
|
시장보고서
상품코드
1521761
보안 서비스 : 시장 점유율 분석, 산업 동향 및 통계, 성장 예측(2024-2029년)Security Services - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2024 - 2029) |
||||||
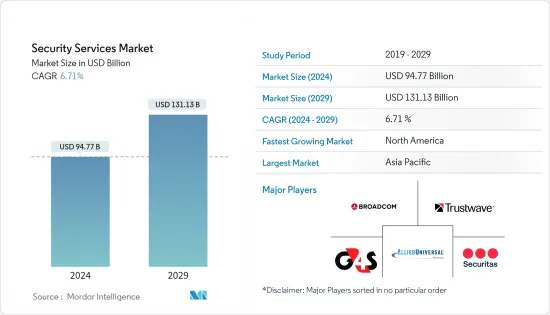
보안 서비스 시장 규모는 2024년 947억 7,000만 달러로 추정되며, 2029년에는 1,311억 3,000만 달러에 달할 것으로 예상되며, 예측 기간(2024-2029년) 동안 6.71%의 CAGR로 성장할 것으로 예상됩니다.
주요 하이라이트
- 물리적 영역과 디지털 영역의 관계는 점점 더 복잡해지고 있으며, 특히 신흥 경제국에서는 더욱 고도화된 보안 시스템 개발이 요구되고 있습니다. 이러한 시스템이 스마트 기기 및 IoT를 통해 빅데이터 및 인공지능(AI)과 같은 기술과 통합되면서 보안 서비스에 대한 요구가 빠르게 증가하고 있습니다. 가상 근무 환경의 출현과 시설 이용에 대한 요구사항의 발전은 새로운 보안 서비스 및 솔루션으로 이어지고 있습니다. 또한, E-Commerce의 성장으로 인해 물류센터 및 이와 유사한 구조물에서 기술 지원 보안 솔루션에 대한 수요가 더욱 증가하고 있습니다.
- 점점 더 많은 사람들이 도시로 이주하면서 도시화와 산업화 속도가 빨라지고 있습니다. 전 세계 도시 인구는 매주 평균 150만 명씩 증가하고 있으며, 이러한 높은 인구 밀도는 범죄 행위에 대한 우려를 증가시킬 수 있습니다. 보안 서비스 시장은 대부분의 신흥국에서 기술적 감시 장비의 사용이 증가함에 따라 급성장할 것으로 예상됩니다. 산업화의 진전과 세계 산업 생산의 성장으로 인해 생산 시설, 사무실 및 기타 작업 환경에 대한 투자가 필요하며, 이에 따른 보안 요구사항이 요구되고 있습니다.
- 세계 인구의 가처분 소득이 증가함에 따라 보안 서비스에 대한 요구도 증가할 것으로 보입니다. 예를 들어, 대중 교통 및 공공 물류 시설과 같은 인프라 투자는 이러한 재산을 보호해야 하기 때문에 보안 수요가 증가할 것입니다. 경제 성장과 세계 신축 투자의 지속은 모두 보안 서비스 시장 개척에 기여하고 있습니다. 예를 들어, 2023년 7월에는 전국 100개 도시에 수십억 달러를 투자하여 빠르게 증가하는 인도 도시 인구에 대응하기 위한 '스마트 시티 미션'이 예정되어 있습니다.
- 사이버 위협의 성격은 끊임없이 변화하고 있기 때문에 보안 서비스도 끊임없이 적응해야 합니다. 새로운 공격 벡터가 등장하고 있는 상황에서 보안 서비스가 미흡할 경우, 조직은 위험에 노출되어 시장 개척에 어려움을 겪을 수 있습니다. 예를 들어, 2023년 데이터 유출 건수가 가장 많았던 산업은 헬스케어, 금융 서비스, 제조업의 세 가지였습니다.
- COVID-19 팬데믹은 세계 보안 서비스 시장에 부정적인 영향을 미쳤습니다. 예를 들어, 콘서트장, 컨퍼런스, 스포츠 대회 등 중요한 공공 행사가 폐쇄되면서 보안 서비스의 필요성이 감소했습니다. 그러나 COVID-19 이후, 사회가 일상으로 돌아가는 것을 촉진하기 위해 봉쇄 기간 동안 소매업, 의료 등 필수 기능에 대한 보안 서비스, 접촉자 추적 및 군중 모니터링과 같은 보안 및 기술 기반 보안 서비스에 대한 수요가 증가하고 있습니다.
