
|
시장보고서
상품코드
1445837
데이터 보안 : 시장 점유율 분석, 산업 동향 및 통계, 성장 예측(2024-2029년)Data Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2024 - 2029) |
||||||
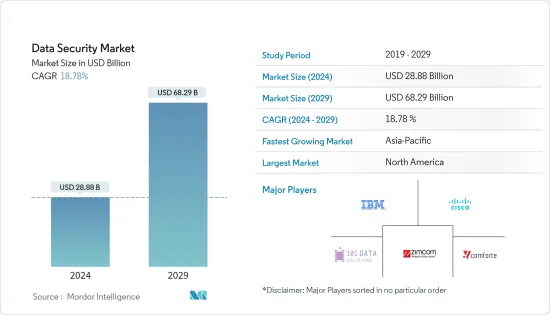
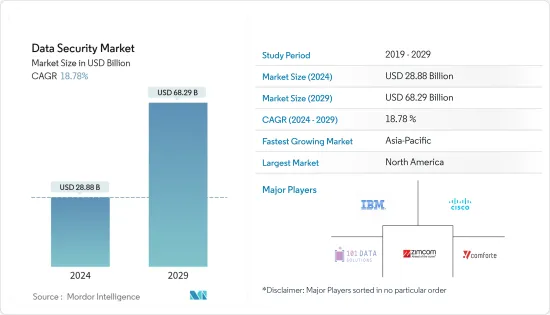
데이터 보안 시장 규모는 2024년 288억 8,000만 달러로 추정됩니다. 2029년까지 682억 9,000만 달러에 달할 것으로 예측되며, 예측 기간(2024-2029년) 동안 18.78%의 연평균 복합 성장률(CAGR)을 나타낼 것으로 예상됩니다.
대량의 데이터와 상업용 데이터 저장 및 마이닝과 같은 정보 용도으로 인해 데이터 양이 증가하고 있습니다. 이러한 용도는 동적이고 다기능입니다. 데이터 보안은 데이터의 신뢰성과 무결성을 유지하고 공격을 방지하기 위해 매우 중요합니다. 또한 해커들은 Odinaff, Danabot, Camubot, Backswap과 같은 악성코드를 도입하여 보안 위협에 대한 데이터 취약성을 증가시켰으며, 이로 인해 기업과 고객은 보다 효과적인 보안 솔루션을 요구하고 있습니다.
주요 하이라이트
- 전략국제문제연구소(CSIS)와 맥아피에 따르면 사이버 범죄는 전 세계적으로 연간 약 6,000억 달러, 즉 세계 GDP의 0.8%에 해당하는 피해를 입히고 있으며, 여기에는 데이터 손상 및 파괴, 금전 도난, 재산 분실, 지적 재산권 도난 등이 포함됩니다. 기타 분야. 이러한 요인으로 인해 보안 및 취약성 관리 소프트웨어 및 서비스 개발이 가속화될 것으로 예상됩니다.
- 디지털화 추세와 디지털 데이터 생성 증가로 인해 데이터 보안 시장에 대한 수요가 증가하고 있습니다. 디지털 데이터 생성은 지난 수십년동안 급격하게 증가했으며, 이러한 추세는 앞으로도 계속될 것으로 예상됩니다. 스마트폰, 노트북 등 디지털 기기의 일상적인 사용 증가는 디지털 데이터 생성 증가를 유발하는 주요 요인 중 하나입니다. 또한 사물인터넷(IoT)의 인기와 수많은 IoT 기기에서 생성되는 데이터로 인해 데이터 보안 시장이 확대되고 있습니다.
- 조직이 운영하는 분야나 업종에 관계없이 데이터 침해로부터 시스템을 보호하기 위해 디지털 혁신을 추진하는 기업들은 GDPR(EU 개인정보보호규정)(EU 개인정보보호규정), PCI DSS, ISO와 같은 엄격한 법규를 준수해야 합니다. 규제와 컴플라이언스로 인해 기업들은 데이터 보안 시장의 성장을 지원하는 효율적인 보안 솔루션을 구현해야 합니다.
