
|
시장보고서
상품코드
1850085
석유 및 가스 보안 시장 : 시장 점유율 분석, 산업 동향, 통계, 성장 예측(2025-2030년)Oil And Gas Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
석유 및 가스 보안 시장 규모는 2025년 303억 8,000만 달러로 추정되고, 예측 기간(2025-2030년) CAGR 5.20%로 성장할 전망이며, 2030년에는 391억 4,000만 달러에 달할 것으로 예측됩니다.

이 성장 궤도는 상품 가격이 변동하는 가운데 에너지 기업이 보안 프로그램에 지속적으로 자본을 투입하고 있음을 보여줍니다. 사이버 인시던트가 정보 기술(IT) 자산뿐만 아니라 운영 기술(OT) 자산에도 영향을 미치게 되었기 때문에 예방적 안전 대책에서 예방적인 인텔리전스 주도 모델로의 전환이 가속화되고 있습니다. 지정학적 긴장 증가, 파이프라인 규제의 엄격화, 보험 요건 증가로 사이버와 물리적 관리 모두에 예산이 고정되어 있습니다. 하드웨어, 소프트웨어 및 관리형 서비스를 통합한 OT-IT 스택을 제공할 수 있는 공급업체는 향후 5년 동안 큰 가치를 얻을 수 있을 것으로 보입니다.
세계의 석유 및 가스 보안 시장 동향 및 인사이트
확대되는 OT-IT 융합이 사이버 리스크 상승 초래
한때 기업 네트워크에서 분리되었던 운영 자산은 현재 클라우드와 기업 시스템에 연결되어 공격 대상이 확대되고 있습니다. 이 협력으로 인한 사고로 인해 적은 IT에서 안전하고 중요한 OT로 축발을 옮겨 물리적 혼란을 일으킬 가능성이 높아집니다. 미국 기관의 보고에 따르면 기술이 낮은 그룹에서도 산업용 제어 시스템을 목표로 삼는 데 성공했으며 취약한 세그먼테이션과 최소한의 다중 요소 인증을 드러낸다고 합니다. 따라서 네트워크 구역화, 제로 트러스트 정책 및 실시간 비정상 감지는 모범 사례에서 기본 기대치로 전환하고 있습니다. 기업이 생산을 멈추지 않고 현대화를 진행함에 따라 복잡성이 커지고 점진적인 롤아웃과 병렬 아키텍처가 필요합니다. IT 보안, 엔지니어링 및 제조 팀을 협업하는 거버넌스의 향상은 예상되는 미래에 지출하는 중요한 요소입니다.
파이프라인에 대한 TSA와 IEC 사이버 규제의 의무화
운수 보안국(TSA)의 개정 지령은 파이프라인 사업자에게 관리책의 검증, 갭의 해소, 정해진 기한 내에서의 위반 보고 등을 의무화하고 있습니다. IEC 62443은 일본의 CERT와 같은 지역 그룹이 실시 지침을 제공함으로써 동시에 세계적인 제어 시스템의 벤치마크로 부상하고 있습니다. 유럽의 NIS2 지침은 24시간 이내에 인시던트 공개를 의무화함으로써 추가 의무를 거듭하고 있습니다. 컴플라이언스 위반에 대한 금전적 처벌과 잠재적인 업무 정지 명령으로 보안은 재량 지출에서 운영 필요성까지 높아지고 있습니다. 거버넌스와 기술적 배포 모두에 익숙한 공급업체는 사업자가 턴키 컴플라이언스 프로그램을 요구하고 있기 때문에 수요가 증가하고 있습니다.
