보고서는 다음 포인트에 대한 인사이트를 제공합니다.
- 주요 촉진요인 분석(텔레매틱스 및 V2X별 차량 연결성 향상, 세계의 자동차 사이버 보안 규정에 대한 의무적 준수, 커넥티드카 및 자율주행 차량에 대한 사이버 공격 증가), 제약 요인(레거시 ECU 및 차량 아키텍처를 통한 보안 업그레이드 복잡성, 높은 구현 및 통합 비용), 기회(관리 보안 서비스 및 차량용 SOC 성장, 보안 OTA 및 라이프사이클 관리에 대한 수요 증가, 강력한 PKI 기반 보안을 필요로 하는 V2X 및 5G 네트워크), 과제(진화하는 사이버 위협, 안전 상 중요한 기능을 손상시키지 않고 오감지를 최소화하는 것)
- 제품개발 및 이노베이션 : 커넥티드카 보안 시장의 향후 기술 동향, 연구개발 활동, 제품 및 서비스 투입에 관한 상세한 분석
- 시장개발 : 다양한 지역의 수익성이 높은 시장에 관한 종합적인 정보
- 시장의 다양화 : 커넥티드카 보안 시장에 있어서의 신제품 및 서비스, 미개척 지역, 최신 동향, 투자에 관한 종합적인 정보
- 경쟁평가 : NXP Semiconductors(네덜란드), AUMOVIO SE(독일), Harman International(미국), Vector Informatik GmbH(독일), BlackBerry Limited(캐나다), Thales(프랑스), ARM Limited(영국), WirelessCar(스웨덴), Astemo Ltd.(일본), Keysight 테크놀로지스(미국)와 같은 주요 기업의 시장 점유율, 성장 전략 및 서비스 제공에 대한 자세한 평가를 실시합니다. 또한 주요 기업에 대해 커넥티드카 보안 시장 내 점유율, 성장 전략, 서비스 제공 내용 등을 상세하게 평가합니다.
자주 묻는 질문
목차
제1장 서론
제2장 조사 방법
제3장 주요 요약
제4장 중요 인사이트
제5장 시장 개요
- 시장 역학
- 미충족 요구와 새로운 시장 기회
- 상호연결된 시장과 분야 간 기회
- Tier 1, 2, 3 기업의 전략적 움직임
제6장 업계 동향
- Porter's Five Forces 분석
- 거시경제 전망
- 공급망 분석
- 생태계 분석
- 가격 분석
- 무역 분석
- 2025-2026년의 주요 회의와 이벤트
- 고객사업에 영향을 주는 동향 및 혼란
- 투자 및 자금조달 시나리오
- 사례 연구 분석
- 미국의 2025년 관세
제7장 고객정세와 구매행동
- 의사결정 프로세스
- 구매자 이해관계자와 구매평가기준
- 채용 장벽과 내부 과제
- 다양한 최종 사용자 산업에서의 미충족 요구
- 시장 수익성
- 수익 가능성
- 비용역학
- 주요 용도에 있어서의 마진 기회
제8장 기술, 특허, 디지털, AI 도입별 전략적 파괴
- 특허 분석
- 생성형 AI가 커넥티드카 보안 시장에 미치는 영향
- 주요 신기술
- 보완적 기술
- 기술 및 제품 로드맵
- 커넥티드카 시장에서의 OEM별 기술 개발
제9장 규제 상황
- 규제 상황
- 지역별 규제
제10장 커넥티드카 보안 시장(용도별)
- 텔레매틱스 제어 유닛(TCUS)
- 인포테인먼트 시스템
- ADAS와 자율주행 시스템
- 통신 모듈
제11장 커넥티드카 보안 시장(전기자동차 유형별)
- 전기자동차
- PHEV
- 하이브리드 자동차
- 연료전지자동차
제12장 커넥티드카 보안 시장(형태별)
- 차재 솔루션
- 외부 클라우드 서비스
제13장 커넥티드카 보안 시장(보안 유형별)
- 엔드포인트 보안
- 애플리케이션 보안
- 네트워크 보안
- 클라우드 보안
제14장 커넥티드카 보안 시장(솔루션 유형별)
- 소프트웨어 기반 솔루션
- 하드웨어 기반 솔루션
제15장 커넥티드카 보안 시장(지역별)
- 아시아태평양
- 아시아태평양 : 거시경제 전망
- 중국
- 일본
- 인도
- 한국
- 기타
- 유럽
- 유럽 : 거시경제 전망
- 영국
- 독일
- 프랑스
- 스페인
- 이탈리아
- 기타
- 북미
- 북미 : 거시경제 전망
- 미국
- 캐나다
- 멕시코
- 기타 지역
- 기타 지역 : 거시 경제 전망
- 이란
- 남아프리카
제16장 경쟁 구도
- 주요 참가 기업의 전략 및 강점(2022-2024년)
- 시장 점유율 분석(2024년)
- 수익 분석(2020-2024년)
- 브랜드 비교
- 기업평가와 재무지표
- 기업평가 매트릭스 : 주요 진입기업(2024년)
- 기업평가 매트릭스 : 스타트업 및 중소기업(2024년)
- 경쟁 시나리오
제17장 기업 프로파일
- 주요 진출기업
- AUMOVIO SE
- BLACKBERRY LIMITED
- VECTOR INFORMATIK GMBH
- NXP SEMICONDUCTORS
- HARMAN INTERNATIONAL
- UPSTREAM SECURITY LTD.