- 데이터 감사, 데이터 실시간 경보, 데이터 위험 평가, 데이터 최소화, 오래된 데이터 삭제와 같은 데이터 보안 기술을 도입하면 조직이 침해 방지, 위험 감소, 데이터 유출 방지를 위한 보호 보안 조치를 유지하는 데 도움이 될 수 있습니다.
- 다양한 출처에서 수집된 정형 및 비정형 데이터에서 기밀 데이터를 찾아내고 분석하는 것은 큰 문제가 되고 있으며, 이는 시장 성장을 저해할 것으로 예상됩니다. 또한, 차세대 방화벽(NGFW) 및 지능형 위협 보호(ATP) 기술을 도입하기 위해서는 젊은 스타트업의 사이버 보안 예산을 늘려야 합니다. 신흥국 중소기업은 자본 부족, 투자 제한 등의 심각한 문제로 인해 데이터 보안 솔루션 도입에 대한 지원이 필요합니다.
- 많은 직원들이 재택근무를 하고 기업 데이터에 접속하는 것이 더 중요해지면서 정부, 공공 기관 및 민간 기업은 코로나19의 영향으로 피싱 공격을 극복하기 위해 많은 노력을 기울이고 있습니다. 또한, 팬데믹 기간 동안 타사 용도의 사용이 크게 증가했습니다. 이러한 모든 요인으로 인해 IT 인프라는 바이러스 및 사이버 공격에 더 취약해졌습니다. 기업들은 보안 조치를 강화할 필요가 있으며, 이는 세계 데이터 보안 시장에도 도움이 되고 있습니다. 예를 들어, 코로나19와 관련된 스피어 피싱 이메일 공격은 작년 12월 이후 67% 증가했습니다.
데이터 보안 시장 동향
데이터 보안 기술, 가장 큰 자산으로 자리매김
- 강력한 데이터 보안 전략은 조직이 컴플라이언스를 준수하고 소매, 금융, 의료, 정부 등 다양한 산업에서 위협에 대한 노출을 줄이는 데 도움이 됩니다. 데이터는 기밀성, 무결성, 가용성 원칙에 따라 사용될 때 조직이 의사결정을 개선하고 전략적 이니셔티브를 실행하며 고객 및 비즈니스 파트너와의 관계를 강화하는 데 도움이 되는 가장 가치 있는 리소스가 될 수 있습니다.
- 데이터 보안 기술에는 방화벽, 인증 및 권한 부여, 암호화, 데이터 마스킹, 하드웨어 기반 보안, 데이터 백업 및 복원력, 데이터 삭제 등이 포함됩니다. 데이터 보안은 비즈니스 운영, 개발 및 재무에 중요한 역할을 합니다. 데이터를 보호함으로써 기업은 데이터 침해와 평판 훼손을 방지하고 규제 요건을 더 잘 충족시킬 수 있습니다. ThoughtLab의 보고서에 따르면 전년도 데이터 침해 건수는 15.1% 증가했습니다. 또한 IDG 보고서에 따르면 CIO의 68%는 향후 몇 년동안 데이터 보안에 대한 지출이 증가할 것으로 예상했습니다.
- AI와 멀티 클라우드 서비스는 데이터 보안에서 중요한 역할을 합니다. 인공지능(AI)은 데이터 피싱과 사이버 공격이 날로 증가하는 가운데 보안 운영 분석가들이 위협과 위험을 미리 예측하고 중요한 의사결정을 내리고 문제를 해결할 수 있도록 돕습니다. 현재 기업은 다양한 소스에서 데이터를 축적하고 있기 때문에 정보 보안은 기업에게 가장 중요한 요소입니다. 데이터 보안에 있어 AI와 ML은 보안 분석가가 당국의 데이터 도난을 방지하는 데 걸리는 시간을 단축하는 데 도움이 될 수 있습니다. AI와 ML은 제공된 알고리즘을 사용하여 정보를 보호하는 데 중점을 두기 때문에 특정 위협이 어떻게 분류되는지 학습할 수 있습니다. 이러한 기술을 사용하면 시스템의 비정상적인 동작을 빠르게 스캔하여 이상 징후가 잠재적 위협으로 분류될 수 있는지 여부를 판단할 수 있습니다.
