
|
시장보고서
상품코드
1639546
북미의 보안 테스트 : 시장 점유율 분석, 산업 동향, 성장 예측(2025-2030년)North America Security Testing - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
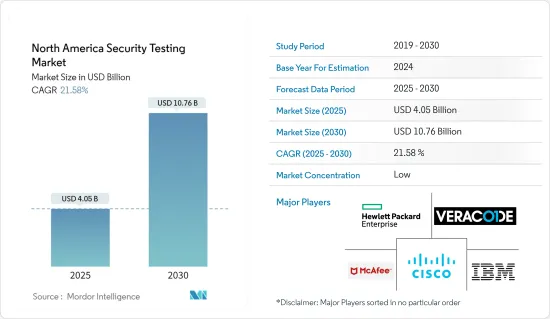
북미 보안 테스트 시장 규모는 2025년에 40억 5,000만 달러로 추정되며, 시장 추계·예측 기간(2025-2030년)의 CAGR은 21.58%로, 2030년에는 107억 6,000만 달러에 달할 것으로 예측됩니다.
북미는 세계적으로 규제가 엄격한 지역으로, 연방 에너지 규제위원회(FERC), HIPAA, PCI DSS, SOX 등 업종에 관계없이 많은 규제와 컴플라이언스가 존재합니다. 북미 기업은 보안, 침입 테스트, 취약성 관리 솔루션의 도입이 상당히 진행되고 있으며 일상 비즈니스 프로세스의 모범 사례로서 침입 테스트 솔루션의 채택을 촉진하고 있습니다.
주요 하이라이트
- 북미는 기술의 중심지입니다. 따라서 연방 정부는 보안 테스트 서비스와 관련하여 매우 엄격한 규칙을 마련하고 있습니다. 또한 BFSI와 같은 업계에서는 컴플라이언스 테스트를 준수해야합니다.
- 보안 위협으로부터의 안전에 대한 요구 증가는 보안 테스트 시장의 성장을 가속하고 있습니다. 디지털 전환 노력, 클라우드 컴퓨팅, IoT, 규제 요구 사항의 조합은 조직의 시스템, 애플리케이션 및 디지털 인프라 취약점을 파악하고 해결하기 위한 종합적인 보안 테스트 서비스에 대한 수요를 낳고 있습니다.
- 정부의 규제는 보안 테스트 시장의 추진에 중요한 역할을 합니다. 북미의 각국 정부는 사이버 보안의 중요성을 인식하고 기밀 데이터, 중요 인프라, 시민의 사생활 보호를 확보하기 위한 규제와 기준을 도입하고 있습니다.
- 보안 테스트의 장점을 모르는 조직은 그러한 관행을 채택하기 어려울 수 있습니다. 조직은 사전 활동적인 보안 조치의 중요성에 더 많은 관심을 기울여야 하며, 사고 대응 및 복구와 같은 반응적인 조치에만 의존할 수 있습니다. 이러한 보안 테스트의 제한적인 채택은 시장 성장을 방해할 수 있습니다.
- COVID-19의 보급에 따라 리모트 워크의 도입이 진행되어, 기업 네트워크나 리소스에 대한 안전한 리모트 액세스가 최우선 사항이 되었습니다. 조직은 가상 사설망(VPN), 원격 데스크톱 프로토콜 및 기타 원격 연결 솔루션을 포함한 원격 액세스 인프라의 보안을 평가하기 위해 보안 테스트에 투자했습니다. 보안 테스트는 이러한 시스템의 취약점을 식별하고 원격 액세스가 제대로 보호되는지 확인하는 데 도움이 되었습니다.
북미 보안 테스트 시장 동향
건강 관리 최종 사용자 산업 부문이 큰 시장 점유율을 차지할 전망
- 건강 관리 최종 사용자 시스템의 보안 테스트는 민감한 환자 데이터 보호, 규정 준수 유지, 잠재적인 보안 침해 방지 등의 이유로 매우 중요합니다. 건강 관리 최종 사용자 시스템의 보안 테스트는 환자 데이터 보호, 규제 준수 유지, 무단 액세스 방지, 의료기기 보호, 운영 위험 경감에 필수적입니다. 보안 테스트를 선호함으로써 의료 조직은 시스템의 기밀성, 무결성, 가용성을 보장하고 환자에게 안전한 의료 서비스를 제공할 수 있습니다.
