
|
시장보고서
상품코드
1640695
고급 인증 - 시장 점유율 분석, 산업 동향 및 통계, 성장 예측(2025-2030년)Advanced Authentication - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
고급 인증 시장 규모는 2025년에 181억 5,000만 달러로 추정되며, 예측 기간(2025-2030년)의 CAGR은 13.2%를 나타낼 전망이며, 2030년에는 337억 3,000만 달러에 달할 것으로 예측됩니다.

이동성의 점진적인 도입과 기업 차원에서 직원, 파트너, 기타 이해관계자가 보다 기밀성이 높은 정보에 액세스할 방법을 모색하는 노력이 고급 인증 시장을 견인하고 있습니다. 보안 위협은 점점 증가 추세에 있으며 해커는 데이터를 훔치는 새로운 방법을 연구하고 기업과 개인 사용자로부터 기밀 정보를 훔치는 새로운 바이러스를 개발하고 있습니다. 대부분의 사용자가 온라인 거래를 선호하게 된 현재 편리하고 안전한 액세스를 보장하는 인증 솔루션의 도입은 조직에 필수적입니다.
주요 하이라이트
- 모든 조직은 사실 관계와 개인의 신원 확인을 확인하기 위해 신뢰할 수 있는 보안 시스템이 필요합니다. 기본 및 전통적인 암호는 깨지거나 복사되거나 공유되어 데이터가 도난당하거나 해킹될 위험이 있습니다.
- 모빌리티의 채용이 증가하고 있는 점도 고급 인증 솔루션 시장의 성장에 기여하고 있는 요인입니다. 기업은 직원, 파트너 및 기타 이해관계자가 어디서나 모든 기기에서 더 민감한 정보에 액세스할 수 있도록 해야 한다는 필요성을 인식하고 있습니다. 따라서 고급 인증 시스템은 기업의 조직 전략에 중요한 측면이 되었습니다.
- 고급 인증 솔루션 공급업체는 기존 인증 방법을 개발하고 개선했습니다. 가장 일반적으로 사용되는 인증 방법은 생체 인식, 스마트 카드, 토큰 등이며 이를 통해 보안 위험을 줄입니다.
- 또한 기업은 보안을 강화하기 위해 사용자의 2단계 인증을 자동으로 활성화하고 있습니다. 예를 들어 Google은 작년에 이 작업을 발표했으며 보도 자료에서 활성화 작업을 통해 비밀번호 도난 계정 수가 50% 감소했다고 발표한 후 2022년 2월 1억 5천만 명 이상의 사용자에 대해 2단계 인증을 활성화했습니다. 이 정책은 200만 명의 YouTube 사용자에게도 활성화를 요구합니다.
- COVID-19 기간 동안 사이버 범죄자는 불안정한 사회 경제 상황에 의한 불안과 공포감을 이용하였고 그 결과 역대 최대치의 사이버 공격이 발생하였습니다. 인터폴은 COVID-19가 사이버 범죄에 미친 영향을 조사한 결과 주요 범죄 대상이 개인과 중소기업에서 대기업, 주요 인프라 및 정부로 변했음을 밝혔습니다.
또한 POLITICO의 분석에 따르면 미국에서는 지난해 약 5,000만 명이 기밀 건강 데이터를 침해당했고 이는 지난 3년간 3배로 증가한 수치입니다. 작년에 사우스 다코타를 제외한 모든 주의 의료 제공업체와 보험 회사에서 이러한 유형의 문제가 보고되었습니다. 따라서 앞으로 수년간 고급 인증의 필요성이 높아졌습니다.
고급 인증 시장 동향
바이오메트릭스가 예측 기간 동안 큰 시장 점유율을 차지
- 바이오메트릭스는 지문, 망막, 홍채, 손바닥, 음성 등 인간의 신체적 특징을 바탕으로 개인을 분석 및 인증하는 기술입니다. 이 인증 기술은 부인이 불가하고 양도할 수 없으며 특정 불가능하다는 장점으로 인해 널리 채택되고 있으며 부정 행위로부터 고도의 보호를 제공합니다.
