
|
시장보고서
상품코드
1630390
클라우드 엔드포인트 보호 : 시장 점유율 분석, 산업 동향과 통계, 성장 예측(2025-2030년)Cloud Endpoint Protection - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
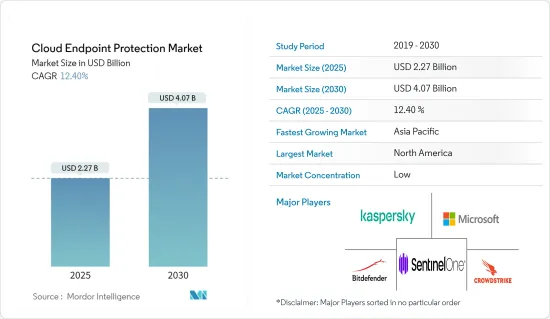
클라우드 엔드포인트 보호 시장 규모는 2025년에 22억 7,000만 달러로 추정되며, 예측 기간(2025-2030년)의 CAGR은 12.4%로, 2030년에는 40억 7,000만 달러에 달할 것으로 예측됩니다.

주요 하이라이트
- 클라우드 엔드포인트 보호 시장은 클라우드 컴퓨팅의 도입 확대와 이에 따른 사이버 위협 증가로 큰 성장을 이루고 있습니다. 이러한 성장은 다양한 업계에서 클라우드의 도입이 급증하고 견고한 보안 대책이 필요해진 것도 요인으로 꼽힙니다.
- 리모트 워크나 BYOD(Bring-your-own-device) 정책의 보급에 의해 사이버 범죄자의 공격 대상이 확대되었습니다. 다양한 위치와 장치에서 기업 리소스에 액세스하는 직원은 데이터 유출 및 기타 사이버 위협을 방지하기 위해 고급 엔드포인트 보호가 필요합니다. 클라우드 기반 엔드포인트 보호 솔루션은 중앙 집중식 관리 및 실시간 위협 감지를 제공하므로 분산된 직원의 안전을 보장하는 데 이상적입니다.
- 사이버 공격의 교묘함은 진화하고 있으며, 위협 당사자는 고급 전술, 기술 및 절차(TTP)를 채택하고 있습니다. 전통적인 엔드포인트 보호 솔루션은 이러한 위협의 진화를 해결할 수 없는 경우가 많습니다. 반면 클라우드 엔드포인트 보호 플랫폼은 인공지능(AI)과 머신러닝(ML)을 활용하여 실시간으로 위협을 감지하고 대응합니다. 새로운 위협에 신속하게 적응하고 대응하는 이 기능을 통해 클라우드 엔드포인트 보호는 현대의 사이버 보안 전략에 매우 중요한 요소가 되었습니다.
- 예를 들어, 2024년 6월, CrowdStrike는 NVIDIA에 의해 가속된 대규모 언어 모델(LLM)을 포함한 엔드 투 엔드 AI 혁신을 보장하기 위해 Hewlett Packard Enterprise와의 전략적 파트너십을 발표했습니다. CrowdStrike Falcon 사이버 보안 플랫폼, HPE GreenLake 클라우드 및 OpsRamp AIOps의 통합을 통해 조직은 단일 통합 프로세스로 IT 운영과 사이버 보안을 원활하게 통합하여 AI 혁신을 안전하게 가속화할 수 있습니다.
- 2024년 5월, 데이터 중심의 클라우드 보안 기업인 Lookout Inc.가 실시한 새로운 조사에서 기업 조직의 직원을 표적으로 한 모바일 피싱 공격에 관한 동향이 밝혀졌습니다. 미국을 거점으로 하는 250명의 CISO를 비롯한 모바일 및 클라우드 사이버 보안 리더가 참가한 이 조사에서는 증가하는 위협에 대항하기 위한 대책 강화가 시급하다는 것이 밝혀졌습니다. 이외에도 SMS 피싱(33%), 소셜 엔지니어링(32%), QR 코드 피싱(30%), 음성 피싱(30%)의 사내 시뮬레이션을 실시하고 있는 응답자는 1/3 다음과 같은 것으로 나타났습니다.