레거시 SCADA 업그레이드 비용 초과
많은 플랫폼은 네트워크에 대한 노출을 가정하여 설계되지 않은 20년 전의 모니터링 제어 시스템에 의존합니다. 기업은 세분화, 다중 요소 인증 및 암호화된 원격 측정에 필요한 엔지니어링 및 다운타임 비용을 일상적으로 과소평가했습니다. 도입 도중에 호환성 문제가 표면화된 경우, 업그레이드에는 당초 예산에서 2-3배의 비용이 드는 경우가 많습니다. 자산의 수명주기가 길어지면 자본 배분이 어려워지고 운영자는 단기적인 생산성 저하 및 장기적인 탄력성을 저울질해야 합니다. 아카데믹 스터디에 따르면, 부서를 넘어서는 비효율적인 커뮤니케이션은 실행을 더욱 늦추고 비용을 팽창시킵니다.
부문 분석
2024년 매출 점유율은 감시 플랫폼이 30.4%를 차지했으며, 이 시장이 오랜 세월에 걸쳐 주변 감시와 상황 인식에 중점을 두고 있음을 뒷받침하고 있습니다. 비디오 분석, 무인 항공기, 입퇴실 관리와 관련된 석유 및 가스 보안 시장 규모는 여전히 크지만, 예산이 디지털 방어에 착수함에 따라 연간 성장률은 완만해집니다. CAGR 8.1%로 성장하는 네트워크 및 사이버 보안 솔루션은 의무화된 파이프라인 규칙과 현장 자산을 목표로 하는 랜섬웨어 증가를 반영합니다. 콜로니얼 파이프라인 공격과 같은 사건은 울타리 침입이 아닌 노트북으로 인해 운영이 중단될 수 있음을 강조하고 침입 감지 및 안전한 원격 액세스 게이트웨이로 자본을 유도했습니다.
향후 예측에서는 카메라 피드와 사이버 텔레메트리를 융합시킨 통합 커맨드 센터가 단일 목적의 배치를 능가할 것으로 예측됩니다. 이 통합을 통해 물리적 배지와 네트워크 로그인을 연관시켜 잘못된 감지를 줄일 수 있습니다. 카메라, 방화벽, 컨트롤러의 이벤트를 통합 스크린에 크로스태그할 수 있는 벤더는 석유 및 가스 보안 시장에서 확대하는 슬라이스를 획득할 가능성이 높습니다. 결과적으로, 모니터링 시스템은 여전히 중요하지만, 보다 광범위한 사이버 물리적 플랫폼에 통합되는 경향이 강해지고 있으며, 단독으로 판매량이 감소하는 반면 소프트웨어 분석의 매출은 증가하고 있습니다.
하드웨어는 2024년 석유 및 가스 보안 시장 점유율의 52.6%를 여전히 차지했으며, 위험 구역용으로 견고한 방화벽, 본질 안전 방폭 카메라, 내진동 서버 등에 이르고 있습니다. 그러나 매니지드 서비스 분야는 운영자가 스킬 부족을 보완하기 위해 24시간 365일 감시와 사고 대응을 계약하기 위해 CAGR 9.3%로 성장할 전망입니다. 새로운 사이트는 고급 분석, 위협 인텔리전스 피드, 정기적인 레드 팀 평가 등을 요구하므로 서비스 리테이너와 관련된 석유 및 가스 보안 시장 규모가 증가하고 있습니다.
서비스 성장은 독립적인 검증 및 문서화를 필요로 하는 규제 감사에도 연결되어 있습니다. 사내 능력이 부족한 기업은 OT 자산에 특화된 MSSP에 의존하고 있습니다. 이러한 공급자는 자산 발견, 취약성 관리 및 컴플라이언스 보고서를 다년간 계약에 번들로 제공합니다. 하드웨어 벤더는 장비와 서비스를 패키징한 성과 기반 모델을 통해 대응하여 수익을 평준화하고 고객의 포위를 깊게 하고 있습니다.
석유 및 가스 보안 시장은 보안 제품 유형별(네트워크 및 사이버 보안, 모니터링, 스크리닝 및 감지 등), 컴포넌트별(하드웨어, 소프트웨어 플랫폼, 서비스), 운영 단계별(업스트림, 미드스트림, 다운스트림), 도입 형태별(온프레미스, 클라우드, 하이브리드 및 에지 클라우드), 용도별(탐사 및 생산 기지, 해양 플랫폼 및 FPSO 등), 지역별로 구분됩니다.