- 최첨단 비즈니스의 대부분은 멀티 클라우드 서비스에 의존하고 있습니다. 이러한 서비스는 다양한 클라우드 컴퓨팅 서비스 제공업체를 활용하여 조직에 종합적인 보안 솔루션을 제공하기 위해 다양한 가능성을 제공합니다. 이 서비스를 통해 기업은 유연성을 높이고, 비용 관리를 개선하며, 복원력을 향상시킬 수 있습니다. 멀티 클라우드 기술과 프로세스를 사용하여 단일 인터페이스에서 다양한 퍼블릭 클라우드의 워크로드를 모니터링하고 관리할 수 있어 데이터 유출을 줄이고 데이터 보안을 강화할 수 있습니다.
- 클라우드 데이터 보안 소프트웨어는 클라우드 서비스 또는 클라우드 기반 용도를 사용하여 저장된 정보를 보호합니다. 이러한 도구는 클라우드 액세스 제어 및 스토리지 정책을 적용하여 데이터 보안을 촉진할 수 있습니다. 기업은 이 도구를 사용하여 보안 프로토콜을 구현하고, 액세스를 모니터링하고, 클라우드 애플리케이션에 저장된 정보 및 클라우드 애플리케이션을 통해 전송되는 정보를 보호합니다.
아시아태평양 시장 확대
- 데이터 보안 솔루션은 인터넷 기술의 급속한 보급과 다양한 산업 분야의 기기 수 증가로 인해 예측 기간 동안 수요가 증가할 것으로 예상됩니다. 이러한 연결된 기기에 대한 공격과 데이터 피싱 증가도 국립정보통신연구원에 의해 예측되고 있습니다. 이러한 사건은 기업이 이러한 사고의 가능성을 예측할 수 있는 솔루션을 개발하도록 장려함으로써 데이터 보안 시장을 촉진할 것입니다.
- 아시아태평양에서는 국내외 고객에게 서비스를 제공하는 대기업이 VPN, 엔드포인트 보호, 보안 테스트와 같은 보안 관련 제품에 대한 정부 및 기업의 투자가 증가하고 있습니다.
- 아시아 시장에서 눈에 띄는 추세는 의료, 은행 업무, 여행, 접객 서비스 등에 접근하기 위해 BYOD와 같은 IoT 기기의 사용이 증가하고 있다는 점입니다. 이러한 증가 추세는 데이터 보안 업계에 큰 기회로 작용하고 있습니다. SPDI 규칙에 따르면 비밀번호, 금융 정보, 의료 기록 등을 포함한 기밀 데이터와 개인 데이터는 보호되어야 하며, 정당한 목적과 관련이 없는 한 개인의 필요에 따라 악용될 수 없습니다. 따라서 데이터 유출을 방지하려면 효과적인 데이터 보안 기술을 구현해야 합니다.
- 클라우드 컴퓨팅, 모바일 기술, 소셜 미디어 증가와 함께 데이터 보안 침해에 대한 보고가 아시아태평양 국가에서 확산되고 있습니다. 예를 들어, 지난해 7월 파이브 아이즈 국가(미국, 캐나다, 영국, 호주, 뉴질랜드)는 NATO와 함께 마이크로소프트 익스체인지(Microsoft Exchange) 해킹과 의학 연구 기관 및 대학에 충격을 안겨주었습니다.
데이터 보안 산업 개요
경쟁이 치열한 데이터 보안 업계에는 수많은 유명 기업들이 존재합니다. 현재 가장 유명한 기업 중 일부는 시장 점유율 측면에서 시장을 독점하고 있습니다. 그러나 보안 서비스가 발전함에 따라 새로운 기업이 시장에서 널리 보급되어 비즈니스의 지리적 범위를 확장하고 있습니다. 필요한 데이터 보안 수준에 따라 기업은 다양한 시스템에 저장된 데이터를 보다 의식적으로 인식하고 있습니다. 그 결과 중소기업은 IBM, McAfee, Intel, Cybereason, Verizon, AT&T와 같은 회사의 서비스를 사용하기 시작했습니다.