- 이 기술은 포렌식, 정부, 은행 및 금융 기관, 기업 ID 관리 등 다양한 최종 사용자에 걸쳐 성공적으로 도입되었습니다. 게다가 저렴한 모바일 기기에 지문 센서가 널리 탑재되게 된 점이나 정부의 국민 신분증 프로그램에 의해 이 기술의 인지도와 채용률이 높아지고 있습니다.
- 2022년 9월, 도로 교통 및 고속도로부(MoRTH)는 시민들이 Aadhaar 디지털 ID를 사용하여 여러 교통 관련 서비스를 온라인으로 이용할 수 있는 서비스를 발표하였습니다. 이러한 서비스를 비접촉 및 비대면으로 제공함으로써 시민의 규제 준수 부담을 경감함과 동시에 시간을 크게 절약할 수 있습니다.
- 또한 2022년 5월 Mastercard는 생체인증 기준을 설정하는 프로그램을 시작하여 소비자는 미소 만으로도 결제할 수 있게 되었습니다. 이 회사의 바이오메트릭 결제 프로그램은 바이오메트릭 결제 인증 서비스를 개발하는 은행, 가맹점 및 기술 제공업체에 대한 기술 보안 및 개인정보 보호 기준을 설정하는 프레임워크입니다.
- 파키스탄에서는 2022년 6월 국가 데이터베이스등록국(Nadra)과 수도 개발국(CDA)은 이슬라마바드에서 보다 안전한 재산 이전을 위한 종합적인 생체인증 시스템을 개발하는 계약을 체결했습니다. 이 시스템은 이슬라마바드에서 부동산 양도 사기를 줄이고 불법적인 수단과 사기꾼에 의한 속임수를 제거하는 데 도움이 됩니다. CDA에서는 연간 약 2만건의 부동산 매매 양도 거래가 행해지고 있습니다.
북미가 큰 시장 점유율을 차지
- 미국 내 조직은 일상 업무를 수행함에 있어서 컴퓨터 네트워크와 전자 데이터에 대한 의존도를 높이고 있으며, 개인정보와 재무정보도 온라인으로 전송 또는 보존되는 경우가 늘고 있습니다. 사람들은 매일 거래에 온라인 서비스를 사용하는 경향이 증가하고 있으며 따라서 고급 인증 서비스의 중요성이 높아지고 있습니다.
- 또한, 국가의 조직 범죄에 관여하는 전문적인 ID 탈취의 정교한 수준은 계속 증가하고 있으며, 국가적으로 기업에 의한 조치의 필요성이 발생하고 있습니다. 또한 BYOD 동향은 점점 커지고 있으며 스마트 카드, 물리적 토큰, KPI(Key Performance Indicator) 등의 고급 인증 방법이 기밀 정보에 액세스하거나 클라이언트 서버에 로그인하는 데 점점 도입되고 있습니다.
- 인증을 보다 안전하게 하기 위해 은행, 소매, 의료 등 이 지역의 많은 최종 사용자 산업은 마이크로칩이 장착된 신용카드 및 직불카드뿐만 아니라 온라인 및 클라우드 서비스에 양방향 인증 시스템을 추가하고 있습니다.
- 2022년 10월, ID 인증 소프트웨어 제조업체인 Mitek Systems는 멀티모달 생체인증을 이용한 비밀번호가 없는 인증 플랫폼을 발표했습니다. 이 플랫폼은 사용자가 셀카 사진을 찍거나 휴대전화에서 문구를 말하여 디지털 계정에 액세스할 수 있도록 합니다. 이러한 시장 개척이 북미 시장을 뒷받침하고 있습니다.
또한 BIO-Key International Inc.는 2022년 5월 BIO-Key MobileAuth를 업그레이드하여 다중 인증 솔루션의 필요성을 줄일 것으로 예상한다고 발표했습니다. 새로운 생체인식 및 푸시 토큰 인증 옵션을 통해 보다 광범위한 이용 사례를 지원하고 기존 인증의 불충분성을 해결할 수 있습니다.
고급 인증 산업 개요
고급 인증시장은 경쟁이 치열하며 여러 대형 기업으로 구성되어 있습니다. 시장 점유율에서 현재 여러 회사가 시장을 독점하고 있습니다. 시장에서 압도적인 점유율을 가진 대기업은 해외 고객 기반 확대에 주력하고 있습니다. 이러한 기업들은 시장 점유율과 수익성을 높이기 위해 전략적 협력 이니셔티브를 활용합니다.