보안 서비스 시장 동향
클라우드 구축이 큰 시장 점유율을 차지
- 클라우드에 구축된 관리형 보안 서비스는 적응력과 확장성이 뛰어납니다. 또한, 서비스 제공업체는 클라우드의 모든 문제에 접근, 추적 및 원격으로 문제를 해결할 수 있습니다. 지속적인 모니터링을 통해 모든 문제를 신속하고 효과적으로 해결할 수 있습니다. 머신러닝(ML), 인공지능(AI), 빅데이터 분석, 위협 인텔리전스, 고도의 자동화 플랫폼의 도입도 클라우드 관리형 보안 서비스로의 전환을 촉진하고 있습니다. 일부 시장 진입 기업들은 변화하는 업계의 요구에 대응하기 위해 혁신적이고 협력적인 노력을 통해 종합적인 서비스를 도입하고 있습니다.
- 팬데믹으로 인해 원격 근무가 급속히 확대되면서 클라우드 기반 협업 도구와 액세스 솔루션에 대한 의존도가 높아지고 있습니다. 이러한 환경의 안전을 보장하기 위해서는 안전한 액세스 및 종합적인 보호와 같은 전문적인 보안 서비스가 필요합니다. 이에 따라 기업들은 클라우드 보안과 관련된 비용과 복잡성을 줄이기 위해 자동화된 보안 조치와 수동 프로세스를 결합한 하이브리드 아키텍처를 선택하는 경우가 늘고 있습니다.
- 디지털 전환을 추진하는 기업이 온프레미스 IT 인프라를 현대화하고 업무의 일부를 클라우드로 이전하는 어렵지만 필수적인 과정을 시작할 때, IT 의사결정권자들은 일반적으로 규제 준수, 보안, 리스크 감소라는 과제에 직면하게 됩니다. 유능한 IT 인력의 부족과 최신 도구, 기술 및 관행에 대한 대응 능력 부족은 이러한 기업의 고민을 더욱 가중시키고 있습니다. 네트워크 및 데이터 보안 리스크가 증가하고 있는 지금, MSSP는 클라우드 구성을 관리하고, 리스크를 줄이고, 규제 준수를 보장하는 데 어려움을 겪고 있는 기업을 지원할 수 있습니다.
- 복잡하고 대규모 아키텍처로 인해 맞춤형 보안 클라우드를 구축해야 하는 조직이나 이기종 시스템에 대한 특정 구현 요구사항이 있는 조직은 이러한 서비스를 통해 큰 이점을 얻을 수 있습니다. 동적 리소스 할당에 의존하는 조직은 일반적으로 동적 환경을 효율적으로 모니터링하기 위해 자동화 개선이 필요합니다. 이러한 복잡한 자동화 요구사항은 AT&T, Verizon, IBM, SecureWorks와 같은 공급자가 제공하는 서비스를 통해 충족할 수 있습니다.
- 2023년 10월, CyberArk는 자사의 위험 기반 지능형 권한 제어를 기반으로 모든 사용자의 클라우드 서비스 및 최신 인프라에 대한 액세스를 보호하기 위한 새로운 기능을 발표했습니다. 이 새로운 보안 제어는 클라우드 환경의 모든 계층에 대한 안전한 액세스를 제공하는 동시에 개발자 및 기타 사용자가 클라우드 서비스에 액세스하는 방식에 혼란이나 변경을 일으키지 않습니다.
아시아태평양이 괄목할만한 성장세를 기록
- 아시아태평양에서는 최근 몇 년 동안 사이버 위협과 공격이 증가하고 있습니다. 사람들의 인터넷 사용 증가, 비즈니스의 디지털화, 지정학적 긴장이 존재하기 때문입니다. 이러한 요인들로 인해 사이버 공격과 침해로부터 자신을 보호하기 위해 신뢰할 수 있는 사이버 보안 서비스의 필요성이 증가하고 있습니다.
- MeitY가 제공한 데이터에 따르면, 2023년 인도에서 150만 건 이상의 사이버 공격이 보고되었으며, 이는 이전보다 상당히 증가한 수치입니다. 인도는 올해 사이버 보안 사고가 가장 많이 발생한 5개국 중 하나였습니다. 또한 인도는 현재 인터넷 사용자 수에서 세계 3위를 차지하고 있습니다.