지역 분석
북미는 2024년 석유 및 가스 보안 시장의 36.22%를 차지했으며, TSA 지령의 의무화와 Colonial Pipeline 랜섬웨어 사건의 여운에 지지를 받고 있습니다. 캐나다의 위협 평가에서는 생산 거점과 중류 허브를 표적으로 하는 국영기업의 관여가 지적되고 있어 관민 일체가 된 훈련이나 OT 세분화을 위한 보조금이 촉구되고 있습니다. 멕시코 만과 노스 슬로프의 해외 자산은 시대 지연 방화벽과 패치 미적용 HMI를 지적한 연방 정부의 감사를 받아 긴급 사이버 업그레이드를 요구하고 있습니다.
아시아태평양은 2030년까지 연평균 복합 성장률(CAGR)이 9.1%로 가장 빠르고 중국이 국경지대에 간선 파이프라인과 저장 능력을 확장하여 OT 보안과 베이징의 주권 클라우드 지령을 융합시키고 있습니다. 일본에서는 석유 및 가스를 중요한 사회 인프라로 분류하는 경제 보안 규칙이 제정되고, 사업자는 규제 당국에 보안 계획을 제출할 의무가 있습니다. 인도는 정유소와 LNG 터미널을 확장하고 벵갈루루와 하이데라바드에 위치한 현지 보안 운영 센터에서 관리 서비스를 조달합니다. 호주와 한국은 남중국해에서 지역적 긴장이 증가함에 따라 새로운 LNG 수출 프로젝트에 OT 안보 조항을 포함합니다.
유럽에서는 24시간 체제의 인시던트 보고와 기간 에너지 사업체에 대한 연차 감사를 의무화하는 NIS2의 틀을 중심으로 근대화가 진행되고 있습니다. 독일, 프랑스, 네덜란드에 걸친 LNG 수입의 증강은 규모와 복잡성을 늘리고 암호화된 해상-터미널 간의 링크가 필요합니다. 중동 및 아프리카에서는 문서화된 공격 건수가 206% 증가하여 자금 조달이 강화되어 지역 사이버 포럼에서 소개되었습니다. 라틴아메리카는 이제 막 시작되었지만 브라질, 아르헨티나, 가이아나가 생산량을 늘리고 IEC 62443과의 무결성을 모색하고 있기 때문에 투자가 증가하고 있습니다.
기타 혜택 :
- 엑셀 형식 시장 예측(ME) 시트
- 3개월간의 애널리스트 서포트
목차
제1장 서론
- 조사의 전제조건 및 시장 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 상황
- 시장 개요
- 시장 성장 촉진요인
- OT와 IT의 융합이 진행됨으로써 사이버 리스크 상승 초래
- 파이프라인에 대한 TSA와 IEC 사이버 룰의 의무화
- AI를 활용한 예측 보안 분석 도입
- 에너지 가격의 변동이 보험 요건 뒷받침
- 엣지 투 코어의 보안을 필요로 하는 해외 자율 자산
- 시장 성장 억제요인
- 기존 SCADA 업그레이드 비용 초과
- 원격지의 유역에 있어서 OT 보안 인재 부족
- 클라우드 기반 데이터 주권 분쟁
- ESG 관련 투자 철수가 장기적인 설비 투자 억제
- 업계 밸류체인 분석
- 규제 상황
- 기술의 전망
- 업계의 매력-Porter's Five Forces 분석
- 신규 참가업체의 위협
- 구매자의 협상력
- 공급기업의 협상력
- 대체품의 위협
- 경쟁 기업 간 경쟁 관계
- 거시 경제 요인이 시장에 미치는 영향
제5장 시장 규모 및 성장 예측(가치)
- 보안 유형별
- 네트워크 및 사이버 보안
- 감시
- 스크리닝 및 검출
- 커맨드 및 컨트롤
- 물리적 액세스 제어
- 기타 유형
- 컴포넌트별
- 하드웨어
- 소프트웨어 플랫폼
- 서비스(매니지드 및 프로페셔널)
- 작전 단계별
- 업스트림(탐사 및 생산)
- 미드스트림(파이프라인 및 저장)
- 다운스트림(정제 및 유통)
- 전개 모드별
- 온프레미스
- 클라우드
- 하이브리드 및 엣지 클라우드
- 용도별
- 탐사 및 생산 현장
- 해외 플랫폼 및 FPSO
- 파이프라인 모니터링
- 정유소 및 석유화학공장
- LNG 및 가스 처리
- 소매 및 유통 터미널