- Managed Security Service Provider(MSSP)의 상승은 시장 성장을 뒷받침하고 있습니다. 많은 기업들은 엔드포인트 보안을 효과적으로 관리하고 모니터링하기 위한 전문 지식을 사내에 가지고 있지 않습니다. MSSP는 클라우드의 엔드포인트 보호를 서비스 포트폴리오의 일부로 제공함으로써 전문적인 전문 지식과 지속적인 모니터링에 대한 액세스를 기업에 제공합니다. 이러한 추세는 보다 광범위한 조직이 고급 엔드포인트 보호에 접근할 수 있게 하여 시장 성장을 더욱 강화하고 있습니다.
- 결론적으로 클라우드 엔드포인트 보호 시장의 성장은 클라우드 컴퓨팅 도입 확대, 원격 근무 환경에서의 견고한 보안 필요성, 사이버 위협 진화, 규제 준수 요구 사항, 랜섬웨어 공격 유행, 보다 광범위한 보안 에코 시스템과의 통합, 경쟁 혁신, 클라우드 솔루션의 확장성, 관리형 보안 서비스의 등장으로 이어집니다.
클라우드 엔드포인트 보호 시장 동향
의료 분야가 큰 성장을 이룰 전망
- 세계의 의료 분야에서는 민감한 데이터를 보호하고 엄격한 규제 기준에 대한 준수를 보장하기 위해 클라우드 엔드포인트 보호 솔루션의 채택이 증가하고 있습니다. 이러한 솔루션의 사용이 증가하고 있는 배경에는 디지털 환자 기록 증가, 연결된 의료기기의 급증, 사이버 위협의 고도화 등 몇 가지 요인이 있습니다.
- 클라우드 엔드포인트 보호는 실시간 위협 감지, 자동 응답 및 중앙 집중식 관리를 모두 클라우드를 통해 제공함으로써 노트북, 스마트폰, 태블릿, 의료기기 등의 엔드포인트를 보호하는 종합적인 접근 방식을 제공합니다.
- 또한 COVID-19 팬데믹 시에 급증한 의료 분야의 원격 의료 서비스의 도입으로 공격 대상이 확대되고 있습니다. 더 많은 건강 관리 전문가와 환자가 원격으로 서비스에 액세스하게 되어 엔드포인트 보안을 확보하는 것이 가장 중요한 과제입니다. 클라우드 엔드포인트 보호 솔루션은 물리적으로 제한되지 않는 강력한 보안 조치를 제공하므로 원격 및 온프레미스 엔드포인트도 동일하게 보호됩니다. 이것은 원격 의료 상호 작용의 무결성과 기밀성을 유지하는 데 매우 중요합니다.
- 예를 들어, 미국의 주요 비영리 학술 의료 센터인 Mayo Clinic은 환자 데이터와 연결된 장치의 광범위한 네트워크를 보호하기 위해 고급 사이버 보안 대책을 통합하는 최전선에 서 있습니다. 이 센터는 AI와 ML을 통합한 클라우드 엔드포인트 보호 솔루션을 활용하여 사이버 보안 태세를 강화하고 있습니다. 이러한 기술을 활용함으로써 Mayo Clinic은 엔드포인트를 지속적으로 모니터링하고, 이상을 감지하고, 잠재적인 위협에 실시간으로 대응할 수 있습니다.
- 2024년 5월 데이터 중심의 클라우드 보안 회사인 Lookout Inc.는 주요 클라우드 상거래 마켓플레이스인 Pax8과의 전략적 파트너십을 발표했습니다. 이 제휴를 통해 관리형 서비스 제공업체(MSP)는 Pax8 마켓플레이스에서 직접 Lookout Mobile Endpoint Security를 구입할 수 있게 되며, 주요 모바일 데이터세트와 조사팀의 실용적인 위협 인텔리전스에 의해 지원됩니다. Lookout Mobile Endpoint Security는 시각화, 조사 및 보호 기능을 결합하여 iOS, Android, ChromeOS용 업계 최첨단 엔드포인트 감지 및 대응(EDR) 솔루션을 제공합니다.