- 의료 시스템은 의료 기록, 개인 정보, 재무 데이터 등 대량의 기밀 환자 정보를 처리합니다. 보안 테스트를 통해 이러한 데이터를 무단 액세스 및 침해에 노출시킬 수 있는 소프트웨어 및 인프라 취약점을 파악할 수 있습니다. 이러한 보안 공백을 적극적으로 테스트하고 해결함으로써 건강 관리 조직은 환자 데이터를 보호하고 기밀성을 유지할 수 있습니다.
- 의료 산업은 미국에서 의료 보험의 상호 운용성과 책임에 관한 법률(HIPAA) 등 다양한 규제 요건의 대상이 되고 있습니다. 보안 테스트는 보안 관리, 암호화 대책, 액세스 제어 및 기타 관련 보안 관행을 평가하여 의료 시스템이 이러한 규정을 준수하는지 확인합니다. 이러한 규정 준수 기준을 충족함으로써 의료 기관은 처벌과 법적 문제를 피할 수 있습니다.
- Identity Theft Resource Center에 따르면 2023년에는 미국의 의료 부서에서 809건 이상의 데이터 유출 사건이 발생했습니다. 보안 테스트는 공격자가 무단 액세스를 위해 악용할 수 있는 의료 시스템의 취약점을 파악하는 데 도움이 됩니다. 여기에는 취약한 인증 메커니즘, 불충분한 액세스 제어, 암호화되지 않은 통신 채널 등에 대한 취약성 테스트가 포함됩니다. 의료 조직은 이러한 취약점을 해결함으로써 환자 기록, 의료기기 또는 중요 시스템에 대한 무단 액세스를 방지할 수 있습니다.
- 의료 산업은 IoT 장치 및 연결 시스템을 포함한 다양한 의료기기에 의존합니다. 보안 테스트는 이러한 장치가 환자의 안전을 위협하거나 민감한 정보를 노출할 수 있는 공격 및 취약성에 대응할 수 있도록 합니다. 의료기기의 보안을 테스트함으로써 조직은 약점을 파악하고 제조업체와 협력하여 필요한 패치 및 업데이트를 적용할 수 있습니다.
- 보안 테스트는 헬스케어 시스템의 운영 연속성에 영향을 줄 수 있는 잠재적인 위험과 취약성을 파악하는 데 도움이 됩니다. 조직은 약점을 파악하여 적극적으로 해결할 수 있으며 시스템 가동 중지 시간, 데이터 유출 및 주요 의료 서비스 중단의 위험을 줄일 수 있습니다.
미국이 큰 시장 점유율을 차지할 전망
- 미국의 보안 테스트 시장은 사이버 보안 위협에 대한 인식을 높이고 업계 전반에 걸친 견고한 보안 조치의 필요성으로 인해 빠르게 성장하고 있습니다.
- 미국에는 건강 관리에 대한 HIPAA 및 지불 카드 데이터 보안에 대한 PCI DSS를 포함하여 엄격한 규정 및 업계 고유의 규정 준수 요구 사항이 있습니다. 이러한 규정은 조직이 컴플라이언스를 확보하고 고객 데이터를 보호하기 위해 노력하는 동안 보안 테스트 서비스에 대한 수요를 창출합니다.
- 2022년 9월, 미국 국립 표준 기술 연구소(NIST)는 미국에서 IoT 장치의 보안 권고안을 발표했습니다. IoT는 정기적으로 해킹 및 데이터 유출로 인한 사이버 보안 위험에 노출되기 때문에 NIST의 핵심 기준선은 제조업체가 IoT 장치에 통합해야 할 권장 보안 기능과 소비자가 쇼핑하는 동안 장치 포장 및 온라인 설명서에서 확인해야 할 지침을 강조했습니다.
- 미국 행정관리예산국에 따르면 2022년 미국 전체 사이버보안 지출은 2023년으로 증가할 것으로 예측됐으며 그 해 부처의 사이버보안예산안 총액은 약 104억 6,000만 달러였습니다.
- 디지털 전환 구상의 보급, 클라우드의 채용, 접속 디바이스 증가에 의해 보안 테스트 서비스에 대한 수요는 크게 늘어나고 있습니다. 미국의 조직은 사전 예방적 보안 대책의 중요성을 인식하고 있으며 종합적인 보안 테스트 솔루션에 대한 투자에 적극적입니다.