- 데이터 보안 및 분석의 선구자인 Varonis Systems, Inc.는 2022년 6월, Amazon Simple Storage Service(S3)의 보안을 강화하고 데이터 가시성을 향상시키는 새로운 기능을 발표했습니다. 이를 통해 고객은 단일 화면에서 중요한 데이터를 보호할 수 있습니다. IaaS 및 SaaS 생태계.
- 2022년 3월, IT 및 데이터 보안 관리 솔루션의 선두주자인 Syxsense의 모바일 디바이스 관리(MDM) 솔루션은 디바이스 등록, 인벤토리, 구성 관리, 용도 배포 등 모바일 엔드포인트에 효과적인 관리를 적용하는 데 필요한 모든 툴을 포함합니다. 모바일 엔드포인트에 효과적인 관리를 적용하는 데 필요한 모든 도구가 포함되어 있습니다. 롤백, 데이터 컨테이너화, 원격 기기 잠금/리셋/지우기 기능을 통해 기술 전문 지식이 분실 또는 도난당한 기기에서 기밀 데이터를 삭제하여 데이터 보안을 제공할 수 있습니다.
기타 혜택
- 엑셀 형식 시장 예측(ME) 시트
- 3개월간 애널리스트 지원
목차
제1장 서론
- 조사의 전제조건과 시장 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 역학
- 시장 개요
- 시장 성장 촉진요인
- 시장 성장 억제요인
- 업계 밸류체인 분석
- 업계의 매력 - Porter의 Five Forces 분석
- 공급 기업의 교섭력
- 소비자의 교섭력
- 신규 진출업체의 위협
- 대체 제품의 위협
- 경쟁 기업간 경쟁도
- COVID-19 감염증이 시장에 미치는 영향 평가
제5장 시장 세분화
- 컴포넌트별
- 솔루션
- 서비스
- 전개 형태별
- 클라우드
- 온프레미스
- 조직 규모별
- 중소기업
- 대기업
- 최종사용자 업계별
- 소매
- 헬스케어
- 제조업
- 은행/금융서비스/보험(B
- 정부
- IT 및 통신
- 기타 최종사용자 산업
- 지역
- 북미
- 유럽
- 아시아태평양
- 라틴아메리카
- 중동 및 아프리카
제6장 경쟁 구도
- 기업 개요
- IBM Corporation
- Cisco Systems Inc
- 101 Data Solutions
- Microsoft Corporation
- Zimcom Internet Solutions
- Comforte AG
- Thales
- Lepide USA Inc
- Varonis Systems Inc
- Checkpoint Software Technologies Ltd
- Oracle Corporation
제7장 투자 분석
제8장 시장 기회와 향후 동향
LSH 24.03.19The Data Security Market size is estimated at USD 28.88 billion in 2024, and is expected to reach USD 68.29 billion by 2029, growing at a CAGR of 18.78% during the forecast period (2024-2029).
Data volumes have been growing because of information applications, including storing and mining massive or commercial data. These applications are dynamic and multifunctional. Data Security is crucial for preserving the authenticity and integrity of the data as well as for preventing attacks. Additionally, hackers are deploying malware like Odinaff, Danabot, Camubot, Backswap, etc., which has increased data vulnerability to security threats, leading businesses and customers to demand more effective security solutions.
Key Highlights
- According to the Center for Strategic and International Studies (CSIS) and McAfee, cybercrimes cost the globe around USD 600 billion annually, or 0.8% of global GDP, and encompass data damage and destruction, money theft, lost property, intellectual property theft, and other sectors. The development of security and vulnerability management software and services is anticipated to be accelerated by such causes.
- The need for the data security market has grown due to rising digitalization trends and digital data generation. The creation of digital data has dramatically expanded over the last few decades, and this trend is anticipated to continue. The growing daily use of digital devices like smartphones and laptops is one of the main factors causing this rise in digital data generation. Additionally, the Data Security Market has expanded due to the rising popularity of the Internet of Things (IoT) and the data produced by numerous IoT devices.