2022년 10월, NEC 말레이시아는 IRIS Corporation Berhad(IRIS)의 자회사인 IRIS Information Technology Systems Sdn Bhd(IITS)가 말레이시아의 국가 통합 입국 관리 시스템(NIISe)에 국경 관리 솔루션 및 자동 생체 인증 시스템을 도입하기 위한 기술 파트너로 선정되었습니다.
2022년 10월, Experian과 Prove Identity Inc.는 고급 본인 확인 기술을 통해 금융 포섭을 추진하는 세계 파트너십을 발표했습니다. 이 제휴를 통해 기업은 암호화 인증과 같은 고도의 본인 확인 기술을 활용할 수 있어 더 많은 소비자를 빠르고 안전하게 확인할 수 있습니다.
기타 혜택
- 엑셀 형식 시장 예측(ME) 시트
- 3개월간의 애널리스트 서포트
목차
제1장 서론
- 조사의 전제조건
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 인사이트
- 시장 개요
- 산업 밸류체인 분석
- 산업의 매력 - Porter's Five Forces 분석
- 신규 참가업체의 위협
- 구매자 및 소비자의 협상력
- 공급기업의 협상력
- 대체품의 위협
- 경쟁 기업간 경쟁 관계
- 정부의 규제와 시책
- 기술 스냅샷
- 기술 개요
- 전개 방법
- 다양한 인증 방법
- 고급 인증 용도
제5장 시장 역학
- 촉진요인
- 클라우드 사용자 수와 데이터센터 수 증가
- 보안 침해 건수와 관련 비용 증가
- 억제요인
- 높은 업그레이드 및 교체 비용
제6장 시장 세분화
- 인증 방식
- 스마트 카드
- 바이오메트릭스
- 모바일 스마트 자격증
- 토큰
- 사용자 기반 공개 키 인프라
- 기타 인증 방법
- 최종 사용자 산업
- BFSI
- 의료
- 정부기관
- 방어
- IT 및 텔레콤
- 기타
- 지역
- 북미
- 미국
- 캐나다
- 유럽
- 영국
- 독일
- 프랑스
- 이탈리아
- 기타 유럽
- 아시아태평양
- 중국
- 인도
- 일본
- 호주
- 기타 아시아태평양
- 라틴아메리카
- 멕시코
- 브라질
- 아르헨티나
- 기타 라틴아메리카
- 중동 및 아프리카
- 아랍에미리트(UAE)
- 사우디아라비아
- 남아프리카
- 기타 중동 및 아프리카
- 북미
제7장 경쟁 구도
- 기업 프로파일
- Fujitsu Ltd.
- Thales Group(Gemalto NV)
- NEC Corp.
- Broadcom Inc.(CA Technologies)
- Dell Technologies Inc.
- Safran Identity and Security SAS
- Lumidigm Inc.
- Validsoft
- Pistolstar
- Securenvoy
제8장 투자 분석
제9장 시장 기회와 앞으로의 동향
CSM 25.02.17The Advanced Authentication Market size is estimated at USD 18.15 billion in 2025, and is expected to reach USD 33.73 billion by 2030, at a CAGR of 13.2% during the forecast period (2025-2030).
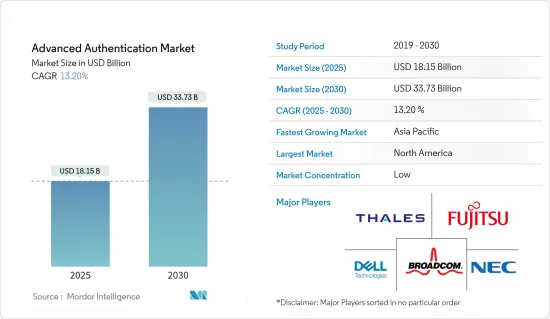
Factors driving the Advanced Authentication Market include increased adoption of mobility, and enterprises are feeling pressure to enable employees, partners, and other stakeholders to access more sensitive information. Security threats have been increasing continuously. Hackers are finding new ways to steal data, while new viruses are being developed to steal sensitive information from enterprises and individual users. With most users now preferring to perform transactions online, it becomes imperative for the organization to deploy authentication solutions that help ensure convenient and secure access.