북미 보안 테스트 산업 개요
북미의 보안 테스트 시장은 Hewlett Packard Enterprise Development LP, IBM Corporation, VERACODE, McAfee LLC, Cisco Systems Inc.와 같은 대기업이 존재하며 매우 단편화되어 있습니다. 이 시장의 기업은 제품 제공을 강화하고 지속 가능한 경쟁 우위를 얻기 위해 제휴 및 인수와 같은 전략을 채택합니다.
2023년 4월, 주요 API 보안 공급자 중 하나인 Noname Security는 IBM과 제휴하여 구성 오류, 취약성 및 설계 결함으로부터 고객을 보호합니다. 고객은 Noname Security의 API 보안 솔루션과 IBM DataPower의 기존 엔터프라이즈 보안 기능을 결합한 새로운 Noname Advanced API Security for IBM을 사용하여 IBM API Connect에 추가 보호 계층을 제공할 수 있습니다. 엔터프라이즈 사용자는 Noname API Security Platform을 통해 검색, 포스처 관리, 런타임 보호 및 보안 테스트와 같은 향상된 API 보안의 이점을 누릴 수 있습니다.
2022년 9월, 소프트웨어 공급망 위험 및 보안 기술의 주요 기업 중 하나인 Cybeats Technologies Inc.(이하 "Cybeats" 또는 "회사")는 애플리케이션 보안 테스트 솔루션의 세계 리더 Veracode와의 전략적 파트너십을 발표했습니다.
기타 혜택
- 엑셀 형식 시장 예측(ME) 시트
- 3개월간의 애널리스트 서포트
목차
제1장 서론
- 조사의 전제조건과 시장 정의
- 조사 범위
제2장 조사 방법
제3장 주요 요약
제4장 시장 역학
- 시장 개요
- 밸류체인/서플라이체인 분석
- 업계의 매력도 - Porter's Five Forces 분석
- 구매자의 협상력
- 공급기업의 협상력
- 신규 참가업체의 위협
- 대체품의 위협
- 경쟁 기업간 경쟁 관계의 강도
- COVID-19가 업계에 미치는 영향의 평가
제5장 시장 인사이트
- 촉진요인
- 보안 위협으로부터의 안전성에 대한 요구 증가
- 보안 요구를 촉진하는 정부 규제
- 시장의 과제
- 보안 테스트에 대한 의식
제6장 시장 세분화
- 전개별
- 온프레미스
- 클라우드
- 하이브리드
- 유형별
- 네트워크 보안 테스트
- VPN 테스트
- 방화벽 테스트
- 기타 서비스 유형
- 애플리케이션 보안 테스트
- 애플리케이션 유형
- 모바일 애플리케이션 보안 테스트
- 웹 애플리케이션 보안 테스트
- 클라우드 애플리케이션 보안 테스트
- 엔터프라이즈 애플리케이션 보안 테스트
- 테스트 유형
- SAST
- DAST
- IAST
- RASP
- 네트워크 보안 테스트
- 테스트 툴별
- 웹 애플리케이션 테스트 툴
- 코드 리뷰 도구
- 침투 테스트 도구
- 소프트웨어 테스트 툴
- 기타 테스트 툴
- 최종 사용자 업계별
- 정부기관
- BFSI
- 헬스케어
- 제조업
- IT 및 통신
- 소매업
- 기타 최종 사용자 산업
- 국가별
- 미국
- 캐나다
제7장 경쟁 구도
- 기업 프로파일
- Hewlett Packard Enterprise Development LP
- IBM Corporation
- VERACODE
- McAfee LLC
- Cisco Systems Inc.
- Core Security Technologies
- Offensive Security
- Accenture PLC
- Maveric Systems
- Synopsys Inc.
- Secureworks Inc.
제8장 투자 분석
제9장 시장의 미래
CSM 25.02.17The North America Security Testing Market size is estimated at USD 4.05 billion in 2025, and is expected to reach USD 10.76 billion by 2030, at a CAGR of 21.58% during the forecast period (2025-2030).