- 의료 분야에서는 환자 데이터를 보호하기 위해 클라우드 엔드포인트 보호에 주목하고 있습니다. 의료 조직은 엄청난 양의 개인 식별 정보(PII)와 보호된 의료 정보(PHI)를 관리하며, 이들은 사이버 범죄자의 모습의 표적이 되고 있습니다. 정보 유출은 엄청난 금전적 손실, 평판 손상, 심각한 법적 영향으로 이어질 수 있습니다.
- 클라우드 엔드포인트 보호 플랫폼은 인공지능(AI) 및 머신러닝(ML)과 같은 고급 기술을 채택하여 보안을 강화하고 위협을 사전에 감지하고 대응합니다. 이러한 기술은 보안 침해를 나타낼 수 있는 비정상적인 패턴과 동작을 식별하고 신속한 개입과 완화를 가능하게 합니다.
아시아태평양이 현저한 성장을 이룰 전망
- 아시아태평양은 각 업계의 디지털 전환 진전, 사이버 보안 위협 증가, 클라우드 기반 솔루션 도입 증가 등을 배경으로 시장의 급속한 성장을 목표로 하고 있습니다. 이 지역의 다양하고 역동적인 경제 상황은 정부의 지원 정책과 함께 CEP 솔루션의 보급에 기여하는 환경을 조성합니다.
- 아시아태평양 시장 성장에 기여하는 주요 요인은 노트북, 데스크톱, 모바일 장치 등의 엔드포인트를 목표로 하는 사이버 위협과 고급 공격의 급증입니다. 또한 은행, 금융서비스, 보험(BFSI), 의료, 소매 등 다양한 분야의 급속한 디지털화로 클라우드에서 처리·보존되는 기밀 데이터의 양이 대폭 증가하고 있습니다. 이러한 이유로 침해 및 무단 액세스로부터 데이터를 보호하기 위해 강력한 클라우드 엔드포인트 보호 대책을 도입해야 합니다.
- 이 지역에서는 IT 인프라가 성장하고 고속 인터넷의 보급이 진행되고 있는 것이 클라우드 엔드포인트 보호의 채용에 더욱 박차를 가하고 있습니다. 중국, 인도, 일본, 한국 등의 국가들은 이 디지털 혁명의 최전선에 있으며, 연결성과 디지털 인프라 강화에 많은 투자가 이루어지고 있습니다. 더 많은 기업들이 클라우드로 전환하고 엔드포인트를 보호하는 견고한 보안 솔루션이 필요함에 따라 시장 성장의 탄탄한 토대가 되고 있습니다.
- 2024년 5월 Amazon.com 산하의 Amazon Web Services(AWS)와 CrowdStrike는 사이버 보안 통합과 클라우드 혁신을 가속화하기 위한 전략적 파트너십 확대를 발표했습니다. 이 파트너십의 일환으로 아마존은 사이버 보안을 CrowdStrike Falcon 플랫폼으로 통합하여 코드에서 클라우드, 디바이스에서 데이터까지 회사를 보호합니다.
- 일본의 사이버 보안 기업인 Trend Micro는 아시아태평양 시장에 견고한 발판을 구축하고 있습니다. Trend Micro는 머신러닝 및 행동 분석을 활용하여 위협을 감지하고 완화하는 종합적인 클라우드 엔드포인트 보호 솔루션을 제공합니다. 이 회사의 솔루션은 지속적인 모니터링, 자동화된 위협 대응 및 기타 보안 도구와의 통합을 제공하며 엔드포인트 보호에 대한 종합적인 접근 방식을 제공합니다.
- 전반적으로, 이 지역은 비즈니스 디지털화의 진전, 사이버 위협의 급증, 클라우드 기반 보안 솔루션이 제공하는 이점이 원동력이 되어 큰 시장 성장을 이루고 있습니다. 정부 규제 지원, IoT 상승, 지역 IT 인프라 개선 등이 성장을 더욱 뒷받침하고 있습니다.