Key Highlights
- Every organization needs a reliable security system to confirm the truth of something or a person's identity. Too often, the basic or traditional password method is broken, copied, or shared, putting data at risk of being stolen or hacked.
- The increased adoption of mobility is the other factor contributing to the growth of the market for advanced authentication solutions. Enterprises are feeling pressure to enable employees, partners, and other stakeholders to access more sensitive information from anywhere and on any device. This makes advanced authentication systems a critical aspect of an enterprise's organizational strategy.
- Vendors of advanced authentication solutions are developing and improving their existing authentication methods. Some of the most commonly used authentication methods are biometrics, smartcards, tokens, and several others for mitigating security risks.
- Further, companies are auto-enabling two-step verification for users for enhanced security. For instance, in February 2022, Google enabled two-step verification for more than 150 million users after announcing the effort last year and noting in a press release that the action had caused the number of accounts hijacked by password theft to decrease by 50%. The initiative has also involved requiring two million YouTube users to enable it.
- Cybercriminals have boosted their attacks at a rapid pace amid COVID-19, thereby exploiting the uncertainty and fear caused by the unstable social and economic situation. Interpol looked at how COVID-19 affected cybercrime and found that the main targets had changed from individuals and small businesses to large corporations, critical infrastructure, and governments.
Also, according to a POLITICO analysis, nearly 50 million people in the United States had their sensitive health data breached last year, a threefold increase in the last three years. Last year, these kinds of problems were reported by healthcare providers and insurers in every state except South Dakota. This increased the need for advanced authentication over the next few years.
Advanced Authentication Market Trends
Biometrics to Hold Significant Market Share During the Forecast Period
- Biometrics analyzes and authenticates individuals based on human physical characteristics, such as fingerprint, retina, iris, palm, speech, and voice, among others. This authentication method has been widely adopted, owing to its key advantages, namely its non-repudiation, non-transferable, and non-identifiable nature, thus providing a high level of protection against fraud.
- The technology has found successful implementation across various end-users, such as forensics, governments, banking and financial institutions, and enterprise identity management, among others. Moreover, the widespread availability of fingerprint sensors in affordable mobile devices and the government's national ID programs have increased awareness and adoption of this technology.
- In September 2022, The Ministry of Road Transport and Highways (MoRTH) issued a notification allowing citizens to access several transport-related services online with their Aadhaar digital ID. Providing such services in a contactless and faceless manner will go a long way in saving time for citizens while easing their compliance burden.
- Also, in May 2022, Mastercard launched a program to set biometric authentication standards, allowing consumers to pay with a smile. The company's Biometric Checkout Program is a framework to set technology security and privacy standards for banks, merchants, and technology providers developing biometric payment authentication services.
- Furthermore, in June 2022, National Database and Registration Authority (Nadra) and Capital Development Authority (CDA) signed an agreement to develop a comprehensive biometric verification system for safer property transfers in Islamabad. The system will help reduce forgery and eliminate deceptive attempts by illegitimate means or persons regarding the transfer of properties in Islamabad. Approximately 20,000 transactions of sale, purchase, and transfer of properties take place annually in CDA.
North America to Hold a Significant Market Share
- Organizations across the United States are increasingly dependent on computer networks and electronic data to conduct their daily operations, and growing pools of personal and financial information are also transferred and stored online. People are more likely to use online services for day-to-day transactions. This has made it more important for the country to have advanced authentication services.
- Moreover, the sophistication level of professional identity thieves involved in organized crime in the country continues to grow, creating a need for countermeasures to be used by companies in the country. Also, the BYOD trend is getting bigger and bigger, which makes it easier for advanced authentication methods like smart cards, physical tokens, and key performance indicators (KPIs) to be used to access sensitive information or log in to client servers.
- To make authentication more secure, many end-user industries across the region, such as banking, retail, and healthcare, have added two-way authentication systems to their online or cloud services, as well as credit and debit cards with microchips.