- Strict laws, like GDPR, PCI DSS, ISO, and others, are being placed on businesses as they go through a digital transformation to protect systems from data breaches, irrespective of the sector or industry that the organization operates. Regulations and compliances require enterprises to implement efficient security solutions, which supports the expansion of the data security market.
- Implementing data security technologies like Data Auditing, Data Real-time Alerts, Data risk assessment, Data minimization, and Purging of stale data could help organizations prevent breaches, reduce risk, and sustain protective security measures to prevent data loss.
- Finding and analyzing sensitive data among the structured and unstructured data collected from various sources has become a significant concern, which is expected to hamper the market growth. Moreover, young start-ups' cybersecurity budgets must be increased to implement Next-Generation Firewalls (NGFWs) and Advanced Threat Protection (ATP) technologies. Small businesses in emerging economies need help adopting data security solutions due to significant concerns, including a shortage of capital and limited investment.
- Since many employees work from home and connect the company's data, which is more important, government, public, and private businesses have launched many initiatives to overcome phishing attempts during COVID-19. Additionally, the use of third-party applications has grown significantly during the pandemic. As a result of all these factors, IT infrastructure is now more susceptible to viruses and cyberattacks. Companies have been compelled to enhance security measures, which has benefited the global data security market. For instance, spear-phishing email attacks related to COVID-19 have increased by 67% since December last year.
Data Security Market Trends
Data Security Technologies As the Greatest Asset
- A robust data security strategy could help organizations stay compliant and reduce exposure to threats in various industries, including retail, finance, healthcare, and government. When used following the principles of confidentiality, integrity, and availability, data would be the most valuable resource that helps organizations improve decisions, carry out strategic initiatives, and build stronger bonds with clients and business partners.
- Data security technologies include firewalls, authentication and authorization, encryption, data masking, hardware-based security, data backup and resilience, and data erasure. It plays a vital role in business operations, development, and finances. By protecting data, companies can prevent data breaches and damage to reputation and better meet regulatory requirements. According to the ThoughtLab report, there was a rise of 15.1% in the number of data breaches in the previous year. Also, IDG reports that 68 percent of CIOs anticipate spending more on data security over the upcoming years.
- AI and multi-cloud services play a significant part in data security. Artificial intelligence (AI) assists security operations analysts in keeping ahead of threats and hazards to make crucial decisions and remediate problems as data phishing and cyberattacks increase in volume daily. As enterprises today are accumulating data from numerous sources, securing information is of utmost importance for companies. AI and ML in data security can assist security analysts in reducing the time taken by authorities to prevent data thefts. As AI and ML focus on securing information by working with algorithms provided to them, they can also learn about how specific threats are classified. With such techniques, these technologies can quickly scan through the abnormal behavior of the system and determine if abnormalities classify as potential threats.
- The majority of cutting-edge businesses rely on multi-cloud services. These take advantage of many cloud computing service providers to provide an organization with a comprehensive security solution from a wide range of possibilities. This service gives firms more flexibility, improved cost management, and increased resilience. The ability to monitor and manage workloads across different public clouds from a single interface using multi-cloud technologies and processes reduces data breaches and improves data security.
- Cloud data security software secures information stored using cloud services or cloud-based applications. These tools can facilitate data security by enforcing cloud access control and storage policies. Companies utilize the tools to implement security protocols, monitor access, and protect information stored within and transferred through cloud applications.
Asia-Pacific witnessed Market Expansion
- Data security solutions are anticipated to grow in demand during the forecast period due to the quick uptake of Internet technologies and the increased number of devices across various industries. An increase in attacks and data phishing on these connected devices was also projected by the National Institute of Information and Communication Technology. Such occurrences drive the market for data security by pushing companies to develop solutions that allow them to predict the possibility of such incidents.
- Investments by governments and corporate enterprises in security-related products, including VPN, endpoint protection, and security testing, have increased in the Asia Pacific region due to the availability of large businesses that serve domestic and international clients.