클라우드 엔드포인트 보호 산업 개요
클라우드 엔드포인트 보호 시장은 소규모, 지역 규모, 다국적 규모 등 모든 규모 공급업체가 존재하기 때문에 매우 세분화되어 있습니다. 시장 경쟁이 치열하기 때문에 주요 기업들은 독자적인 가치 제안, 제품 차별화, 여러 파트너십 형성에 주력하여 입지를 강화하고 있습니다.
기타 혜택 :
- 엑셀 형식 시장 예측(ME) 시트
- 3개월간의 애널리스트 서포트
목차
제1장 서론
- 조사의 전제조건과 시장 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 인사이트
- 시장 개요
- 산업 밸류체인 분석
- 업계의 매력도 - Porter's Five Forces 분석
- 공급기업의 협상력
- 소비자의 협상력
- 신규 진입업자의 위협
- 대체품의 위협
- 경쟁 기업 간 경쟁 관계
제5장 시장 역학
- 시장 성장 촉진요인
- 스마트 디바이스 시장의 성장
- 데이터 유출 증가
- 시장 성장 억제요인
- 사이버 공격에 대한 인식 부족
- 거시 경제 요인이 업계에 미치는 영향 평가
제6장 시장 세분화
- 기업 규모별
- 중소기업
- 대기업
- 배포 모드별
- 프라이빗 클라우드
- 퍼블릭 클라우드
- 하이브리드 클라우드
- 최종 사용자 업계별
- BFSI
- 정부기관
- 헬스케어
- 에너지 및 전력
- 소매
- IT 및 텔레콤
- 기타 최종 사용자 산업
- 지역별
- 북미
- 유럽
- 아시아
- 호주 및 뉴질랜드
- 라틴아메리카
- 중동 및 아프리카
제7장 경쟁 구도
- 기업 프로파일
- Bitdefender LLC
- CrowdStrike Holdings, Inc.
- Microsoft Corporation
- SentinelOne Inc.
- Kaspersky Lab Inc.
- Sophos Group PLC
- Vmware, Inc.
- Cisco Systems Inc.
- McAfee LLC
- Trend Micro Inc.
- Fortinet Inc.
- Broadcom Inc.(Symantec Corporation)
- Avast Software SRO
제8장 투자 분석
제9장 시장의 미래
KTH 25.02.05The Cloud Endpoint Protection Market size is estimated at USD 2.27 billion in 2025, and is expected to reach USD 4.07 billion by 2030, at a CAGR of 12.4% during the forecast period (2025-2030).
Key Highlights
- The cloud endpoint protection market has experienced significant growth driven by the increased adoption of cloud computing and the corresponding rise in cyber threats. The growth can also be attributed to factors like the surge in cloud adoption across various industries, which necessitated robust security measures.
- The proliferation of remote work and bring-your-own-device (BYOD) policies expanded the attack surface for cybercriminals. Employees accessing corporate resources from various locations and devices require advanced endpoint protection to prevent data breaches and other cyber threats. Cloud endpoint protection solutions offer centralized management and real-time threat detection, making them ideal for securing a distributed workforce.
- The sophistication of cyberattacks has evolved, with threat actors employing advanced tactics, techniques, and procedures (TTPs). Traditional endpoint protection solutions often struggle to keep pace with these evolving threats. In contrast, cloud endpoint protection platforms leverage artificial intelligence (AI) and machine learning (ML) to detect and respond to threats in real time. This capability to adapt and respond to new threats quickly has made cloud endpoint protection a crucial component of modern cybersecurity strategies.
- For instance, in June 2024, CrowdStrike announced a strategic partnership with Hewlett Packard Enterprise to secure end-to-end AI innovation, including large language models (LLMs), accelerated by NVIDIA. With the integration of the CrowdStrike Falcon cybersecurity platform, HPE GreenLake cloud, and OpsRamp AIOps, organizations can seamlessly unify IT operations and cybersecurity in a single, unified process to securely accelerate AI innovation.