- ASTEMO, LTD.
- TRUSTONIC
- KPIT
- THALES
- T-SYSTEMS INTERNATIONAL GMBH
- AUTOCRYPT CO., LTD.
- 기타 기업
- ARM LIMITED
- TREND MICRO INCORPORATED
- ETAS
- KEYSIGHT TECHNOLOGIES
- INTERTEK GROUP PLC
- DEVICE AUTHORITY
- SECUNET SECURITY NETWORKS AG
- TRILLIUM SECURE, INC.
- WIRELESSCAR
- KARAMBA SECURITY
- INTERTRUST TECHNOLOGIES CORPORATION
- GUARDKNOX
- TATA ELXSI
제18장 부록
CSM 25.12.23The connected car security market is projected to grow from USD 3.37 billion in 2025 to reach USD 6.99 billion by 2032, at a CAGR of 11.0% from 2025 to 2032. Market growth is driven by the rapid expansion of software-defined vehicles (SDVs), over-the-air (OTA) update capabilities, V2X communication, and the rising cybersecurity threats targeting vehicle ECUs, telematics units, and cloud platforms.
| Scope of the Report | |
|---|---|
| Years Considered for the Study | 2019-2032 |
| Base Year | 2024 |
| Forecast Period | 2025-2032 |
| Units Considered | USD Billion |
| Segments | Type, Solution, Application, Form, EV Type & Region |
| Regions covered | Asia Pacific, Europe, North America, Rest of the World |
Additionally, regulations such as UNECE WP.29 CSMS, ISO/SAE 21434, the US NHTSA cybersecurity guidelines, and China's Automotive Data Security Regulations are pushing automakers to adopt secure gateways, IDS/IPS, hardware-secured modules, and encrypted communication frameworks. Moreover, the shift toward electric vehicles and connected ADAS features increases cybersecurity complexity, requiring multi-layer protection for infotainment, telematics, and autonomous driving stacks. Substantial contributions from the Asia Pacific region, especially China, combined with increasing investments from Europe and North America, are accelerating the global adoption of advanced connected car security architectures.
"By form, the in-vehicle solutions segment is projected to account for a larger share than the external cloud services segment during the forecast period."
The dominance of in-vehicle security solutions is driven by the rising complexity of electronic control units (ECUs), domain controllers, and telematics systems, which require embedded protection to prevent unauthorized access and system manipulation. Compliance mandates under UNECE WP.29, ISO/SAE 21434, and China's Automotive Data Security Regulations have accelerated OEM adoption of secure gateways, hardware security modules (HSMs), and intrusion detection systems inside the vehicle architecture. As connected ADAS, digital cockpits, and V2X communication become standard across mid-range and premium models, in-vehicle security becomes the core protection layer for safeguarding internal networks, OTA software, and data flows. This sustained regulatory and technological push positions in-vehicle solutions as the largest revenue-generating segment in the market.
"By solution type, the hardware-based solutions segment is projected to be a faster-growing segment than the software-based segment during the forecast period."
The use of hardware-based solutions is expanding rapidly due to the industry's shift toward tamper-resistant architectures that ensure secure data processing, cryptographic key storage, and real-time threat mitigation at the ECU level. Components such as TPMs, HSMs, secure microcontrollers, and cryptographic accelerators are becoming essential for protecting safety-critical ADAS systems, high-performance computing units, and autonomous driving platforms. With rising cybersecurity threats targeting vehicle firmware and communication buses, OEMs are increasingly adopting hardware-rooted trust models for stronger authentication and encryption. Growing SDV adoption and the need for secured zonal architectures further accelerate demand, making hardware-based solutions the fastest-growing segment despite higher integration costs.
"Asia Pacific is projected to be the fastest-growing segment in the global connected car security market during the forecast period."
Asia Pacific is projected to witness strong and accelerating growth driven by the rapid expansion of connected and autonomous mobility ecosystems in China, Japan, South Korea, and India. China is leading this momentum through the strict enforcement of the automotive data security regulations, compelling OEMs such as BYD, NIO, XPeng, Zeekr, and SAIC to adopt encrypted in-vehicle communication, secure OTA platforms, and embedded IDS/IPS solutions. Japan and South Korea are advancing deployments in line with UNECE WP.29 CSMS frameworks, supported by robust telematics networks and high connected car penetration across both luxury and mass-market segments. With rapid EV adoption, strong 5G rollout, and government-led cybersecurity compliance, Asia Pacific continues to generate significant new revenue opportunities, making it the fastest-growing region in the connected car security market.