North America is a highly regulated region globally with numerous regulations and compliances, such as the Federal Energy Regulatory Commission (FERC), HIPAA, PCI DSS, and SOX, across verticals. North American companies are quite advanced at deploying security, penetration testing, and vulnerability management solutions and have best practices for everyday business processes, thereby driving the adoption of penetration testing solutions.
Key Highlights
- The North American region is a technology hub. Therefore, the federal government has made very stringent rules regarding security testing services. Moreover, it is compulsory for industries, such as BFSI, to adhere to compliance testing.
- The increasing need for safety from security threats is driving the growth of the security testing market. The combination of digital transformation initiatives, cloud computing, IoT, and regulatory requirements has created a demand for comprehensive security testing services to help organizations identify and address vulnerabilities in their systems, applications, and digital infrastructure.
- Government regulations play a significant role in driving the security testing market. Governments in North America have recognized the importance of cybersecurity and have introduced regulations and standards to ensure the protection of sensitive data, critical infrastructure, and citizen privacy.
- Organizations unaware of the benefits of security testing may be less likely to adopt such practices. They might need to pay more attention to the importance of proactive security measures and rely solely on reactive measures like incident response and recovery. This limited adoption of security testing can hinder the growth of the market.
- With the widespread COVID-19, the adoption of remote work, securing remote access to corporate networks and resources became a top priority. Organizations invested in security testing to assess the security of their remote access infrastructure, including virtual private networks (VPNs), remote desktop protocols, and other remote connectivity solutions. Security testing helped identify vulnerabilities in these systems and ensured that remote access was adequately protected.
North America Security Testing Market Trends
Healthcare End User Industry Segment is Expected to Hold Significant Market Share
- Security testing is crucial in healthcare end-user systems by protecting sensitive patient data, maintaining regulatory compliance, and preventing potential security breaches. Security testing in healthcare end-user systems is essential for protecting patient data, maintaining regulatory compliance, preventing unauthorized access, securing medical devices, and mitigating operational risks. By prioritizing security testing, healthcare organizations can ensure their systems' confidentiality, integrity, and availability and provide patients with safer and more secure healthcare services.
- Healthcare systems handle many sensitive patient information, including medical records, personal details, and financial data. Security testing helps identify vulnerabilities and weaknesses in the software and infrastructure that could expose this data to unauthorized access or breaches. By proactively testing and addressing these security gaps, healthcare organizations can safeguard patient data and maintain confidentiality.
- The healthcare industry is subject to various regulatory requirements, such as the Health Insurance Portability and Accountability Act (HIPAA) in the United States. Security testing ensures that healthcare systems comply with these regulations by assessing their security controls, encryption measures, access controls, and other relevant security practices. Meeting these compliance standards helps healthcare organizations avoid penalties and legal issues.
- According to Identity Theft Resource Center, In 2023, there were more than 809 incidents of data compromises in the healthcare sector in the United States. Security testing helps identify vulnerabilities and weaknesses in healthcare systems that attackers could exploit to gain unauthorized access. This includes testing for vulnerabilities such as weak authentication mechanisms, inadequate access controls, or unencrypted communication channels. Healthcare organizations can prevent unauthorized access to patient records, medical devices, or critical systems by addressing these vulnerabilities.
- The healthcare industry relies on various medical devices, including IoT devices and connected systems. Security testing ensures these devices resist potential attacks and vulnerabilities that could compromise patient safety or expose sensitive information. By testing the security of medical devices, organizations can identify weaknesses and work with manufacturers to apply necessary patches or updates.
- Security testing helps identify potential risks and vulnerabilities that could impact the operational continuity of healthcare systems. Organizations can proactively address weaknesses by identifying them and reducing the risk of system downtime, data loss, or disruption of critical healthcare services.
United States is Expected to Hold Significant Market Share
- The security testing market in the United States is rapidly growing due to the increasing awareness of cybersecurity threats and the need for robust security measures across industries.
- The United States has stringent regulations and industry-specific compliance requirements, such as HIPAA for healthcare and PCI DSS for payment card data security. These regulations drive the demand for security testing services as organizations strive to ensure compliance and protect customer data.
- In September 2022, The National Institute of Standards and Technology (NIST) issued Draft Security Recommendations for IoT Devices in the United States. Because IoT regularly posed a cybersecurity risk through hacks and data breaches, the NIST's Core Baseline highlighted recommended security features for manufacturers to incorporate into their IoT devices and guidelines for consumers to look for on a device's box or online description while shopping.