- 지역별
- 북미
- 미국
- 캐나다
- 멕시코
- 남미
- 브라질
- 아르헨티나
- 칠레
- 기타 남미
- 유럽
- 독일
- 영국
- 프랑스
- 이탈리아
- 스페인
- 러시아
- 기타 유럽
- 아시아태평양
- 중국
- 인도
- 일본
- 한국
- 말레이시아
- 싱가포르
- 호주
- 기타 아시아태평양
- 중동 및 아프리카
- 중동
- 아랍에미리트(UAE)
- 사우디아라비아
- 튀르키예
- 기타 중동
- 아프리카
- 남아프리카
- 나이지리아
- 이집트
- 기타 아프리카
- 북미
제6장 경쟁 구도
- 시장 집중도
- 전략적 동향
- 시장 점유율 분석
- 기업 프로파일
- ABB Ltd.
- Airbus Defence and Space
- BAE Systems plc
- Baker Hughes Cyber-Security Services
- Belden Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems Inc.
- Claroty Ltd.
- Dragos Inc.
- Fortinet Inc.
- Honeywell International Inc.
- Huawei Technologies Co. Ltd.
- Johnson Controls International plc
- Kaspersky Lab JSC
- Microsoft Corp.
- Nozomi Networks Inc.
- Palo Alto Networks Inc.
- Parsons Corp.
- Rockwell Automation Inc.
- Schneider Electric SE
- Siemens AG
- Tenable OT Security
- Thales Group
- Trend Micro Inc.
- Waterfall Security Solutions Ltd.
제7장 시장 기회 및 향후 동향
- 화이트 스페이스 및 미충족 요구의 평가
The Oil And Gas Security Market size is estimated at USD 30.38 billion in 2025, and is expected to reach USD 39.14 billion by 2030, at a CAGR of 5.20% during the forecast period (2025-2030).
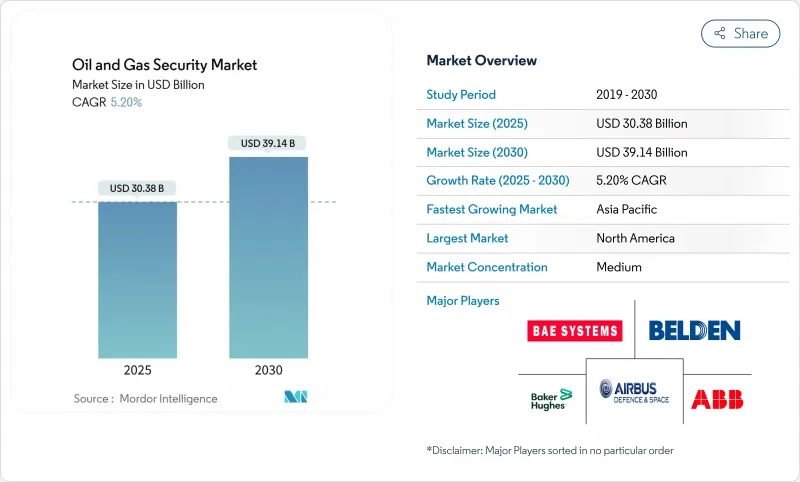
This growth trajectory shows that energy companies are putting sustained capital into security programs even as commodity prices swing. The shift from reactive safeguards to proactive, intelligence-driven models is accelerating because cyber incidents now expose operational technology (OT) as well as information technology (IT) assets. Heightened geopolitical tension, stricter pipeline rules, and rising insurance prerequisites keep budgets anchored on both cyber and physical controls. Vendors that can blend hardware, software, and managed services into a unified OT-IT stack are positioned to capture disproportionate value in the next five years.