In-depth interviews were conducted with CEOs, marketing directors, other innovation and technology directors, and executives from various key organizations operating in this market.
- By Company Type: OEMs - 10% and Tier 1 Companies - 90%
- By Designation: C-Level Executive - 60%; Director-Level - 30%; Others - 10%
- By Region: North America - 40%; Europe - 50%; and Asia Pacific - 10%
Note: Others include Sales Managers and Product Managers.
The connected car security market is dominated by major players, such as NXP Semiconductors (Netherlands), AUMOVIO SE (Germany), Harman International (US), Vector Informatik GmbH (Germany), BlackBerry Limited (Canada), Thales (France), ARM Limited (UK), WirelessCar (Sweden), Astemo Ltd. (Japan), and Keysight Technologies (US.) These companies are expanding their portfolios to strengthen their connected car security market position.
Research Coverage
The report covers the connected car security market in terms of security type (Endpoint Security, Application Security, Network Security, and Cloud Security), application [Telematics Control Units (TCUs), Infotainment Systems, ADAS & Autonomous Driving Systems, and Communication Modules], electric vehicle type (BEV, PHEV, HEV, and FCEV), solution type (Software-based Solutions and Hardware-based Solutions), form (In-Vehicle Solutions and External Cloud Services), and Region (North America, Asia Pacific, Europe, and Rest of the World). It covers the competitive landscape and company profiles of the key players in the significant connected car security market.
The study also includes an in-depth competitive analysis of the key market players, their company profiles, key observations related to product and business offerings, recent developments, and key market strategies.
Key Benefits of Buying the Report:
- The report will help market leaders/new entrants with information on the closest approximations of revenue numbers for the connected car security market and its subsegments.
- This report will help stakeholders understand the competitive landscape and gain more insights, enabling them to position their businesses better and plan suitable go-to-market strategies.
- The report will also help stakeholders understand the market pulse and provide information on key market drivers, restraints, challenges, and opportunities.
- The report will also help stakeholders understand the current and future pricing trends of the connected car security market.
The report also provides insights into the following pointers:
- Analysis of key drivers (Increasing vehicle connectivity through telematics and V2X, mandatory compliance with global automotive cybersecurity regulations, and rising cyberattacks on connected and autonomous vehicles), restraints (Legacy ECU and vehicle architectures complicate security upgrades and high implementation and integration costs), opportunities (Growth of managed security services and vehicle SOCs, rising demand for secure OTA and lifecycle management, and V2X and 5G networks requiring strong PKI-based security), and challenges (Evolving cyber threats and minimizing false positives without compromising safety-critical functions)
- Product Developments/Innovation: Detailed insights into upcoming technologies, research & development activities, and product & service launches in the connected car security market.