- A prominent trend in the Asian market is the growing use of IoT devices, such as BYOD, to access healthcare, banking, travel, hospitality services, etc. This ever-increasing trend indicates a significant opportunity for the data security industry. According to SPDI Rules, sensitive and personal data that includes passwords, financial information, medical records, etc., should be protected and cannot be misused for any individual needs unless involved in legitimate purposes. Hence effective data security techniques are to be implemented to avoid data loss.
- With an increase in cloud computing, mobile technology, and social media, reports on data security breaches have become prevalent in Asia Pacific countries. For instance, in July last year, the Five Eyes countries (the U.S., Canada, the U.K., Australia, and New Zealand), along with NATO, expressed concerns over a series of malicious cyberattacks, such as the Microsoft Exchange Hacks and cyberattacks that shook medical research institutes and universities.
Data Security Industry Overview
There are numerous prominent companies in the fiercely competitive data security Industry. Some of the most famous players now control the market regarding market share. However, as security services develop, new companies are becoming more prevalent on the market and extending their geographic reach for their businesses. Depending on the level of data security required, businesses are becoming more conscientious and aware of the data stored in various systems. As a result, small and medium enterprises are taking advantage of services from firms like IBM, McAfee, Intel, Cybereason, Verizon, AT&T, etc.
- In June 2022, Varonis Systems, Inc., a pioneer in data security and analytics, announced new features to improve safety and boost data visibility in Amazon Simple Storage Service (S3), which gives customers a single pane of glass to protect critical data across their IaaS and SaaS ecosystem.
- In March 2022, The Mobile Device Management (MDM) solution from Syxsense, a leader in IT and data security management solutions, includes all the tools required to apply effective management to mobile endpoints, including Device Enrolment, Inventory, and Configuration Management, Application Deployment and Rollback, Data Containerization, and Remote Device Lock/Reset/Wipe, allowing Technology expertise to wipe sensitive data from lost or stolen devices to provide data security.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Rise in Digitization Trends and Digital Data Production
- 4.2.2 Increase in Data Security Technologies
- 4.3 Market Restraints
- 4.3.1 Identifying and Analyzing Sensitive Information and Costly Installation
- 4.4 Industry Value Chain Analysis
- 4.5 Industry Attractiveness - Porter's Five Force Analysis
- 4.5.1 Bargaining Power of Suppliers
- 4.5.2 Bargaining Power of Consumers
- 4.5.3 Threat of New Entrants
- 4.5.4 Threat of Substitute Products
- 4.5.5 Intensity of Competitive Rivalry
- 4.6 Assesment of Impact of COVID-19 on the Market
5 MARKET SEGMENTATION
- 5.1 By Component
- 5.1.1 Solutions
- 5.1.2 Services
- 5.2 By Deployment
- 5.2.1 Cloud
- 5.2.2 On-premises
- 5.3 By Organization Size
- 5.3.1 Small and Medium Enterprises
- 5.3.2 Large Enterprises
- 5.4 By End-user Industry
- 5.4.1 Retail
- 5.4.2 Healthcare
- 5.4.3 Manufacturing
- 5.4.4 Banking, Financial Services and Insurance
- 5.4.5 Government
- 5.4.6 IT & Telecommunications
- 5.4.7 Other End-user Industries
- 5.5 Geography
- 5.5.1 North America
- 5.5.2 Europe
- 5.5.3 Asia-Pacific
- 5.5.4 Latin America
- 5.5.5 Middle East & Africa
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles
- 6.1.1 IBM Corporation
- 6.1.2 Cisco Systems Inc
- 6.1.3 101 Data Solutions
- 6.1.4 Microsoft Corporation
- 6.1.5 Zimcom Internet Solutions
- 6.1.6 Comforte AG
- 6.1.7 Thales
- 6.1.8 Lepide USA Inc
- 6.1.9 Varonis Systems Inc
- 6.1.10 Checkpoint Software Technologies Ltd
- 6.1.11 Oracle Corporation



