Global Oil And Gas Security Market Trends and Insights
Growing OT-IT Convergence Elevating Cyber-Risk
Operational assets, once isolated from corporate networks, now connect to cloud and enterprise systems, broadening attack surfaces. Incidents prompted by this linkage allow adversaries to pivot from IT into safety-critical OT, increasing the likelihood of physical disruption. United States agencies report that even low-skill groups successfully target industrial control systems, exposing weak segmentation and minimal multifactor authentication. Network zoning, zero-trust policies, and real-time anomaly detection are therefore moving from best practice to baseline expectation. Complexity grows as firms modernize without halting production, forcing staged rollouts and parallel architectures. Improved governance that aligns IT security, engineering, and production teams forms a critical piece of spend over the forecast horizon.
Mandatory TSA and IEC Cyber Rules for Pipelines
Revised Transportation Security Administration directives compel pipeline operators to verify controls, close gaps, and report breaches in set time windows. IEC 62443 is simultaneously emerging as the global control-system benchmark, with regional groups such as Japan's CERT delivering implementation guidance. Europe's NIS2 directive layers additional duties by mandating incident disclosure within 24 hours. Monetary penalties and potential shutdown orders for non-compliance raise security from discretionary spending to operational necessity. Vendors versed in both governance and technical deployment are in demand as operators seek turnkey compliance programs.
Legacy SCADA Upgrades Cost Overruns
Many platforms still rely on 20-year-old supervisory control systems never architected for network exposure. Firms routinely underestimate the engineering and downtime expense needed for segmentation, multifactor authentication, and encrypted telemetry. Upgrades often cost two to three times the original budget when compatibility hurdles surface mid-deployment. Extended asset lifecycles make capital allocation difficult, forcing operators to weigh short-term productivity loss against long-term resilience. Academic studies find that ineffective cross-department communication further delays execution and inflates cost.
Other drivers and restraints analyzed in the detailed report include:
- AI-Driven Predictive Security Analytics Adoption
- Energy-Price Volatility Boosting Insurance Requirements
- Shortage of OT-Security Talent in Remote Basins
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Surveillance platforms commanded 30.4% revenue share in 2024, confirming the market's long-standing focus on perimeter and situational awareness. The oil and gas security market size tied to video analytics, drones, and access control remains significant, but annual growth moderates as budgets reallocate toward digital defenses. Network and cybersecurity solutions, advancing at an 8.1% CAGR, reflect mandatory pipeline rules and the rise in ransomware aimed at field assets. Incidents such as the Colonial Pipeline attack emphasized that an operational halt can stem from a laptop rather than a fence breach, nudging capital toward intrusion detection and secure remote-access gateways.
In the forecast window, integrated command centers that fuse camera feeds with cyber telemetry are expected to outpace single-purpose deployments. This convergence reduces false positives by correlating physical badges with network logins. Vendors able to cross-tag events from cameras, firewalls, and controllers into a unified screen are likely to capture an expanding slice of the oil and gas security market. Consequently, surveillance remains vital but increasingly embedded within broader cyber-physical platforms, moderating standalone unit sales while lifting software analytics revenue.
Hardware still comprised 52.6% of the oil and gas security market share in 2024, spanning firewalls ruggedized for hazardous zones, intrinsically safe cameras, and vibration-resistant servers. However, the managed-services segment posts a 9.3% CAGR as operators contract 24 X 7 monitoring and incident response to offset skill gaps. The oil and gas security market size attached to service retainers is increasing because each new site demands advanced analytics, threat intelligence feeds, and periodic red-team assessments.