- Market Development: Comprehensive information about lucrative markets across varied regions
- Market Diversification: Exhaustive information about new products & services, untapped geographies, recent developments, and investments in the connected car security market
- Competitive Assessment: In-depth assessment of market share, growth strategies, and service offerings of leading players like as NXP Semiconductors (Netherlands), AUMOVIO SE (Germany), Harman International (US), Vector Informatik GmbH (Germany), BlackBerry Limited (Canada), Thales (France), ARM Limited (UK), WirelessCar (Sweden), Astemo Ltd. (Japan), and Keysight Technologies (US), among others, in connected car security market
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 STUDY OBJECTIVES
- 1.2 MARKET DEFINITION
- 1.3 STUDY SCOPE
- 1.3.1 MARKET SEGMENTATION & REGIONAL SCOPE
- 1.3.2 INCLUSIONS & EXCLUSIONS
- 1.4 YEARS CONSIDERED
- 1.5 CURRENCY CONSIDERED
- 1.6 STAKEHOLDERS
2 RESEARCH METHODOLOGY
- 2.1 RESEARCH DATA
- 2.1.1 SECONDARY DATA
- 2.1.1.1 Key secondary sources
- 2.1.1.2 Key data from secondary sources
- 2.1.2 PRIMARY DATA
- 2.1.2.1 Primary participants
- 2.1.2.2 Key industry insights
- 2.1.1 SECONDARY DATA
- 2.2 MARKET BREAKDOWN & DATA TRIANGULATION
- 2.3 MARKET SIZE ESTIMATION
- 2.3.1 TOP-DOWN APPROACH
- 2.4 MARKET FORECAST
- 2.5 RESEARCH ASSUMPTIONS
- 2.6 RESEARCH LIMITATIONS
3 EXECUTIVE SUMMARY
- 3.1 KEY INSIGHTS AND MARKET HIGHLIGHTS
- 3.2 KEY MARKET PARTICIPANTS: SHARED INSIGHTS AND STRATEGIC DEVELOPMENTS
- 3.3 DISRUPTIVE TRENDS SHAPING MARKET
- 3.4 HIGH-GROWTH SEGMENTS AND EMERGING FRONTIERS
- 3.5 SNAPSHOT: GLOBAL MARKET SIZE, GROWTH RATE, AND FORECAST
4 PREMIUM INSIGHTS
- 4.1 ATTRACTIVE OPPORTUNITIES FOR PLAYERS IN CONNECTED CAR SECURITY MARKET
- 4.2 CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE
- 4.3 CONNECTED CAR SECURITY MARKET, BY ELECTRIC VEHICLE TYPE
- 4.4 CONNECTED CAR SECURITY MARKET, BY FORM
- 4.5 CONNECTED CAR SECURITY MARKET, BY APPLICATION
- 4.6 CONNECTED CAR SECURITY MARKET, BY SOLUTION TYPE
- 4.7 CONNECTED CAR SECURITY MARKET, BY REGION
5 MARKET OVERVIEW
- 5.1 INTRODUCTION
- 5.2 MARKET DYNAMICS
- 5.2.1 DRIVERS
- 5.2.1.1 Increasing vehicle connectivity through telematic and V2X
- 5.2.1.2 Mandatory compliance with global automotive cybersecurity regulations
- 5.2.1.3 Rising cyberattacks on connected and autonomous vehicles
- 5.2.2 RESTRAINTS
- 5.2.2.1 Legacy ECU and vehicle architectures complicating security upgrades
- 5.2.2.2 High implementation and integration costs
- 5.2.3 OPPORTUNITIES
- 5.2.3.1 Growth of managed security services and vehicle SOCs
- 5.2.3.2 Rising demand for secure OTA and lifecycle management
- 5.2.3.3 V2X and 5G networks require strong PKI-based security
- 5.2.4 CHALLENGES
- 5.2.4.1 Evolving cyber threats hindering long-term protection
- 5.2.4.2 Minimizing false positives without compromising safety-critical functions
- 5.2.1 DRIVERS
- 5.3 UNMET NEEDS AND WHITE SPACES
- 5.3.1 UNMET NEEDS IN CONNECTED CAR SECURITY MARKET
- 5.3.2 WHITE SPACE OPPORTUNITIES
- 5.4 INTERCONNECTED MARKETS AND CROSS-SECTOR OPPORTUNITIES
- 5.4.1 INTERCONNECTED MARKETS
- 5.4.2 CROSS-SECTOR OPPORTUNITIES
- 5.5 STRATEGIC MOVES BY TIER 1/2/3 PLAYERS
- 5.5.1 KEY MOVES AND STRATEGIC FOCUS
6 INDUSTRY TRENDS