- In October 2022, Mitek Systems, an ID verification software maker, launched a passwordless authentication platform with multimodal biometrics. The platform enables users to access digital accounts by taking a selfie and speaking a phrase with their phone. Such developments are boosting the North American market under consideration.
Furthermore, BIO-Key International Inc announced that its BIO-Key MobileAuth will be upgraded in May 2022, eliminating the need for multiple authentication solutions. New biometric and push token authentication options to support a wider range of use cases and address the insufficiencies of traditional authentication.
Advanced Authentication Industry Overview
The advanced authentication market is highly competitive and consists of several major players. In terms of market share, few players currently dominate the market. These major players with prominent shares in the market are focusing on expanding their customer base across foreign countries. These companies leverage strategic collaborative initiatives to increase their market share and profitability.
In October 2022, NEC Malaysia was selected as a technology partner for the implementation of its border Control Solution and Automated Biometric Identification System for Malaysia's National Integrated Immigration System (NIISe), IRIS Information Technology Systems Sdn Bhd (IITS), a subsidiary of IRIS Corporation Berhad (IRIS).
In October 2022, Experian and Prove Identity Inc announced a global partnership to further financial inclusion through advanced identity verification technology. The partnership will give more access to companies for advanced identity technology, such as cryptographic authentication, that they can use to verify more consumers in a quick and secure manner.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Value Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Force Analysis
- 4.3.1 Threat of New Entrants
- 4.3.2 Bargaining Power of Buyers/Consumers
- 4.3.3 Bargaining Power of Suppliers
- 4.3.4 Threat of Substitute Products
- 4.3.5 Intensity of Competitive Rivalry
- 4.4 Government Policies and Industry Regulations
- 4.5 TECHNOLOGY SNAPSHOT
- 4.5.1 Technology Overview
- 4.5.2 Deployment Methods
- 4.5.3 Different Authentication Methods
- 4.5.4 Advanced Authentication Applications
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Increased Number of Cloud Users and Data Centers
- 5.1.2 Increasing Number of Security Breaches and Related Costs
- 5.2 Market Restraints
- 5.2.1 High Upgrade and Replacement Costs
6 MARKET SEGMENTATION
- 6.1 Authentication Methods
- 6.1.1 Smart Cards
- 6.1.2 Biometrics
- 6.1.3 Mobile Smart Credentials
- 6.1.4 Tokens
- 6.1.5 User-based Public Key Infrastructure
- 6.1.6 Other Authentication Methods
- 6.2 End-user Industry
- 6.2.1 BFSI
- 6.2.2 Healthcare
- 6.2.3 Government
- 6.2.4 Defense
- 6.2.5 IT and Telecom
- 6.2.6 Other End-user Industries
- 6.3 Geography
- 6.3.1 North America
- 6.3.1.1 United States
- 6.3.1.2 Canada
- 6.3.2 Europe
- 6.3.2.1 United Kingdom
- 6.3.2.2 Germany
- 6.3.2.3 France
- 6.3.2.4 Italy
- 6.3.2.5 Rest of Europe
- 6.3.3 Asia-Pacific
- 6.3.3.1 China
- 6.3.3.2 India
- 6.3.3.3 Japan
- 6.3.3.4 Australia
- 6.3.3.5 Rest of Asia-Pacific
- 6.3.4 Latin America
- 6.3.4.1 Mexico
- 6.3.4.2 Brazil
- 6.3.4.3 Argentina
- 6.3.4.4 Rest of Latin America
- 6.3.5 Middle East & Africa
- 6.3.5.1 United Arab Emirates
- 6.3.5.2 Saudi Arabia
- 6.3.5.3 South Africa
- 6.3.5.4 Rest of Middle East & Africa
- 6.3.1 North America
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 Fujitsu Ltd.
- 7.1.2 Thales Group (Gemalto NV)
- 7.1.3 NEC Corp.
- 7.1.4 Broadcom Inc. (CA Technologies)
- 7.1.5 Dell Technologies Inc.
- 7.1.6 Safran Identity and Security SAS
- 7.1.7 Lumidigm Inc.
- 7.1.8 Validsoft
- 7.1.9 Pistolstar
- 7.1.10 Securenvoy