Service growth is also tied to regulatory audits, which require independent validation and documentation. Firms lacking internal capacity rely on MSSPs that specialise in OT assets; these providers bundle asset discovery, vulnerability management, and compliance reporting into multi-year agreements. Hardware vendors are reacting through outcome-based models that package equipment and services, thereby smoothing revenue and deepening customer lock-in.
Oil and Gas Security Market is Segmented by Security Type (Network and Cyber Security, Surveillance, Screening and Detection, and More), Component (Hardware, Software Platforms, and Services), Operation Stage (Upstream, Midstream, and Downstream), Deployment Mode (On-Premise, Cloud, and Hybrid/Edge-Cloud), Application (Exploration and Production Sites, Offshore Platforms and FPSOs, and More), and Geography.
Geography Analysis
North America maintained a 36.22% stake in the oil and gas security market in 2024, supported by mandatory TSA directives and the lingering lessons of the Colonial Pipeline ransomware event. Canada's threat assessments cite state-sponsored actors targeting production and midstream hubs, prompting coordinated public-private drills and grants for OT segmentation. Offshore assets in the Gulf of Mexico and the North Slope face calls for urgent cyber upgrades following federal audits that flagged outdated firewalls and unpatched HMIs.
Asia-Pacific records the fastest CAGR at 9.1% through 2030 as China extends trunk pipelines and storage capacity into border regions, blending OT security with sovereign cloud mandates from Beijing. Japan legislated economic-security rules that classify oil and gas as critical social infrastructure, compelling operators to file security plans with regulators. India expands refinery capacity and LNG terminals, sourcing managed services from local security operations centers in Bengaluru and Hyderabad. Australia and South Korea embed OT security clauses into new LNG export projects after noting rising regional tension in the South China Sea.
Europe's modernization drive centers on the NIS2 framework that mandates 24-hour incident reporting and annual audits for essential energy entities. LNG import build-outs across Germany, France, and the Netherlands add scale and complexity, necessitating encrypted maritime-to-terminal links. The Middle East and Africa experience stepped-up funding after a 206% rise in documented attacks, showcased at regional cyber forums. Latin America remains nascent but sees incremental investment as Brazil, Argentina, and Guyana grow production and seek alignment with IEC 62443.
- ABB Ltd.
- Airbus Defence and Space
- BAE Systems plc
- Baker Hughes Cyber-Security Services
- Belden Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems Inc.
- Claroty Ltd.
- Dragos Inc.
- Fortinet Inc.
- Honeywell International Inc.
- Huawei Technologies Co. Ltd.
- Johnson Controls International plc
- Kaspersky Lab JSC
- Microsoft Corp.
- Nozomi Networks Inc.
- Palo Alto Networks Inc.
- Parsons Corp.
- Rockwell Automation Inc.
- Schneider Electric SE
- Siemens AG
- Tenable OT Security
- Thales Group
- Trend Micro Inc.