- In May 2024, a new survey conducted by Lookout Inc., the data-centric cloud security company, unveiled concerning trends regarding mobile phishing attacks targeting the employees of enterprise organizations. The survey, completed by 250 United States-based CISOs and other mobile and cloud cybersecurity leaders, shed light on the urgent need for enhanced measures to combat the growing threat. In addition to this, the results indicated that less than one-third of respondents conducted internal simulations of SMS phishing (33%), social engineering (32%), QR code phishing (30%), or voice phishing (30%).
- The rise of managed security service providers (MSSPs) has also bolstered the market's growth. Many organizations lack the in-house expertise to effectively manage and monitor endpoint security. MSSPs offer cloud endpoint protection as part of their service portfolio, providing organizations with access to specialized expertise and continuous monitoring. This trend has made advanced endpoint protection accessible to a broader range of organizations, further driving market growth.
- In conclusion, the growth of the cloud endpoint protection market is driven by the increasing adoption of cloud computing, the need for robust security in remote work environments, the evolution of cyber threats, regulatory compliance requirements, the prevalence of ransomware attacks, the integration with broader security ecosystems, competitive innovation, the scalability of cloud solutions, and the rise of managed security services.
Cloud Endpoint Protection Market Trends
The Healthcare Segment is Expected to Witness Significant Growth
- The global healthcare sector has been increasingly adopting cloud endpoint protection solutions to safeguard sensitive data and ensure compliance with stringent regulatory standards. The rising usage of these solutions is driven by several factors, including the increasing volume of digital patient records, the proliferation of connected medical devices, and the growing sophistication of cyber threats.
- Cloud endpoint protection offers a comprehensive approach to securing endpoints such as laptops, smartphones, tablets, and medical devices by providing real-time threat detection, automated response, and centralized management, all delivered through the cloud.
- Moreover, the healthcare sector's adoption of telehealth services, which surged during the COVID-19 pandemic, has expanded the attack surface. With more healthcare professionals and patients accessing services remotely, securing endpoints becomes paramount. Cloud endpoint protection solutions provide robust security measures that are not limited by physical location, ensuring that remote and on-premises endpoints are equally protected. This is crucial in maintaining the integrity and confidentiality of telehealth interactions.
- For instance, Mayo Clinic, a key nonprofit American academic medical center, has been at the forefront of integrating advanced cybersecurity measures to protect its extensive network of patient data and connected devices. The organization utilizes a cloud endpoint protection solution that incorporates AI and ML to enhance its cybersecurity posture. By leveraging these technologies, Mayo Clinic can continuously monitor its endpoints, detect anomalies, and respond to potential threats in real time.
- In May 2024, Lookout Inc., the data-centric cloud security company, introduced a strategic partnership with Pax8, a key cloud commerce marketplace. The partnership enables managed service providers (MSPs) to acquire Lookout Mobile Endpoint Security directly from the Pax8 Marketplace, backed by actionable threat intelligence from the leading mobile dataset and research team. Lookout Mobile Endpoint Security combines visibility, research, and protection to deliver the industry's most advanced endpoint detection and response (EDR) solution for iOS, Android, and ChromeOS.
- There is a heightened focus on cloud endpoint protection in healthcare to protect patient data. Healthcare organizations manage vast amounts of personally identifiable information (PII) and protected health information (PHI), which are prime targets for cybercriminals. Breaches can lead to significant financial losses, damage to reputation, and severe legal consequences.
- Cloud endpoint protection platforms enhance security by employing advanced technologies such as artificial intelligence (AI) and machine learning (ML) to detect and respond to threats proactively. These technologies enable the identification of unusual patterns and behaviors that may indicate a security breach, allowing for quicker intervention and mitigation.
Asia-Pacific is Expected to Witness Significant Growth
- Asia-Pacific is witnessing rapid growth in the market, driven by increasing digital transformation across industries, rising cybersecurity threats, and the increasing adoption of cloud-based solutions. The region's diverse and dynamic economic landscape, coupled with supportive government policies, is fostering a conducive environment for the proliferation of CEP solutions.