- According to the US Office of Management and Budget, In 2022, the overall cyber security spending in the United States was projected to increase in 2023, with the total proposed agency cyber security funding for the year approximately USD 10.46 billion.
- With the proliferation of digital transformation initiatives, cloud adoption, and an increasing number of connected devices, the demand for security testing services has grown significantly. Organizations in the United States realize the importance of proactive security measures and are willing to invest in comprehensive security testing solutions.
North America Security Testing Industry Overview
The North American Security Testing Market is highly fragmented with the presence of major players like Hewlett Packard Enterprise Development LP, IBM Corporation, VERACODE, McAfee LLC, and Cisco Systems Inc. Players in the market are adopting strategies such as partnerships and acquisitions to enhance their product offerings and gain sustainable competitive advantage.
In April 2023, Noname Security, one of the significant API security providers, partnered with IBM to protect clients against misconfigurations, vulnerabilities, and design defects. Customers can use Noname Security's API security solution and IBM DataPower's existing enterprise security capabilities to provide an extra layer of protection for IBM API Connect with the new Noname Advanced API Security for IBM. Enterprise users would benefit from enhanced API security, such as discovery, posture management, runtime protection, and security testing, with the Noname API Security Platform.
In September 2022, Cybeats Technologies Inc. ("Cybeats" or the "Company"), one of the leading providers of software supply chain risk and security technologies, announced a strategic partnership with Veracode, one of the global leaders in application security testing solutions.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Value Chain/Supply Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Forces Analysis
- 4.3.1 Bargaining Power of Buyers
- 4.3.2 Bargaining Power of Suppliers
- 4.3.3 Threat of New Entrants
- 4.3.4 Threat of Substitute Products
- 4.3.5 Intensity of Competitive Rivalry
- 4.4 Assessment of the COVID-19 Impact on the Industry
5 MARKET INSIGHTS
- 5.1 Market Drivers
- 5.1.1 Increasing Need for Safety from Security Threats
- 5.1.2 Government Regulations Driving Security Needs
- 5.2 Market Challenges
- 5.2.1 Awareness Regarding Security Testing
6 MARKET SEGMENTATION
- 6.1 By Deployment
- 6.1.1 On-premise
- 6.1.2 Cloud
- 6.1.3 Hybrid
- 6.2 By Type
- 6.2.1 Network Security Testing
- 6.2.1.1 VPN Testing
- 6.2.1.2 Firewall Testing
- 6.2.1.3 Other Service Types
- 6.2.2 Application Security Testing
- 6.2.2.1 Application Type
- 6.2.2.1.1 Mobile Application Security Testing
- 6.2.2.1.2 Web Application Security Testing
- 6.2.2.1.3 Cloud Application Security Testing
- 6.2.2.1.4 Enterprise Application Security Testing
- 6.2.2.2 Testing Type
- 6.2.2.2.1 SAST
- 6.2.2.2.2 DAST
- 6.2.2.2.3 IAST
- 6.2.2.2.4 RASP
- 6.2.1 Network Security Testing
- 6.3 By Testing Tool
- 6.3.1 Web Application Testing Tool
- 6.3.2 Code Review Tool
- 6.3.3 Penetration Testing Tool
- 6.3.4 Software Testing Tool
- 6.3.5 Other Testing Tools
- 6.4 By End-user Industry
- 6.4.1 Government
- 6.4.2 BFSI
- 6.4.3 Healthcare
- 6.4.4 Manufacturing
- 6.4.5 IT and Telecom
- 6.4.6 Retail
- 6.4.7 Other End-user Industries
- 6.5 By Country
- 6.5.1 United States
- 6.5.2 Canada
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 Hewlett Packard Enterprise Development LP
- 7.1.2 IBM Corporation
- 7.1.3 VERACODE
- 7.1.4 McAfee LLC
- 7.1.5 Cisco Systems Inc.
- 7.1.6 Core Security Technologies
- 7.1.7 Offensive Security
- 7.1.8 Accenture PLC
- 7.1.9 Maveric Systems
- 7.1.10 Synopsys Inc.
- 7.1.11 Secureworks Inc.



