- IT 랜섬웨어 공격, 분산서비스거부(DDoS) 공격, 데이터 탈취, 미디어를 통한 대규모 사이버 공격에 대한 인지도가 높아지는 등 사이버 보안에 대한 위협이 증가함에 따라, 이 지역의 조직들은 점점 더 많은 관리형 보안 서비스를 이용하고 있습니다. 전통적인 산업에서 디지털 전환의 도입과 IT 기술 향상으로 인터넷 센터 서비스에 대한 수요가 증가하면서 시장 성장에 더욱 기여하고 있습니다.
- 인공지능, 5G, 사물인터넷, 가상현실 기술의 급속한 발전과 상용화로 인해 데이터 처리 및 정보 교환의 필요성이 증가하고 있습니다. 이러한 요인으로 인해 이 지역에서는 데이터센터 건설이 가속화되어 산업이 급성장할 가능성이 있습니다. 인도에서는 조직 정보의 보안, 기밀성 및 가용성에 대한 위협이 증가함에 따라 고객의 전반적인 보안을 위해 비즈니스 위험 접근 방식에 기반한 정보 보안 표준 모델을 도입, 구현, 운영, 모니터링, 검토, 유지보수 및 개선할 필요성이 강조되고 있습니다.
- 아시아태평양에서 디지털 전환을 최우선 과제로 채택하는 기업이 증가하고 있습니다. 더 많은 기업들이 디지털 전환을 추진하기 위해 공식적인 전략을 채택함에 따라 디지털 전환에 대한 시장 수요가 크게 증가하고 있습니다. 중국, 인도, 일본, 한국 등 일부 국가에서는 의료, 금융 서비스, 행정, 제조 등 다양한 분야에서 디지털 전환이 빠르게 진행되고 있습니다. 이러한 변화에는 클라우드 컴퓨팅, 사물인터넷(IoT), 디지털 플랫폼의 활용이 필요하며, 디지털 자산을 보호하기 위한 고도의 보안 서비스 제공이 요구되고 있습니다.
보안 서비스 산업 개요
보안 서비스 시장은 경쟁이 치열합니다. 크고 작은 플레이어가 존재하기 때문에 시장은 세분화되어 있습니다. 대형 업체들은 모두 시장 점유율이 높으며, 소비자 기반을 확대하는 데 주력하고 있습니다. 이 시장의 주요 기업으로는 Broadcom, Trustwave Holdings Inc, G4S Limited, Securitas Inc, Allied Universal, Unity Resource Group, Constellis, DSS Securitech Pvt. Ltd., Fortra LLC 등이 있습니다. 이들 업체들은 예측 기간 동안 경쟁력을 확보하기 위해 여러 파트너십, 제휴, 인수를 체결하고 신제품 도입에 투자하여 시장 점유율을 확대하고 있습니다.
2023년 4월 보안 및 시설 서비스 제공업체인 Allied Universal은 Allied Universal의 자회사인 MSA Security와 제휴하여 Elite Tactical Security Solutions를 인수했습니다. 엘리트 택티컬 인수를 통해 얼라이드 유니버설은 보안 및 임원 보호 서비스, 폭발물 및 총기 탐지견 팀을 제공할 수 있게 됐습니다. 이번 인수로 Allied Universal의 솔루션 포트폴리오는 라스베가스에서 경비원 및 임원 보호 서비스 관리를 담당하게 되며, Elite Tactical의 탐지견 서비스는 MSA Security의 프로그램에 통합될 예정입니다.
2023년 3월 - Fortra의 Terranova Security가 Elevate Security와 파트너십을 맺고 시장에 최고의 보안 인식과 위협 모니터링을 제공합니다. 이 요소는 기밀 정보를 보호하고, 정보 보안을 강화하며, 사이버 공격 및 데이터 유출의 인적 위험을 줄이려는 조직에 필수적입니다. 피싱 사고의 80%는 4%의 사용자에 의해 발생하며, 악성코드 사고의 92%는 3%의 사용자에 의해 발생하는데, Elevate Security는 조직의 가장 취약한 사용자를 선제적으로 식별하고 대응하여 보안 사고가 발생하기 전에 사용자 및 보안 위험을 줄일 수 있는 가시성과 분석 기능을 제공합니다.