- 6.1 PORTER'S FIVE FORCES ANALYSIS
- 6.1.1 THREAT FROM NEW ENTRANTS
- 6.1.2 THREAT FROM SUBSTITUTES
- 6.1.3 BARGAINING POWER OF SUPPLIERS
- 6.1.4 BARGAINING POWER OF BUYERS
- 6.1.5 INTENSITY OF COMPETITIVE RIVALRY
- 6.2 MACROECONOMIC OUTLOOK
- 6.2.1 INTRODUCTION
- 6.2.2 GDP TRENDS AND FORECAST
- 6.2.3 TRENDS IN GLOBAL CONNECTED CAR INDUSTRY
- 6.2.3.1 Transition toward software-defined vehicle era
- 6.2.3.2 Connectivity as enabler of autonomous mobility
- 6.2.3.3 Vehicle-to-everything (V2X) to build foundation for smart mobility
- 6.2.3.4 Evolution of vehicle architecture in software-driven era
- 6.2.3.5 Personalization and connected experiences in modern mobility
- 6.2.4 TRENDS IN GLOBAL AUTOMOTIVE & TRANSPORTATION INDUSTRY
- 6.2.4.1 Rapid but uneven EV adoption and market share gains
- 6.2.4.2 Battery pack cost decline and cell supply overcapacity reshaping economics
- 6.2.4.3 Heavy-duty and commercial electrification (plus selective hydrogen use) accelerating heterogeneously
- 6.2.4.4 ADAS proliferation and measured progress toward high autonomy and rise of pilot robotaxi deployment
- 6.2.4.5 Semiconductor cycles, supply resilience, and industrial policy reshaping auto supply chains
- 6.3 SUPPLY CHAIN ANALYSIS
- 6.4 ECOSYSTEM ANALYSIS
- 6.5 PRICING ANALYSIS
- 6.5.1 INDICATIVE PRICING, BY APPLICATION
- 6.5.2 INDICATIVE PRICING, BY SECURITY TYPE
- 6.5.3 INDICATIVE PRICING, BY REGION
- 6.6 TRADE ANALYSIS
- 6.6.1 IMPORT SCENARIO
- 6.6.2 EXPORT SCENARIO
- 6.7 KEY CONFERENCES & EVENTS, 2025-2026
- 6.8 TRENDS/DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- 6.9 INVESTMENT & FUNDING SCENARIO
- 6.10 CASE STUDY ANALYSIS
- 6.10.1 CONTINENTAL DEVELOPED IN-VEHICLE CYBERSECURITY FRAMEWORK TO PROTECT CONNECTED ECUS AND SECURE DATA EXCHANGE
- 6.10.2 BOSCH IMPLEMENTED SECURE GATEWAY MODULE TO CONTROL EXTERNAL ACCESS AND STRENGTHEN VEHICLE COMMUNICATION SECURITY
- 6.10.3 HARMAN ENABLED CLOUD-BASED THREAT DETECTION TO MONITOR AND MITIGATE CYBER RISKS IN CONNECTED VEHICLE FLEETS
- 6.10.4 APTIV DEPLOYED END-TO-END CYBERSECURITY ARCHITECTURE TO SAFEGUARD OVER-THE-AIR UPDATES AND DATA TRANSFER
- 6.10.5 NXP INTRODUCED AUTOMOTIVE HARDWARE SECURITY MODULES TO ENCRYPT DATA AND ENSURE SECURE ECU COMMUNICATION
- 6.10.6 UPSTREAM SECURED VEHICLE FLEET OPERATIONS USING CLOUD ANALYTICS FOR THREAT DETECTION AND INCIDENT RESPONSE
- 6.10.7 ARGUS DEVELOPED NETWORK INTRUSION DETECTION AND PREVENTION SYSTEMS TO IDENTIFY AND BLOCK MALICIOUS TRAFFIC
- 6.10.8 BLACKBERRY QNX PROVIDED SECURE OPERATING SYSTEM FOUNDATION TO SUPPORT SAFETY-CRITICAL AUTOMOTIVE SOFTWARE
- 6.11 US 2025 TARIFF
- 6.11.1 INTRODUCTION
- 6.11.2 KEY TARIFF RATES
- 6.11.2.1 Key product-related tariffs
- 6.11.3 PRICE IMPACT ANALYSIS
- 6.11.4 IMPACT ON COUNTRY/REGION
- 6.11.4.1 US
- 6.11.4.2 Europe
- 6.11.4.3 Asia Pacific
- 6.11.5 IMPACT ON END-USE INDUSTRIES
7 CUSTOMER LANDSCAPE AND BUYER BEHAVIOR
- 7.1 DECISION-MAKING PROCESS
- 7.2 BUYER STAKEHOLDERS AND BUYING EVALUATION CRITERIA
- 7.2.1 KEY STAKEHOLDERS IN BUYING PROCESS
- 7.2.2 BUYING CRITERIA
- 7.3 ADOPTION BARRIERS AND INTERNAL CHALLENGES
- 7.4 UNMET NEEDS IN VARIOUS END-USER INDUSTRIES
- 7.5 MARKET PROFITABILITY
- 7.6 REVENUE POTENTIAL
- 7.7 COST DYNAMICS
- 7.8 MARGIN OPPORTUNITIES IN KEY APPLICATIONS
8 STRATEGIC DISRUPTION THROUGH TECHNOLOGY, PATENTS, DIGITAL, AND AI ADOPTION