- Waterfall Security Solutions Ltd.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Growing OT and IT convergence elevating cyber-risk
- 4.2.2 Mandatory TSA and IEC cyber rules for pipelines
- 4.2.3 AI-driven predictive security analytics adoption
- 4.2.4 Energy-price volatility boosting insurance requirements
- 4.2.5 Autonomous offshore assets needing edge-to-core security
- 4.3 Market Restraints
- 4.3.1 Legacy SCADA upgrades cost overruns
- 4.3.2 Shortage of OT-security talent in remote basins
- 4.3.3 Cloud-based data-sovereignty conflicts
- 4.3.4 ESG divestments curbing long-term capex
- 4.4 Industry Value Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Industry Attractiveness - Porter's Five Forces Analysis
- 4.7.1 Threat of New Entrants
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Bargaining Power of Suppliers
- 4.7.4 Threat of Substitutes
- 4.7.5 Intensity of Competitive Rivalry
- 4.8 Impact of Macroeconomic Factors on the Market
5 MARKET SIZE AND GROWTH FORECASTS (VALUES)
- 5.1 By Security Type
- 5.1.1 Network and Cyber Security
- 5.1.2 Surveillance
- 5.1.3 Screening and Detection
- 5.1.4 Command and Control
- 5.1.5 Physical Access Control
- 5.1.6 Other Types
- 5.2 By Component
- 5.2.1 Hardware
- 5.2.2 Software Platforms
- 5.2.3 Services (Managed and Professional)
- 5.3 By Operation Stage
- 5.3.1 Upstream (Exploration and Production)
- 5.3.2 Midstream (Pipelines and Storage)
- 5.3.3 Downstream (Refining and Distribution)
- 5.4 By Deployment Mode
- 5.4.1 On-premise
- 5.4.2 Cloud
- 5.4.3 Hybrid/Edge-Cloud
- 5.5 By Application
- 5.5.1 Exploration and Production Sites
- 5.5.2 Offshore Platforms and FPSOs
- 5.5.3 Pipeline Monitoring
- 5.5.4 Refineries and Petrochem Plants
- 5.5.5 LNG and Gas Processing
- 5.5.6 Retail and Distribution Terminals
- 5.6 By Geography
- 5.6.1 North America
- 5.6.1.1 United States
- 5.6.1.2 Canada
- 5.6.1.3 Mexico
- 5.6.2 South America
- 5.6.2.1 Brazil
- 5.6.2.2 Argentina
- 5.6.2.3 Chile
- 5.6.2.4 Rest of South America
- 5.6.3 Europe
- 5.6.3.1 Germany
- 5.6.3.2 United Kingdom
- 5.6.3.3 France
- 5.6.3.4 Italy
- 5.6.3.5 Spain
- 5.6.3.6 Russia
- 5.6.3.7 Rest of Europe
- 5.6.4 Asia-Pacific
- 5.6.4.1 China
- 5.6.4.2 India
- 5.6.4.3 Japan
- 5.6.4.4 South Korea
- 5.6.4.5 Malaysia
- 5.6.4.6 Singapore
- 5.6.4.7 Australia
- 5.6.4.8 Rest of Asia-Pacific
- 5.6.5 Middle East and Africa
- 5.6.5.1 Middle East
- 5.6.5.1.1 United Arab Emirates
- 5.6.5.1.2 Saudi Arabia
- 5.6.5.1.3 Turkey
- 5.6.5.1.4 Rest of Middle East
- 5.6.5.2 Africa
- 5.6.5.2.1 South Africa
- 5.6.5.2.2 Nigeria
- 5.6.5.2.3 Egypt
- 5.6.5.2.4 Rest of Africa
- 5.6.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 ABB Ltd.
- 6.4.2 Airbus Defence and Space
- 6.4.3 BAE Systems plc
- 6.4.4 Baker Hughes Cyber-Security Services
- 6.4.5 Belden Inc.
- 6.4.6 Check Point Software Technologies Ltd.
- 6.4.7 Cisco Systems Inc.
- 6.4.8 Claroty Ltd.
- 6.4.9 Dragos Inc.
- 6.4.10 Fortinet Inc.
- 6.4.11 Honeywell International Inc.
- 6.4.12 Huawei Technologies Co. Ltd.
- 6.4.13 Johnson Controls International plc
- 6.4.14 Kaspersky Lab JSC
- 6.4.15 Microsoft Corp.
- 6.4.16 Nozomi Networks Inc.
- 6.4.17 Palo Alto Networks Inc.
- 6.4.18 Parsons Corp.
- 6.4.19 Rockwell Automation Inc.
- 6.4.20 Schneider Electric SE
- 6.4.21 Siemens AG
- 6.4.22 Tenable OT Security
- 6.4.23 Thales Group
- 6.4.24 Trend Micro Inc.
- 6.4.25 Waterfall Security Solutions Ltd.
7 MARKET OPPORTUNITIES AND FUTURE TRENDS
- 7.1 White-Space and Unmet-Need Assessment




