- The primary factors contributing to the growth of the market in Asia-Pacific are the surge in cyber threats and sophisticated attacks targeting endpoints, including laptops, desktops, and mobile devices. Furthermore, the rapid digitization of various sectors, such as banking, financial services, and insurance (BFSI), healthcare, and retail, has significantly increased the volume of sensitive data being processed and stored in the cloud. This has necessitated the deployment of robust cloud endpoint protection measures to safeguard data against breaches and unauthorized access.
- The region's growing IT infrastructure and the increasing penetration of high-speed internet are further fueling the adoption of cloud endpoint protection. Countries like China, India, Japan, and South Korea are at the forefront of this digital revolution, with substantial investments being made in enhancing connectivity and digital infrastructure. This is providing a solid foundation for the growth of the market as more businesses migrate to the cloud, requiring robust security solutions to protect endpoints.
- In May 2024, Amazon Web Services (AWS), an Amazon.com company, and CrowdStrike announced an expanded strategic partnership to accelerate cybersecurity consolidation and cloud transformation. As part of the partnership, Amazon unified its cybersecurity protection on the CrowdStrike Falcon platform, protecting the company from code to cloud and device to data.
- Trend Micro, a Japanese cybersecurity company, has a strong foothold in the Asia-Pacific market. Trend Micro offers a comprehensive cloud endpoint protection solution that leverages machine learning and behavioral analysis to detect and mitigate threats. The company's solution provides continuous monitoring, automated threat response, and integration with other security tools to offer a holistic approach to endpoint protection.
- Overall, the region is experiencing significant market growth, driven by the increasing digitalization of businesses, the surge in cyber threats, and the advantages offered by cloud-based security solutions. The support from government regulations, the rise of IoT, and the region's improving IT infrastructure are further propelling this growth.
Cloud Endpoint Protection Industry Overview
The cloud endpoint protection market is highly fragmented due to several vendors across all scales, i.e., small-scale, regional, and large multi-national scales. Due to intense market rivalry, key players focus on making unique value prepositions, product differentiation, and forming multiple partnerships to increase their geographical presence.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Value Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Forces Analysis
- 4.3.1 Bargaining Power of Suppliers
- 4.3.2 Bargaining Power of Consumers
- 4.3.3 Threat of New Entrants
- 4.3.4 Threat of Substitutes
- 4.3.5 Intensity of Competitive Rivalry
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Growth of Smart Devices
- 5.1.2 Increasing number of Data Breaches
- 5.2 Market Restraints
- 5.2.1 Lack of Awareness about Cyberattacks
- 5.3 Assessment of Impact of Macroeconomic Factors on the Industry
6 MARKET SEGMENTATION
- 6.1 By Enterprise Size
- 6.1.1 Small & Medium Enterprises
- 6.1.2 Large Enterprises
- 6.2 By Deployment Mode
- 6.2.1 Private Cloud
- 6.2.2 Public Cloud
- 6.2.3 Hybrid Cloud
- 6.3 By End-user Industry
- 6.3.1 BFSI
- 6.3.2 Government
- 6.3.3 Healthcare
- 6.3.4 Energy and Power
- 6.3.5 Retail
- 6.3.6 IT & Telecom
- 6.3.7 Other End-user Industry
- 6.4 By Geography
- 6.4.1 North America
- 6.4.2 Europe
- 6.4.3 Asia
- 6.4.4 Australia and New Zealand
- 6.4.5 Latin America
- 6.4.6 Middle East and Africa
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 Bitdefender LLC
- 7.1.2 CrowdStrike Holdings, Inc.
- 7.1.3 Microsoft Corporation
- 7.1.4 SentinelOne Inc.
- 7.1.5 Kaspersky Lab Inc.
- 7.1.6 Sophos Group PLC
- 7.1.7 Vmware, Inc.
- 7.1.8 Cisco Systems Inc.
- 7.1.9 McAfee LLC
- 7.1.10 Trend Micro Inc.
- 7.1.11 Fortinet Inc.
- 7.1.12 Broadcom Inc. (Symantec Corporation)
- 7.1.13 Avast Software SRO


