- 8.1 PATENT ANALYSIS
- 8.1.1 INTRODUCTION
- 8.1.2 LIST OF PATENTS GRANTED TO LG ELECTRONICS
- 8.1.3 LIST OF PATENTS GRANTED TO INTEL CORPORATION
- 8.1.4 LIST OF PATENTS GRANTED TO SAMSUNG ELECTRONICS
- 8.2 IMPACT OF GENERATIVE AI ON CONNECTED CAR SECURITY MARKET
- 8.3 KEY EMERGING TECHNOLOGIES
- 8.3.1 VEHICLE SECURITY OPERATIONS CENTERS (VSOCS)
- 8.3.2 INTRUSION DETECTION & PREVENTION SYSTEMS
- 8.3.3 SECURE COMMUNICATION PROTOCOLS
- 8.3.4 ENCRYPTION & CRYPTOGRAPHY
- 8.3.5 HARDWARE SECURITY MODULES (HSMS)
- 8.3.6 TRUSTED PLATFORM MODULES (TPMS)
- 8.3.7 IDENTITY & ACCESS MANAGEMENT (IAM)
- 8.4 COMPLEMENTARY TECHNOLOGIES
- 8.4.1 CLOUD & EDGE-BASED VEHICLE SECURITY
- 8.4.2 AI-/ML-DRIVEN INTRUSION DETECTION & RESPONSE
- 8.4.3 BLOCKCHAIN FOR V2X AND DATA INTEGRITY
- 8.4.4 BIOMETRIC AUTHENTICATION FOR DRIVER & VEHICLE ACCESS
- 8.5 TECHNOLOGY/PRODUCT ROADMAP
- 8.5.1 SHORT-TERM (2025-2027): FOUNDATION & EARLY COMMERCIALIZATION
- 8.5.2 MID-TERM (2027-2030): EXPANSION & STANDARDIZATION
- 8.5.3 LONG-TERM (2030 ONWARDS): MASS COMMERCIALIZATION & DISRUPTION
- 8.6 TECHNOLOGICAL DEVELOPMENTS IN CONNECTED CAR MARKET, BY OEM
9 REGULATORY LANDSCAPE
- 9.1 REGULATORY LANDSCAPE
- 9.1.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- 9.2 REGULATIONS, BY REGION
- 9.2.1 NORTH AMERICA
- 9.2.2 EUROPE
- 9.2.3 ASIA PACIFIC
10 CONNECTED CAR SECURITY MARKET, BY APPLICATION
- 10.1 INTRODUCTION
- 10.2 TELEMATICS CONTROL UNITS (TCUS)
- 10.2.1 GROWING INTEGRATION OF CONNECTED SERVICES AND REAL-TIME VEHICLE MONITORING TO DRIVE MARKET
- 10.3 INFOTAINMENT SYSTEMS
- 10.3.1 GROWING COMPLEXITY OF INFOTAINMENT ARCHITECTURES TO DRIVE MARKET
- 10.4 ADAS & AUTONOMOUS DRIVING SYSTEMS
- 10.4.1 NEED FOR STRENGTHENING CYBERSECURITY FOR ADAS AND AUTONOMOUS DRIVING SYSTEMS TO BOOST MARKET
- 10.5 COMMUNICATION MODULES
- 10.5.1 GROWING ADOPTION OF OVER-THE-AIR UPDATES, REMOTE DIAGNOSTICS, PREDICTIVE MAINTENANCE, AND CONNECTED-SERVICE PLATFORMS TO DRIVE MARKET
11 CONNECTED CAR SECURITY MARKET, BY ELECTRIC VEHICLE TYPE
- 11.1 INTRODUCTION
- 11.2 BEV
- 11.2.1 STRONG ENDPOINT PROTECTION AND SECURE COMMUNICATION FRAMEWORKS IN BEVS TO DRIVE MARKET
- 11.3 PHEV
- 11.3.1 EXPANDING SOFTWARE DEPENDENCIES INCREASING CYBERSECURITY EXPOSURE TO DRIVE MARKET
- 11.4 HEV
- 11.4.1 FOCUS ON SAFEGUARDING VEHICLE-TO-VEHICLE AND VEHICLE-TO-INFRASTRUCTURE CHANNELS TO BOOST MARKET
- 11.5 FCEV
- 11.5.1 RELIANCE OF FCEVS ON CLOUD-BASED INFRASTRUCTURE TO BOOST MARKET
12 CONNECTED CAR SECURITY MARKET, BY FORM
- 12.1 INTRODUCTION
- 12.2 IN-VEHICLE SOLUTIONS
- 12.2.1 RAPIDLY ADOPTING ADVANCED ENDPOINT PROTECTION, INTRUSION DETECTION, SECURE UPDATES, AND RESILIENT COMMUNICATION FRAMEWORKS TO DRIVE MARKET
- 12.3 EXTERNAL CLOUD SERVICES
- 12.3.1 INCREASING RELIANCE OF VEHICLES ON ELECTRONIC CONTROL UNITS AND TELEMATICS TO DRIVE MARKET
13 CONNECTED CAR SECURITY MARKET, BY SECURITY TYPE
- 13.1 INTRODUCTION
- 13.2 ENDPOINT SECURITY
- 13.2.1 FOCUS ON DEVICE AUTHENTICATION, INTRUSION DETECTION, ENCRYPTION, AND DATA INTEGRITY TO BOOST MARKET
- 13.3 APPLICATION SECURITY
- 13.3.1 NEED FOR SECURING APPLICATIONS AGAINST DATA BREACHES TO DRIVE MARKET
- 13.4 NETWORK SECURITY
- 13.4.1 NEED FOR INTEGRATION OF ADVANCED ENCRYPTION, INTRUSION DETECTION SYSTEMS, AND SECURE GATEWAYS TO BOOST MARKET
- 13.5 CLOUD SECURITY