기타 혜택:
- 엑셀 형식의 시장 예측(ME) 시트
- 3개월간의 애널리스트 지원
목차
제1장 소개
- 조사 가정과 시장 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 인사이트
- 시장 개요
- 업계의 매력 - Porter's Five Forces 분석
- 공급 기업의 교섭력
- 소비자의 협상력
- 신규 참여업체의 위협
- 대체품의 위협
- 경쟁 기업 간의 경쟁 관계
- COVID-19의 영향과 기타 거시경제 요인이 시장에 미치는 영향
제5장 시장 역학
- 시장 성장 촉진요인
- 디지털 파괴와 컴플라이언스 요구 상승
- 멀티 클라우드 또는 하이브리드 클라우드 전략 채용 증가
- 각국 정부의 사이버 보안에 대한 주력
- 시장 과제
- 보안 서비스에 대한 인식 부족
- 보안 서비스에 대한 조직 한정된 예산 제약
- 복잡성과 통합 과제
제6장 시장 세분화
- 서비스 유형별
- 매니지드 보안 서비스
- 프로페셔널 보안 서비스
- 컨설팅 서비스
- 위협 인텔리전스 보안 서비스
- 도입 형태별
- 온프레미스
- 클라우드
- 최종 이용 업계별
- IT 및 인프라
- 정부기관
- 산업
- 헬스케어
- 운송·물류
- 은행
- 기타 최종 이용 산업
- 지역별*
- 북미
- 미국
- 캐나다
- 유럽
- 독일
- 영국
- 프랑스
- 아시아
- 인도
- 중국
- 일본
- 호주·뉴질랜드
- 라틴아메리카
- 중동 및 아프리카
- 북미
제7장 경쟁 상황
- 기업 개요
- Broadcom
- Trustwave Holdings Inc
- G4S Limited
- Allied Universal
- Securitas Inc
- Unity Resource Group
- Constellis
- DSS Securitech Pvt. Ltd
- Fortra LLC
- IBM Corporation
- VS4 Security Services
- Fujitsu
- Verizon
- Wipro
제8장 투자 분석
제9장 시장 전망
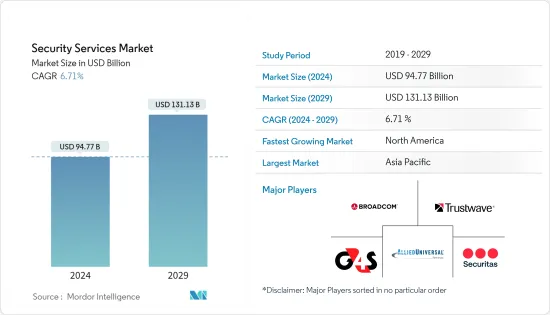
ksm 24.08.01The Security Services Market size is estimated at USD 94.77 billion in 2024, and is expected to reach USD 131.13 billion by 2029, growing at a CAGR of 6.71% during the forecast period (2024-2029).
Key Highlights
- The relationship between the physical and digital realms is becoming increasingly complex, necessitating the development of more sophisticated security systems, particularly in more developed economies. The need for security services is rapidly growing as these systems integrate with technologies such as big data and artificial intelligence (AI) through smart devices and the IoT. The emergence of virtual working environments and the ever-evolving demands for facility utilization are leading to new security services and solutions. Additionally, the growth of e-commerce has further increased the demand for technology-enabled security solutions in distribution centers and similar structures.
- The rate of urbanization and industrialization is accelerating as more and more people relocate to cities. The world's urban population is increasing by an average of 1.5 million individuals each week, and this high population density could raise concerns about criminal activity. It is anticipated that the security services market will experience a rapid expansion in the majority of developed countries as the utilization of technological monitoring equipment increases. The ongoing industrialization and growth of global industrial production necessitates the investment of production facilities, offices, and other work environments, each with its security requirements.
- As the global population increases its disposable income, the requirement for security services is likely to grow. For instance, infrastructure investments in public transport and public logistics facilities require the protection of these properties, thus necessitating an increase in the demand for security. Economic growth and ongoing global investment in new construction are both contributing to the development of the security services market. For instance, in July 2023, the Smart Cities Mission seeks to address India's rapidly expanding urban population by investing billions in 100 cities nationwide.