- 13.5.1 INCREASED RELIANCE OF CONNECTED VEHICLES ON CLOUD FOR OTA UPDATES AND REAL-TIME NAVIGATION TO DRIVE MARKET
14 CONNECTED CAR SECURITY MARKET, BY SOLUTION TYPE
- 14.1 INTRODUCTION
- 14.2 SOFTWARE-BASED SOLUTIONS
- 14.2.1 POPULARITY OF TELEMATICS, CLOUD CONNECTIVITY, ADAS, AND V2X COMMUNICATION TO BOOST GROWTH
- 14.3 HARDWARE-BASED SOLUTIONS
- 14.3.1 NEED FOR PREVENTING UNAUTHORIZED ACCESS, TAMPERING, AND SYSTEM MANIPULATION TO BOOST MARKET
15 CONNECTED CAR SECURITY MARKET, BY REGION
- 15.1 INTRODUCTION
- 15.2 ASIA PACIFIC
- 15.2.1 ASIA PACIFIC: MACROECONOMIC OUTLOOK
- 15.2.2 CHINA
- 15.2.2.1 Enforcement of stringent data rules for connected vehicles to drive market
- 15.2.3 JAPAN
- 15.2.3.1 Focus on strengthening connected car security amid digital shift to boost market
- 15.2.4 INDIA
- 15.2.4.1 Need for fast-track cybersecurity compliance for connected mobility to boost demand
- 15.2.5 SOUTH KOREA
- 15.2.5.1 Emphasis on enforcing stringent data rules for connected vehicles to boost market
- 15.2.6 REST OF ASIA PACIFIC
- 15.3 EUROPE
- 15.3.1 EUROPE: MACROECONOMIC OUTLOOK
- 15.3.2 UK
- 15.3.2.1 Need for new cybersecurity standards for connected vehicles to boost market
- 15.3.3 GERMANY
- 15.3.3.1 Focus on enforcing CSMS & SUMS compliance for new vehicles to drive market
- 15.3.4 FRANCE
- 15.3.4.1 Stringent enforcement of UNECE cybersecurity requirements to boost market
- 15.3.5 SPAIN
- 15.3.5.1 Innovation and rapid technological advancements to drive market
- 15.3.6 ITALY
- 15.3.6.1 Need for accelerating cybersecurity integration in smart mobility to drive market
- 15.3.7 REST OF EUROPE
- 15.4 NORTH AMERICA
- 15.4.1 NORTH AMERICA: MACROECONOMIC OUTLOOK
- 15.4.2 US
- 15.4.2.1 Focus on strengthening national security rules to drive market
- 15.4.3 CANADA
- 15.4.3.1 Need for advancing security of connected vehicles through comprehensive guidance to boost market
- 15.4.4 MEXICO
- 15.4.4.1 Awareness regarding critical importance of cybersecurity in automotive industry to drive market
- 15.5 REST OF THE WORLD
- 15.5.1 REST OF THE WORLD: MACROECONOMIC OUTLOOK
- 15.5.2 IRAN
- 15.5.2.1 Focus on secure connectivity to drive demand
- 15.5.3 SOUTH AFRICA
- 15.5.3.1 Rising adoption of connected mobility to drive market
16 COMPETITIVE LANDSCAPE
- 16.1 KEY PLAYER STRATEGIES/RIGHT TO WIN, 2022-2024
- 16.2 MARKET SHARE ANALYSIS, 2024
- 16.3 REVENUE ANALYSIS, 2020-2024
- 16.4 BRAND COMPARISON
- 16.5 COMPANY VALUATION AND FINANCIAL METRICS
- 16.6 COMPANY EVALUATION MATRIX: KEY PLAYERS, 2024
- 16.6.1 STARS
- 16.6.2 EMERGING LEADERS
- 16.6.3 PERVASIVE PLAYERS
- 16.6.4 PARTICIPANTS
- 16.6.5 COMPANY FOOTPRINT: KEY PLAYERS, 2024
- 16.6.5.1 Company footprint
- 16.6.5.2 Region footprint
- 16.6.5.3 Solution type footprint
- 16.6.5.4 Security type footprint
- 16.7 COMPANY EVALUATION MATRIX: STARTUPS/SMES, 2024
- 16.7.1 PROGRESSIVE COMPANIES
- 16.7.2 RESPONSIVE COMPANIES
- 16.7.3 DYNAMIC COMPANIES
- 16.7.4 STARTING BLOCKS
- 16.7.5 COMPETITIVE BENCHMARKING: STARTUPS/SMES, 2024
- 16.7.5.1 Detailed list of key startups/SMEs
- 16.7.5.2 Competitive benchmarking of key startups/SMEs
- 16.8 COMPETITIVE SCENARIO
- 16.8.1 PRODUCT LAUNCHES/ENHANCEMENTS
- 16.8.2 DEALS
17 COMPANY PROFILES
- 17.1 KEY PLAYERS
- 17.1.1 AUMOVIO SE
- 17.1.1.1 Business overview
- 17.1.1.2 Products/Solutions/Services offered
- 17.1.1.3 Recent developments
- 17.1.1.3.1 Product launches/enhancements
- 17.1.1.3.2 Deals
- 17.1.1.3.3 Expansion
- 17.1.1.4 MnM view
- 17.1.1.4.1 Key strengths
- 17.1.1.4.2 Strategic choices
- 17.1.1.4.3 Weaknesses and competitive threats
- 17.1.2 BLACKBERRY LIMITED
- 17.1.2.1 Business overview
- 17.1.2.2 Products/Solutions/Services offered
- 17.1.2.3 Recent developments
- 17.1.2.3.1 Product launches/enhancements
- 17.1.2.3.2 Deals
- 17.1.2.4 MnM view
- 17.1.2.4.1 Key strengths
- 17.1.2.4.2 Strategic choices
- 17.1.2.4.3 Weaknesses & competitive threats
- 17.1.3 VECTOR INFORMATIK GMBH
- 17.1.3.1 Business overview
- 17.1.3.2 Products/Solutions/Services offered
- 17.1.3.3 Recent developments
- 17.1.3.3.1 Product launches/enhancements
- 17.1.3.3.2 Deals
- 17.1.3.4 MnM view
- 17.1.3.4.1 Key strengths
- 17.1.3.4.2 Strategic choices
- 17.1.3.4.3 Weaknesses and competitive threats
- 17.1.4 NXP SEMICONDUCTORS
- 17.1.4.1 Business overview
- 17.1.4.2 Products/Solutions/Services offered
- 17.1.4.3 Recent developments
- 17.1.4.3.1 Deals
- 17.1.4.4 MnM view
- 17.1.4.4.1 Key strengths
- 17.1.4.4.2 Strategic choices
- 17.1.4.4.3 Weaknesses and competitive threats
- 17.1.5 HARMAN INTERNATIONAL
- 17.1.5.1 Business overview
- 17.1.5.2 Products/Solutions/Services offered
- 17.1.5.3 Recent developments
- 17.1.5.3.1 Deals
- 17.1.5.4 MnM view
- 17.1.5.4.1 Key strengths
- 17.1.5.4.2 Strategic choices
- 17.1.5.4.3 Weaknesses and competitive threats
- 17.1.6 UPSTREAM SECURITY LTD.
- 17.1.6.1 Business overview
- 17.1.6.2 Products/Solutions/Services offered
- 17.1.6.3 Recent developments
- 17.1.6.3.1 Product launches/enhancements
- 17.1.6.3.2 Deals
- 17.1.7 ASTEMO, LTD.
- 17.1.7.1 Business overview
- 17.1.7.2 Products/Solutions/Services offered
- 17.1.7.3 Recent developments
- 17.1.7.3.1 Deals
- 17.1.7.3.2 Expansion
- 17.1.8 TRUSTONIC
- 17.1.8.1 Business overview
- 17.1.8.2 Products/Solutions/Services offered
- 17.1.8.3 Recent developments
- 17.1.8.3.1 Product launches/enhancements
- 17.1.8.3.2 Deals
- 17.1.9 KPIT
- 17.1.9.1 Business overview
- 17.1.9.2 Products/Solutions/Services offered
- 17.1.9.3 Recent developments
- 17.1.9.3.1 Deals
- 17.1.10 THALES
- 17.1.10.1 Business overview
- 17.1.10.2 Products/Solutions/Services offered
- 17.1.10.3 Recent developments
- 17.1.10.3.1 Product launches/enhancements
- 17.1.10.3.2 Deals
- 17.1.11 T-SYSTEMS INTERNATIONAL GMBH
- 17.1.11.1 Business overview
- 17.1.11.2 Products/Solutions/Services offered
- 17.1.11.3 Recent developments
- 17.1.11.3.1 Product launches/enhancements
- 17.1.11.3.2 Deals
- 17.1.12 AUTOCRYPT CO., LTD.
- 17.1.12.1 Business overview
- 17.1.12.2 Products/Solutions/Services offered
- 17.1.12.3 Recent developments
- 17.1.12.3.1 Product launches/enhancements
- 17.1.12.3.2 Deals
- 17.1.1 AUMOVIO SE
- 17.2 OTHER PLAYERS
- 17.2.1 ARM LIMITED
- 17.2.2 TREND MICRO INCORPORATED
- 17.2.3 ETAS
- 17.2.4 KEYSIGHT TECHNOLOGIES
- 17.2.5 INTERTEK GROUP PLC
- 17.2.6 DEVICE AUTHORITY
- 17.2.7 SECUNET SECURITY NETWORKS AG
- 17.2.8 TRILLIUM SECURE, INC.
- 17.2.9 WIRELESSCAR
- 17.2.10 KARAMBA SECURITY
- 17.2.11 INTERTRUST TECHNOLOGIES CORPORATION
- 17.2.12 GUARDKNOX
- 17.2.13 TATA ELXSI
18 APPENDIX
- 18.1 DISCUSSION GUIDE
- 18.2 KNOWLEDGESTORE: MARKETSANDMARKETS' SUBSCRIPTION PORTAL
- 18.3 CUSTOMIZATION OPTIONS
- 18.4 RELATED REPORTS
- 18.5 AUTHOR DETAILS



