- The ever-changing nature of cyber threats necessitates that security services must be constantly adapted. As new attack vectors emerge, organizations can be put at risk if security services are inadequate, thus impeding market development. For instance, in 2023, the three industries that experienced the highest number of data breaches were the healthcare, financial services, and manufacturing sectors.
- The COVID-19 pandemic had a detrimental effect on the global security services market. For instance, the closure of significant public events, such as concert venues, conferences, and sports competitions, reduced the need for security services. However, post-COVID-19, there is an increase in the demand for security services for essential functions, such as retail and healthcare during lockdown, as well as for security and technology-enabled security services, such as contact tracing and crowd surveillance, to facilitate the return of societies to normalcy.
Security Services Market Trends
Cloud Deployment to Hold Significant Market Share
- Managed security services deployed in the cloud are highly adaptable and scalable. Additionally, the service provider can access, track, and even remotely resolve any problems within the cloud. Continuous monitoring ensures the prompt and effective resolution of any issues. The rising adoption of machine learning (ML), artificial intelligence (AI), big data analytics, threat intelligence, and advanced automation platforms further supports the transition to cloud-managed security services. Several market participants are introducing comprehensive services through innovative and collaborative initiatives to meet the changing needs of the industry.
- The rapid expansion of remote work due to the pandemic has necessitated a greater reliance on cloud-based collaborative tools and access solutions. Specialized security services are necessary to guarantee the safety of these environments, including secure access and comprehensive protection. As a result, enterprises will increasingly opt for hybrid architectures that combine automated security measures with manual processes to reduce the costs and intricacies associated with cloud security.
- IT decision-makers typically face regulatory compliance, security, and risk reduction challenges as companies amid digital transformation embark on the difficult yet necessary process of modernizing their on-premise IT infrastructure and transitioning some of their operations into the cloud. The lack of qualified IT personnel and the inability to remain up-to-date with the latest tools, technologies, and practices exacerbate these corporate worries. At a time when network and data security risks are on the rise, MSSPs can assist overwhelmed enterprises in managing cloud configuration, reducing risk, and ensuring regulatory compliance.
- Organizations that require a custom security cloud deployment due to a complex or expansive architecture or have specific implementation requirements with disparate systems can benefit significantly from such services. Organizations that rely on dynamic resource allocation typically require improved automation to monitor their dynamic environments efficiently. These complex automation requirements can be met through the services provided by providers such as AT&T, Verizon, IBM, and SecureWorks.
- In October 2023, CyberArk announced new capabilities for securing access to cloud services and modern infrastructure for all users based on the company's risk-based intelligent privilege controls. The new security controls enable secure access to every layer of cloud environments while causing no disruption or change to how developers and other users access cloud services.
Asia-Pacific to Witness Significant Growth
- Cyber threats and attacks have increased in Asia-Pacific over the last few years. People increasingly use the internet, businesses are digitalizing, and geopolitical tension exists. These factors have heightened the need for reliable cybersecurity services to safeguard against cyberattacks and breaches.
- In India, according to data provided by MeitY, more than 1.5 million cyberattacks were reported in 2023, which was a considerable rise from previous years. India was one of the five countries with the highest number of cybersecurity incidents in the year. Additionally, India is currently ranked third worldwide in terms of internet user numbers.
- Organizations in the region are increasingly turning to managed security services due to the growing threats to cybersecurity, such as IT ransomware attacks, distributed denial-of-service (DDoS) attacks, data extraction, and the increased visibility of major cyberattacks in the media. Traditional industries are increasingly embracing digital transformation and improving their IT technologies, increasing the demand for Internet center services, further contributing to the market's growth.
- The rapid emergence of artificial intelligence, 5G, the Internet of Things, and virtual reality technologies, as well as the commercialization of these technologies, has increased the need for data processing and the exchange of information. These factors may lead to accelerating data center construction in the region, potentially resulting in a rapid expansion of the industry. The threats to the security, confidentiality, and availability of organization information are on the rise in India, thus emphasizing the need for a standardized model of information security based on the business risk approach to be implemented, implemented, operated, monitored, reviewed, maintained, and improved for the overall security of customers.
- Asia-Pacific has seen an increase in the adoption of digital transformation as a top priority. As more businesses adopt formal strategies to facilitate their efforts, the market demand for digital transformation has increased significantly. Several countries, such as China, India, Japan, and South Korea, are experiencing rapid digital transformation in various sectors, including healthcare, financial services, administration, and manufacturing. This transformation necessitates the utilization of cloud computing and the Internet of Things (IoT), as well as digital platforms, which requires the provision of sophisticated security services to protect digital assets.
Security Services Industry Overview
The security services market is very competitive. The market is fragmented due to the presence of various small and large players. All the major players account for a significant market share and focus on expanding the consumer base. Some of the significant players in the market are Broadcom, Trustwave Holdings Inc., G4S Limited, Securitas Inc., Allied Universal, Unity Resource Group, Constellis, DSS Securitech Pvt. Ltd, and Fortra LLC. Companies are increasing their market share by forming multiple partnerships, collaborations, and acquisitions and investing in introducing new products to earn a competitive edge during the forecast period.
April 2023: Allied Universal, a security and facility services provider, partnered with MSA Security, a subsidiary of Allied Universal, to acquire Elite Tactical Security Solutions, a strategic extension of their services to the Las Vegas area. The acquisition of Elite Tactical will enable Allied Universal to provide security and executive protection services and explosives and firearms detection canine teams. As a result of this acquisition, Allied Universal's portfolio of solutions will be responsible for managing security guard and executive protection services in Las Vegas. Elite Tactical's canine services will be integrated into MSA Security's program.
March 2023 - Fortra's Terranova Security partnered with Elevate Security to bring the best security awareness and threat monitoring to the marketplace. This factor is essential for organizations looking to protect sensitive information, enhance information security, and mitigate the human risk of cyber-attacks and data breaches. 4% of users account for 80% of all phishing incidents and 3% for 92% of all malware incidents. Elevate security proactively identifies and responds to an organization's most vulnerable users and provides security teams with visibility and analytics to mitigate user risk before enabling a security incident.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Attractiveness - Porter's Five Forces Analysis
- 4.2.1 Bargaining Power of Suppliers
- 4.2.2 Bargaining Power of Consumers
- 4.2.3 Threat of New Entrants
- 4.2.4 Threat of Substitutes
- 4.2.5 Intensity of Competitive Rivalry
- 4.3 Impact of COVID-19 Aftereffects and Other Macroeconomic Factors on the Market
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Rising Digital Disruption and Increased Compliance Demands
- 5.1.2 Increasing Adoption of Multi-Cloud or Hybrid Cloud Strategies
- 5.1.3 Governments Focus on CyberSecurity
- 5.2 Market Challenges
- 5.2.1 Lack of Awareness of Security Services
- 5.2.2 Limited Budget Constraints by Organizations for Security Services
- 5.2.3 Complexity and Integration Challenges
6 MARKET SEGMENTATION
- 6.1 By Service Type
- 6.1.1 Managed Security Services
- 6.1.2 Professional Security Services
- 6.1.3 Consulting Services
- 6.1.4 Threat Intelligence Security Services
- 6.2 By Mode of Deployment
- 6.2.1 On-Premise
- 6.2.2 Cloud
- 6.3 By End-user Industry
- 6.3.1 IT and Infrastructure
- 6.3.2 Government
- 6.3.3 Industrial
- 6.3.4 Healthcare
- 6.3.5 Transportation and Logistics
- 6.3.6 Banking
- 6.3.7 Other End-user Industries
- 6.4 By Geography***
- 6.4.1 North America
- 6.4.1.1 United States
- 6.4.1.2 Canada
- 6.4.2 Europe
- 6.4.2.1 Germany
- 6.4.2.2 United Kingdom
- 6.4.2.3 France
- 6.4.3 Asia
- 6.4.3.1 India
- 6.4.3.2 China
- 6.4.3.3 Japan
- 6.4.3.4 Australia and New Zealand
- 6.4.4 Latin America
- 6.4.5 Middle East and Africa
- 6.4.1 North America
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles*
- 7.1.1 Broadcom
- 7.1.2 Trustwave Holdings Inc
- 7.1.3 G4S Limited
- 7.1.4 Allied Universal
- 7.1.5 Securitas Inc
- 7.1.6 Unity Resource Group
- 7.1.7 Constellis
- 7.1.8 DSS Securitech Pvt. Ltd
- 7.1.9 Fortra LLC
- 7.1.10 IBM Corporation
- 7.1.11 VS4 Security Services
- 7.1.12 Fujitsu
- 7.1.13 Verizon
- 7.1.14 Wipro



















